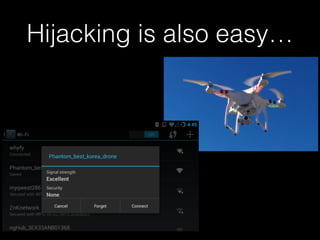
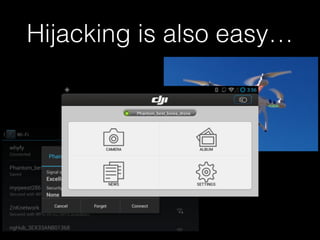
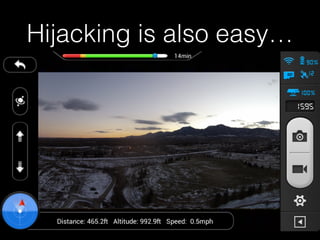
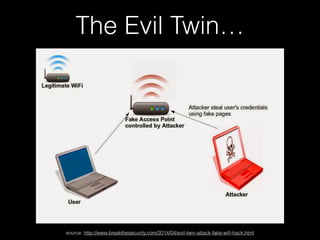
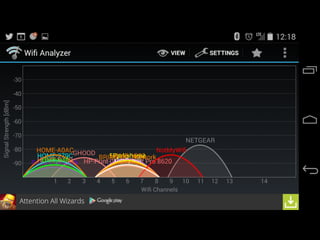
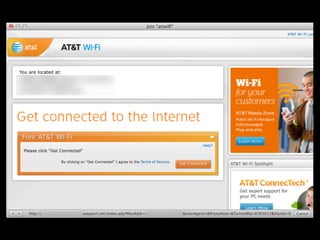
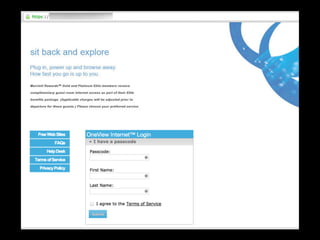
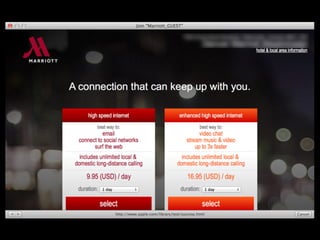
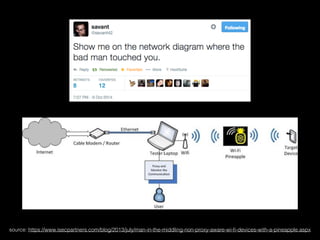
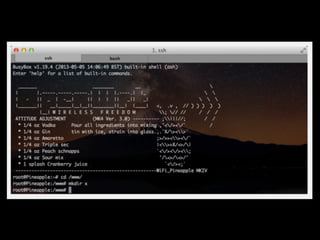
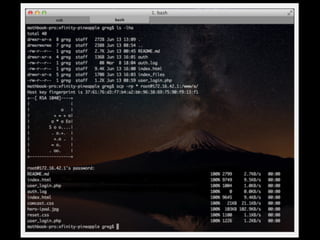
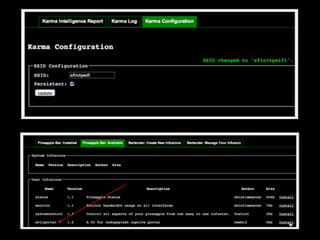
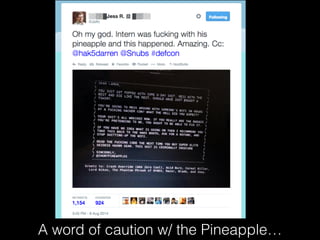
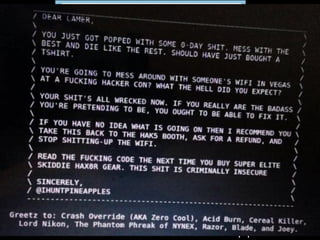
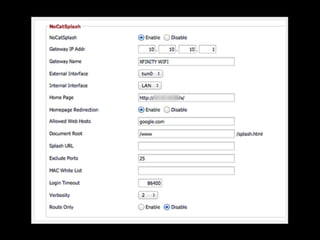
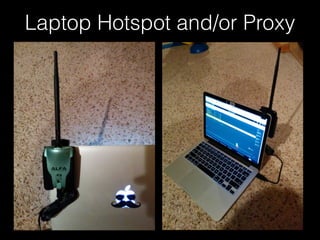
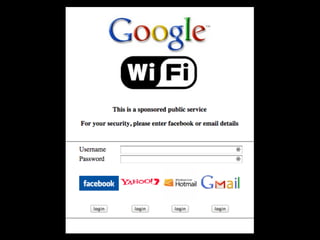
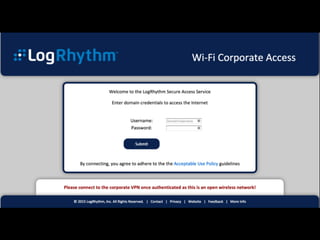
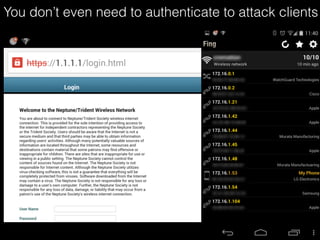
The document is a presentation on Wi-Fi hacking techniques aimed at web pentesters, discussing various attacks such as WEP cracking, WPA/WPA2 attacks, and man-in-the-middle strategies. It provides methods for bypassing captive portals, deauthentication of clients, and hijacking techniques, while also warning that many techniques demonstrated are likely illegal and not advisable against unauthorized targets. The document includes resources and tools for testing and defending against potential Wi-Fi security threats.











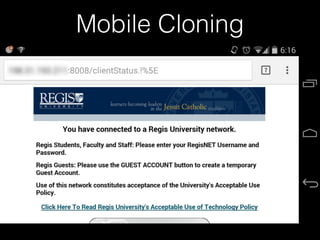
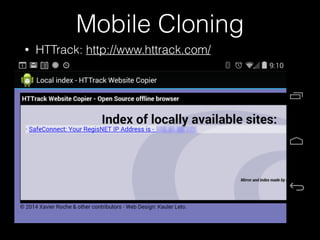





![Landing Page
Pineapple Configuration - JavaScript Necessities
/www/[directory]/index.html](https://image.slidesharecdn.com/wifi-hotspot-attacks-141026103248-conversion-gate02/85/Wi-Fi-Hotspot-Attacks-38-320.jpg)
![PHP Form Processor
Pineapple Configuration
Easier than using IPTables
/www/[directory]/auth/login.php](https://image.slidesharecdn.com/wifi-hotspot-attacks-141026103248-conversion-gate02/85/Wi-Fi-Hotspot-Attacks-39-320.jpg)


















![Thank You!
Questions?
https://github.com/gfoss/misc/Wireless/Captive-Portals/
Greg Foss
Senior Security Research Engineer
greg.foss[at]LogRhythm.com
@heinzarelli](https://image.slidesharecdn.com/wifi-hotspot-attacks-141026103248-conversion-gate02/85/Wi-Fi-Hotspot-Attacks-73-320.jpg)