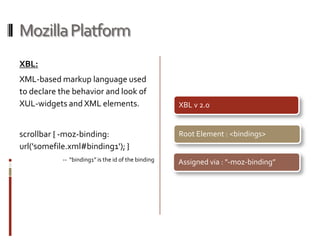
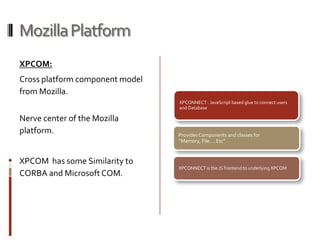
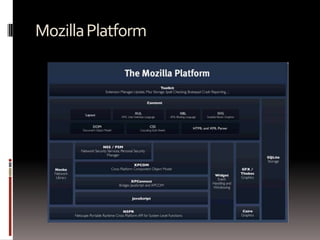
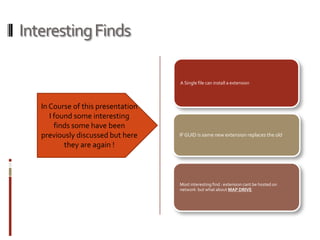
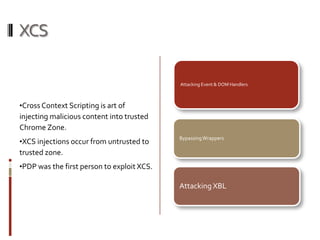
This presentation demonstrates how the Mozilla Firefox browser platform could be exploited by malicious extensions. It shows how extensions have full trust and can access and modify other extensions. It then demonstrates attacks like logging keystrokes, executing native code, and cracking passwords. It also discusses cross-context scripting and other techniques like bypassing wrappers and exploiting XML bindings. The presentation recommends steps users and developers can take to help secure the platform like verifying extension files and privileges.