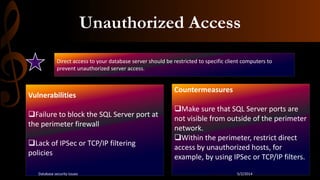
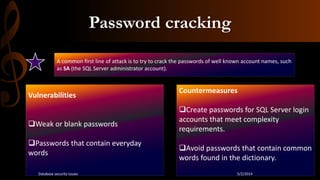
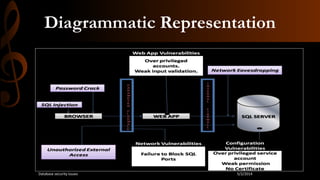
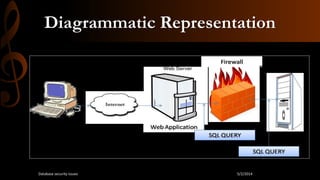
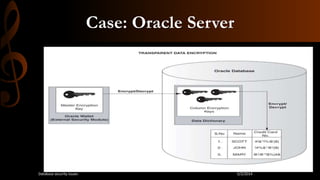
This document discusses database security. It begins by stating that as threats to databases have increased, security of databases is increasingly important. It then defines database security as protecting the confidentiality, integrity, and availability of database data. The document outlines some common database security threats like SQL injection, unauthorized access, password cracking, and network eavesdropping. It then discusses some methods of securing databases, including through firewalls and data encryption. Firewalls work by filtering database traffic according to rules, while data encryption scrambles data so it can only be read by authorized users. The document stresses the importance of restricting database access to authorized users and applications.