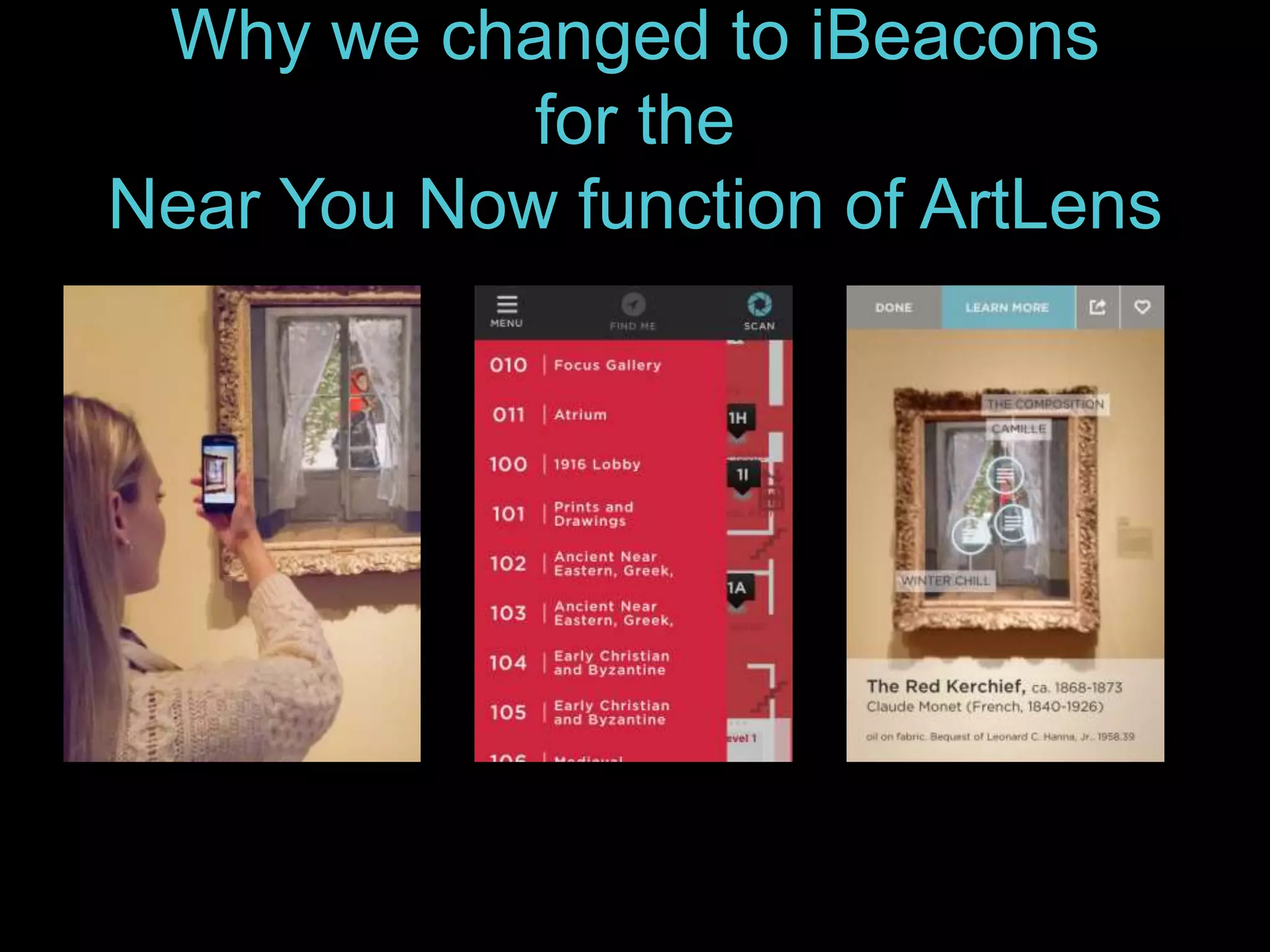
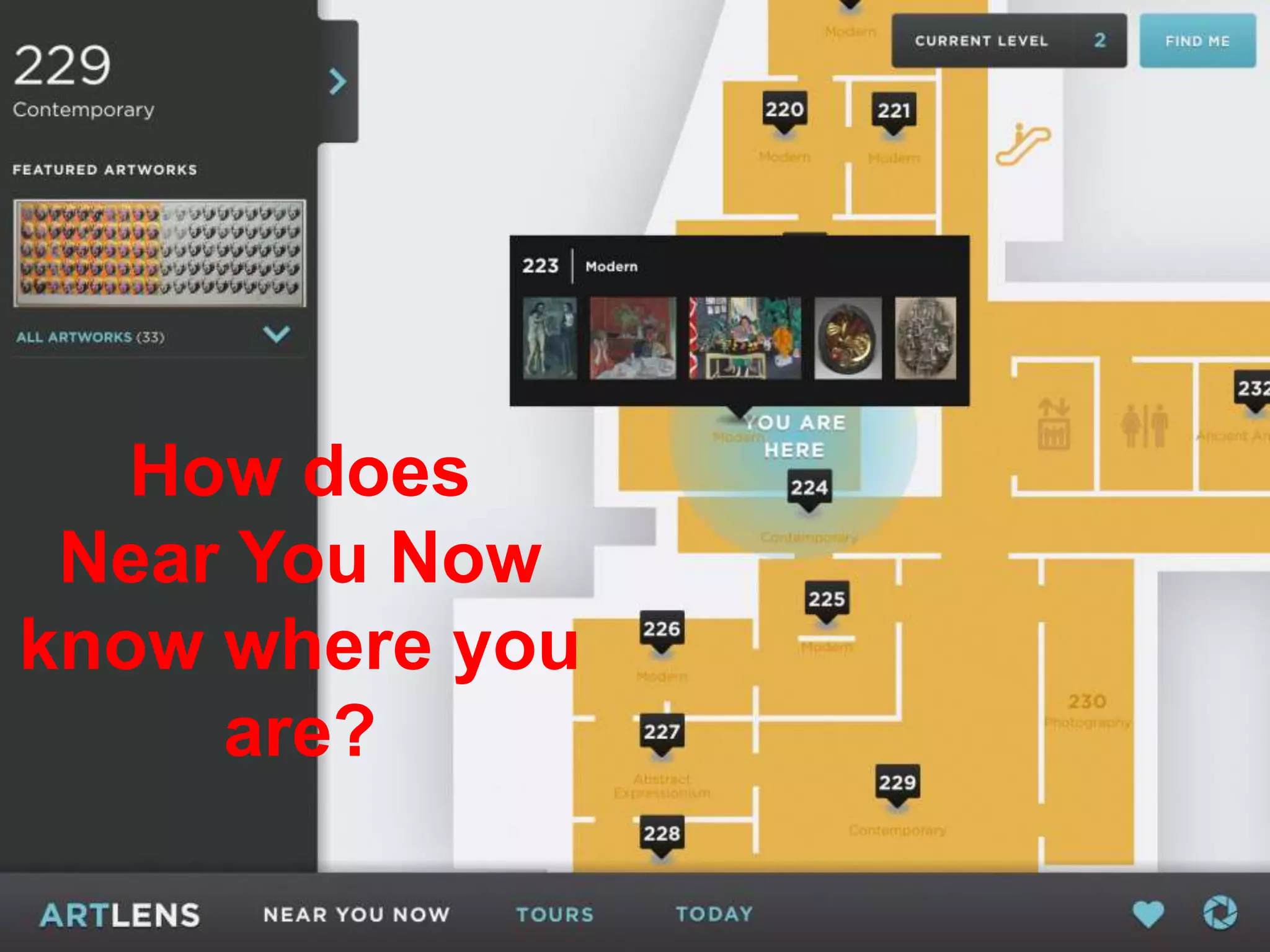
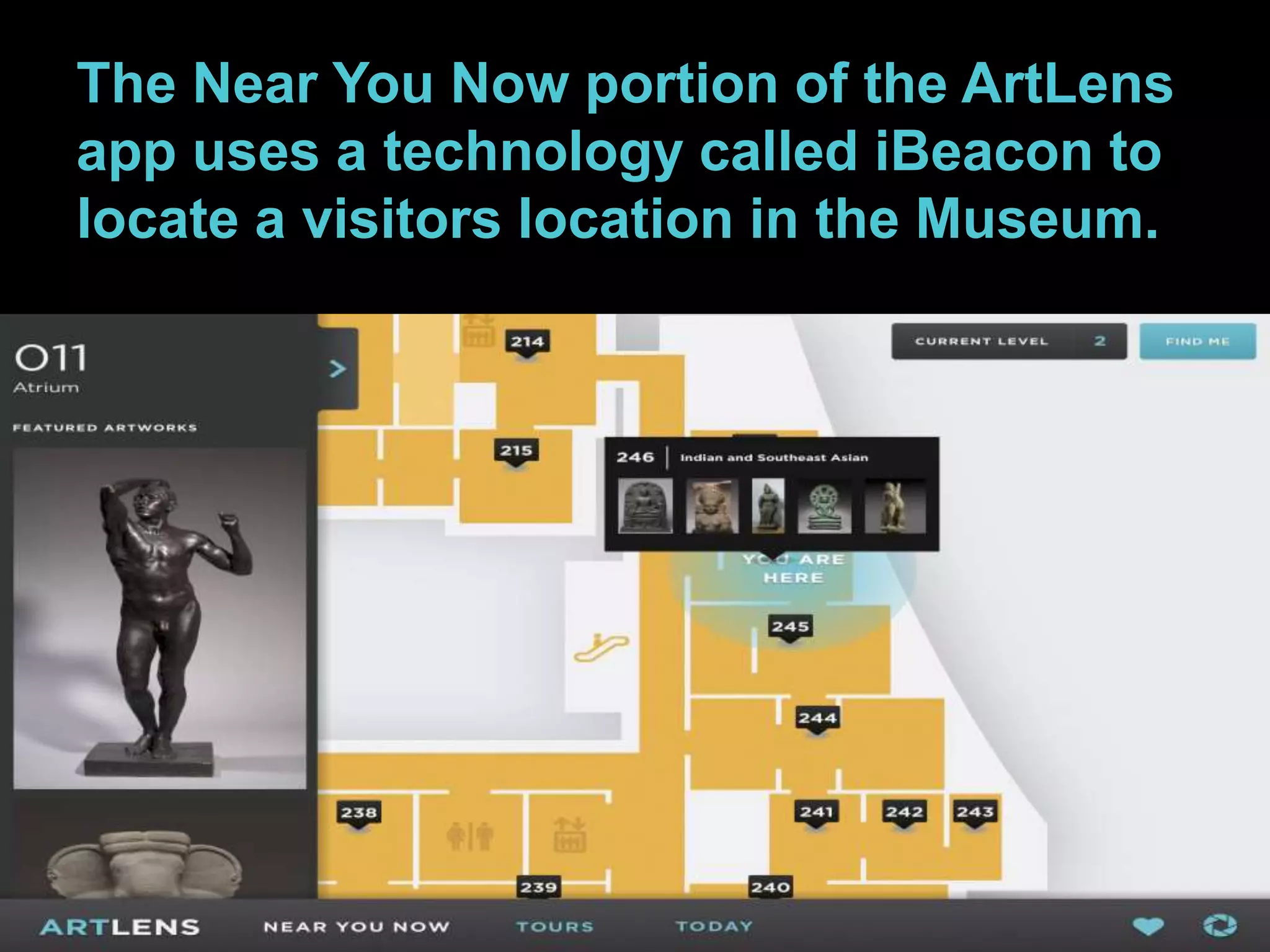
