This document discusses mobile malware and how to protect against it. It begins by defining malware and listing common types. It then provides statistics on the distribution of mobile operating systems and malware detections. The document outlines sources of mobile malware infections and discusses why mobile devices contain sensitive information. It recommends implementing mobile device management to centrally manage devices and deploy security policies. Examples of recent mobile threats are also described. The document concludes by recommending security best practices like using antivirus software, updating devices, and educating users.















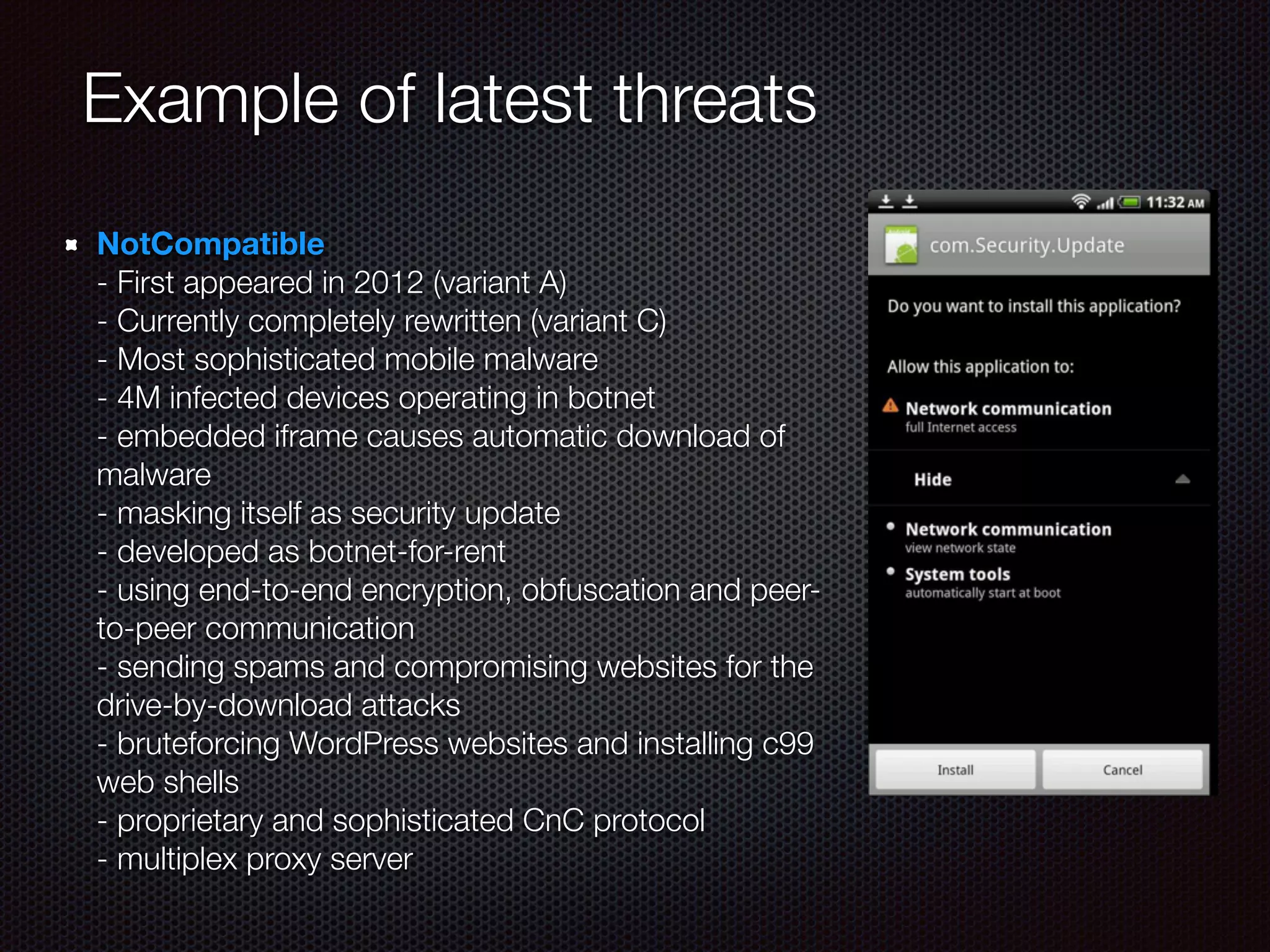
![Example of latest threats
DoubleDirect (Zimperium) - MitM attack affecting iOS and Android
devices. Spoofing ICMP Redirect message from gateway in order
to divert traffic via attackers node.
In fact for MitM is redirect of DNS IP all what you need :]
CVE-2014-7911 affecting all Androids versions except 5.0.
Attacker is able to execute arbitrary code and escalate privileges.
Other Android versions are not patched and more-likely it will not
happen.
Trojan-Banker.AndroidOS.Binv.a
Published on official Google Play store as banking application of
two well known Brazilian banks. Because in Brazil are not used
tokens or OTPs, application just showed phishing website and
capture credentials.](https://image.slidesharecdn.com/mpfqaumvqt6bt4dmg230-signature-588125ffb526b9cd8ea2e0fd4cc14d29ec5e1a0f2a599b092490c0d40c93d8ea-poli-141130072422-conversion-gate02/75/Mobile-Malware-16-2048.jpg)