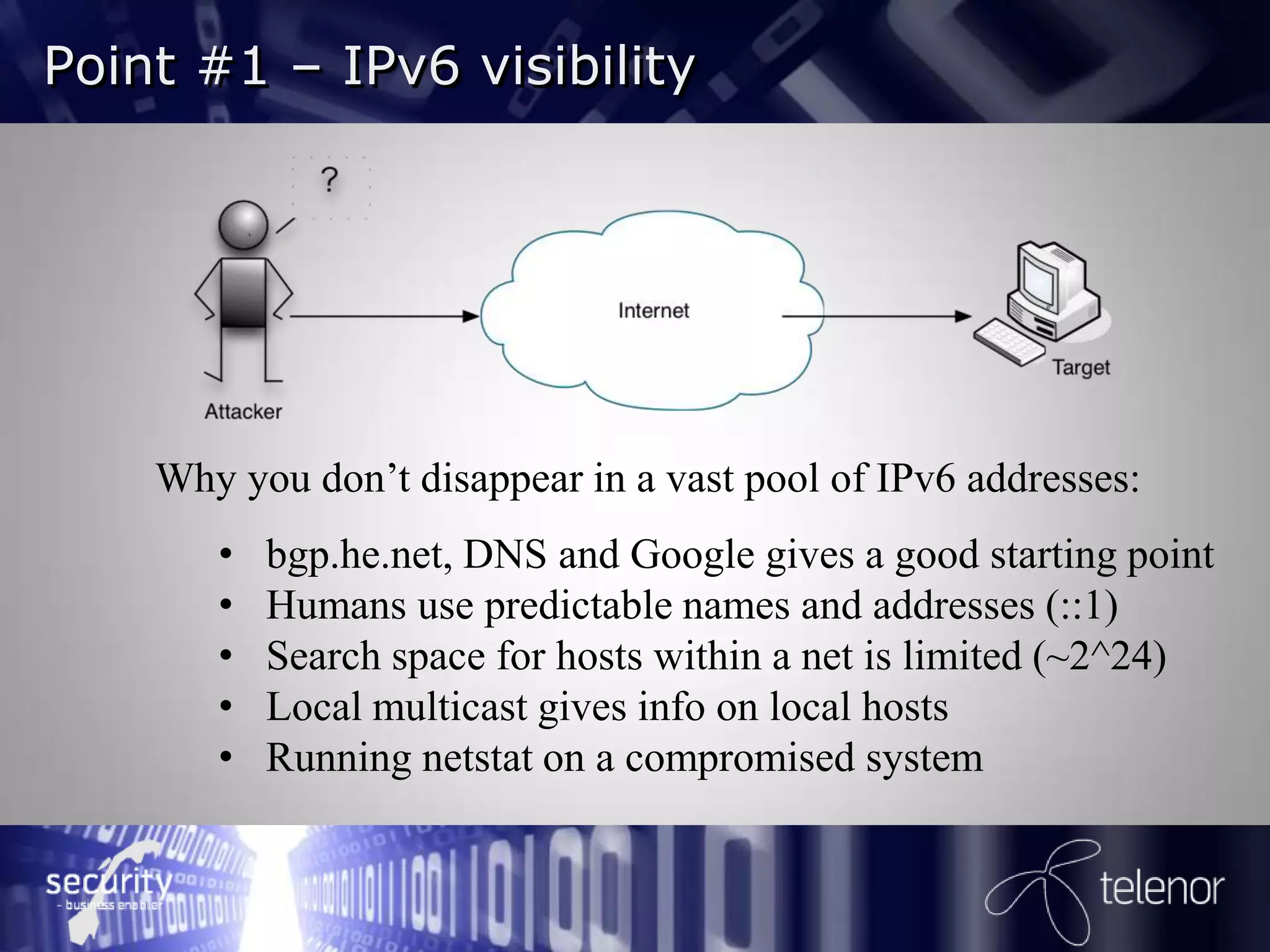
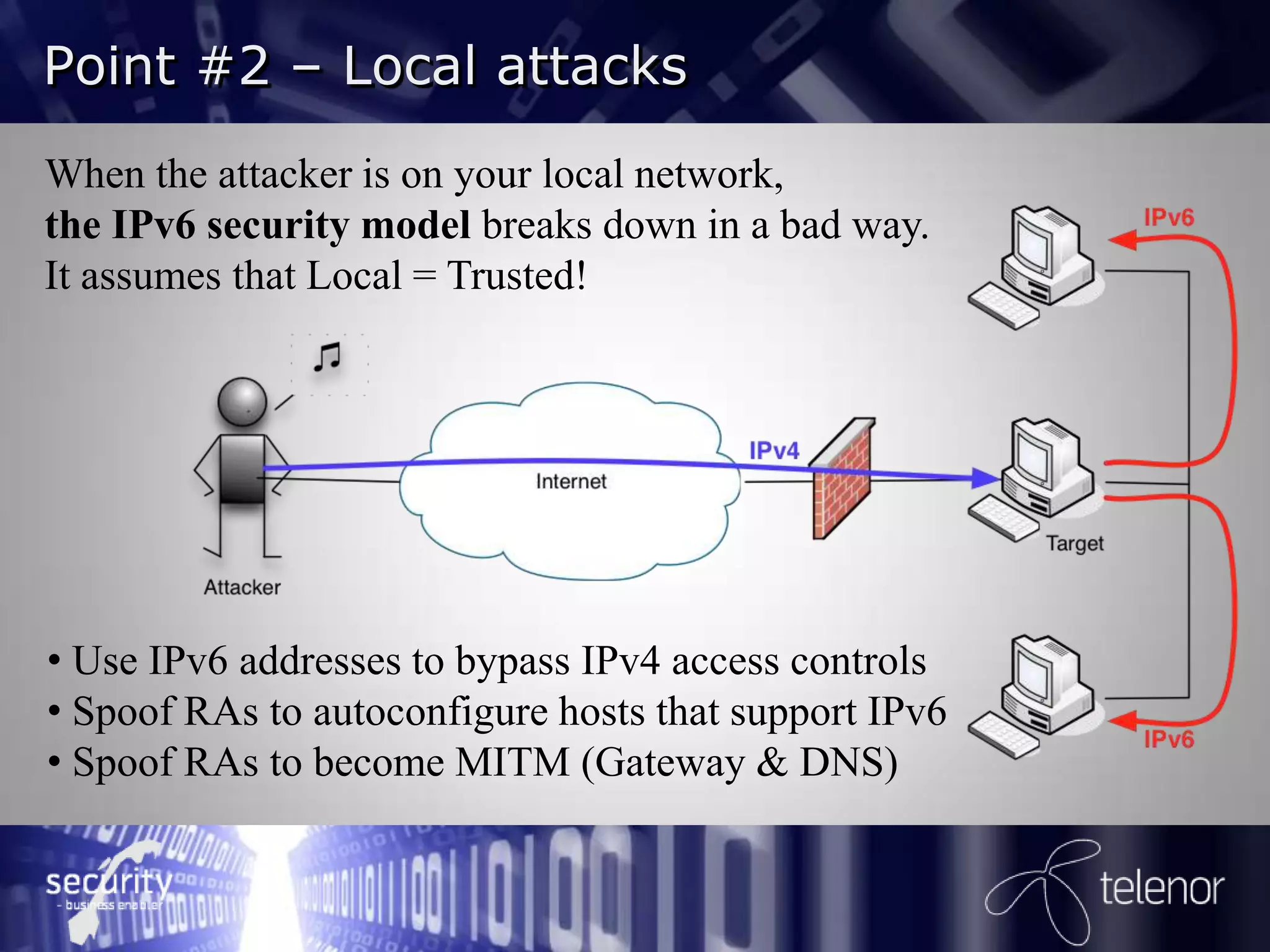
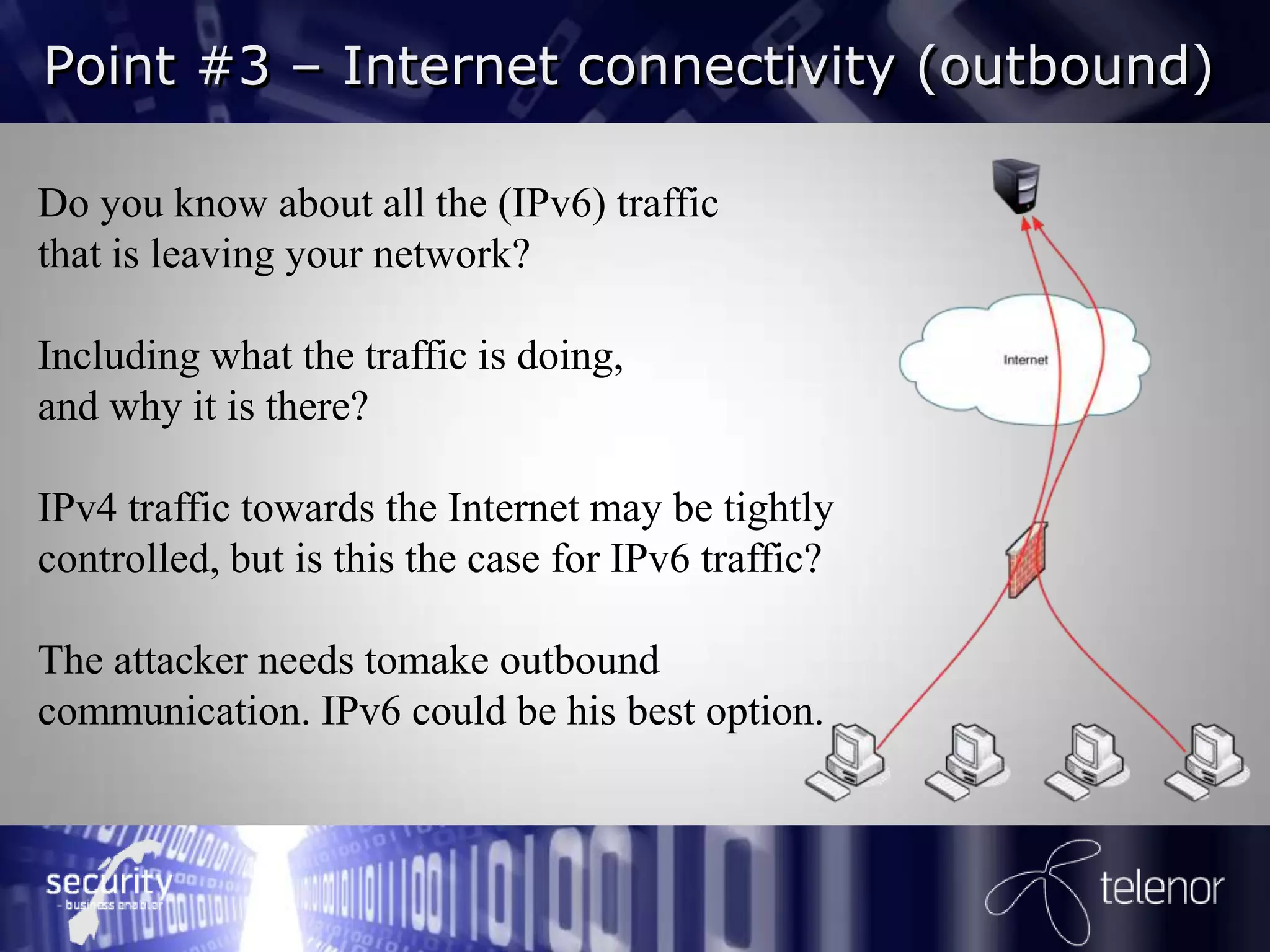
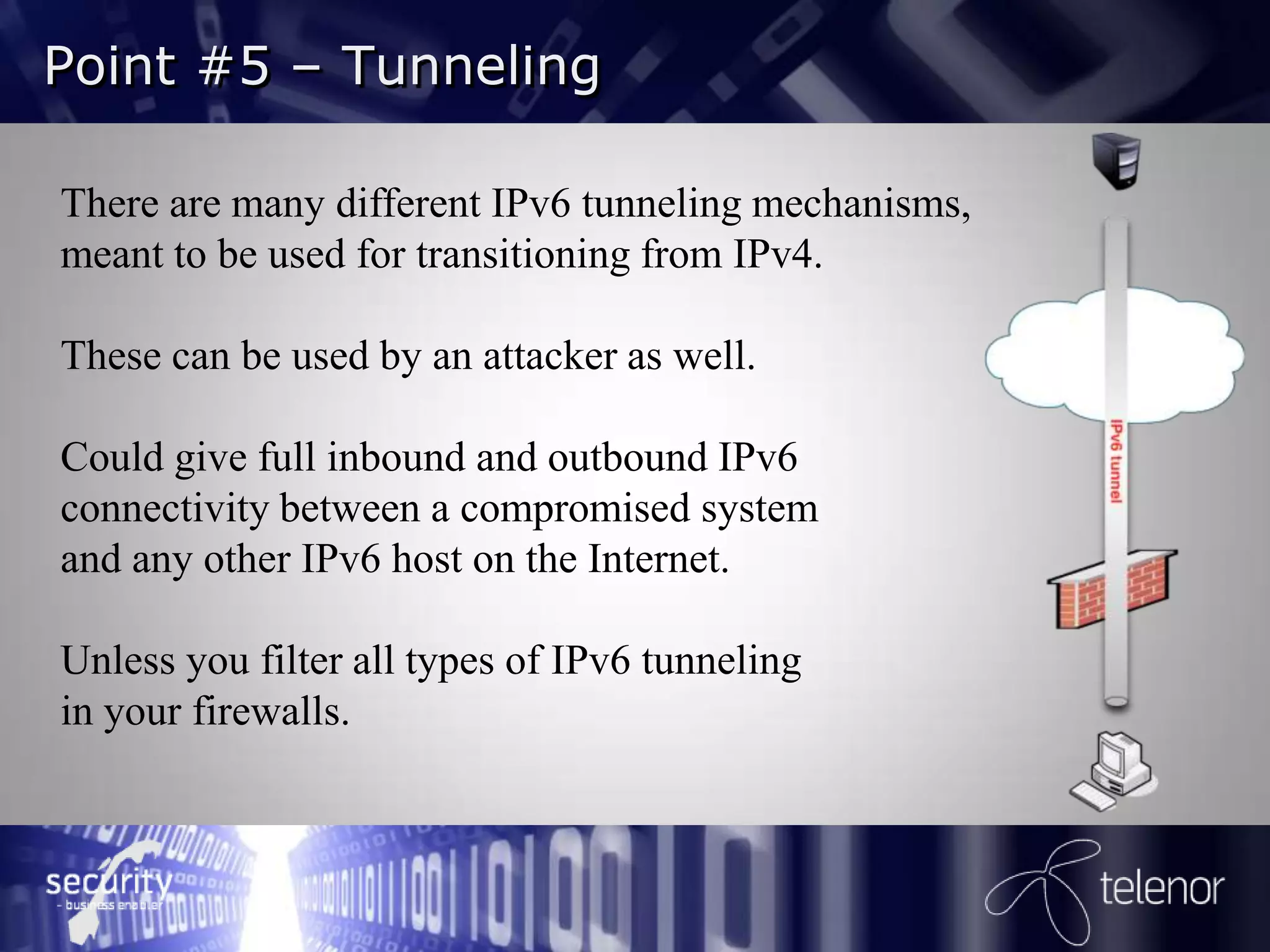
Henrik Strøm discusses IPv6 security from an attacker's perspective. He outlines 6 points on how attackers can exploit IPv6 vulnerabilities, including using IPv6 to bypass IPv4 access controls when on a local network, spoofing router advertisements to hijack traffic, using tunneling to enable inbound and outbound connectivity, and launching denial of service attacks. He recommends network administrators decide how to implement IPv6 security, monitor for IPv6 traffic, harden clients and servers, and filter all types of IPv6 tunneling. Further reading suggests there is still significant work needed on IPv6 firewalling and many IPv4 issues have been transferred to IPv6.