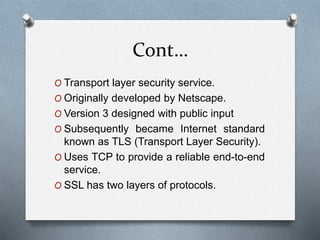
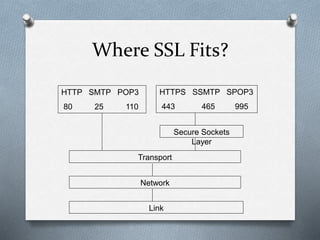
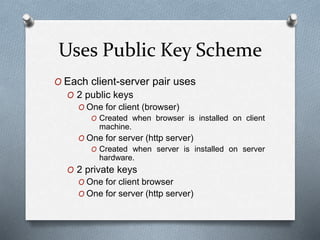
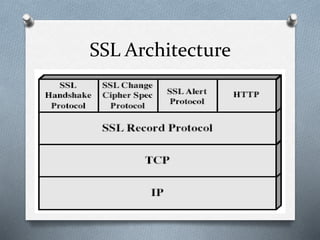
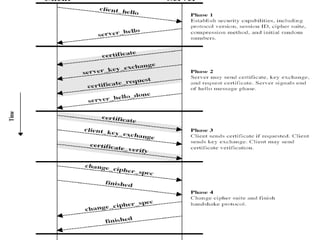
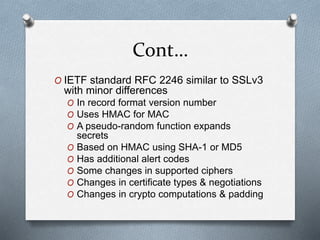
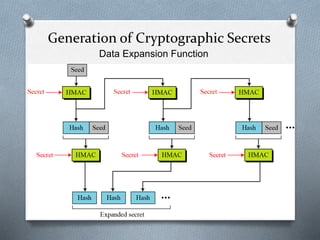
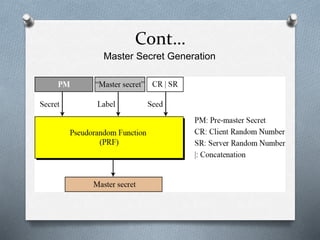
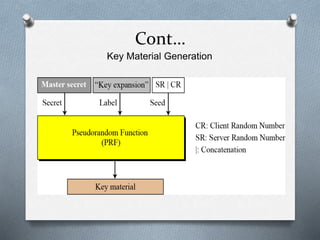
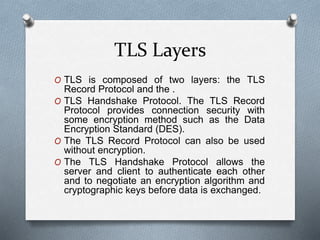
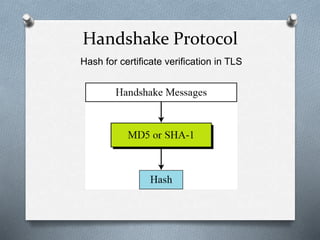
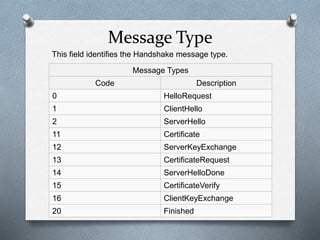
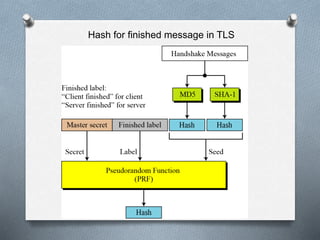
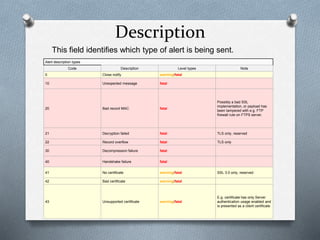
SSL and TLS are cryptographic protocols that provide secure communication on the internet. They use public/private key encryption to authenticate servers and establish encrypted connections. While similar, TLS is the standardized successor to SSL. Key differences include TLS using HMAC for integrity checking and having additional alert codes not found in SSL. Both protocols operate at the transport layer and provide data confidentiality, integrity, and server authentication.