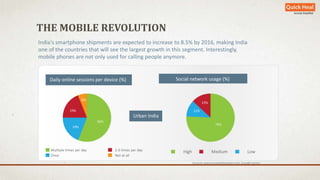
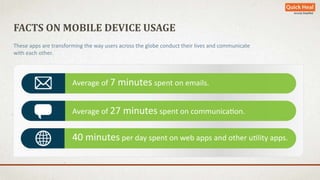
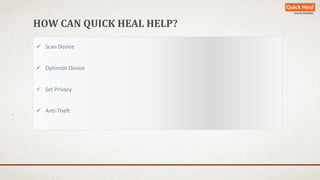
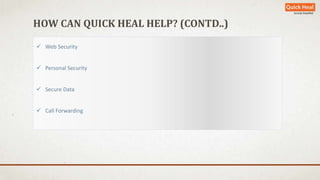
The document discusses the rapid growth of mobile device usage, particularly in India, and highlights the dominance of the Android platform with significant security risks associated with personal data accessibility. It outlines various tips for securing Android devices against malware and unauthorized access, emphasizing the importance of app permissions and secure practices. Quick Heal Technologies offers solutions for device security, optimization, and personal safety in response to the increasing threats to mobile devices.