Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
$4 Million Average Cost to an Organisation For a Data Breach!

$4 Million Average Cost to an Organisation For a Data Breach!
Mobile Security - 2015 Wrap-up and 2016 Predictions

Mobile Security - 2015 Wrap-up and 2016 Predictions
Phone for Enterprises Business Corporations Governments

Phone for Enterprises Business Corporations Governments
Cisco Visual Networking Index Graphic--By the Numbers

Cisco Visual Networking Index Graphic--By the Numbers
Viewers also liked
Viewers also liked (7)
Economic Sanctions - The New Compliance Minefield - J. Boscariol

Economic Sanctions - The New Compliance Minefield - J. Boscariol
รู้ค่าเงินตราต่างประเทศอย่างง่ายดายถ้ามี Currencies master

รู้ค่าเงินตราต่างประเทศอย่างง่ายดายถ้ามี Currencies master
Similar to Surfing Safe on the Road
Similar to Surfing Safe on the Road (20)
50 Incredible Wi-Fi Tech Statistics That Businesses Must Know

50 Incredible Wi-Fi Tech Statistics That Businesses Must Know
FIDO Webinar – A New Model for Online Authentication: Implications for Policy...

FIDO Webinar – A New Model for Online Authentication: Implications for Policy...
Three Principals for Simple, Secure Content Sharing

Three Principals for Simple, Secure Content Sharing
Mobile security mobile malware countermeasure academic csirt

Mobile security mobile malware countermeasure academic csirt
I.G.N. Mantra - Mobile Security, Mobile Malware,and Countermeasure

I.G.N. Mantra - Mobile Security, Mobile Malware,and Countermeasure
InfraGard Albany Member Alliance Monthly Security Tips

InfraGard Albany Member Alliance Monthly Security Tips
IRJET- An Implementation and Efficient Way to Improve Women Safety Empowe...

IRJET- An Implementation and Efficient Way to Improve Women Safety Empowe...
More from F-Secure Corporation
More from F-Secure Corporation (20)
The Real Costs of SIEM vs. Managed Security Service

The Real Costs of SIEM vs. Managed Security Service
Security A to Z: Glossary of the most important terms

Security A to Z: Glossary of the most important terms
Les attaques menées depuis la France dans le cyber espace 

Les attaques menées depuis la France dans le cyber espace
Les attaques menées depuis la France dans le cyber espace

Les attaques menées depuis la France dans le cyber espace
Cyber security webinar 6 - How to build systems that resist attacks?

Cyber security webinar 6 - How to build systems that resist attacks?
Defending Workstations - Cyber security webinar part 2

Defending Workstations - Cyber security webinar part 2
F secure Radar vulnerability scanning and management

F secure Radar vulnerability scanning and management
F-Secure Policy Manager - onsite security management with superior control

F-Secure Policy Manager - onsite security management with superior control
Six things to take into account when choosing cloud solutions

Six things to take into account when choosing cloud solutions
Small and midsize business security is big business

Small and midsize business security is big business
Why should you care about government surveillance?

Why should you care about government surveillance?
Surfing Safe on the Road
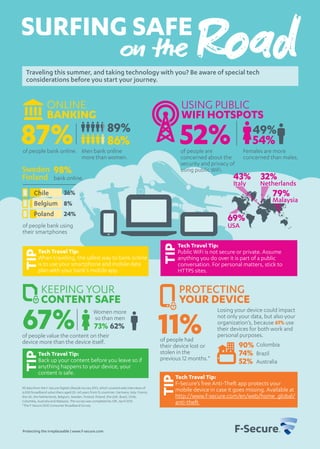
- 1. KEEPING YOUR CONTENT SAFE 43% 32% 69% 62%73% 90% 74% 52% 79% 87% 86% 89% TIP Protecting the irreplaceable | www.f-secure.com Traveling this summer, and taking technology with you? Be aware of special tech considerations before you start your journey. on the RoadSURFING SAFE PROTECTING YOUR DEVICE Tech Travel Tip: Public WiFi is not secure or private. Assume anything you do over it is part of a public conversation. For personal matters, stick to HTTPS sites. TIP Tech Travel Tip: F-Secure’s free Anti-Theft app protects your mobile device in case it goes missing. Available at http://www.f-secure.com/en/web/home_global/ anti-theft TIP Italy Netherlands USING PUBLIC WIFI HOTSPOTS 52% 49% 54% of people are concerned about the security and privacy of using public WiFi. Females are more concerned than males. 67%of people value the content on their device more than the device itself. All data from the F-Secure Digital Lifestyle Survey 2013, which covered web interviews of 6,000 broadband subscribers aged 20–60 years from 15 countries: Germany, Italy, France, the UK, the Netherlands, Belgium, Sweden, Finland, Poland, the USA, Brazil, Chile, Colombia, Australia and Malaysia. The survey was completed by GfK, April 2013. *The F-Secure 2012 Consumer Broadband Survey 11%of people had their device lost or stolen in the previous 12 months.* Colombia Losing your device could impact not only your data, but also your organization’s, because 61% use their devices for both work and personal purposes. Brazil Australia Women more so than men USA Malaysia 98%Sweden Finland 36% 8% 24% of people bank online. bank online. of people bank using their smartphones ONLINE BANKING Men bank online more than women. Tech Travel Tip: When traveling, the safest way to bank online is to use your smartphone and mobile data plan with your bank’s mobile app. TIP Tech Travel Tip: Back up your content before you leave so if anything happens to your device, your content is safe. Chile Belgium Poland
