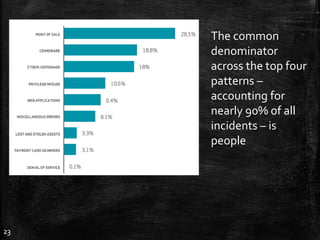
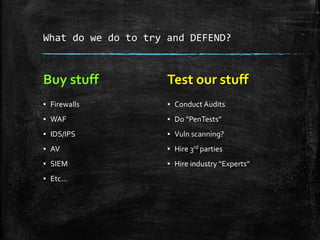
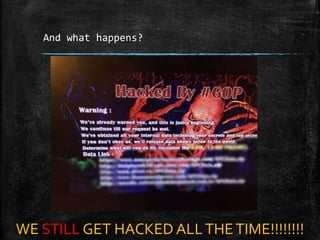
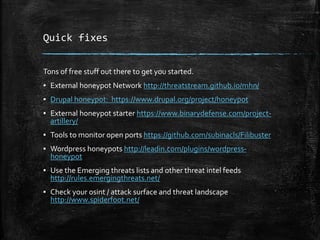
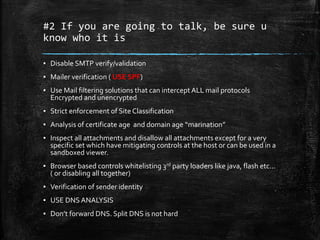
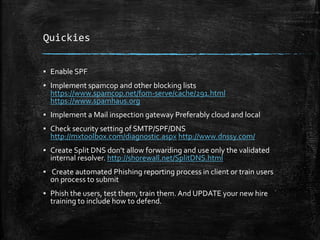
The document discusses the importance of robust cybersecurity measures and outlines various strategies to defend against cyber attacks. It highlights that many security incidents stem from human behavior and suggests implementing advanced monitoring, strict access controls, and thorough incident response plans. Additionally, the author offers tools and resources for improving network security and emphasizes the need for continuous adaptation and user training.