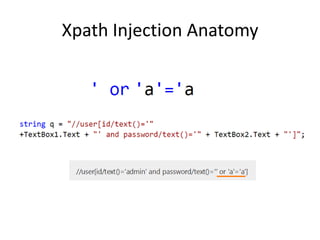
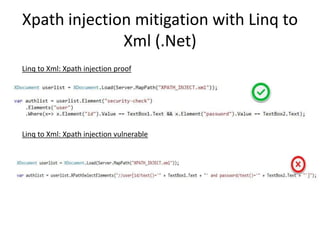
The document discusses XML security, focusing on various injection attacks like XPath and external entity expansions, along with their mitigations. It highlights the importance of keeping software updated, managing server information disclosure, and adhering to secure coding practices to defend against these threats. Resources and further reading are provided for deeper understanding of these vulnerabilities and their defenses.

















![External Entity Expansions
http://msdn.microsoft.com/en-us/magazine/ee335713.aspx
<!ENTITY stockprice SYSTEM "http://www.contoso.com/currentstockprice.ashx">
public class DoS : IHttpHandler
{
public void ProcessRequest(HttpContext context)
{
context.Response.ContentType = "text/plain";
byte[] data = new byte[1000000];
for (int i = 0; i < data.Length; i++) { data[i] = (byte)'A'; }
while (true)
{
context.Response.OutputStream.Write(data, 0, data.Length);
context.Response.Flush();
}
}
public bool IsReusable { get { return false; } }
}](https://image.slidesharecdn.com/devouringsecurityxmlattacks-140509121926-phpapp01/85/Devouring-Security-XML-Attack-surface-and-Defences-20-320.jpg)


![Directory browsing and file access
(JAXB)
import javax.xml.bind.*;
import javax.xml.stream.*;
import javax.xml.transform.stream.StreamSource;
public class Demo {
public static void main(String[] args) throws Exception {
JAXBContext jc = JAXBContext.newInstance(Customer.class);
XMLInputFactory xif = XMLInputFactory.newFactory();
xif.setProperty(XMLInputFactory.IS_SUPPORTING_EXTERNAL_ENTITIES, false);
xif.setProperty(XMLInputFactory.SUPPORT_DTD, false);
XMLStreamReader xsr = xif.createXMLStreamReader(new StreamSource("src/xxe/input.xml"));
Unmarshaller unmarshaller = jc.createUnmarshaller();
Customer customer = (Customer) unmarshaller.unmarshal(xsr);
Marshaller marshaller = jc.createMarshaller();
marshaller.setProperty(Marshaller.JAXB_FORMATTED_OUTPUT, true);
marshaller.marshal(customer, System.out);
}
}
More:
http://stackoverflow.com/questions/12977299/preven-xxe-attack-with-jaxb](https://image.slidesharecdn.com/devouringsecurityxmlattacks-140509121926-phpapp01/85/Devouring-Security-XML-Attack-surface-and-Defences-23-320.jpg)