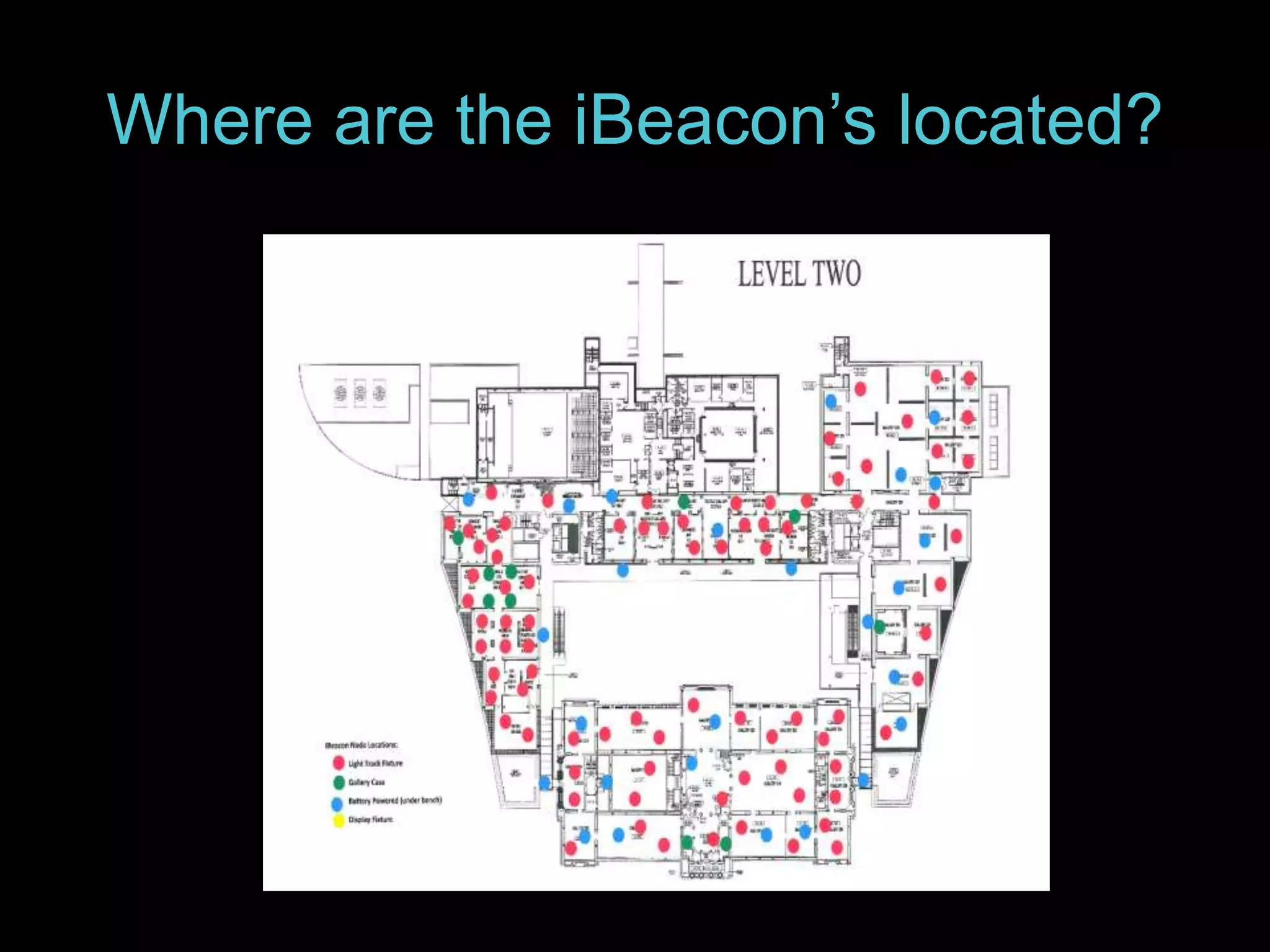
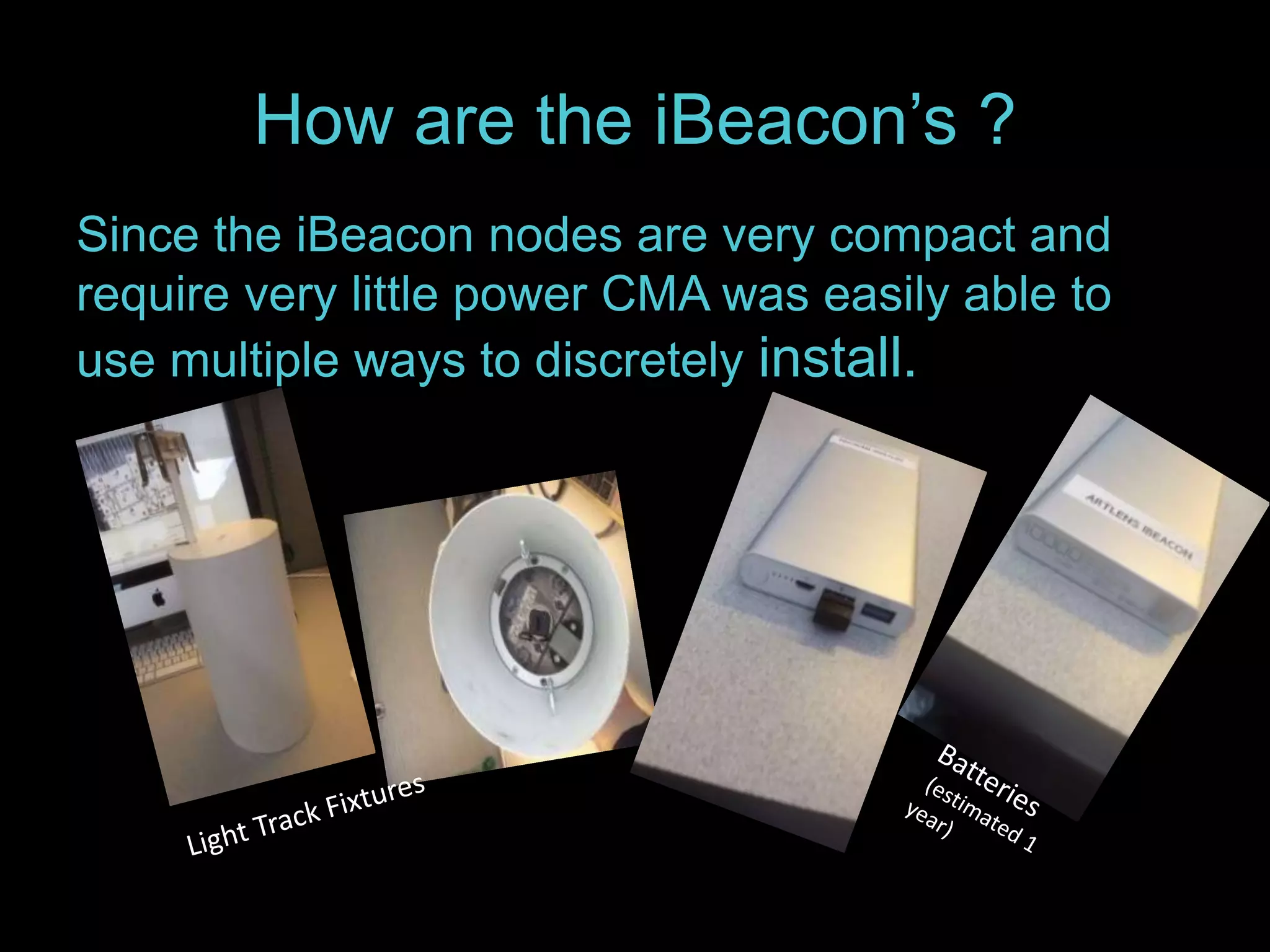
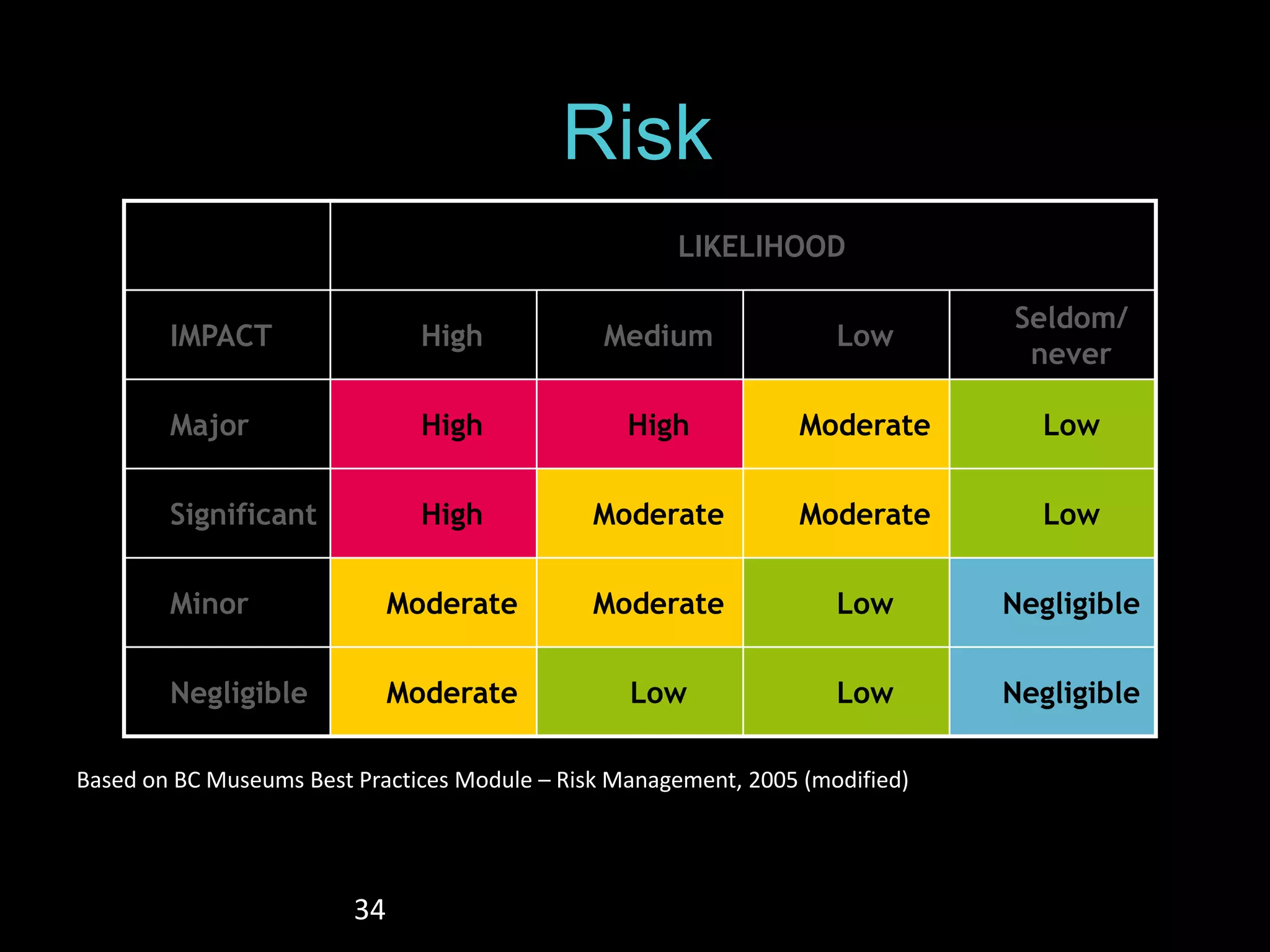
