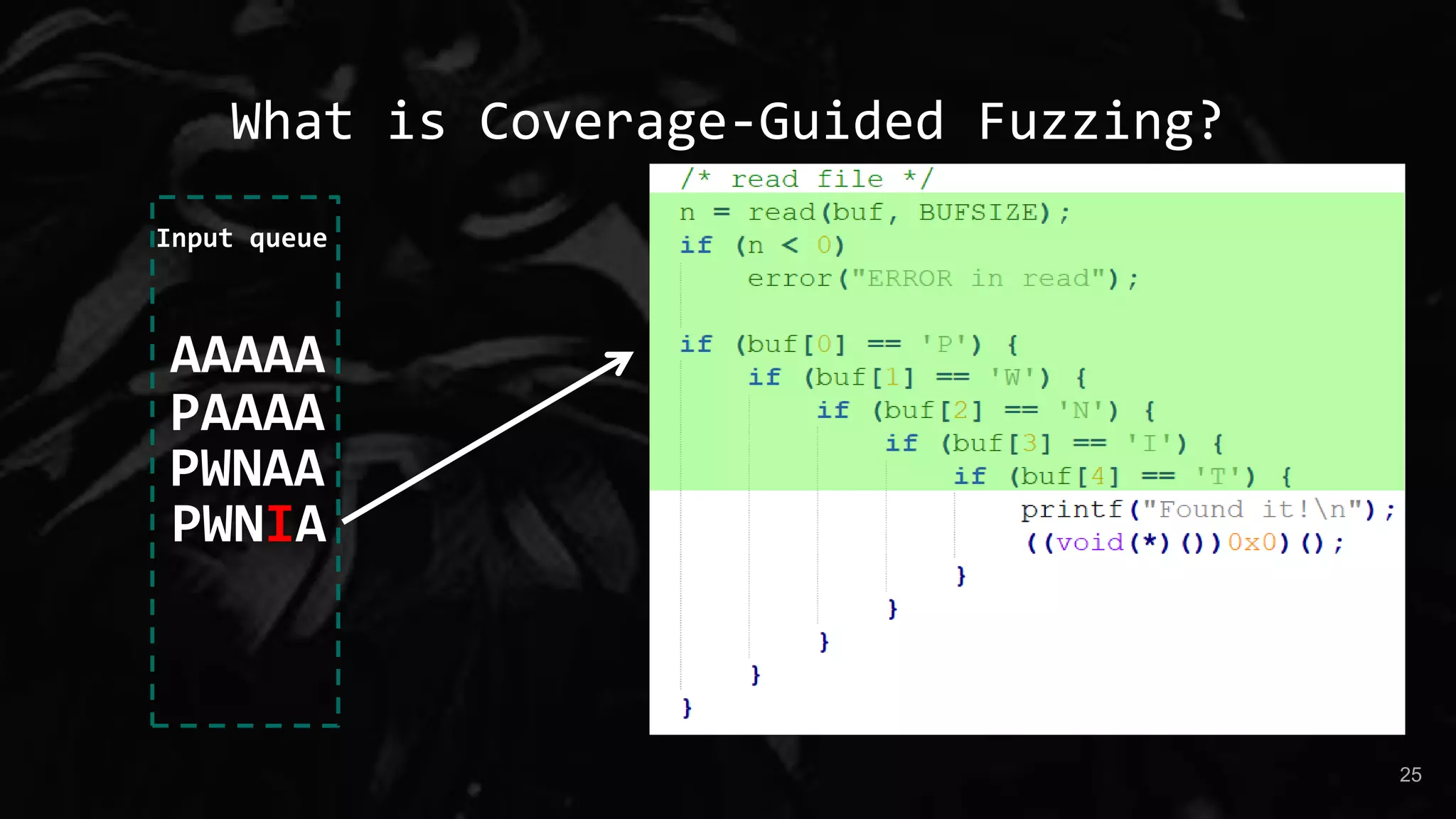
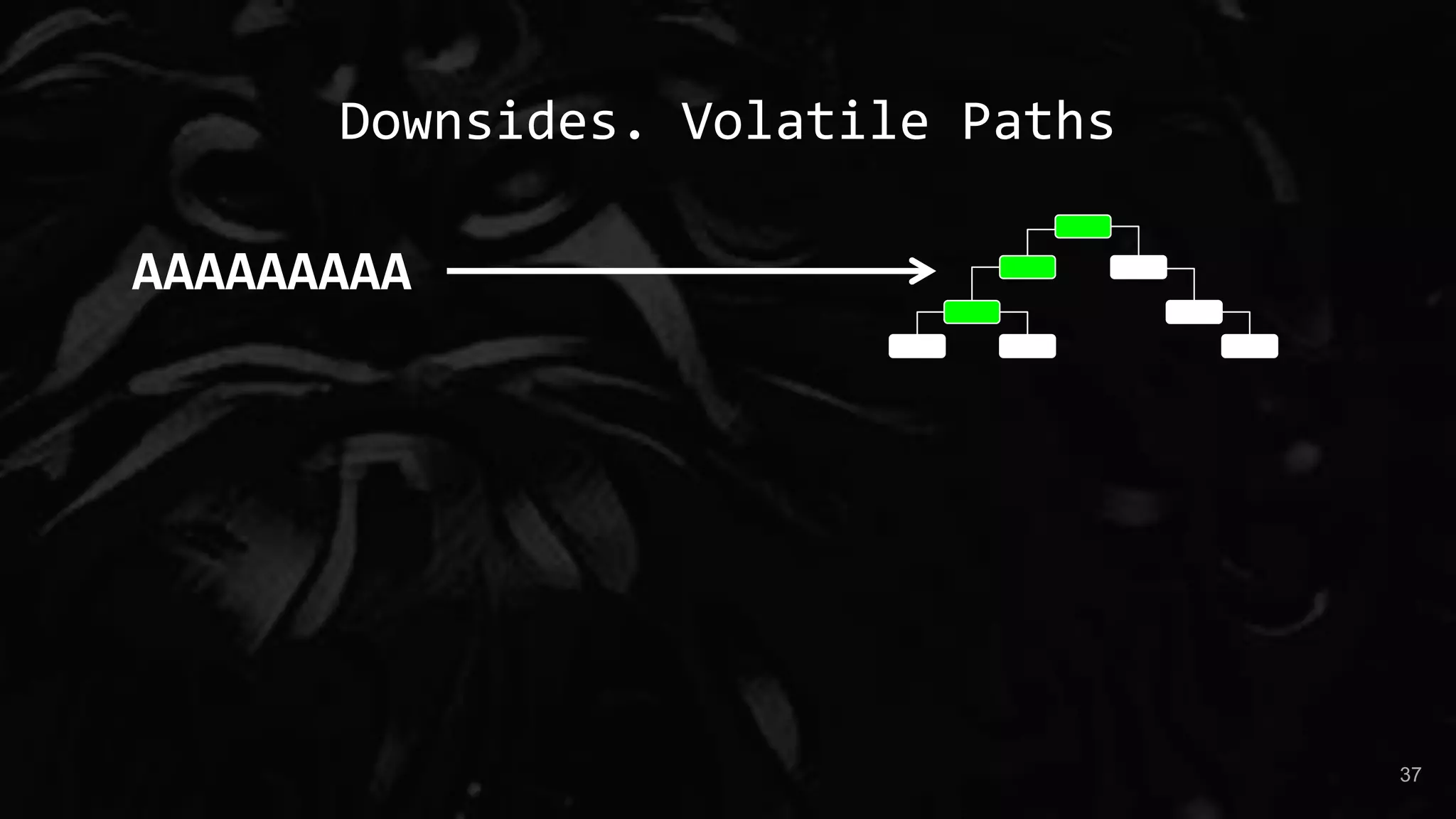
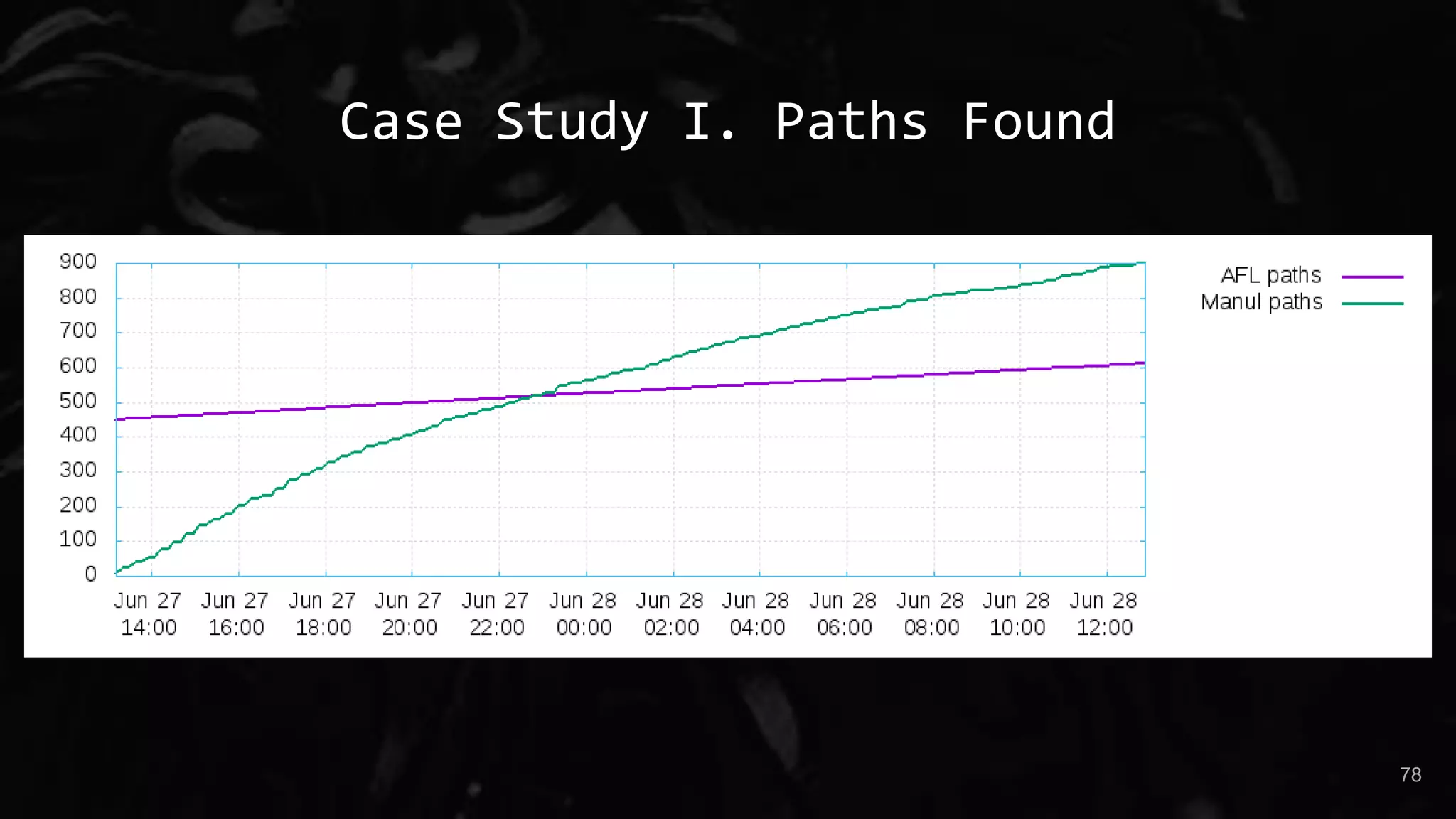
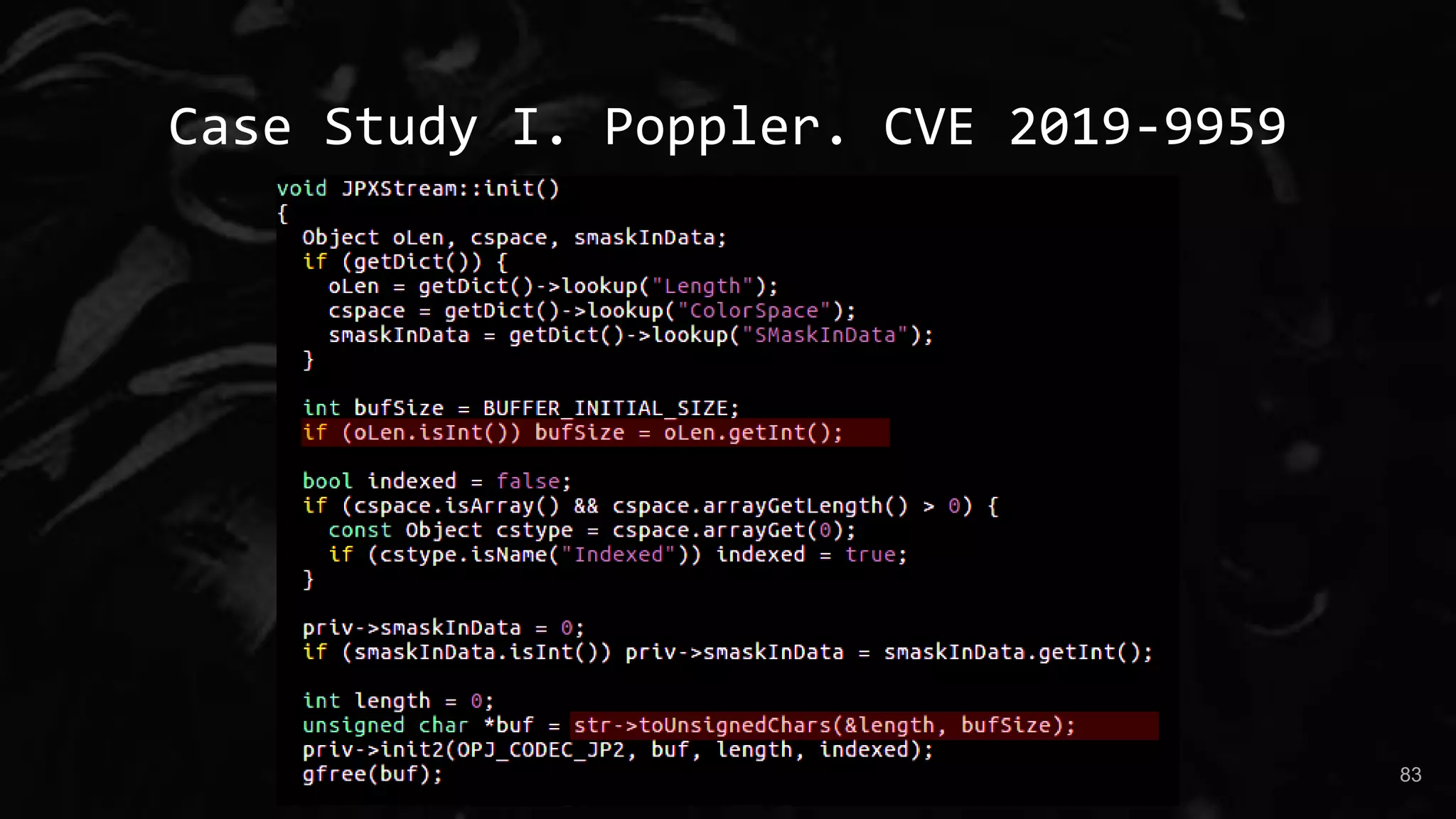
The document presents a talk by Maksim Shudrak on improving coverage-guided fuzzing and discovering zero-day vulnerabilities in challenging software targets. It introduces 'manul,' a new open-source fuzzer that offers advanced features like parallel fuzzing and integration with third-party mutators, outperforming traditional tools like AFL. Case studies demonstrate manul's effectiveness in identifying critical vulnerabilities in widely used open-source projects such as Poppler and Zeek.