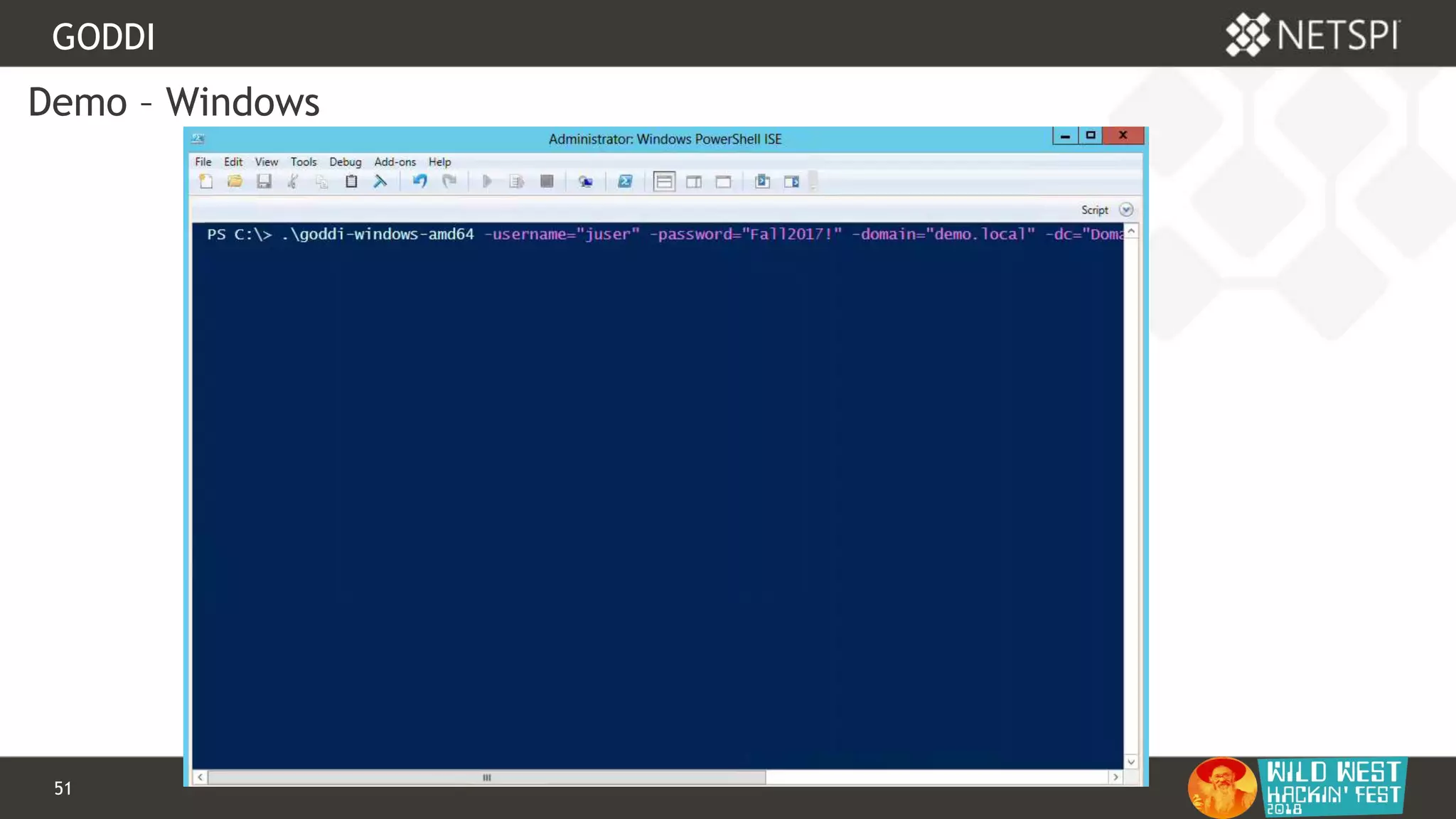
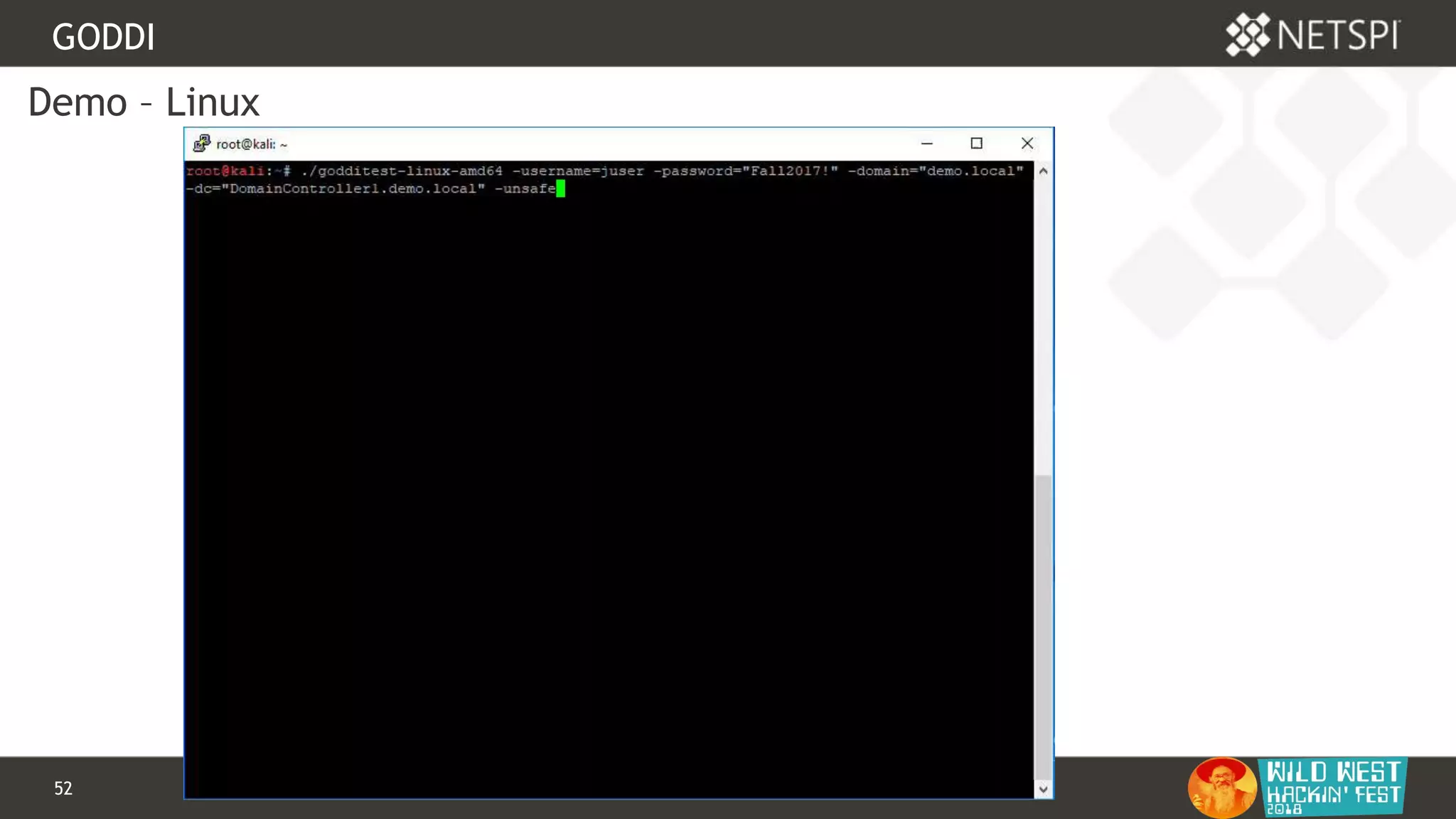
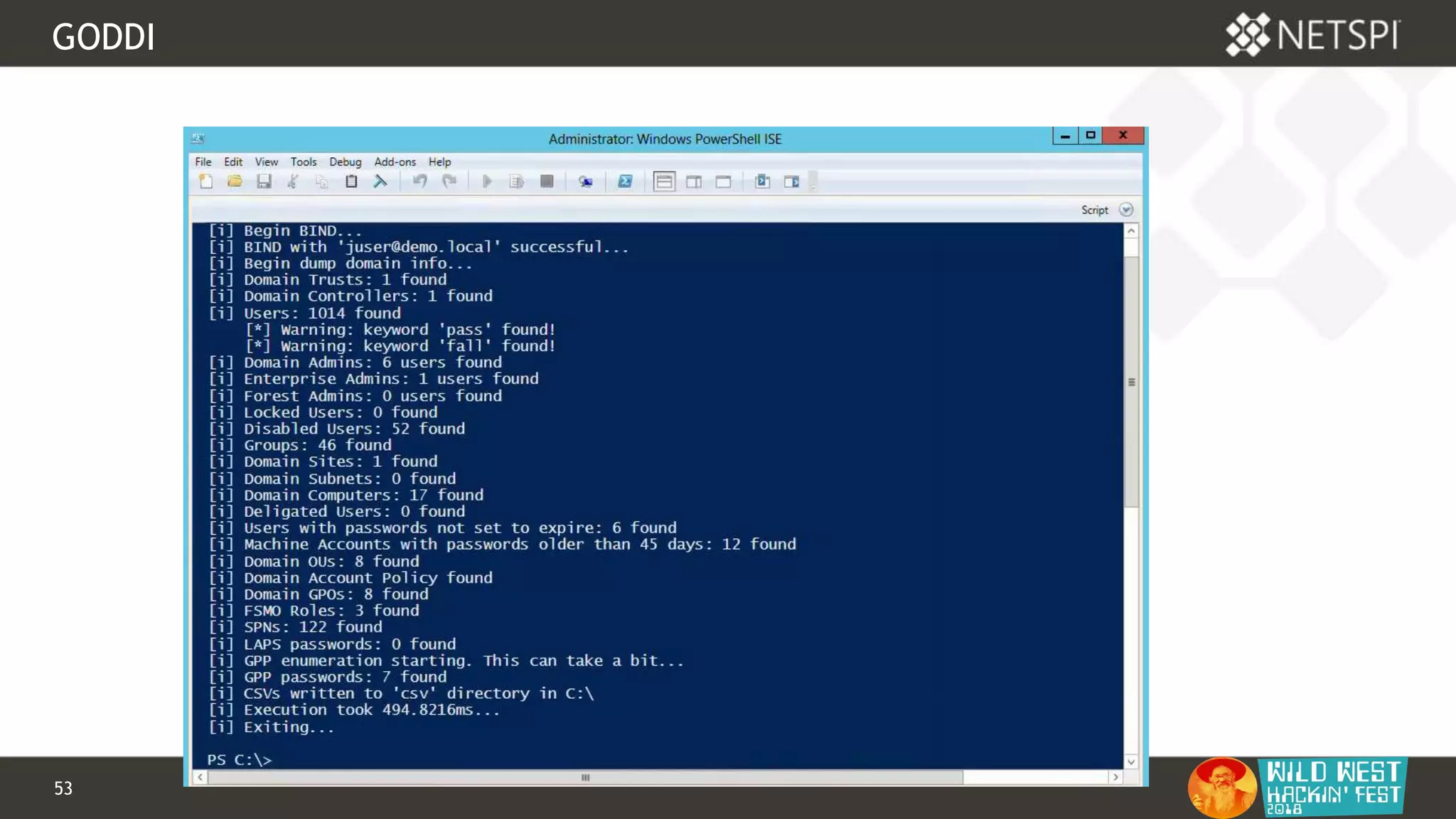
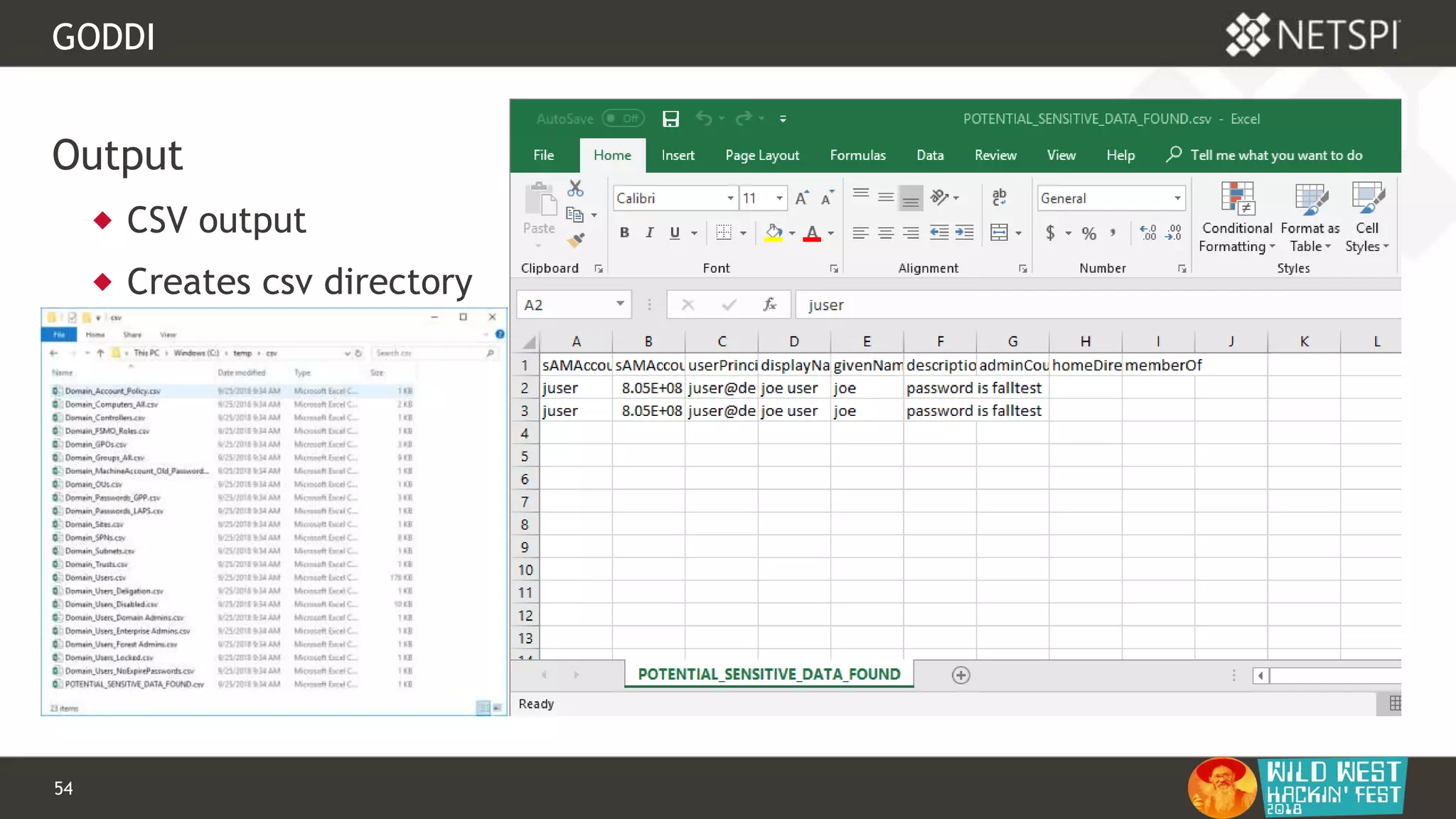
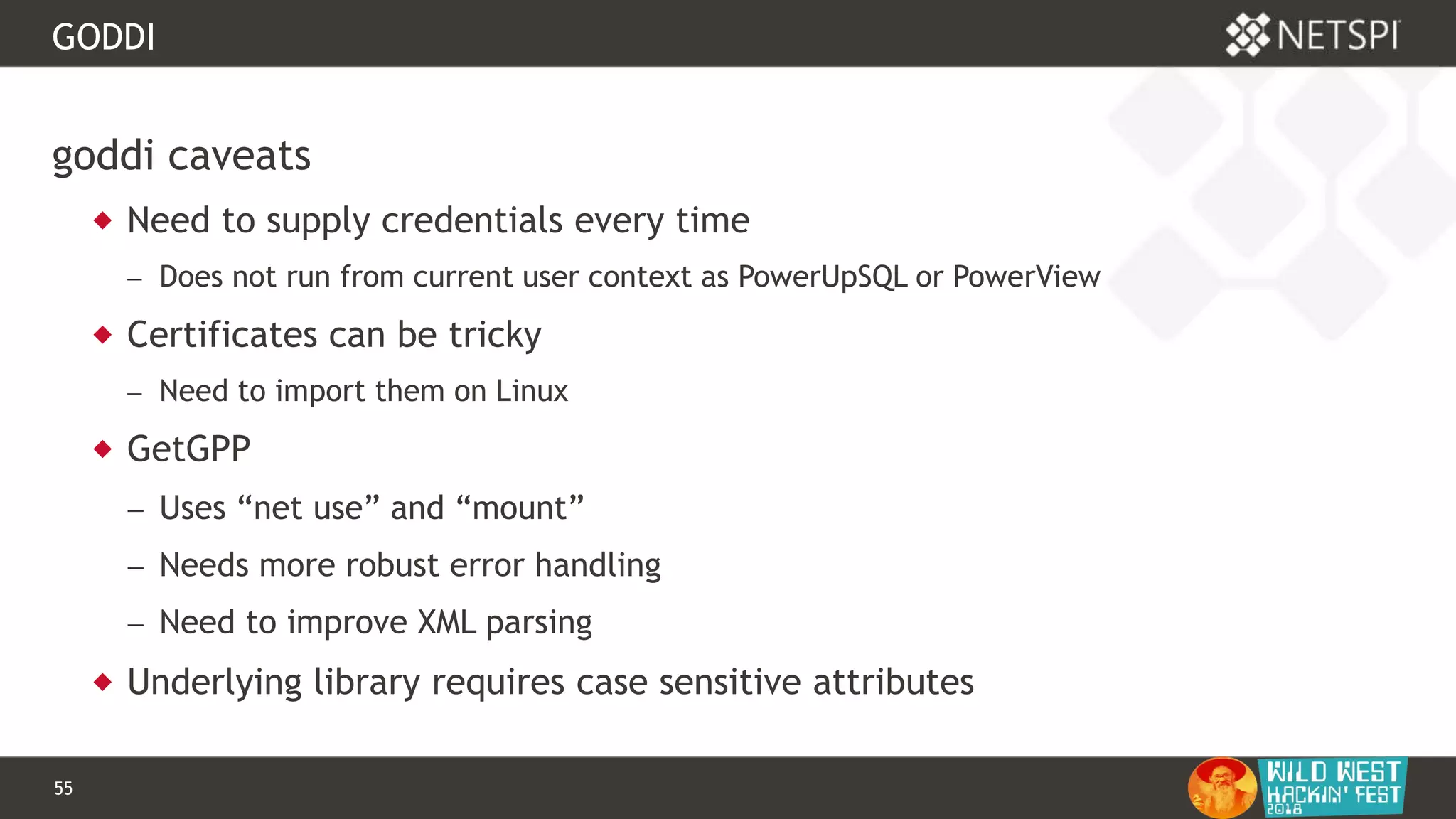
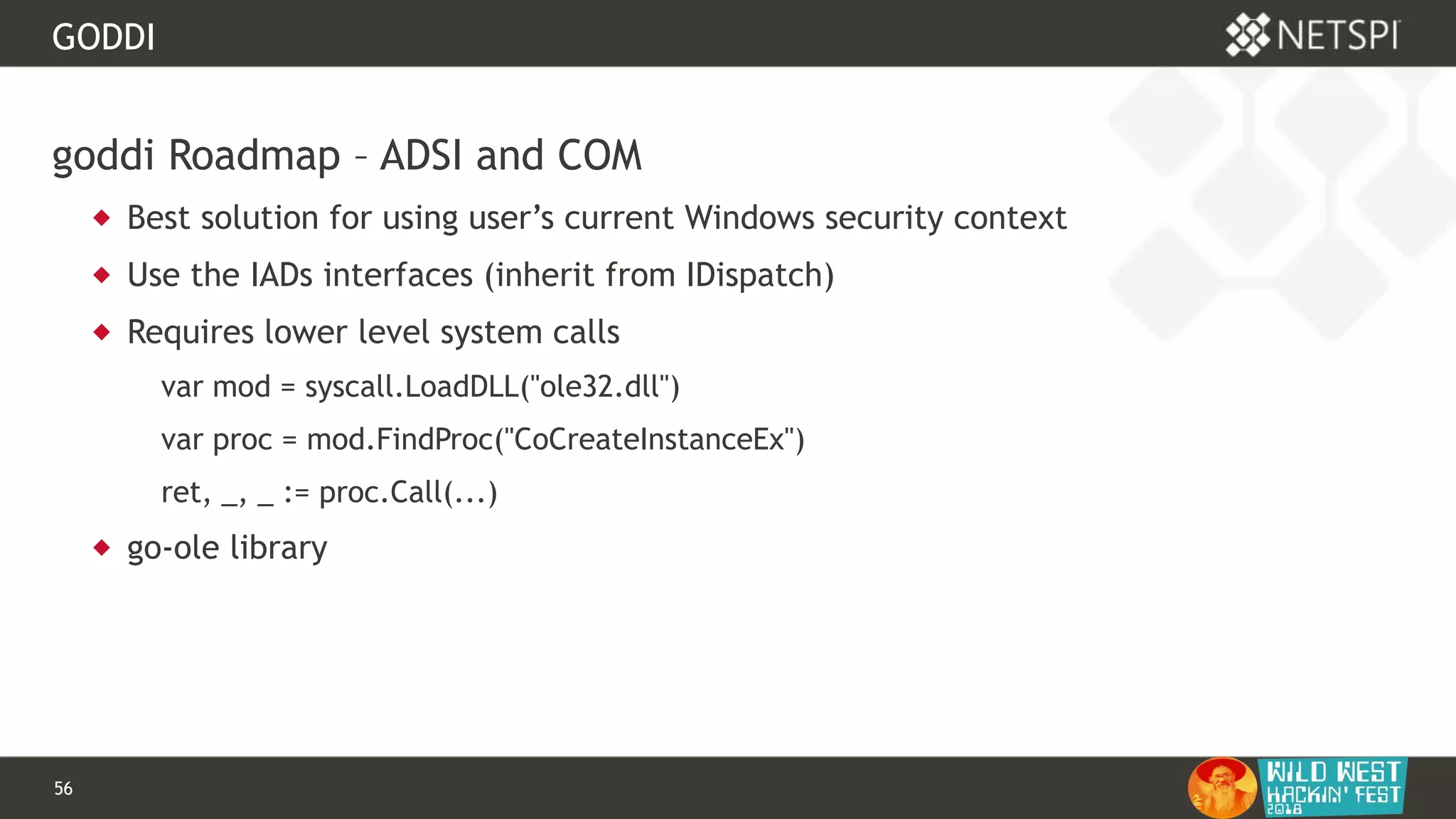
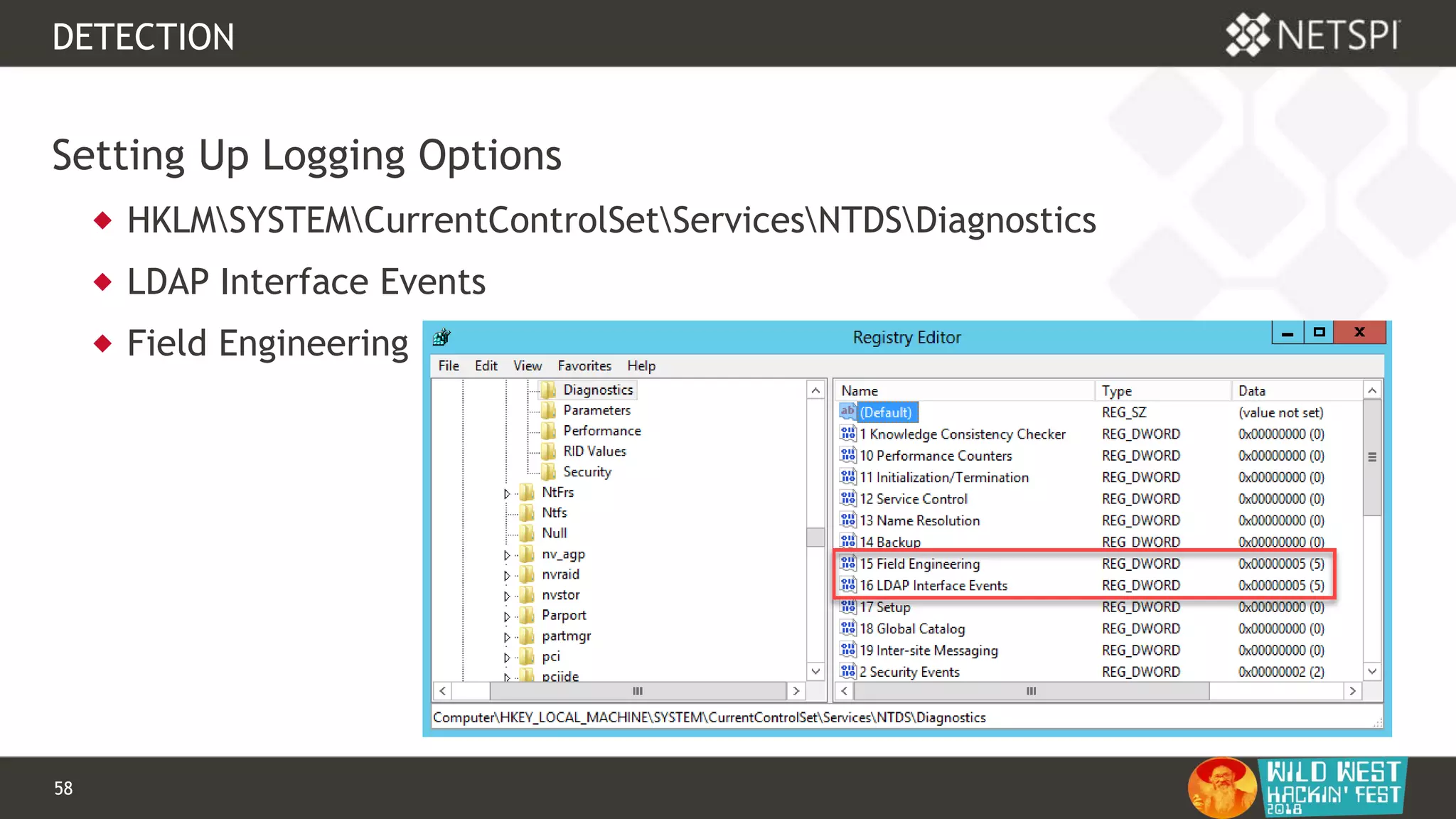
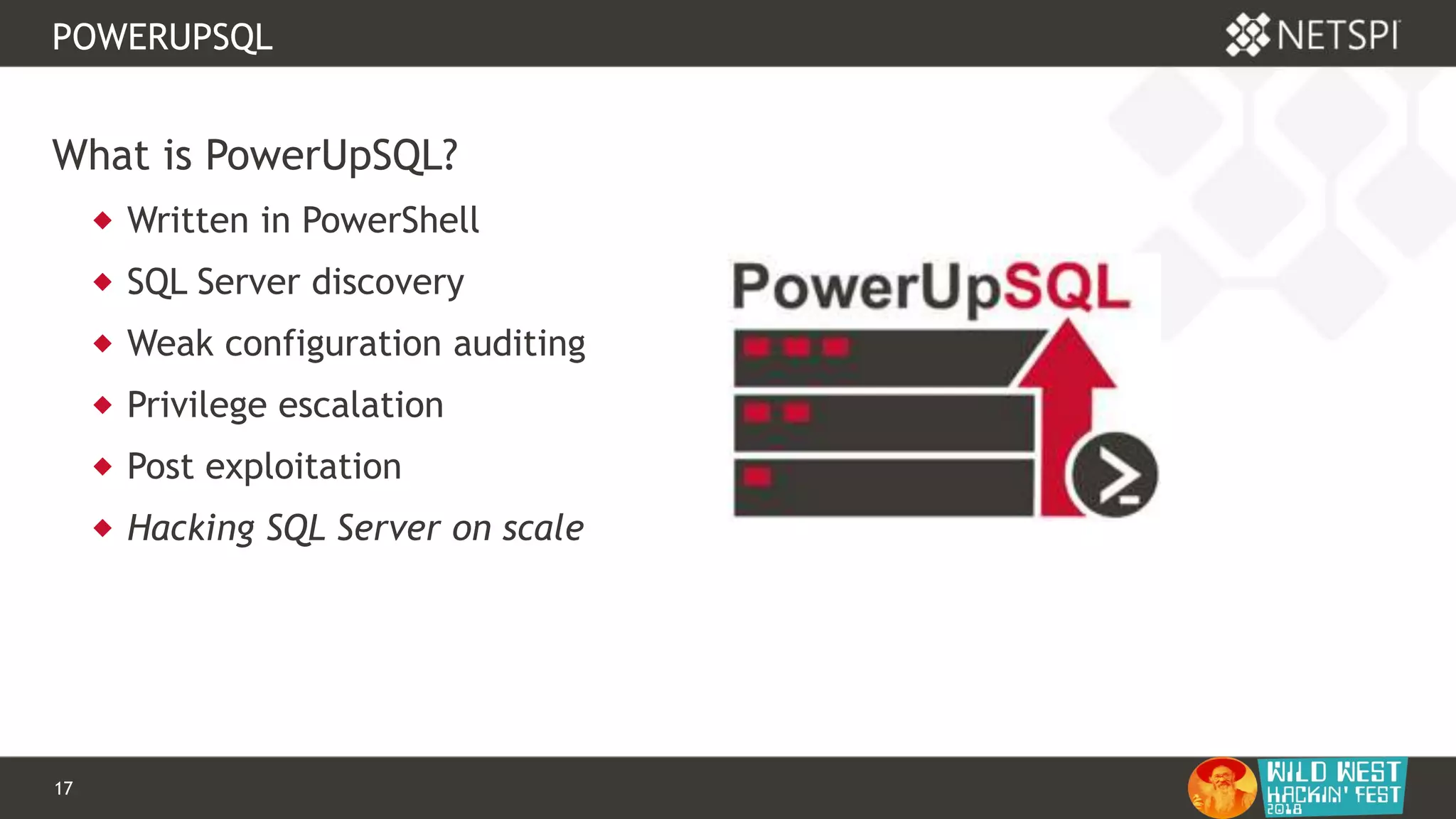
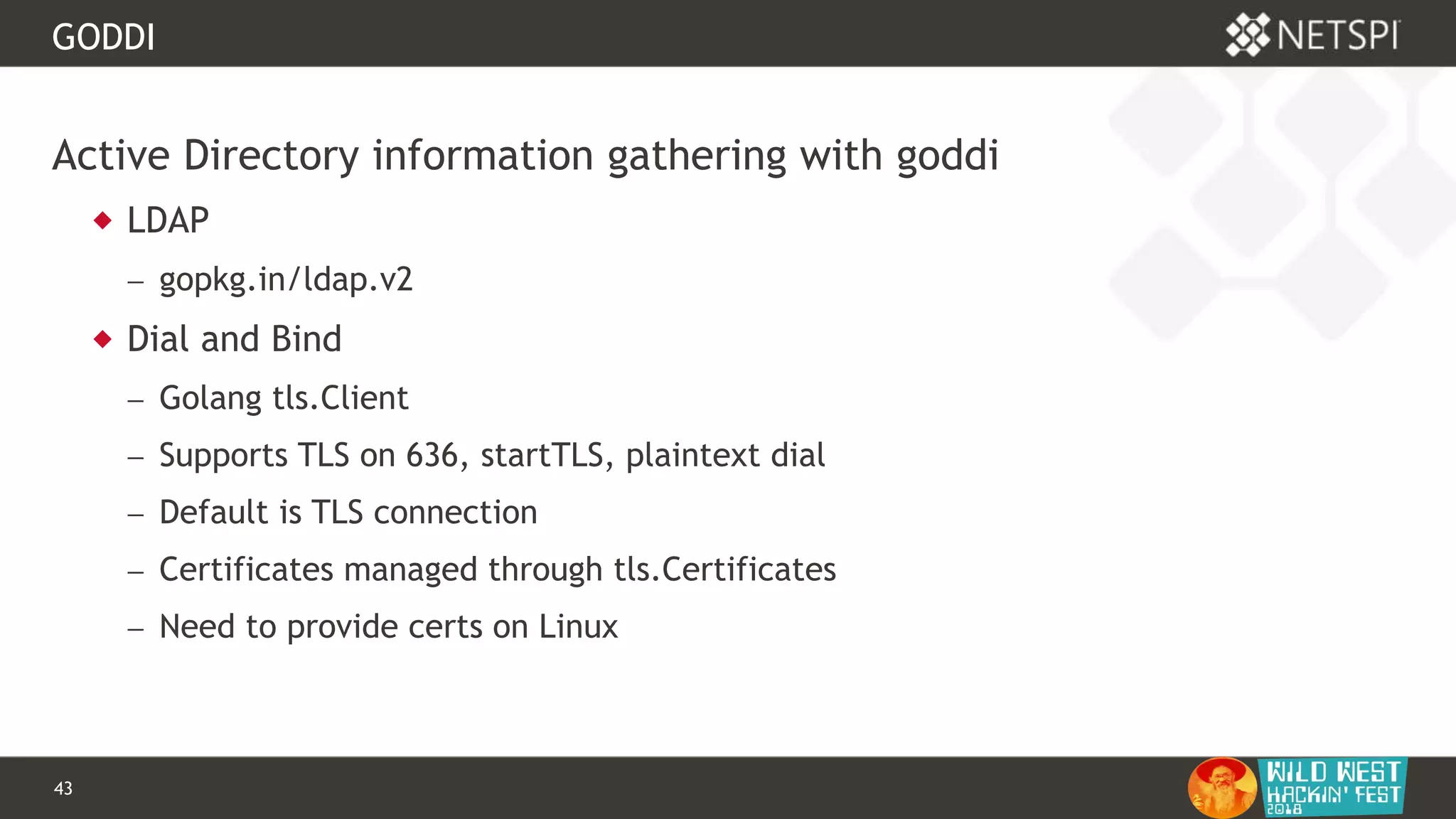