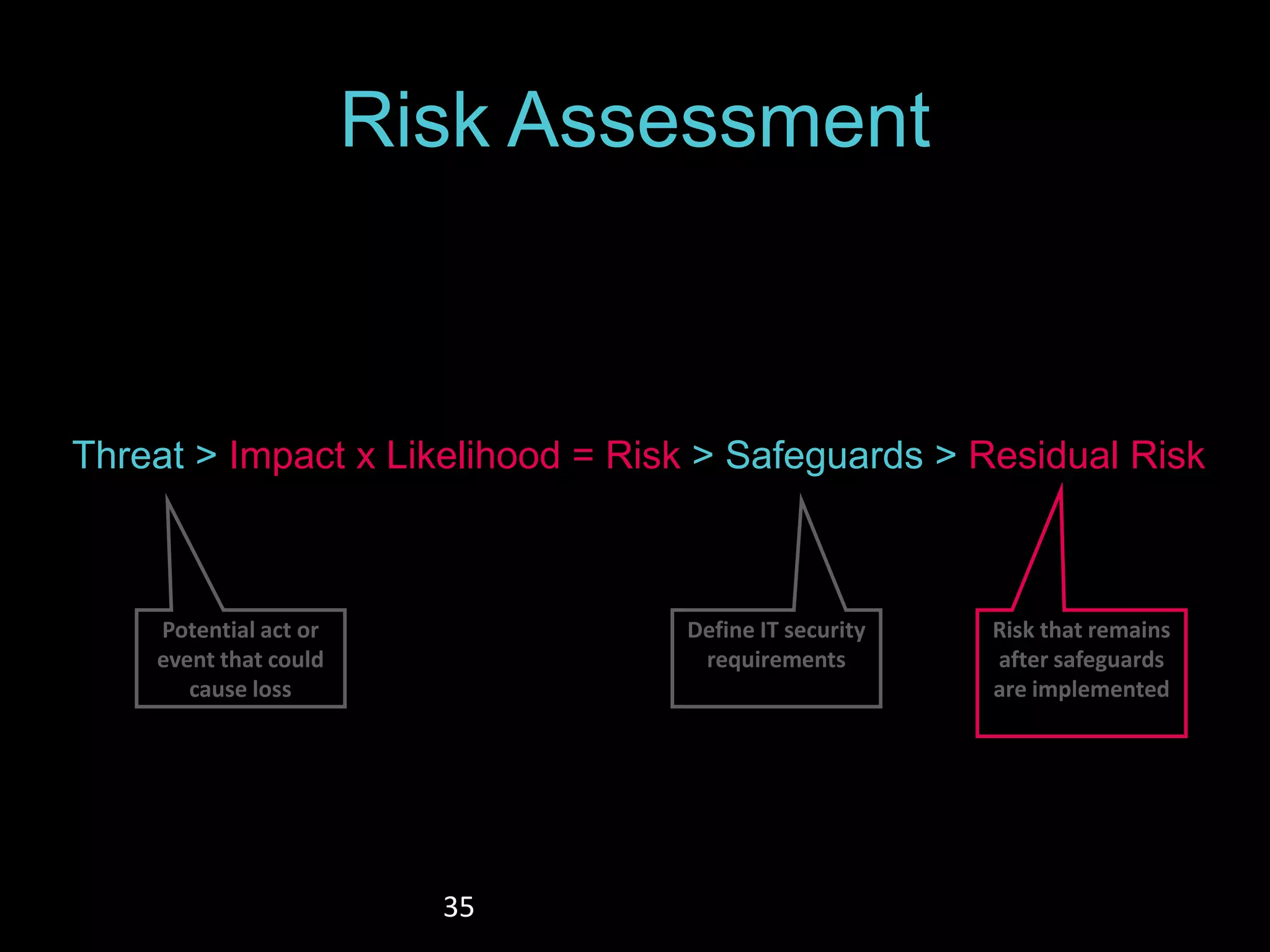
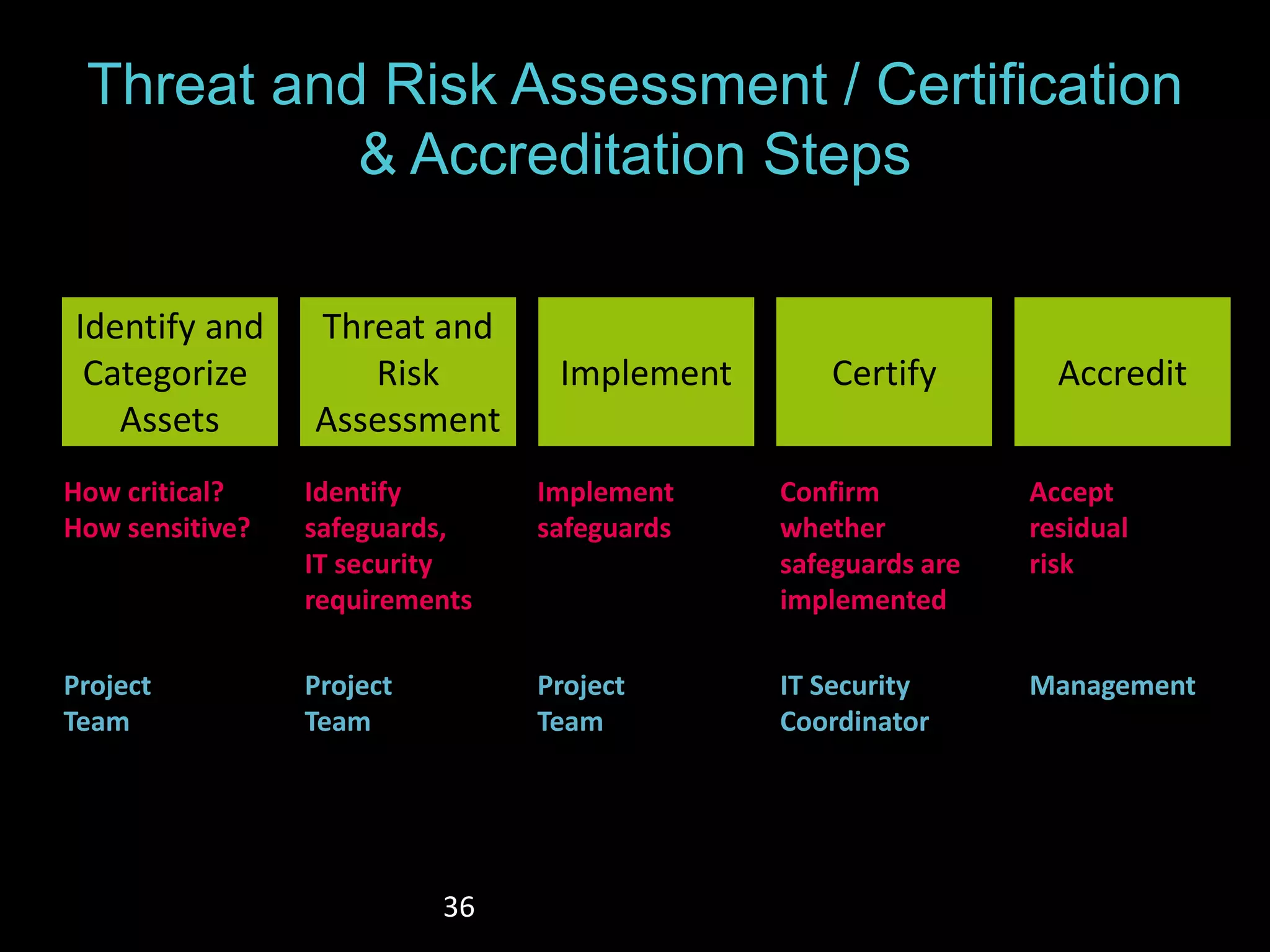
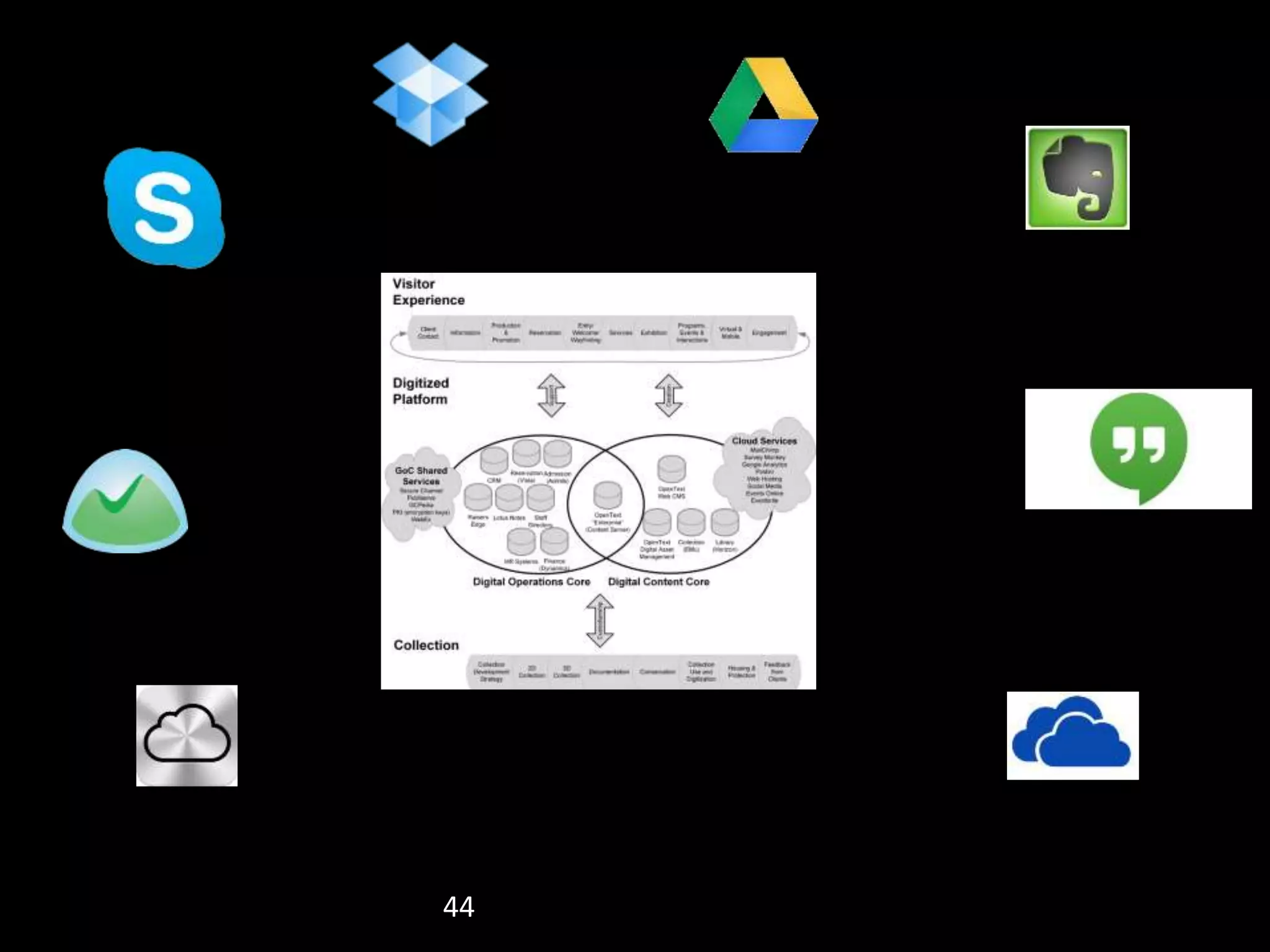
