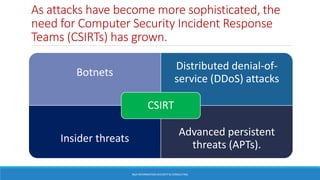
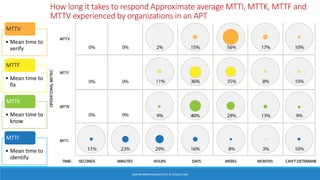
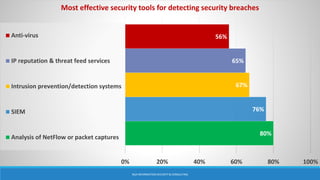
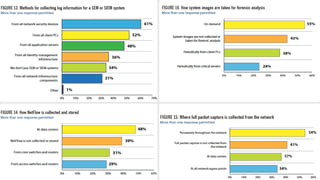
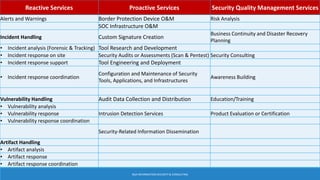
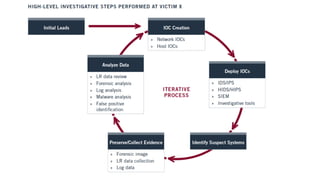
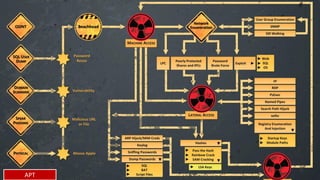
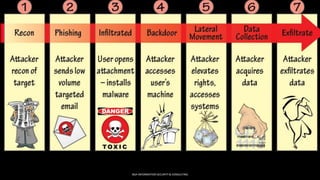
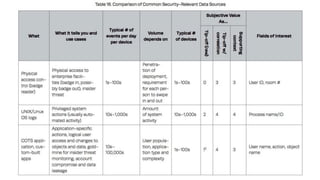
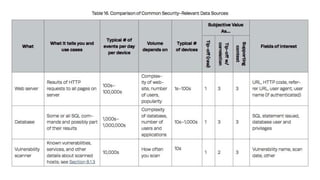
As attacks have become more sophisticated, the need for Computer Security Incident Response Teams (CSIRTs) has grown to address challenges like botnets, distributed denial-of-service (DDoS) attacks, insider threats, and advanced persistent threats (APTs). The presentation discusses best practices for creating a CSIRT, including obtaining management support, determining a strategic plan, designing a vision, implementation, and evaluating effectiveness. It also covers Security Operations Centers (SOCs), their mission to prevent, monitor, detect, respond to, and report on cybersecurity incidents, and best practices for establishing an SOC.
















![References
[1] West-Brown, Moira J.; Stikvoort, Don; & Kossakowski, Klaus-Peter. Handbook for Computer Security Incident Response
Teams (CSIRTs) (CMU/SEI-98-HB-001). Pittsburgh, PA: Software Engineering Institute, Carnegie Mellon University, 1998.
Note that this document was superceded by the 2nd edition (CMU/SEI-2003-HB-002), published in April 2003.
[2] Kossakowski, Klaus-Peter. Information Technology Incident Response Capabilities. Hamburg: Books on Demand, 2001
(ISBN: 3-8311-0059-4).
[3] Kossakowski; Klaus-Peter & Stikvoort, Don. A Trusted CSIRT Introducer in Europe. Amersfoort, Netherlands:
M&I/Stelvio, February, 2000.
[4] Exposing One of China’s Cyber Espionage Units http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf
[5] M-Trends® 2013: Attack the Security Gap http://pages.fireeye.com/MF0D0O0PDVp6y106k0TI0B3
[6] M-Trends® 2011: When Prevention Fails http://www.mandiant.com/assets/PDF_MTrends_2011.pdf
[7] M-Trends® 2012: An Evolving Threat http://www.mandiant.com/assets/PDF_MTrends_2012.pdf
[8] Cyber Security Incident Response 2014 http://www.lancope.com/files/documents/Industry-Reports/Lancope-
Ponemon-Report-Cyber-Security-Incident-Response.pdf
[9] Create a CSIRT https://www.cert.org/incident-management/products-services/creating-a-csirt.cfm
[10] CSIRT Services list from CERT/CC https://www.enisa.europa.eu/activities/cert/support/guide/appendix/csirt-services
BGA INFORMATION SECURITY & CONSULTING](https://image.slidesharecdn.com/b841414d-5765-480d-8256-ef02c1bca729-150929145705-lva1-app6891/85/CSIRT_16_Jun-51-320.jpg)
![References
[1] Wikimedia Foundation, Inc., “Advanced Persistent Threat,” 3 Feb 2014. [Online]. Available:
http://en.wikipedia.org/wiki/Advanced_persistent_threat. [Accessed 13 Feb 2014].
[2] R. G. Bace, Intrusion Detection, Indianapolis: Macmillan Technical Publishing, 2000.
[3] G. Killcrece, K.-P. Kossakowski, R. Ruefle and M. Zajicek, “State of the Practice of Computer Security Incident Response
Teams (CSIRTs),” October 2003. [Online]. Available: http://resources.sei.cmu.edu/library/asset-view.cfm?assetID=6571.
[Accessed 13 Feb 2014].
[4] Killcrece, Georgia; Kossakowski, Klaus-Peter; Ruegle, Robin; Zajicek, Mark, “Organizational Models for Computer
Security Incident Response Teams,” December 2003. [Online]. Available: www.cert.org/archive/pdf/03hb001.pdf.
[Accessed 13 Feb 2014].
[5] S. Northcutt, Network Intrusion Detection (3rd Edition), Indianapolis: New Riders Publishing, 2002.
[6] T. Parker, E. Shaw, E. Stroz, M. G. Devost and M. H. Sachs, Cyber Adversary Characterization: Auditing the Hacker Mind,
Rockland, MA: Syngress Publishing, Inc., 2004.
[7] L. Spitzner, Honeypots: Tracking Hackers, Addison-Wesley Professional, 2002.
[8] M. J. West-Brown, D. Stikvoort, K.-P. Kossakowski, G. Killcrece, R. Ruefle and M. Zajicekm, “Handbook for Computer
Security Incident Response Teams (CSIRTs),” April 2003. [Online]. Available: http://resources.sei.cmu.edu/library/asset-
view.cfm?assetid=6305. [Accessed 13 Feb 2014].
BGA INFORMATION SECURITY & CONSULTING](https://image.slidesharecdn.com/b841414d-5765-480d-8256-ef02c1bca729-150929145705-lva1-app6891/85/CSIRT_16_Jun-52-320.jpg)

