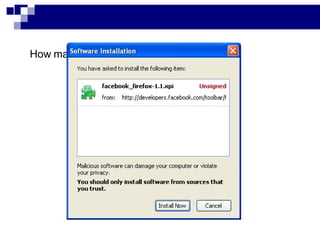
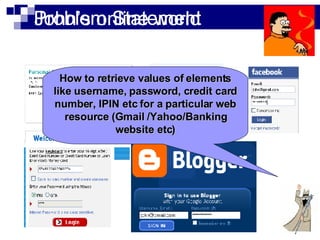
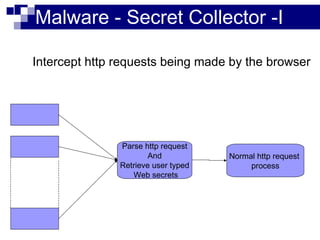
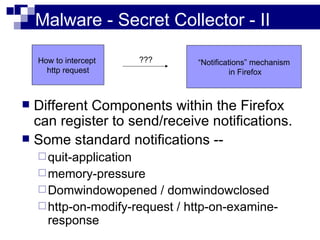
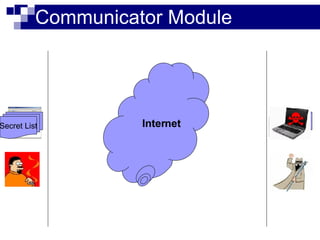
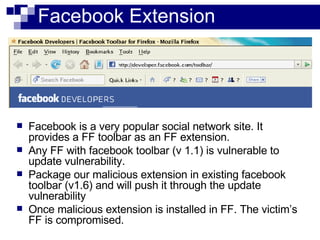
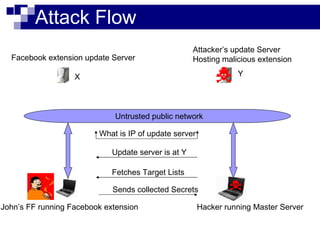
This document summarizes how malware can steal sensitive web information by exploiting Firefox vulnerabilities. It discusses how a malicious Firefox extension could intercept HTTP requests, parse them to retrieve usernames, passwords, credit card numbers entered by the user on various websites. The malware would collect these secrets into a list and send this list over the internet. It then describes some ways such a malicious extension could install itself on a victim's Firefox browser without their knowledge, including exploiting other software or extension upgrade vulnerabilities. It warns users to only install extensions from trusted sources and monitor their browser for unusual behavior.








![Thank U [email_address]](https://image.slidesharecdn.com/sunilhackingfirefox-5643/85/Sunil-Hacking_firefox-19-320.jpg)