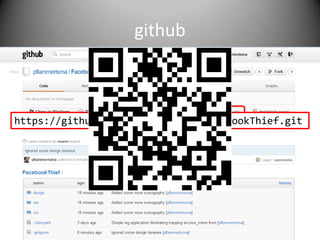
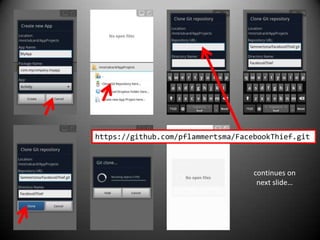
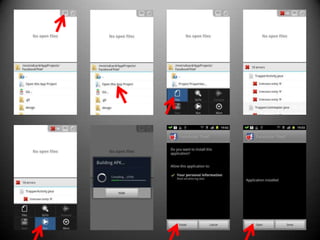
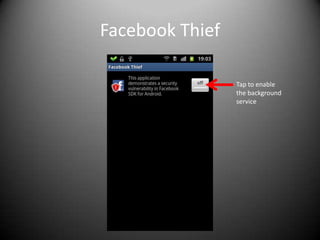
This document discusses building an Android app to reveal security holes. It begins by instructing attendees to connect to an open wireless network and allow non-market apps. It then discusses Android security principles like permissions and sandboxing. It notes the implications of rooting a device, including granting permissions and accessing app data. The document describes exploiting the Facebook SDK to steal login credentials from other apps. It recommends attendees download code from a GitHub link to create an app that can steal Facebook logins in the background without user knowledge.