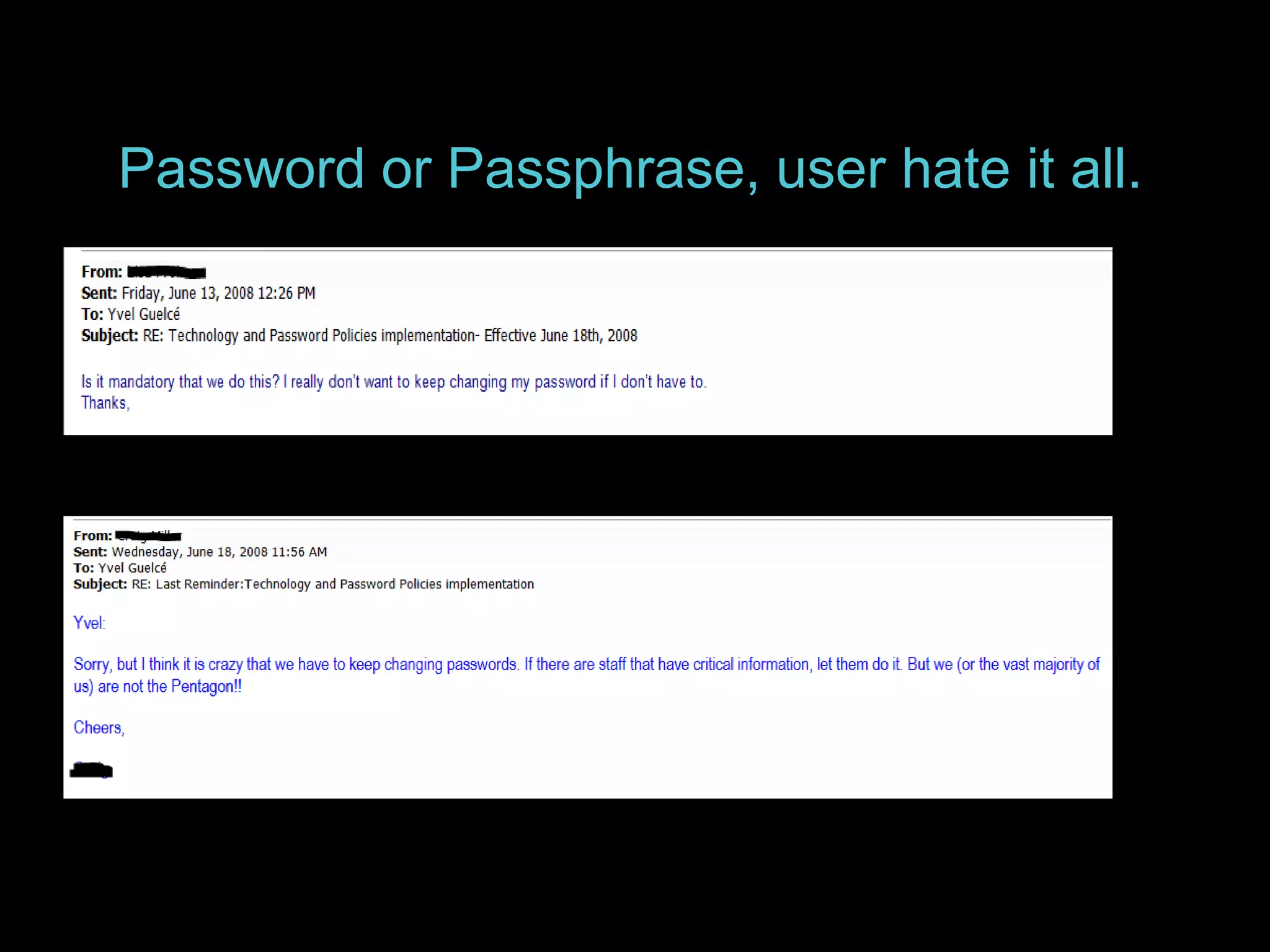
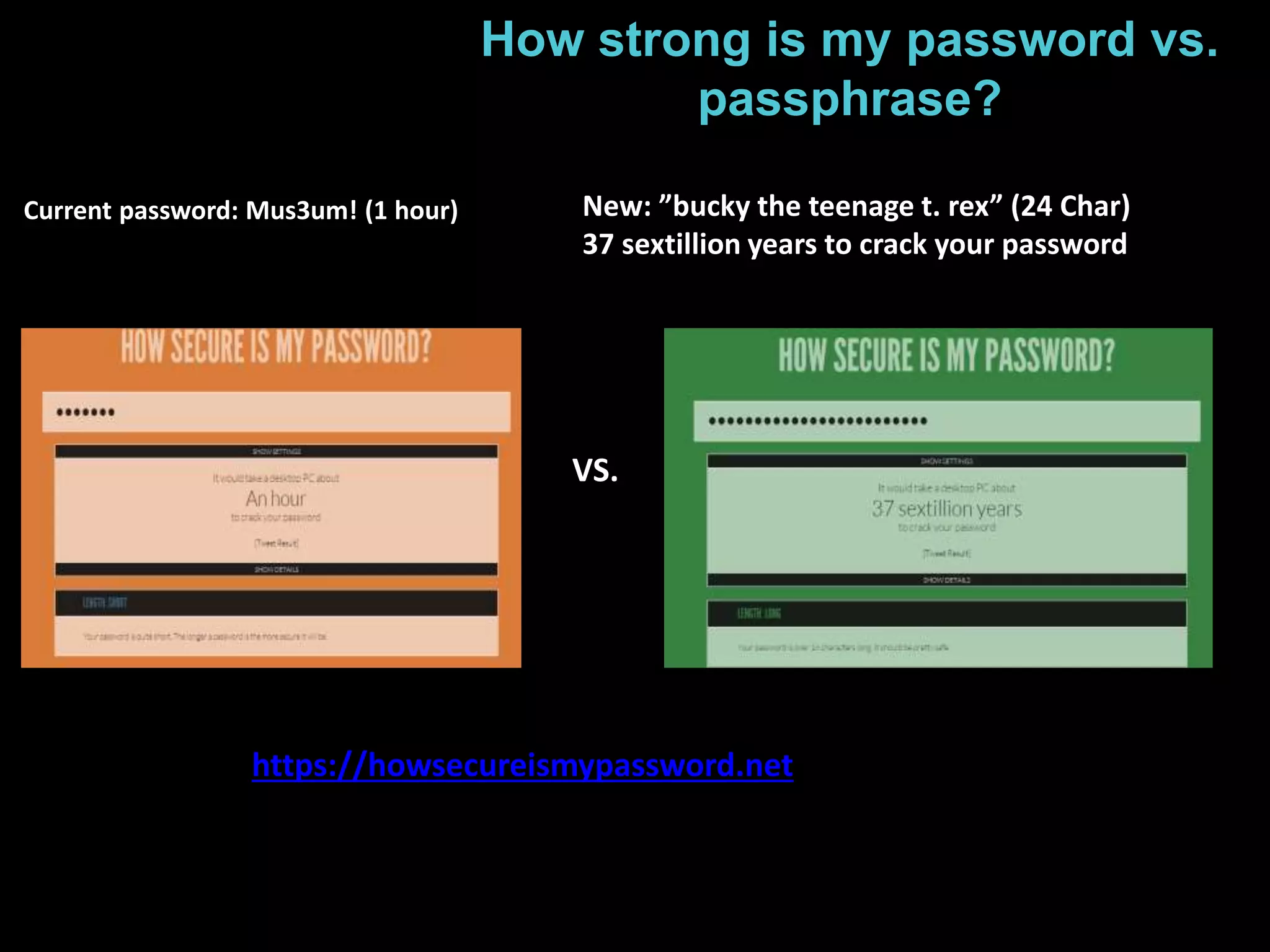
The document details the advantages of using cloud archival repositories, emphasizing cost savings and adherence to best practices. It also discusses the implementation of iBeacon technology in the ArtLens app for enhanced visitor location tracking in museums, along with background on the necessary systems and compliance with PCI standards for payment security. Additionally, it outlines password management strategies, suggesting the use of passphrases to increase security while maintaining memorability.