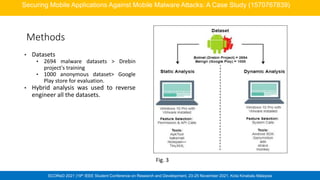
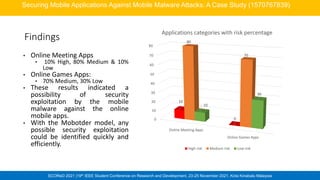
This case study presents a new model called Mobotder to detect possible security exploits in mobile applications like online meeting and gaming apps. The model analyzes app features like geolocation, permissions, API calls and system calls. It evaluated 2694 malware and 1000 benign apps, achieving 99.1% accuracy in classifying apps as malicious or benign. The model found 10% of meeting apps and 30% of gaming apps have high or medium risk of exploit. This shows Mobotder can efficiently identify potential security issues in mobile apps.








![SCOReD 2021 |19th IEEE Student Conference on Research and Development, 23-25 November 2021, Kota Kinabalu Malaysia
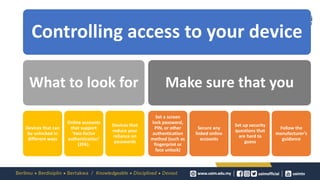
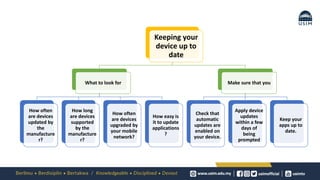
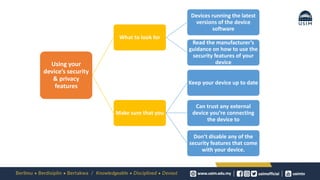
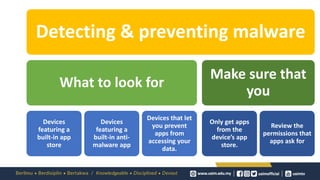
Findings
Securing Mobile Applications Against Mobile Malware Attacks: A Case Study (1570767839)
Fig.4: Example of Mobotder
Mobile App Simulation for Online
Gaming Mobile Apps Evaluation
Fig.5: Example of Mobotder
Mobile App Simulation for Online
Meeting Mobile Apps Evaluation
Feature Work by
[19]
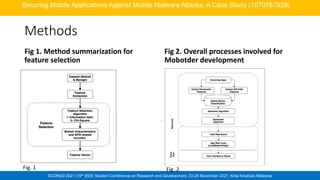
Work by [20] Work by [21] Work by [22] Mobotder
Number of
Samples
(Malware/
Benign)
1929/
150
250/
250
5560/ 5560 1931/1150 2694/1000
Number of
Features
(Permission/AP
I calls)
63/
1414
12
/8
Not stated the
number of
Permission, API
calls, hardware
components,
intents
Not stated the
number of
Permission, API
calls, intents,
metadata, system
calls, network
30/38
ML Classifier
Accuracy
Rate(%)
Random
Forest
93.9
PSO-ANFIS
89
Random Forest
97.24
Random Forest
97.48
Random
Forest
99.1
Comparison with previous studies](https://image.slidesharecdn.com/week5mobiledevicesecurity31032022-220331021615/85/WEEK5-Mobile-Device-Security-31032022-pdf-26-320.jpg)

![SCOReD 2021 |19th IEEE Student Conference on Research and Development, 23-25 November 2021, Kota Kinabalu Malaysia
References
[1] P. Laplante, “Contactless u: Higher education in the postcoronavirus world,” Computer (Long. Beach. Calif)., vol. 53, no. 7, pp. 76–79, Jul. 2020, doi:
10.1109/MC.2020.2990360.
[2] M. Humayun, M. Niazi, · Nz Jhanjhi, · Mohammad Alshayeb, and · Sajjad Mahmood, “Cyber Security Threats and Vulnerabilities: A Systematic Mapping
Study,” Arab. J. Sci. Eng., vol. 45, no. 3, pp. 3171–3189, 2020, doi: 10.1007/s13369-019-04319-2.
[3] Paul Wagenseil, “Zoom security issues: Everything that’s gone wrong (so far) ,” Tom’s Guide, 2020. https://www.tomsguide.com/news/zoom-security-
privacy-woes (accessed Mar. 23, 2021).
[7] Sue Poremba, “Online Gaming Adds More Risk to WFH - Security Boulevard,” Security Boulevard, Jan. 04, 2020.
https://securityboulevard.com/2021/01/online-gaming-adds-more-risk-to-wfh/ (accessed Mar. 24, 2021).
[19] L. Onwuzurike, E. Mariconti, P. Andriotis, E. De Cristofaro, G. Ross, and G. Stringhini, “Mamadroid: Detecting android malware by building Markov chains of
behavioral models (extended version),” ACM Trans. Priv. Secur., vol. 22, no. 2, 2019, doi: 10.1145/3313391.
[20] A. Feizollah, N. B. Anuar, R. Salleh, G. Suarez-Tangil, and S. Furnell, “AndroDialysis: Analysis of Android Intent Effectiveness in Malware Detection,” Comput.
Secur., vol. 65, pp. 121–134, Mar. 2017, doi: 10.1016/J.COSE.2016.11.007.
[21] E. M. B. Karbab, M. Debbabi, A. Derhab, and D. Mouheb, “MalDozer: Automatic framework for android malware detection using deep learning,” in
Proceedings of the 5fth Annual DFRWS Europe, Mar. 2018, vol. 24, pp. S48–S59, doi: 10.1016/J.DIIN.2018.01.007.
[22] C. Tansettanakorn, S. Thongprasit, S. Thamkongka, and V. Visoottiviseth, “ABIS: A prototype of Android Botnet Identification System,” Proc. 2016 5th ICT
Int. Student Proj. Conf. ICT-ISPC 2016, pp. 1–5, Jul. 2016, doi: 10.1109/ICT-ISPC.2016.7519221.
Securing Mobile Applications Against Mobile Malware Attacks: A Case Study (1570767839)](https://image.slidesharecdn.com/week5mobiledevicesecurity31032022-220331021615/85/WEEK5-Mobile-Device-Security-31032022-pdf-29-320.jpg)
