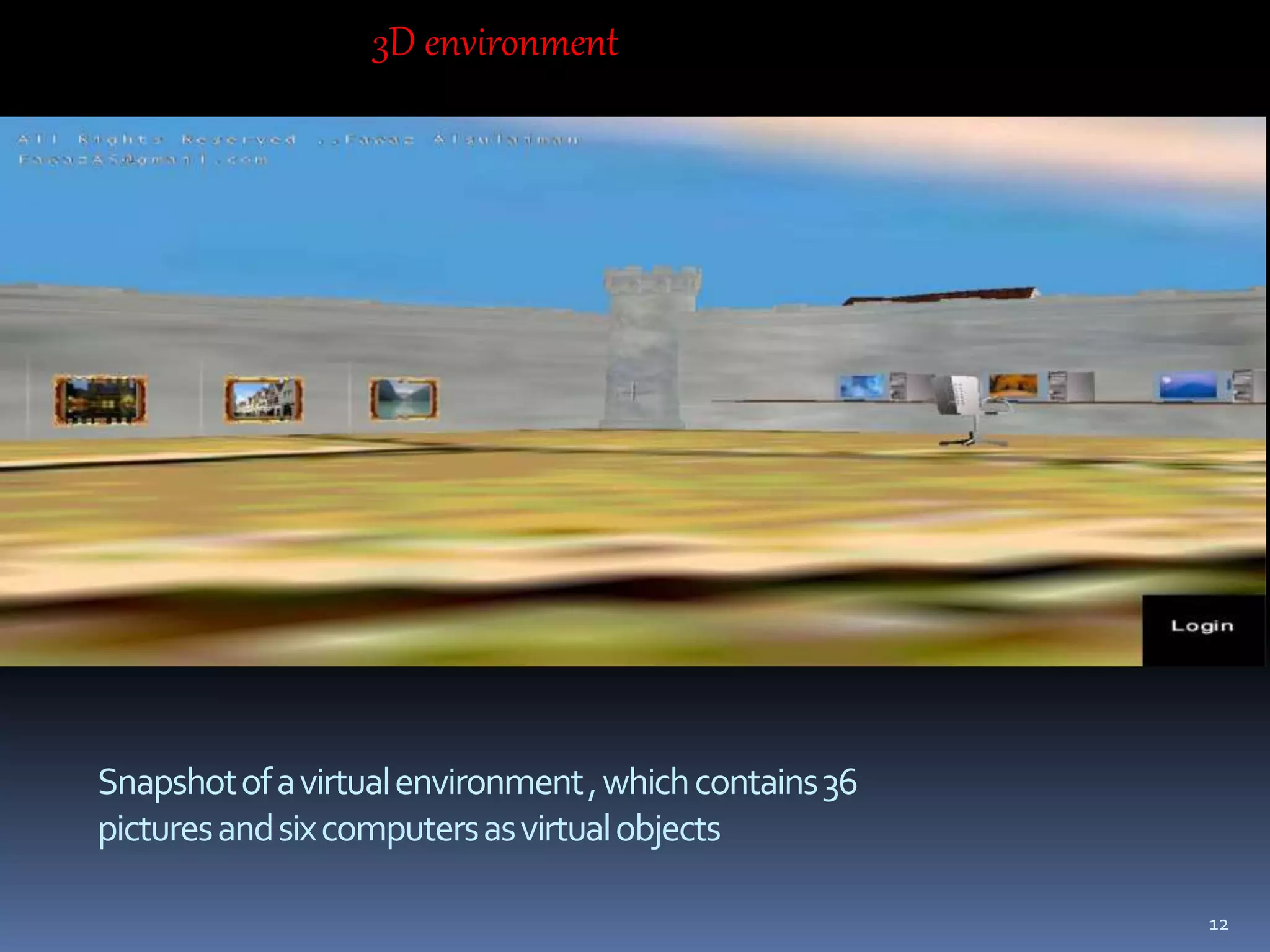
This document proposes a new 3D password authentication scheme. It combines existing authentication methods like passwords, PINs, biometrics into a 3D virtual environment. Users can navigate the environment and interact with virtual objects, with the sequence and combination of interactions forming their unique 3D password. The scheme aims to provide passwords that are easy to remember but difficult to guess. It discusses designing the virtual environment, selecting objects, and analyzing the security and potential attacks against 3D password schemes.