This document discusses tools for Active Directory information gathering called PowerUpSQL and goddi. PowerUpSQL uses SQL Server and the OLE DB provider to query Active Directory via LDAP, while goddi uses Go and the LDAP library to directly query Active Directory. The document provides overviews of both tools, including how to install them, the methodology behind how they gather information, and demos of them in use. It also discusses some of the limitations and optimizations of each tool.







![20 Confidential & Proprietary
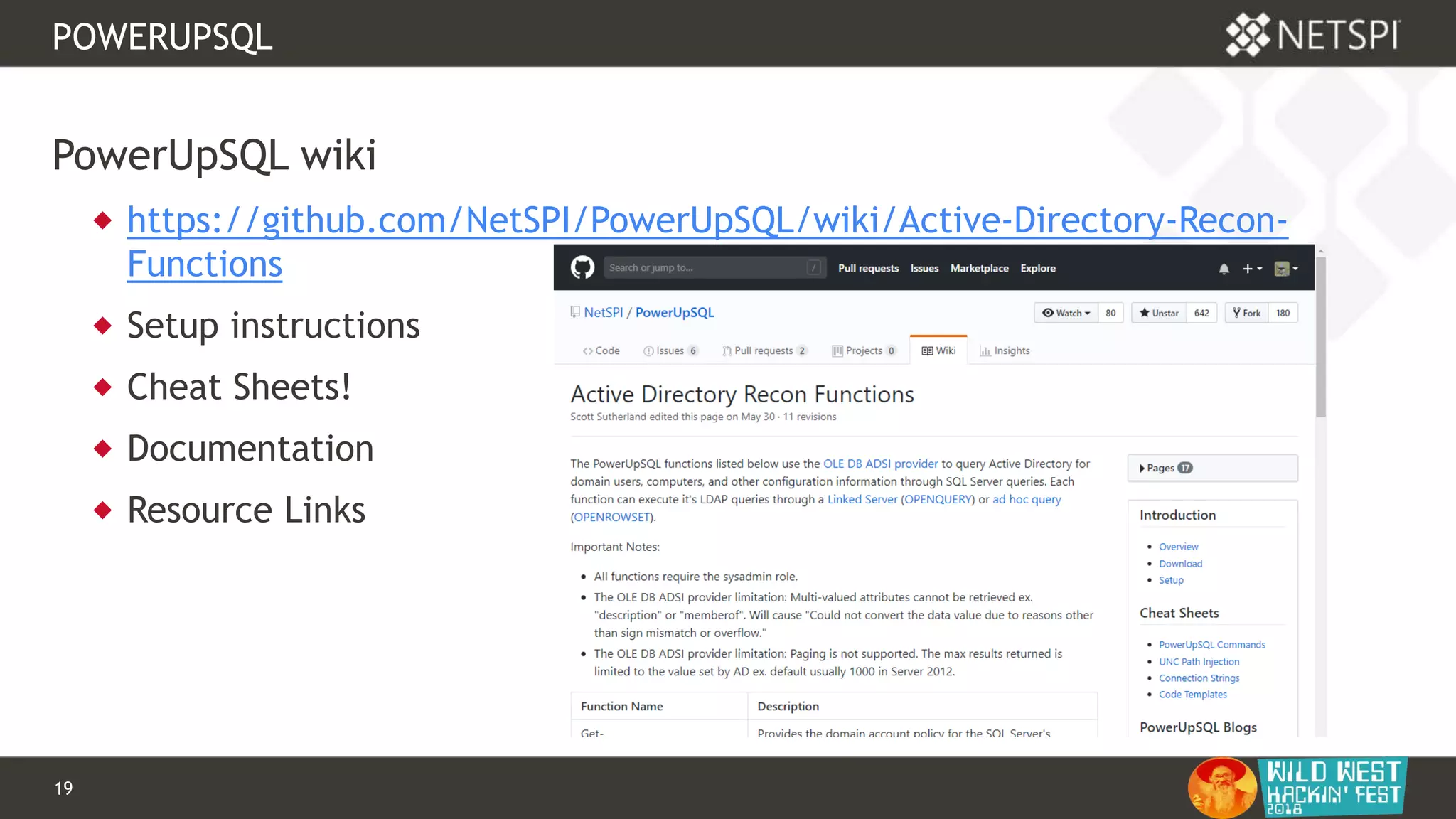
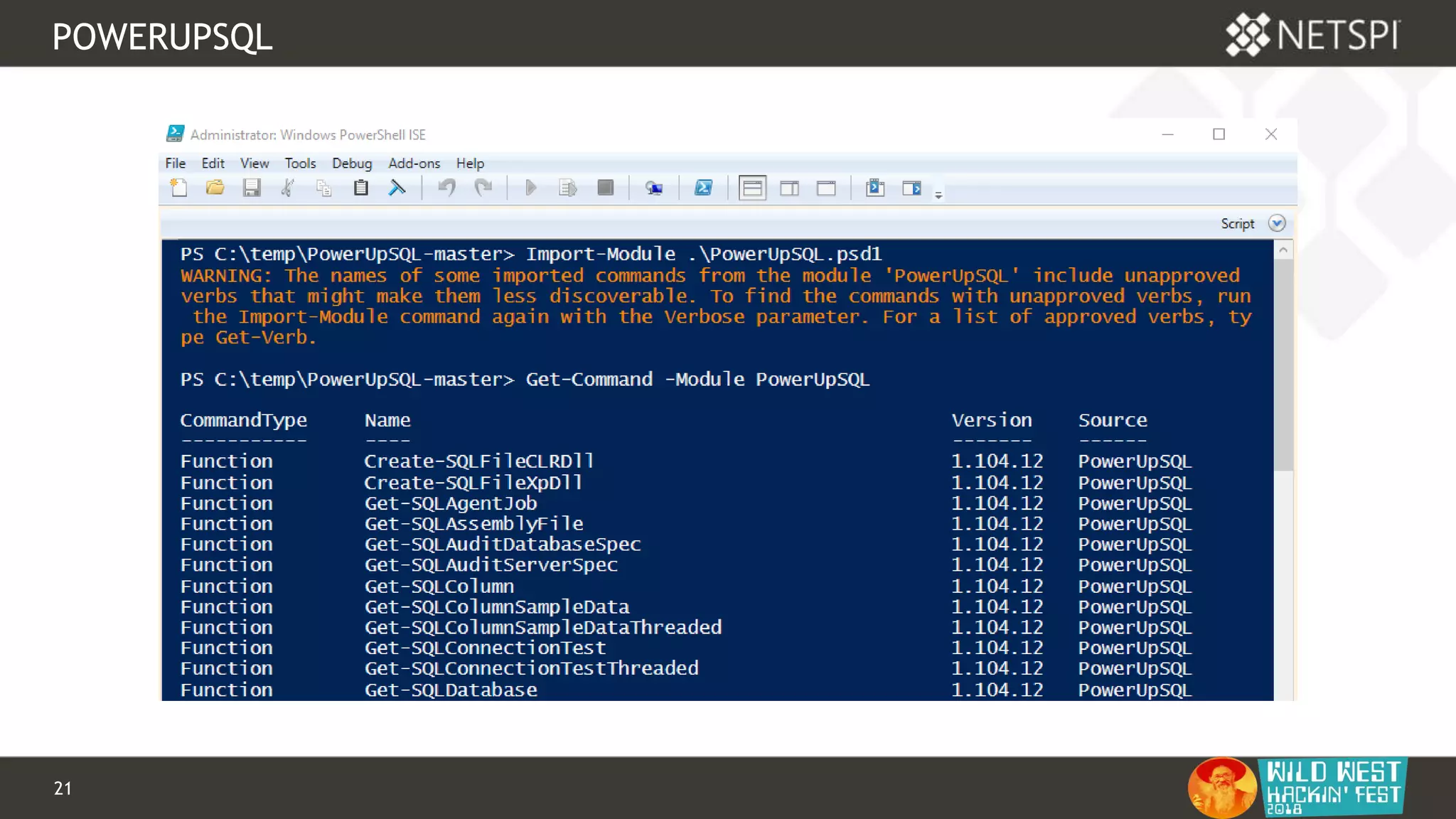
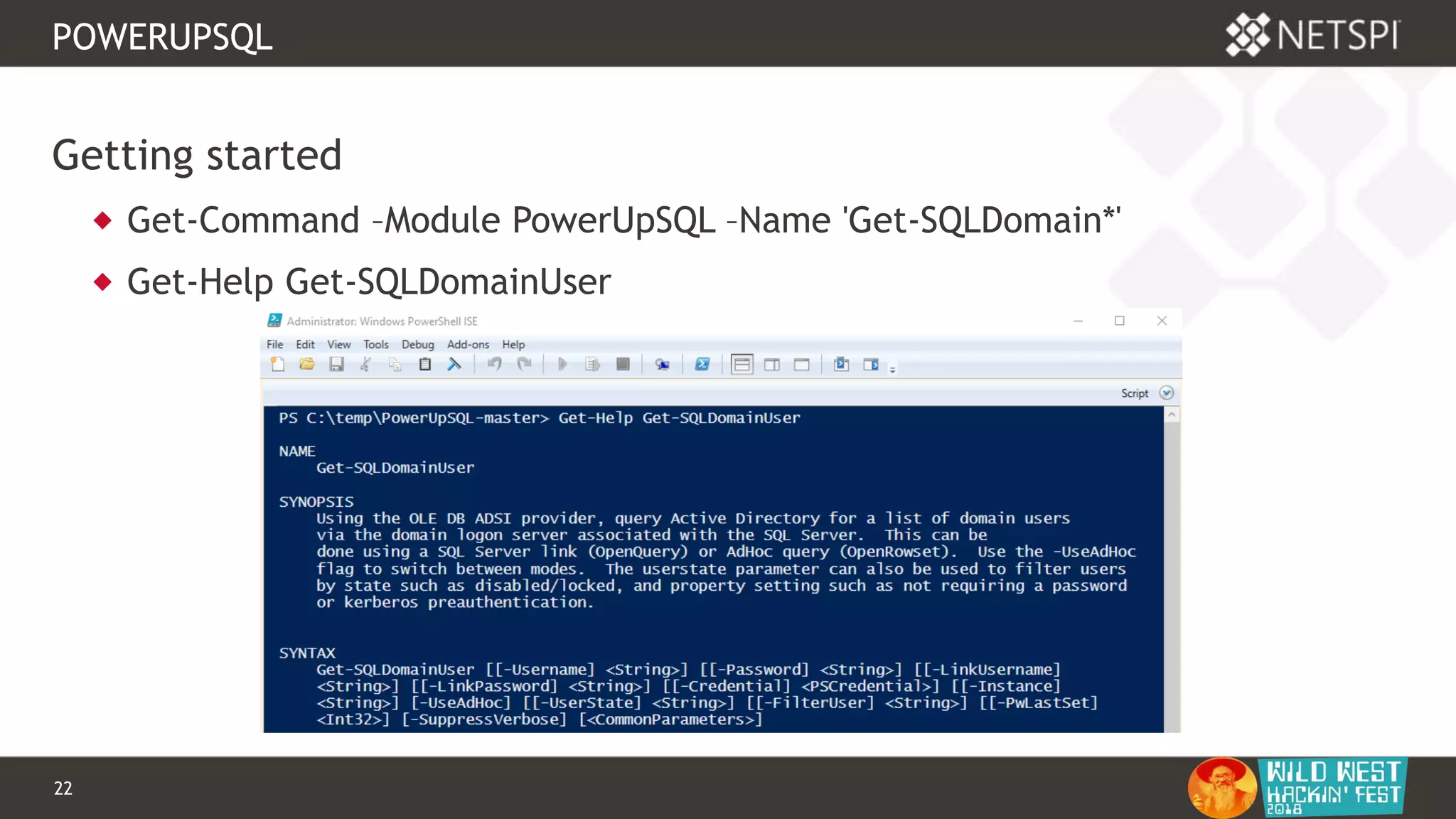
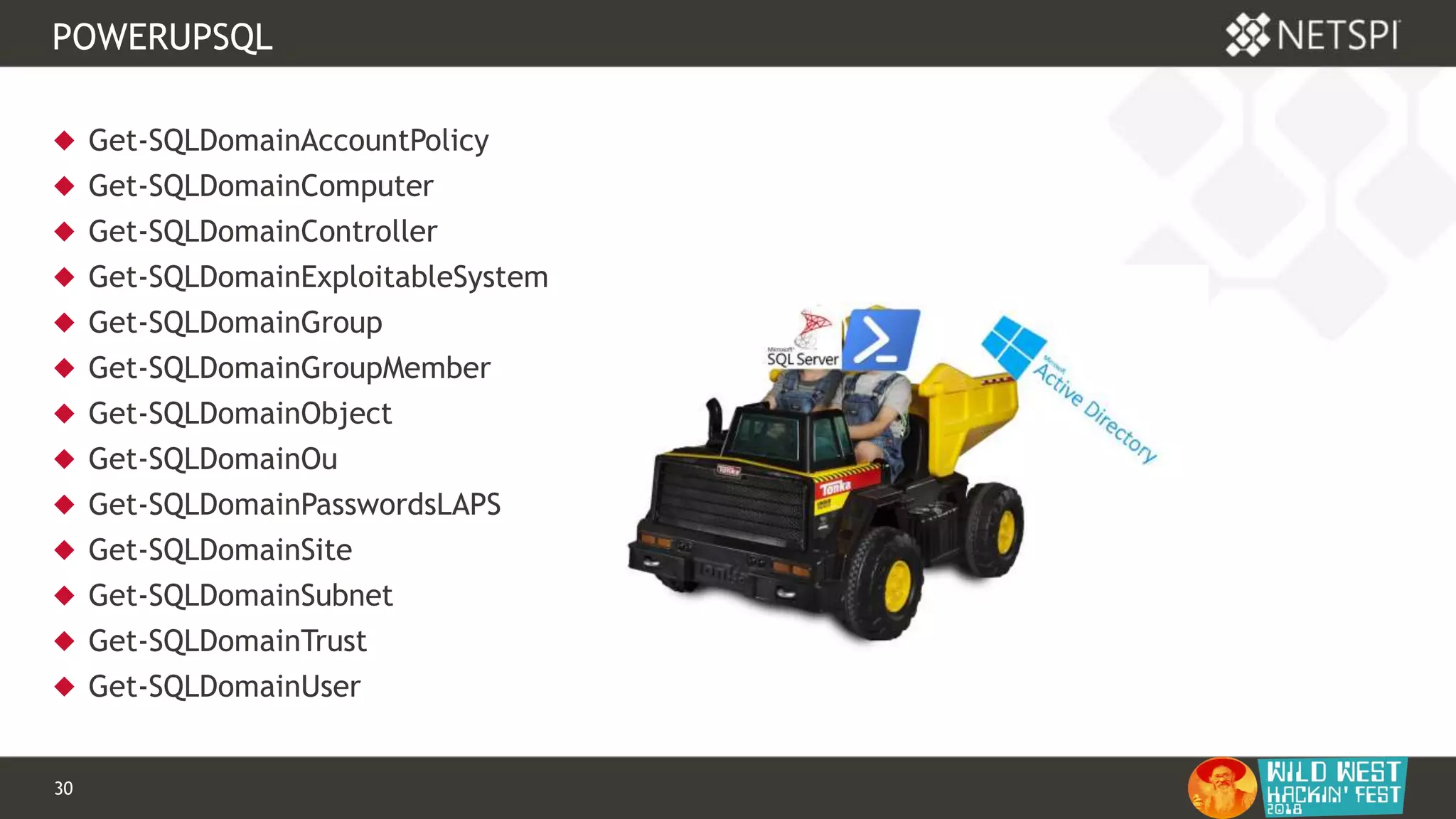
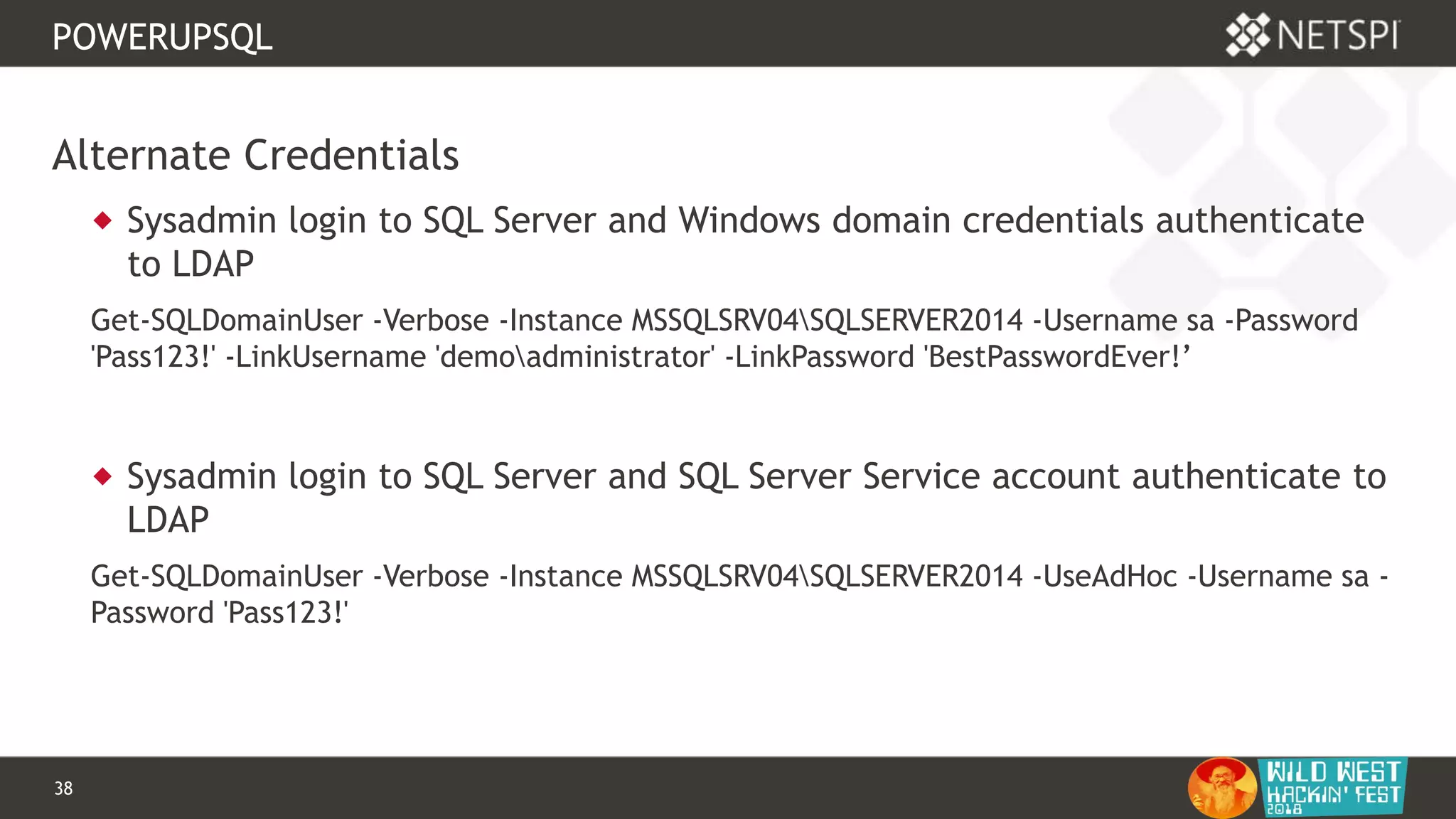
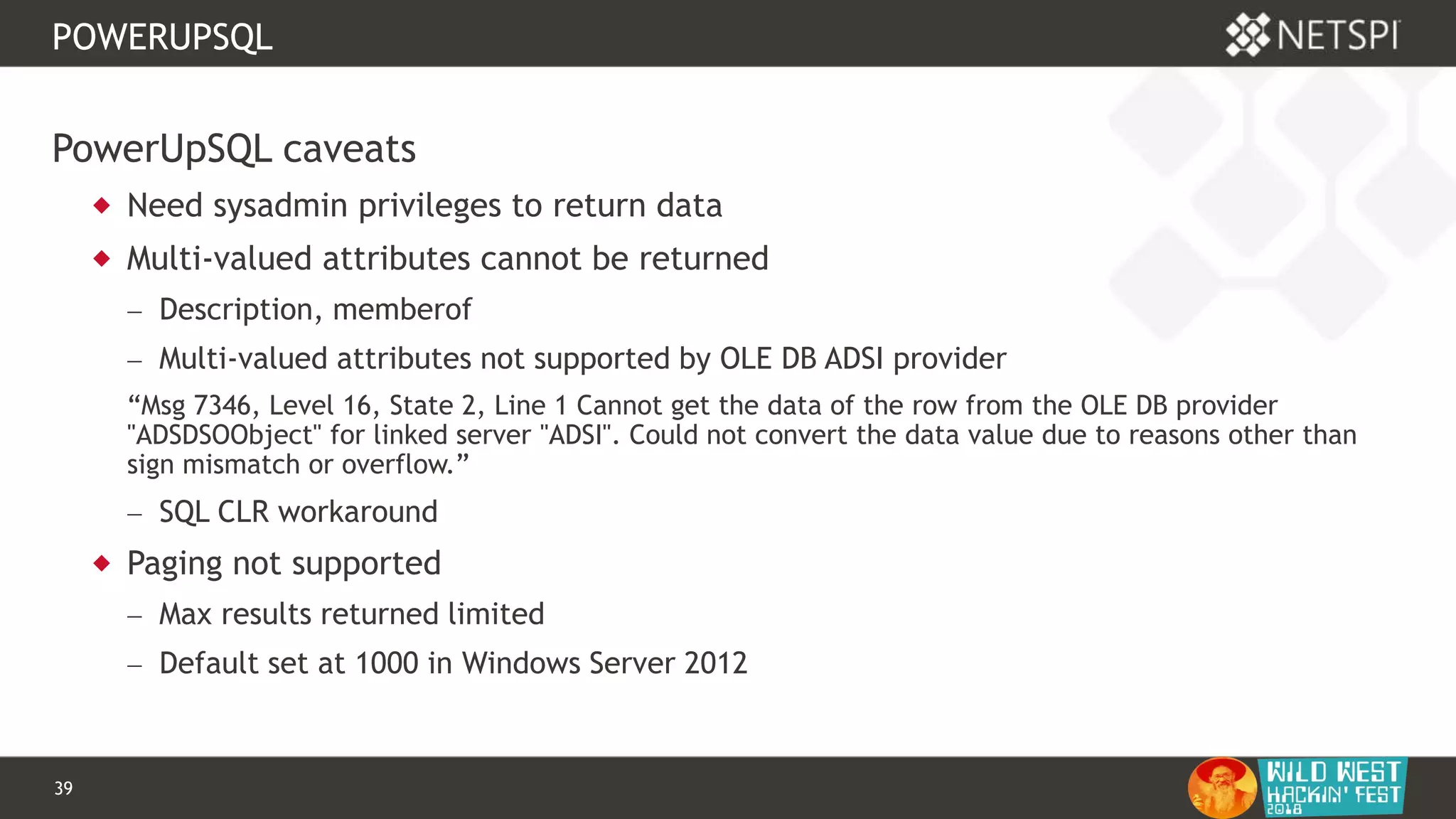
POWERUPSQL
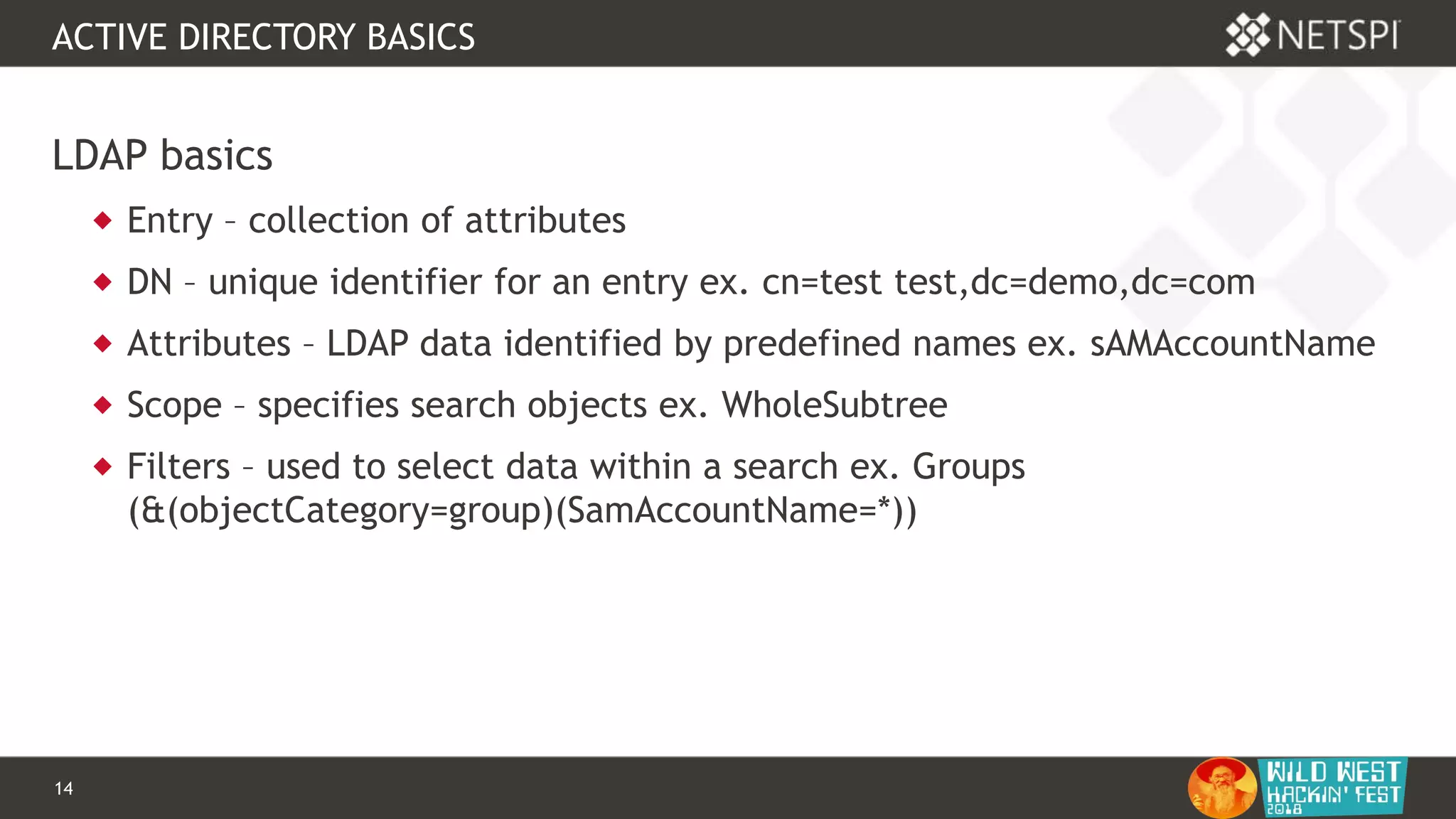
