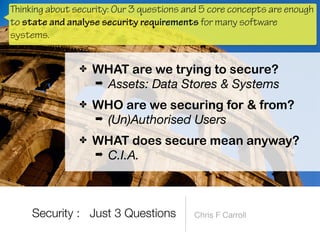
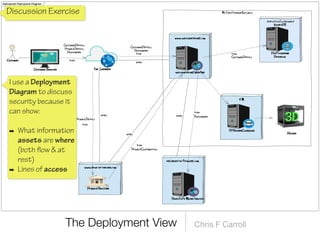
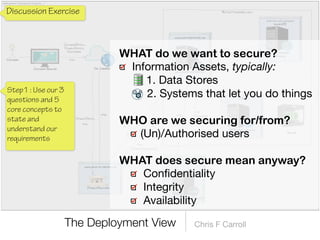
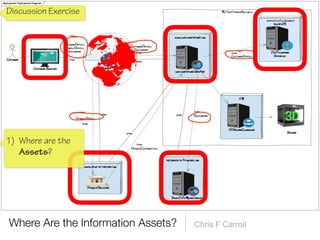
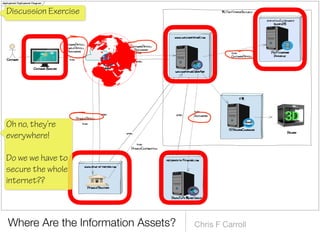
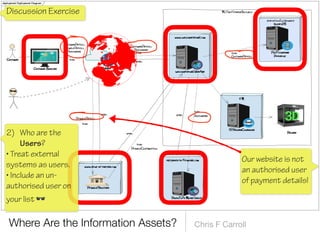
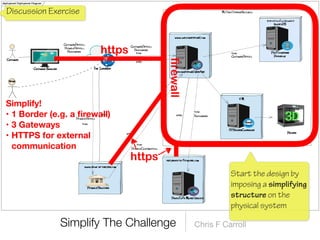
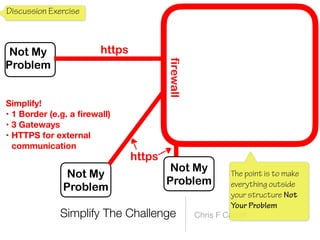
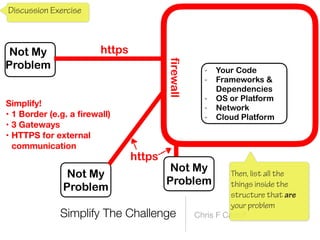
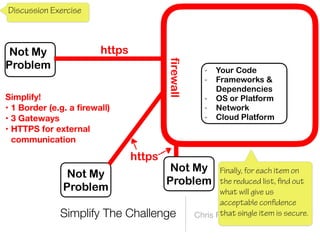
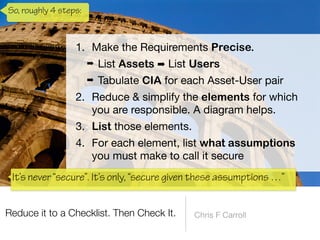
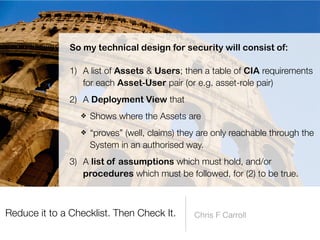
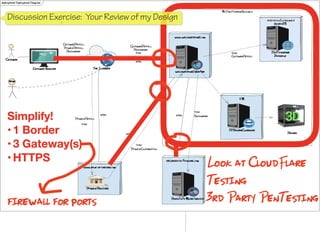
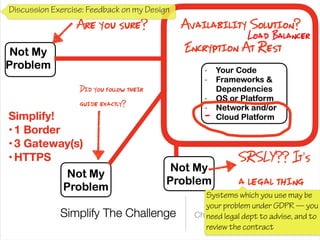
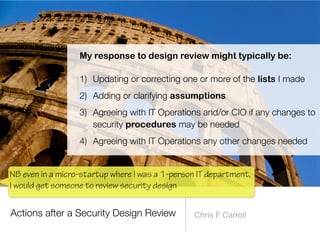
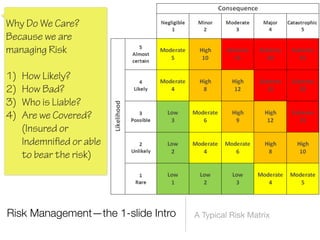
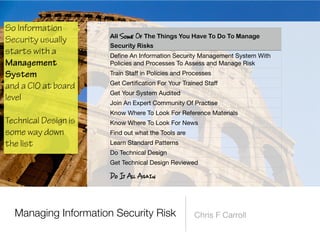
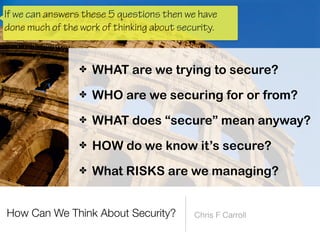
The document discusses a framework for thinking about security in software architecture, emphasizing the need to ask critical questions regarding what needs to be secured, who the security is for, and what 'secure' means in terms of confidentiality, integrity, and availability. It also outlines the importance of a common vocabulary and highlights the continuous nature of managing security, suggesting the establishment of an information security management system for ongoing compliance and risk management. The author advocates for a structured approach to identify and protect information assets while simplifying the design process.