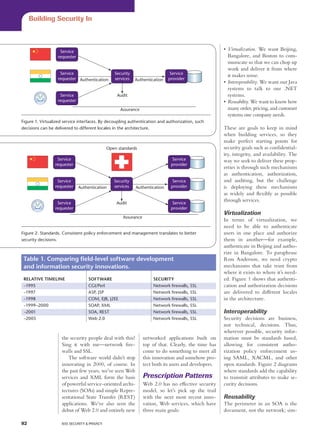
This document discusses how information security has failed to evolve with advances in software development and web applications. Specifically:
- Security approaches like firewalls and SSL have not changed meaningfully in over 13 years, despite huge growth in web integration, distributed applications, and reliance on web apps for business functions.
- As software evolved to integrate disparate systems using SOAP and XML, security did not develop models for authentication, authorization, or confidentiality for these new programming models.
- For security to progress, it needs to learn from software development practices and priorities like virtualization, interoperability, and reusability - and deliver properties like authentication and authorization as widely deployed services.