PowerUpSQL setup
Import-Module PowerUpSQL.psd1
Install-Module -Name PowerUpSQL
IEX(New-Object
System.Net.WebClient).DownloadString("https://raw.githubusercontent.com
/NetSPI/PowerUpSQL/master/PowerUpSQL.ps1")
&([scriptblock]::Create((new-object
net.webclient).downloadstring("https://raw.githubusercontent.com/NetSPI/
PowerUpSQL/master/PowerUpSQL.ps1")))](https://image.slidesharecdn.com/wwhf-181027003858/75/WWHF-2018-Using-PowerUpSQL-and-goddi-for-Active-Directory-Information-Gathering-20-2048.jpg)

![28 Confidential & Proprietary
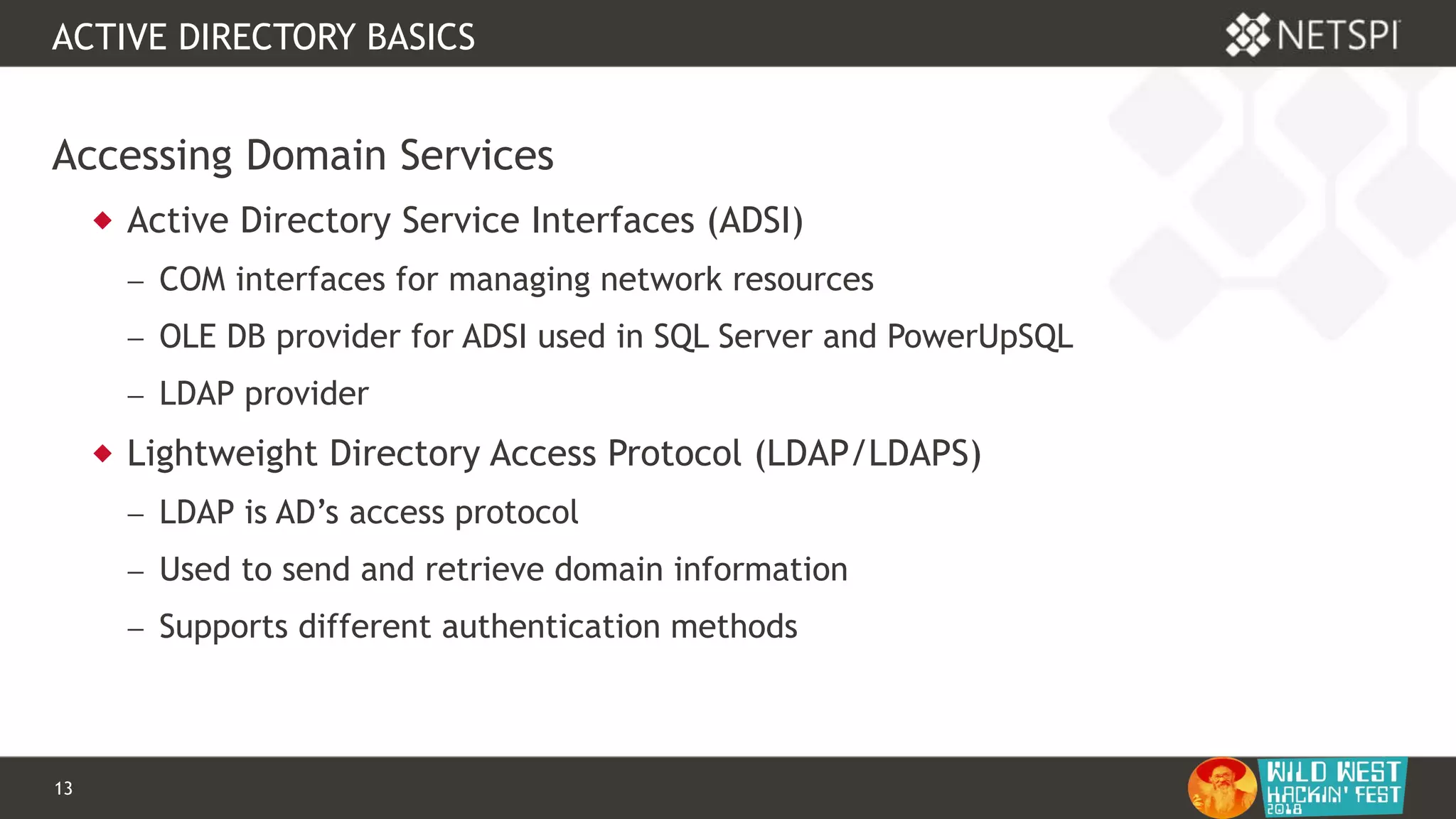
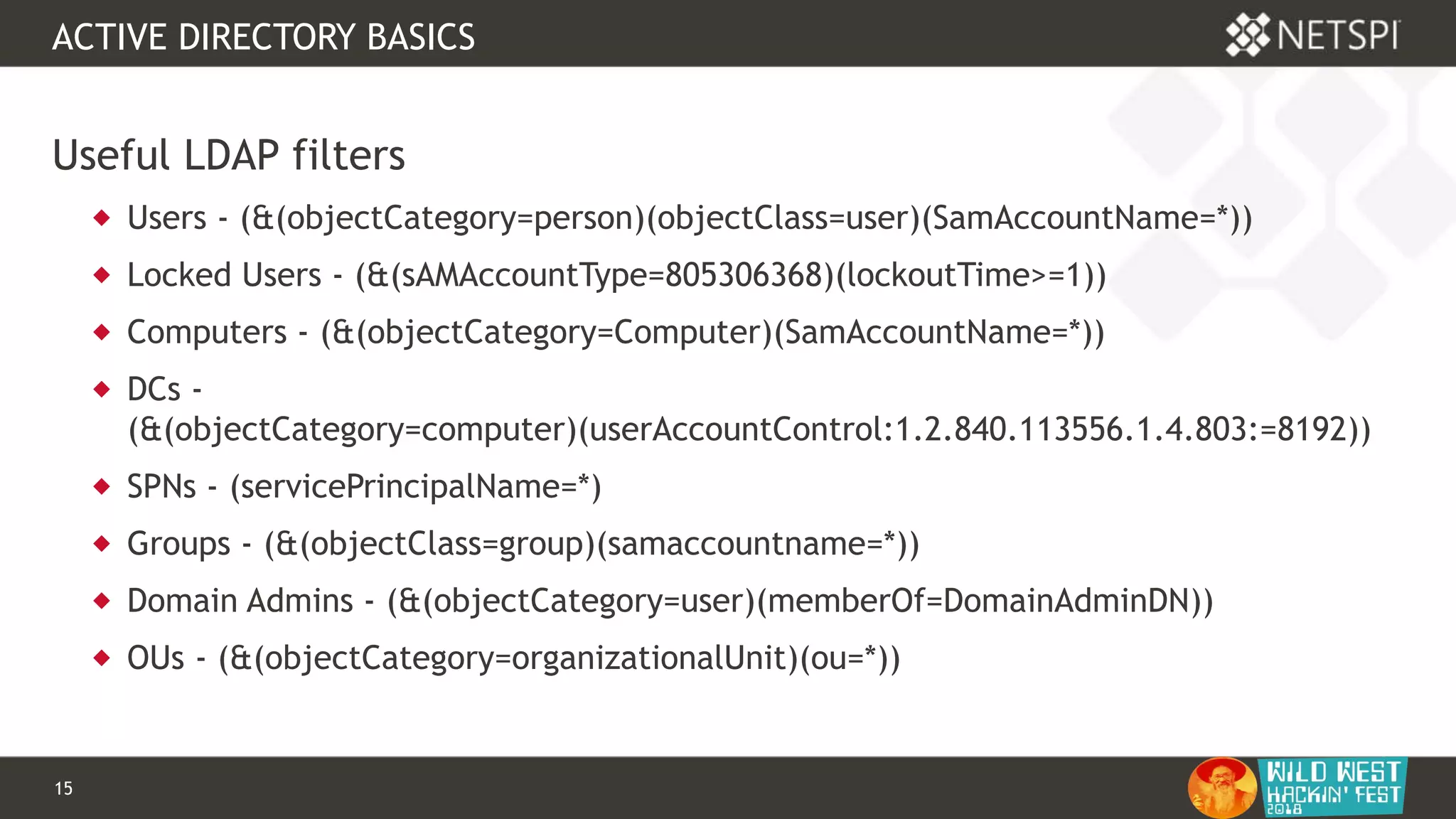
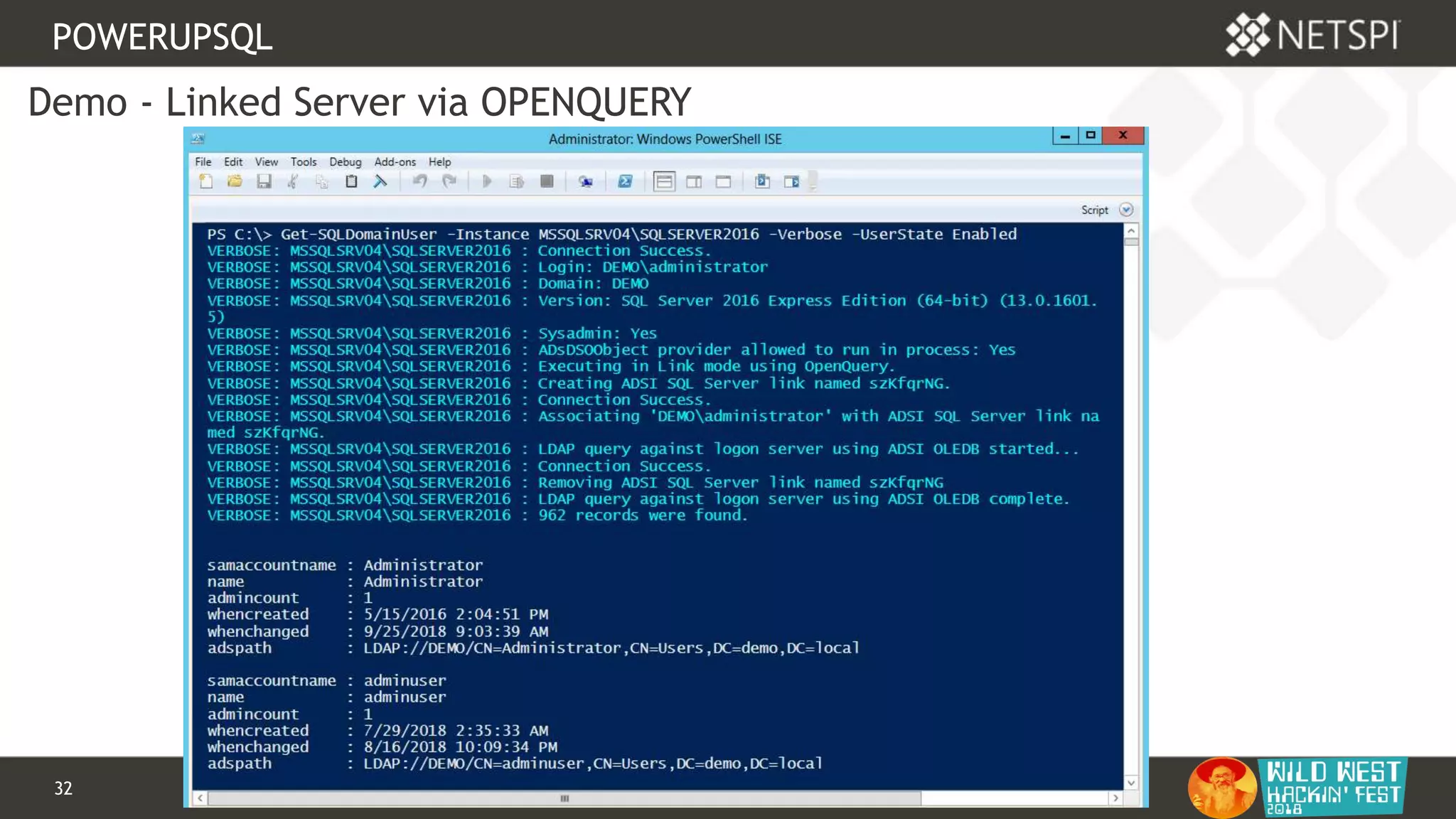
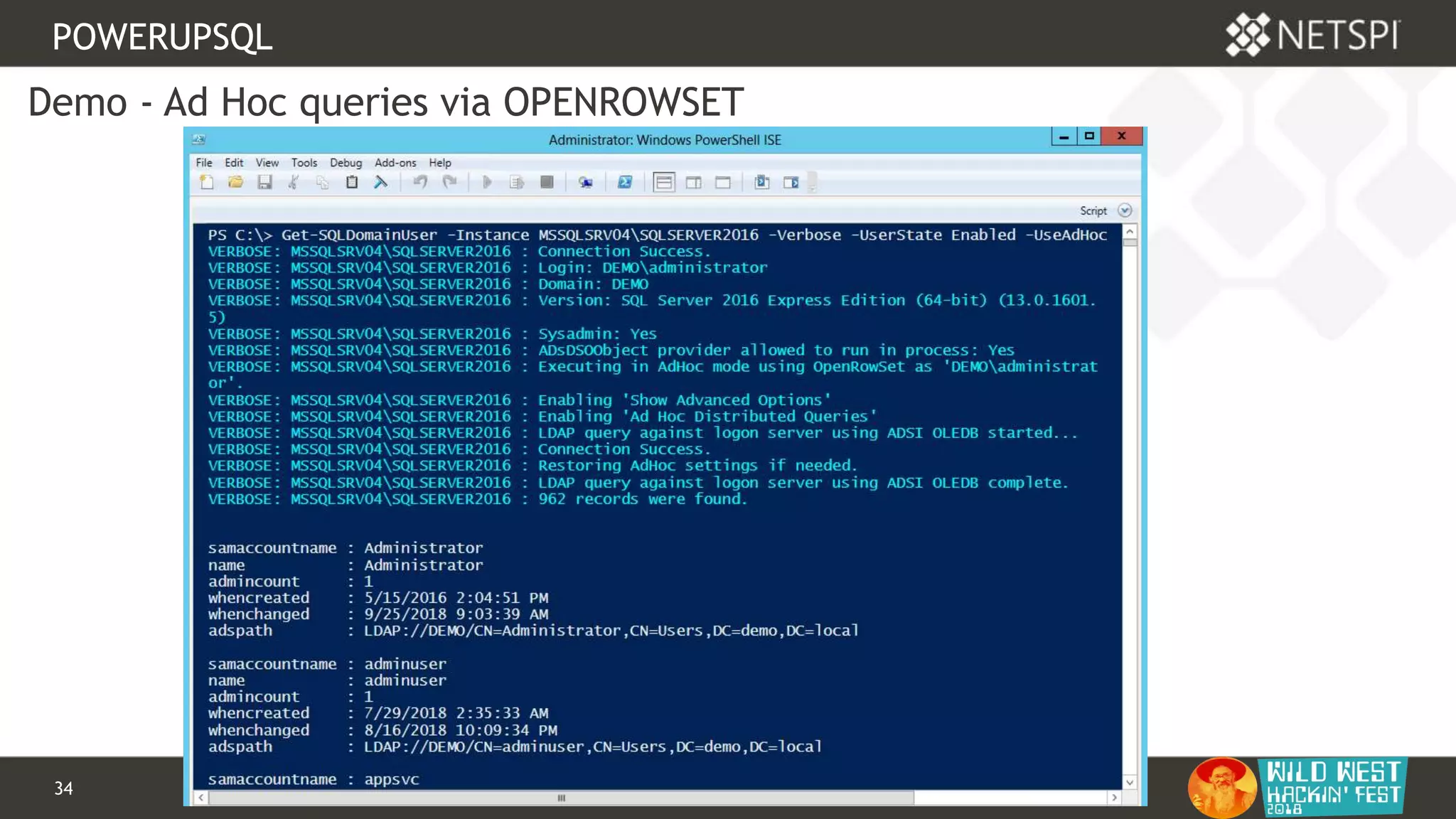
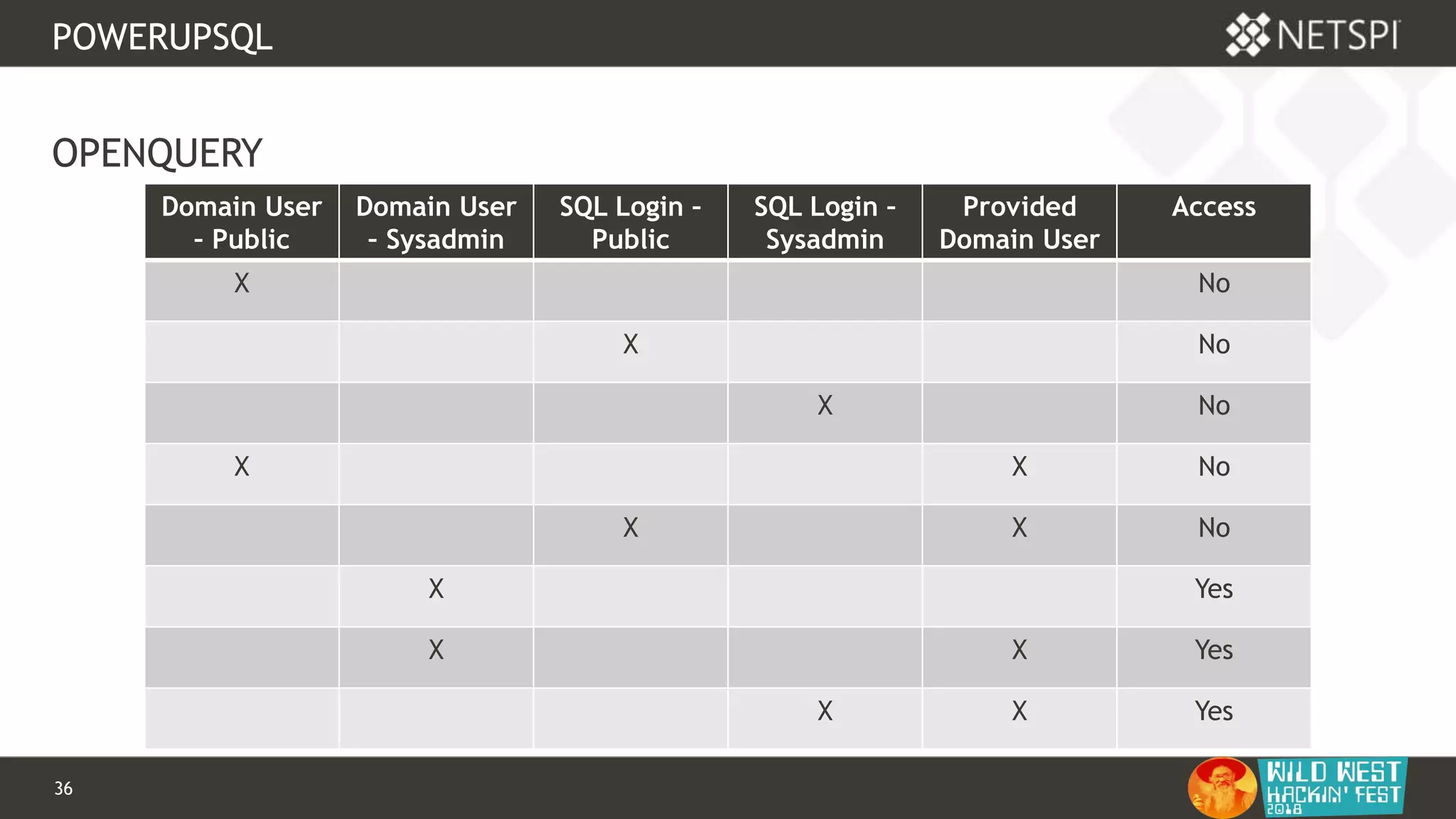
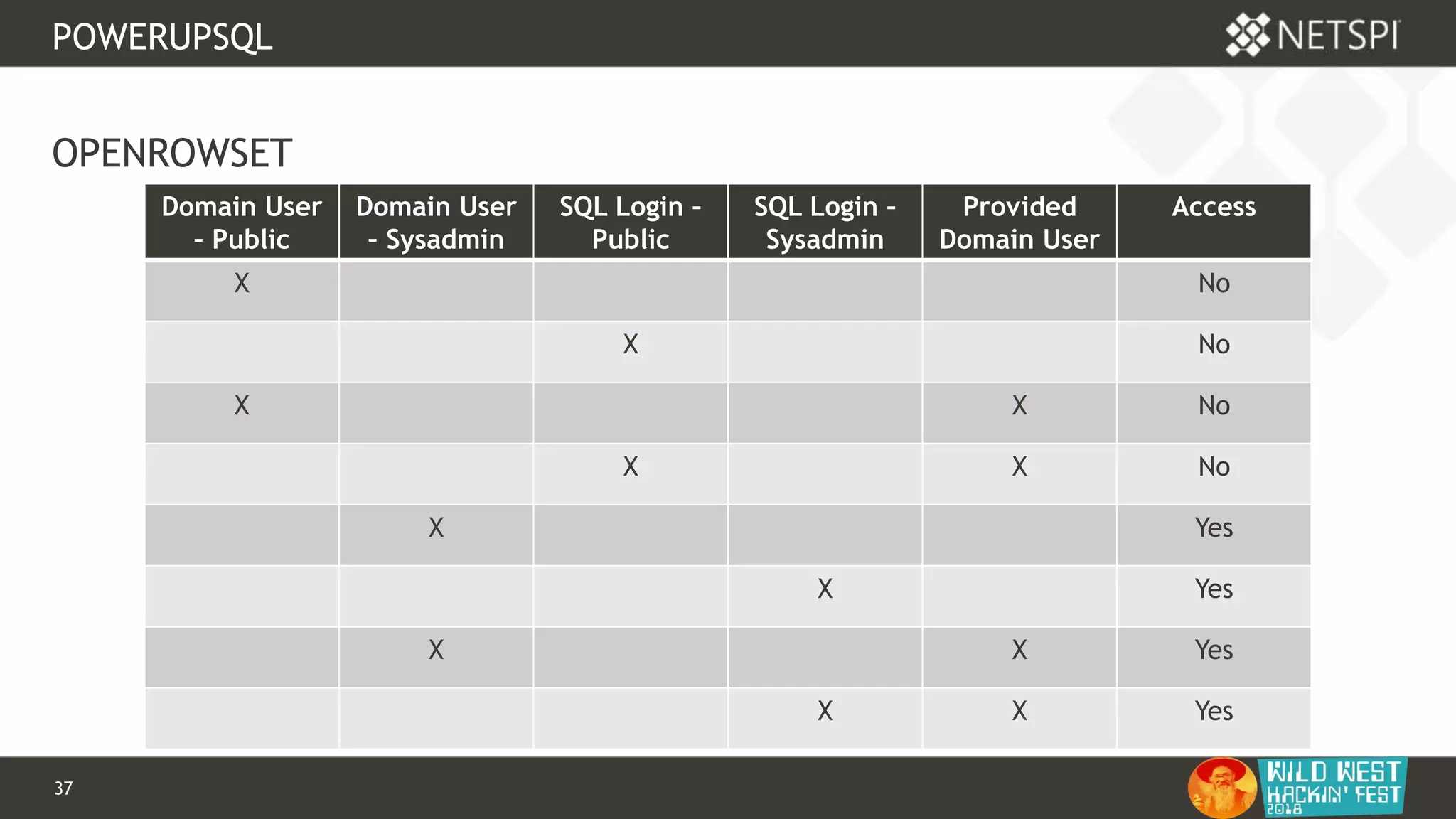
POWERUPSQL
