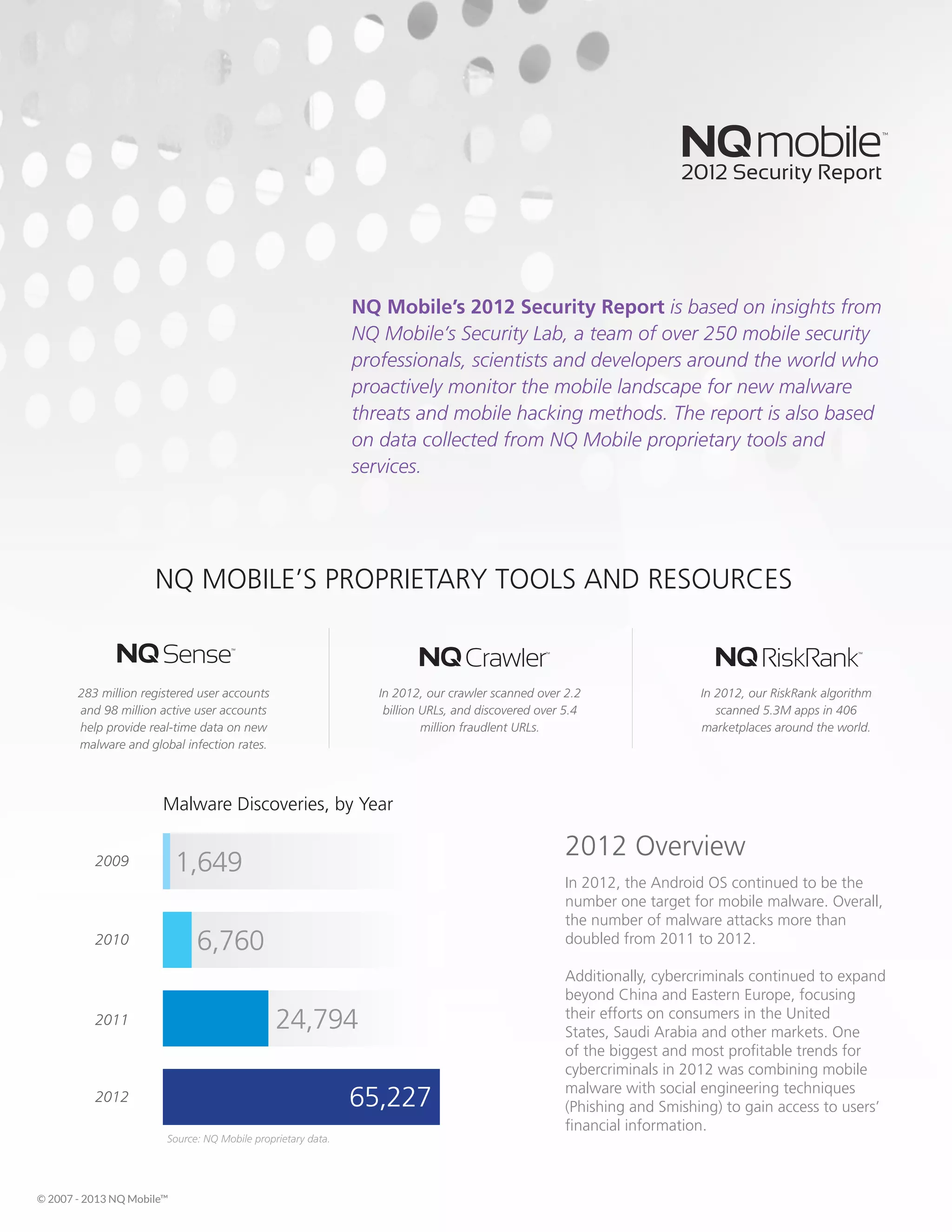
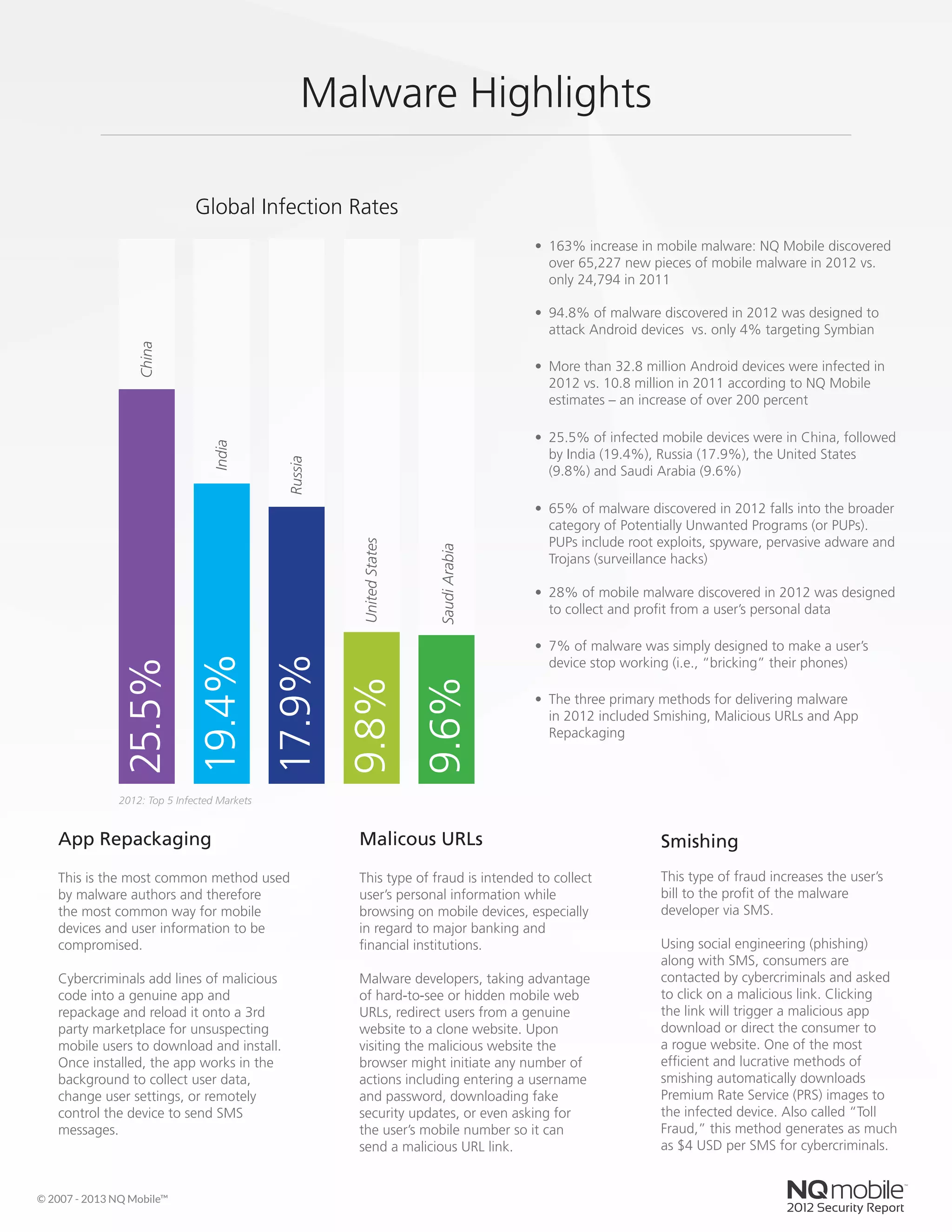
The Android operating system continued to be the primary target for mobile malware in 2012, with the number of malware attacks more than doubling from 2011. Cybercriminals expanded beyond China and Eastern Europe to target consumers in the United States, Saudi Arabia, and other markets. One of the most profitable trends for cybercriminals was combining mobile malware with social engineering techniques like phishing and smishing to steal users' financial information.