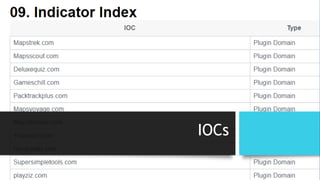
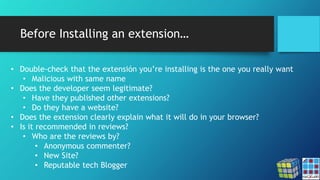
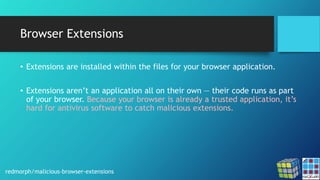
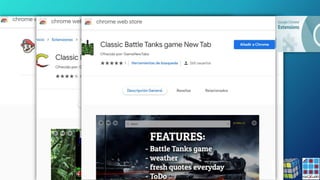
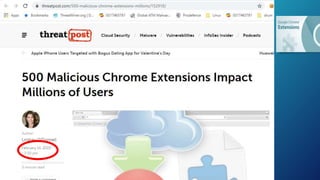
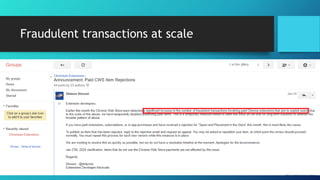
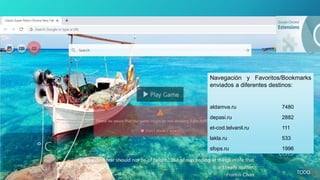
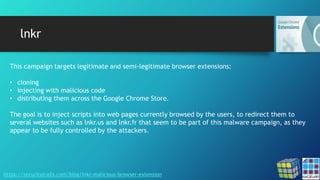
The document discusses the risks associated with Google Chrome extensions, highlighting their purpose, how they can be malicious, and the challenges in detecting such threats due to lack of pre-screening by platforms like the Chrome Web Store. It outlines examples of malicious extensions that have been involved in data theft and fraud, along with recommendations for users to verify the legitimacy of extensions before installation. Additionally, it offers guidance for administrators on managing and blocking risky extensions in organizational settings.













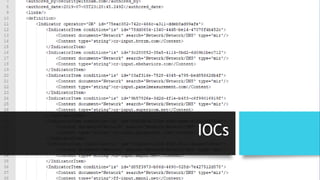
![DataSpii: The catastrophic data leak via
browser extensions - Sam Jadali
https://securitywithsam.com/2019/07/dataspii-leak-via-browser-extensions/
Test 1. SuperZoom extension on macOS.
Our original visit:
OUR-REDACTED-IP – – [11/Mar/2019:20:50:06 +0000] “GET
/samtesting.html?&os=mac&brow=crmium&v=74.0.3684.0&ext=SZ&date=mar112019&time=149pmpst&socse
c=123004567&customerssn=123004567&lastname=doe&first=john&last=doe&password=mypass&p=anotherpa
ss&apikey=XYZ HTTP/1.1” 200 198 “-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3684.0 Safari/537.36”
Approximately 4 hours later, an unknown AWS IP performed a GET request of the collected URL:
184.72.115.35 – – [12/Mar/2019:01:03:45 +0000] “GET
/samtesting.html?&os=mac&brow=crmium&v=74.0.3684.0&ext=SZ&date=mar112019&time=149pmpst&socse
c=123004567&customerssn=123004567&lastname=doe&first=john&last=doe&password=mypass&p=anotherpa
ss&apikey=XYZ HTTP/1.1” 200 198 “-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1)
AppleWebKit/600.1.25 (KHTML, like Gecko) Version/8.0 Safari/600.1.25”](https://image.slidesharecdn.com/chromeexthacklab032020v2-200305164401/85/Chrome-Extensions-Masking-risks-in-entertainment-24-320.jpg)
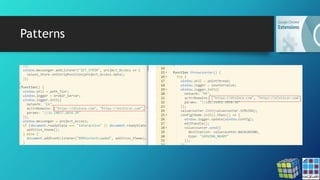
![DataSpii: The catastrophic data leak via
browser extensions - Sam Jadali
https://securitywithsam.com/2019/07/dataspii-leak-via-browser-extensions/
Test 2. SaveFrom.net Helper extension (installed via the extension author’s website) on macOS.
Our original visit:
[OUR-REDACTED-IP] – – [11/Mar/2019:21:42:00 +0000] “GET
/samtesting.html?&os=macosx10143&brow=ff&v=65.0.1&ext=SFfromsfhelpernet&date=mar112019&time=24
1pmpst&socsec=123004567&customerssn=123004567&lastname=doe&first=john&last=doe&password=mypass
&p=anotherpass&apikey=XYZ HTTP/1.1” 200 198 “-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:65.0)
Gecko/20100101 Firefox/65.0”
Approximately 3.5 hours later, an unknown AWS IP performed a GET request of the collected URL:
184.72.115.35 – – [12/Mar/2019:01:17:47 +0000] “GET
/samtesting.html?&os=macosx10143&brow=ff&v=65.0.1&ext=SFfromsfhelpernet&date=mar112019&time=24
1pmpst&socsec=123004567&customerssn=123004567&lastname=doe&first=john&last=doe&password=mypass
&p=anotherpass&apikey=XYZ HTTP/1.1” 200 198 “-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1)
AppleWebKit/600.1.25 (KHTML, like Gecko) Version/8.0 Safari/600.1.25”](https://image.slidesharecdn.com/chromeexthacklab032020v2-200305164401/85/Chrome-Extensions-Masking-risks-in-entertainment-25-320.jpg)
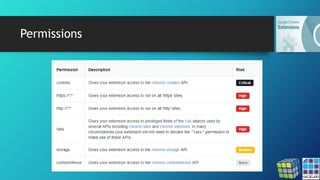
![DataSpii: The catastrophic data leak via
browser extensions - Sam Jadali
https://securitywithsam.com/2019/07/dataspii-leak-via-browser-extensions/
Using a browser with a Party Y extension, we visited various sample file types, including zip and SQL database
files.
When visiting the zip file, the browser downloaded the file into the file system. It did not load them directly in
the browser. As a result, we did not observe the transmission of the zip URL to a third-party hostname.
However, the SQL files were loaded in the browser and the URL of our SQL files was transmitted to cr-
input.hvrzm.com. Three hours after it was collected by the Party Y extension, we observed a third-party visit to
our SQL file:
184.72.115.35 – – [18/May/2019:12:50:27 +0000] “GET /dataspii-sql-50000rows.sql HTTP/1.1” 200 4393501
“-” “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_1) AppleWebKit/600.1.25 (KHTML, like Gecko)
Version/8.0 Safari/600.1.25”](https://image.slidesharecdn.com/chromeexthacklab032020v2-200305164401/85/Chrome-Extensions-Masking-risks-in-entertainment-26-320.jpg)