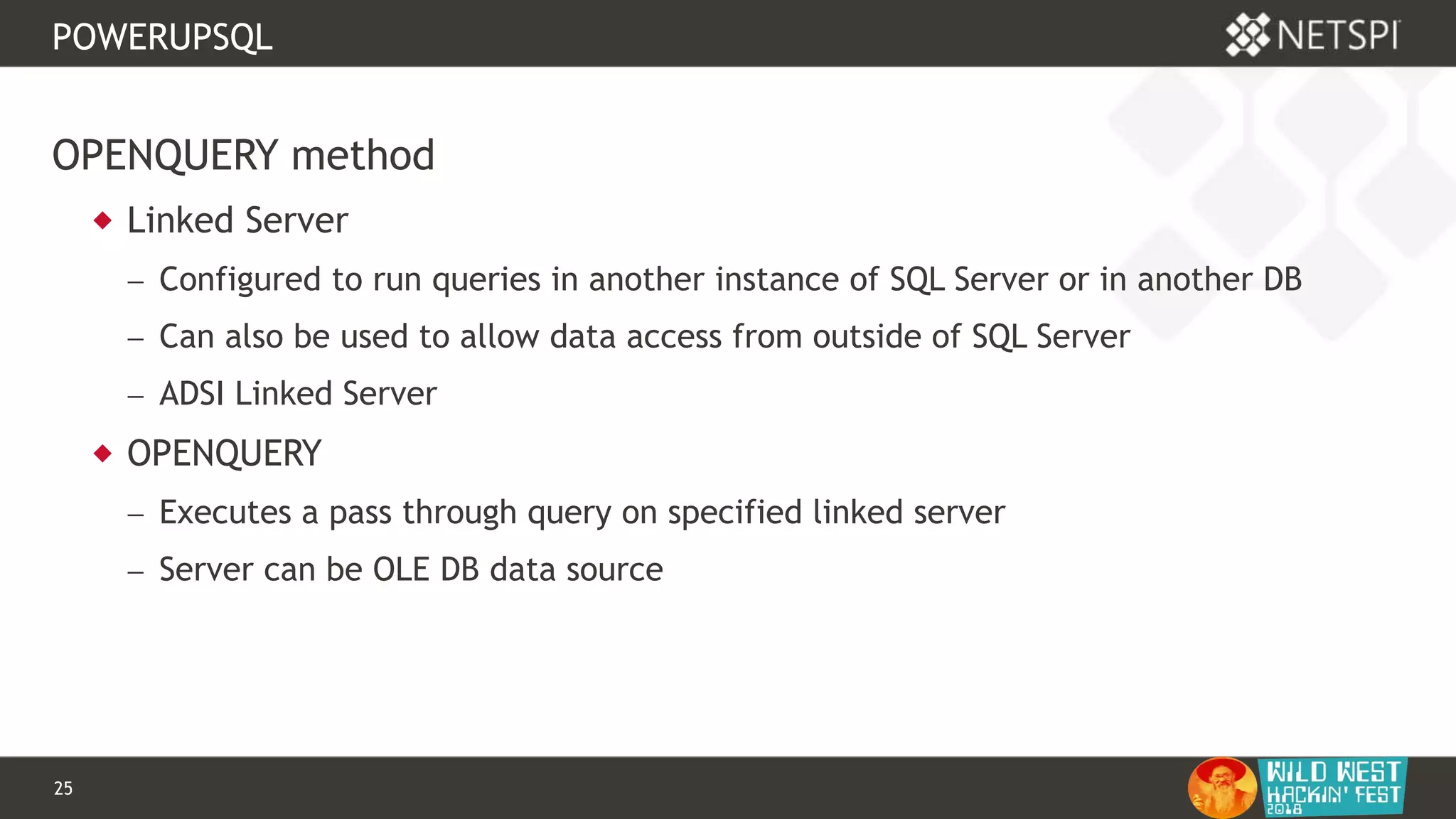
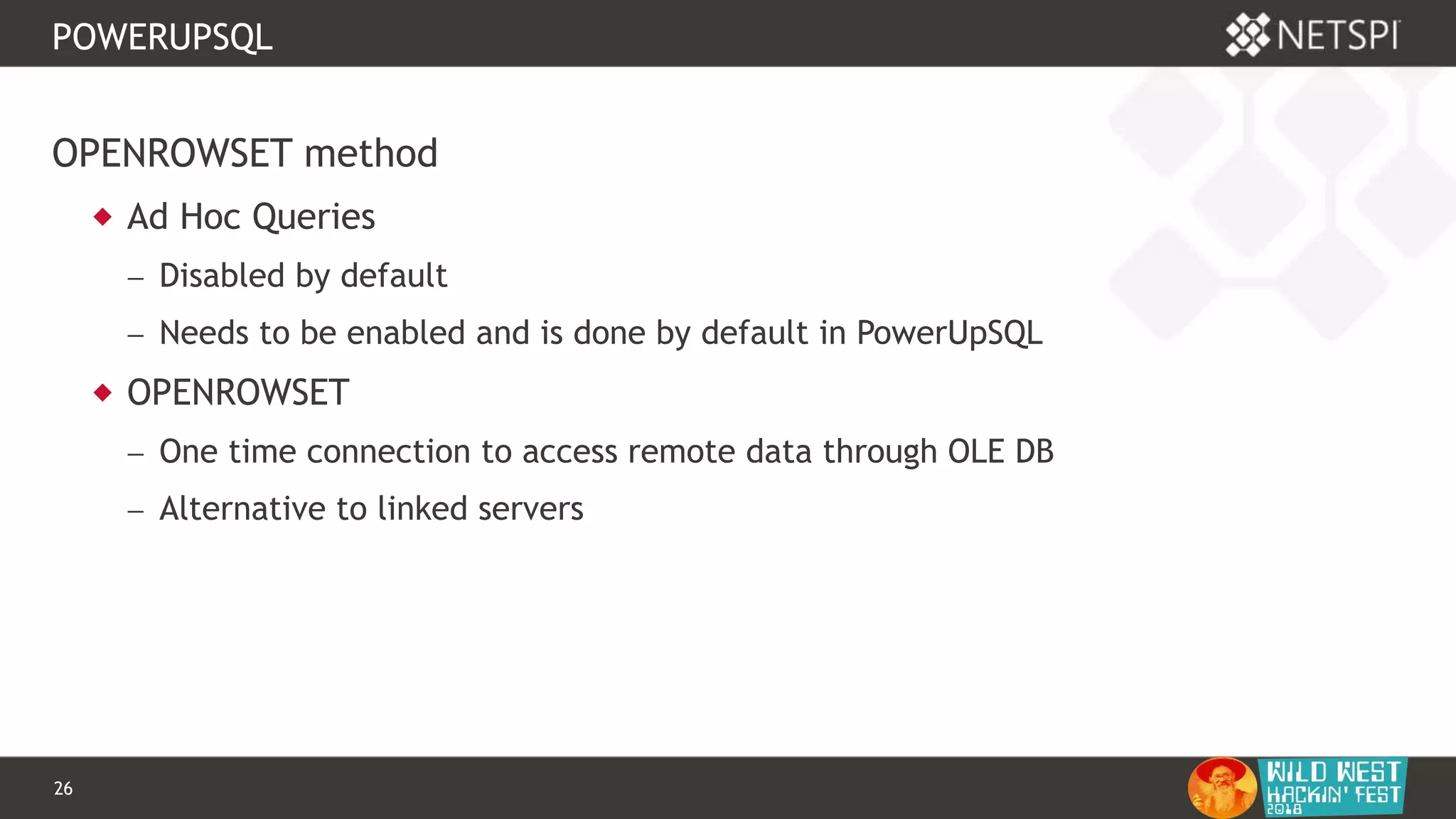
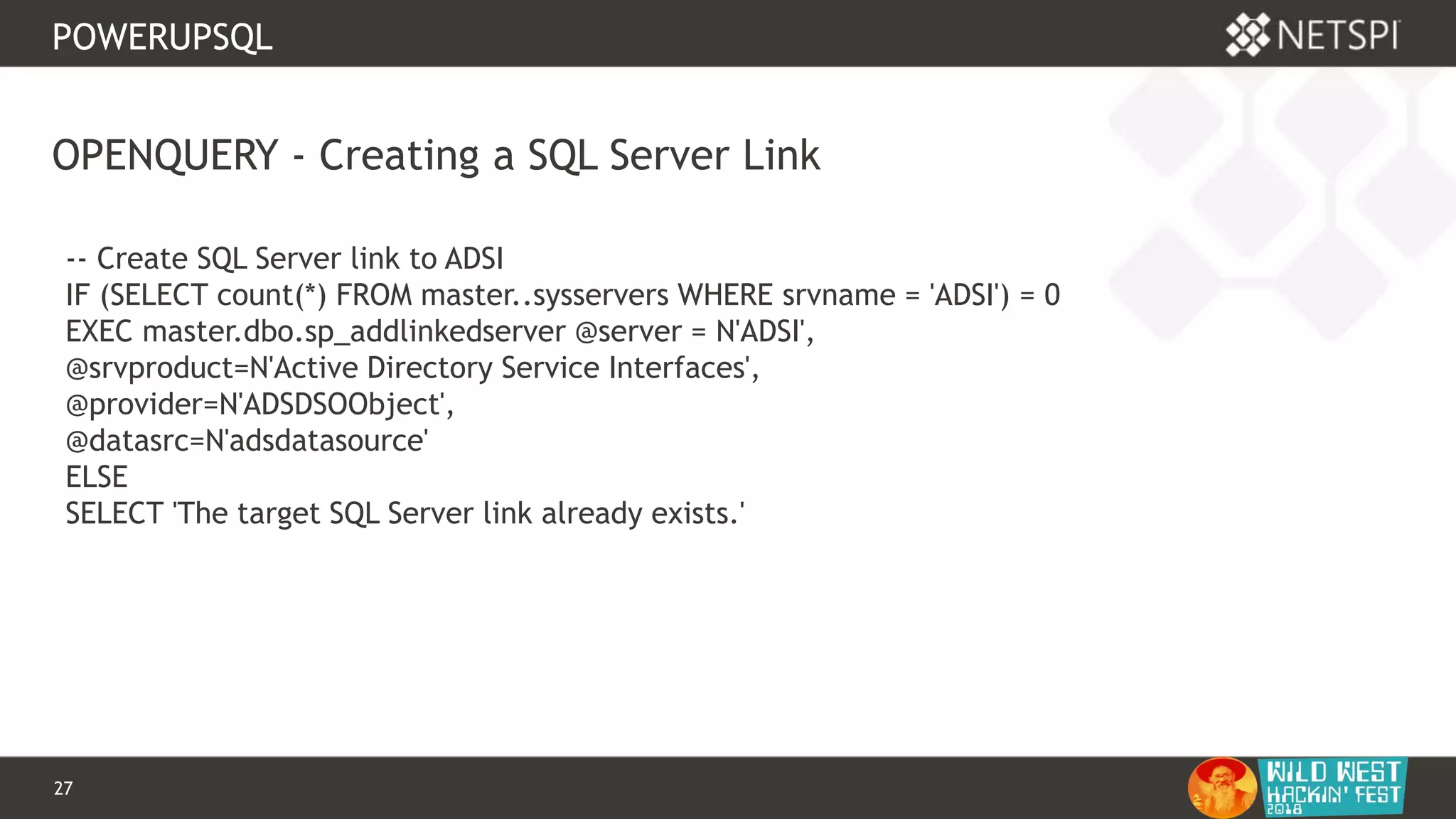
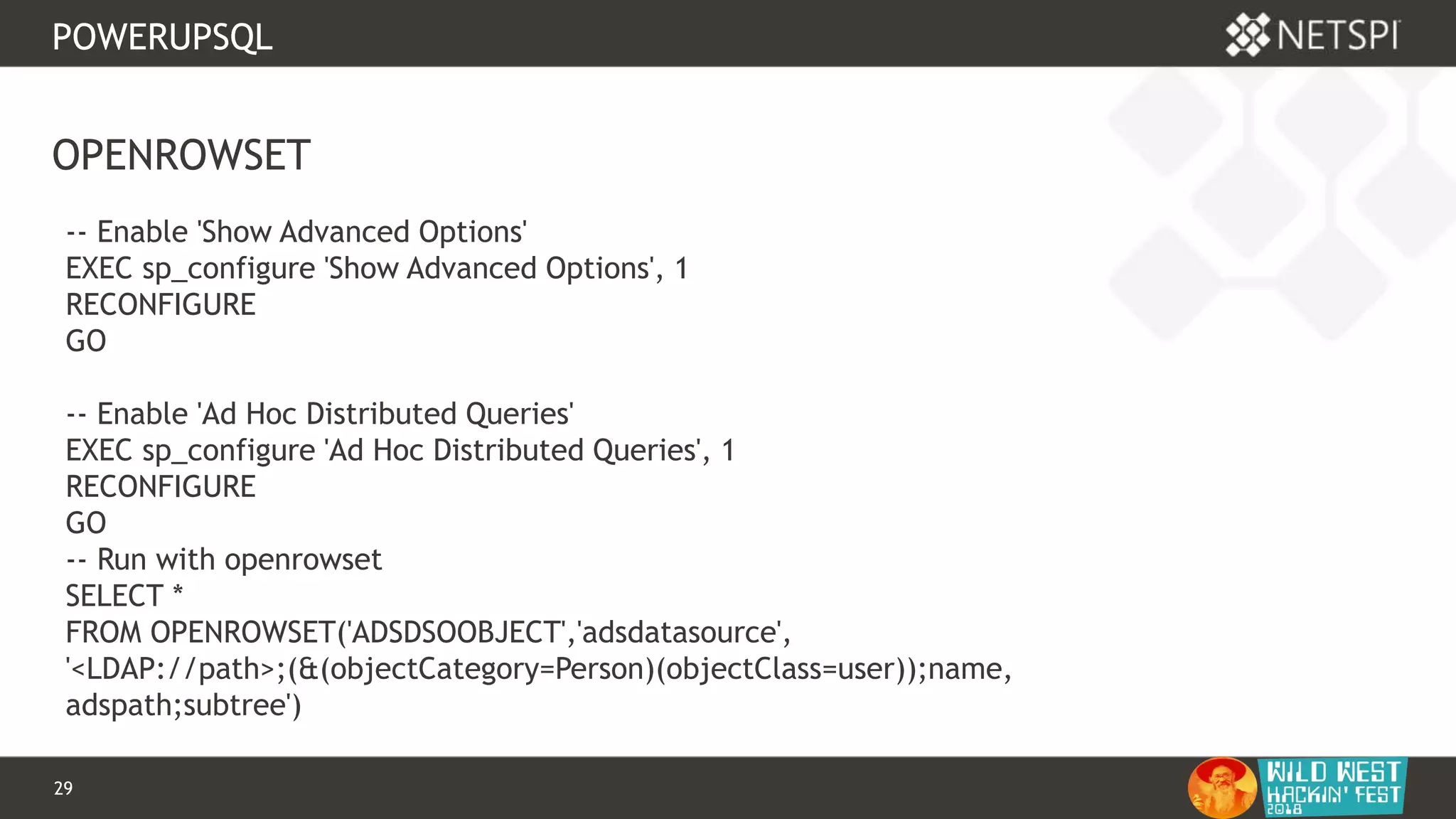
OPENQUERY
-- Define authentication context - OPENQUERY
EXEC sp_addlinkedsrvlogin
@rmtsrvname=N'ADSI',
@useself=N'True',
@locallogin=NULL,
@rmtuser=NULL,
@rmtpassword=NULL
GO
-- Use OPENQUERY
SELECT *
FROM
