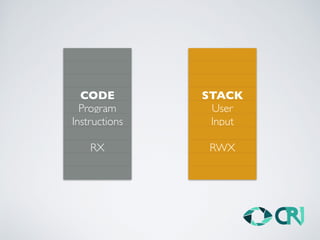
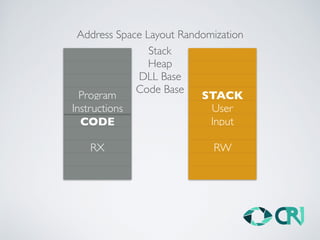
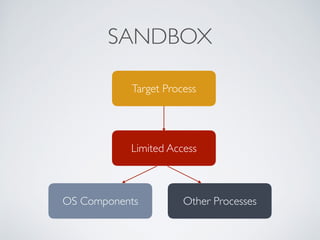
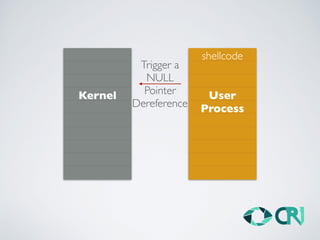
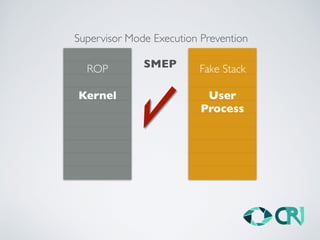
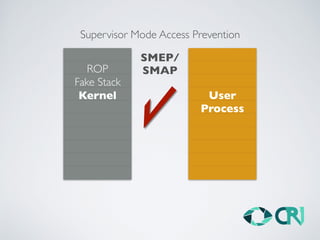
This document discusses the history and evolution of computer exploits from early vulnerabilities like stack overflows to modern techniques like return oriented programming and kernel exploits. It provides examples of major exploits from the Morris Worm in 1988 to recent zero-days. It also outlines numerous bypass techniques for defenses such as ASLR, sandboxes, and KASLR. The document examines the sophisticated Pegasus spyware and its developer, the Israeli cybersecurity firm NSO Group.