OPENQUERY([ADSI],'<LDAP://path>;(&(objectCategory=Person)(objectClass
=user));name, adspath;subtree')](https://image.slidesharecdn.com/wwhf-181027003858/75/WWHF-2018-Using-PowerUpSQL-and-goddi-for-Active-Directory-Information-Gathering-28-2048.jpg)


![45 Confidential & Proprietary
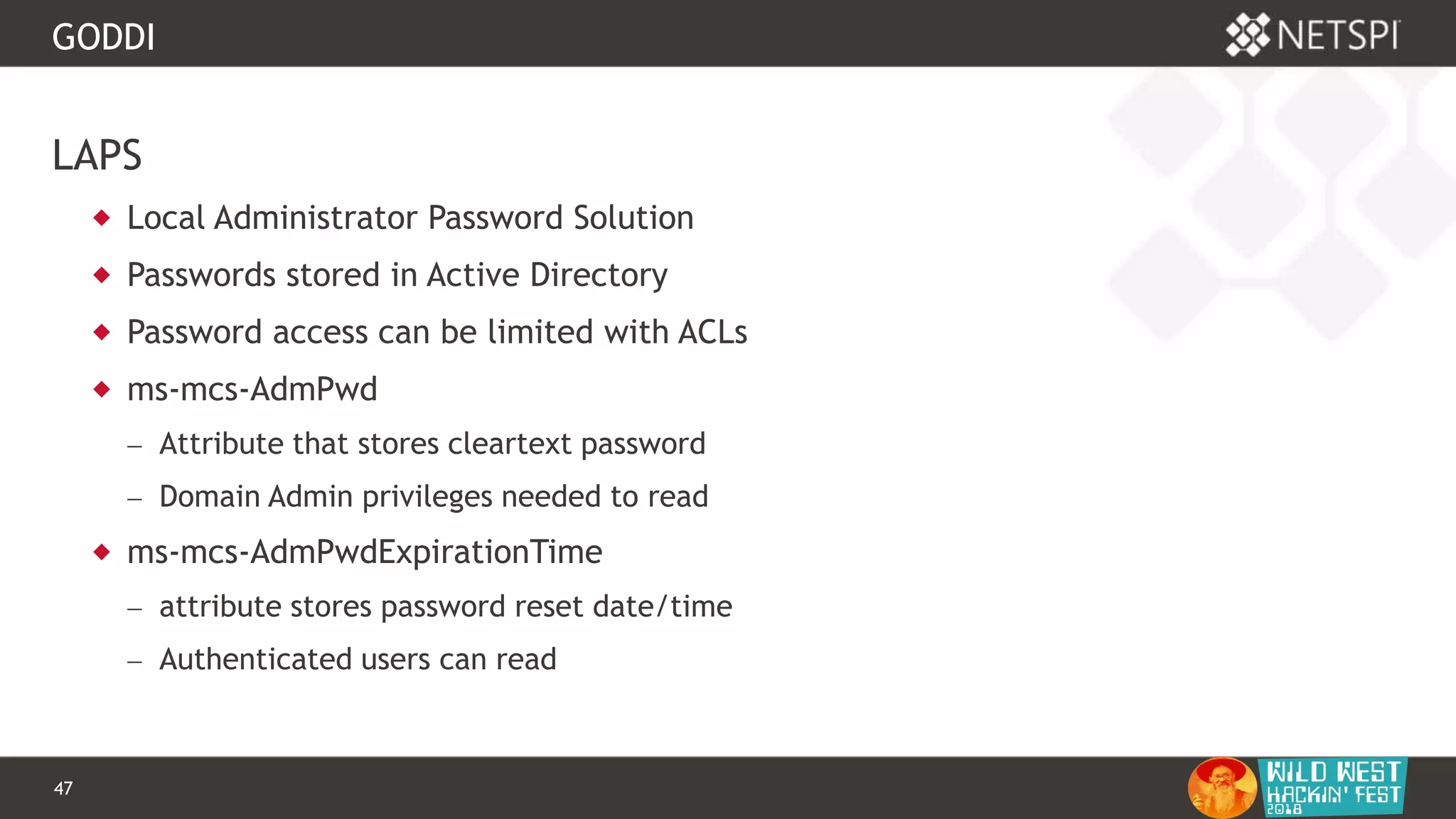
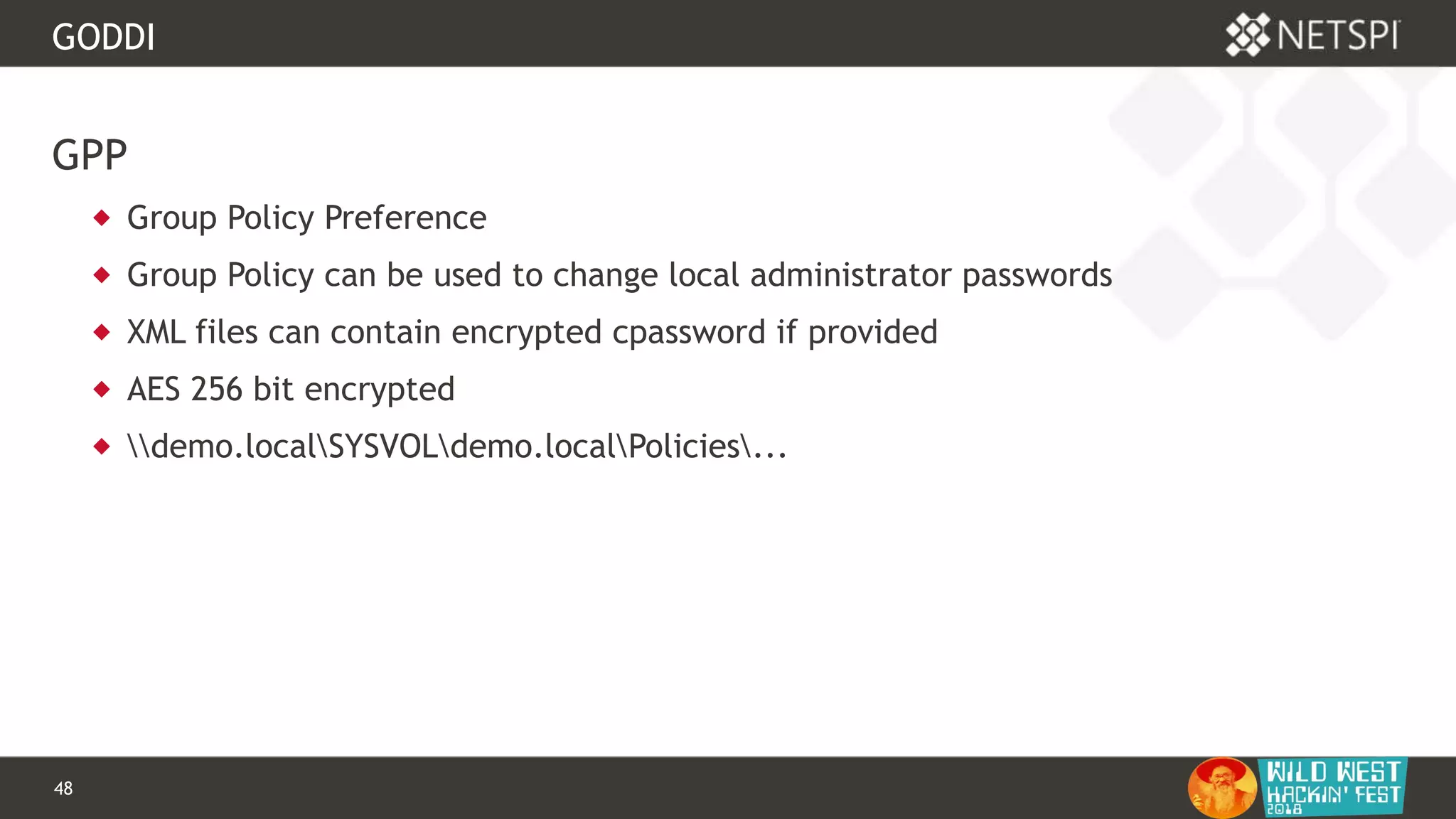
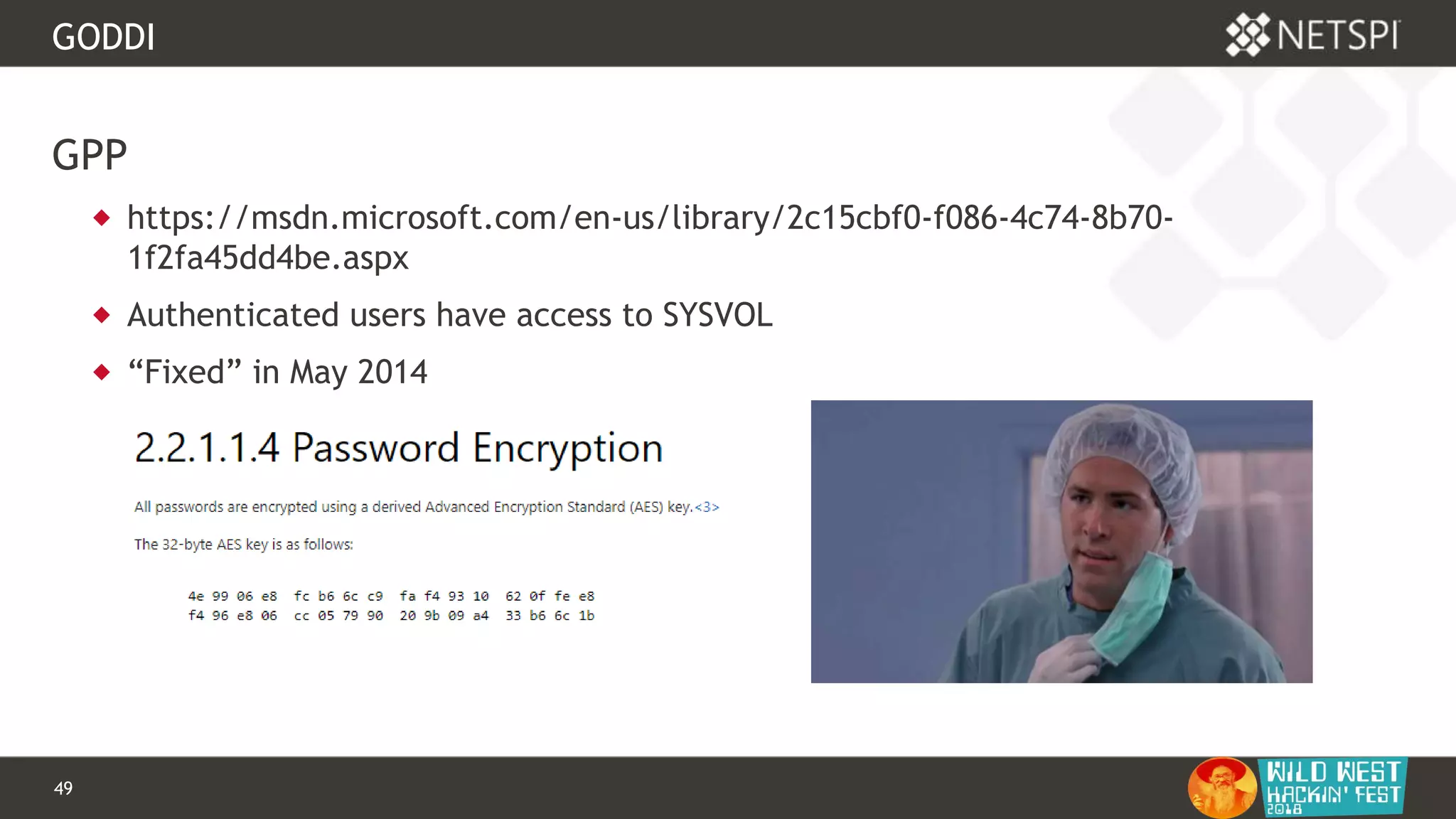
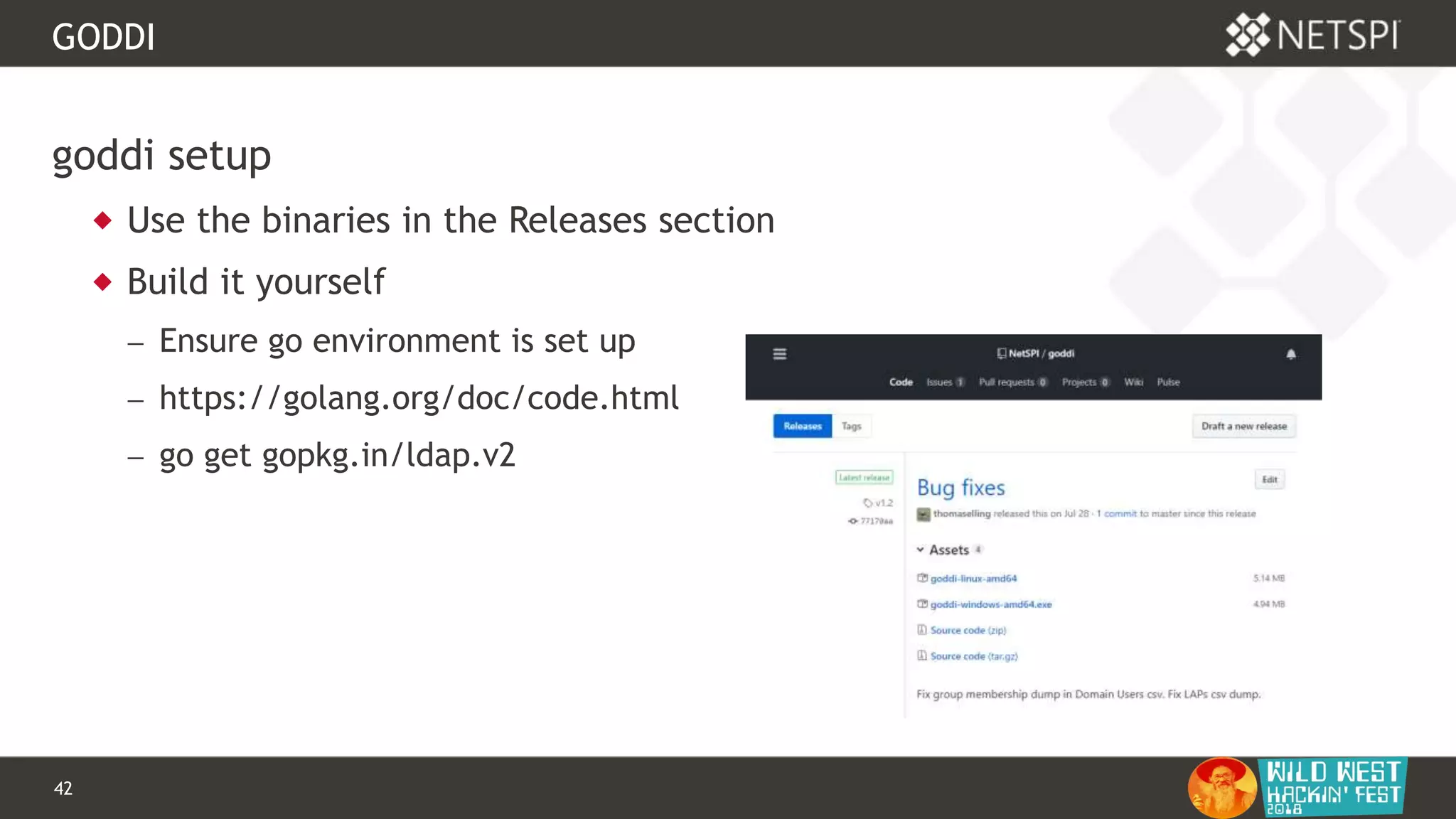
GODDI
func GetLAPS(conn *ldap.Conn, baseDN string) {
attributes := []string{
"dNSHostName",
"ms-Mcs-AdmPwd",
"ms-Mcs-AdmPwdExpirationTime"}
filter := "(objectCategory=Computer)"
sr := ldapSearch(baseDN, filter, attributes, conn)](https://image.slidesharecdn.com/wwhf-181027003858/75/WWHF-2018-Using-PowerUpSQL-and-goddi-for-Active-Directory-Information-Gathering-45-2048.jpg)