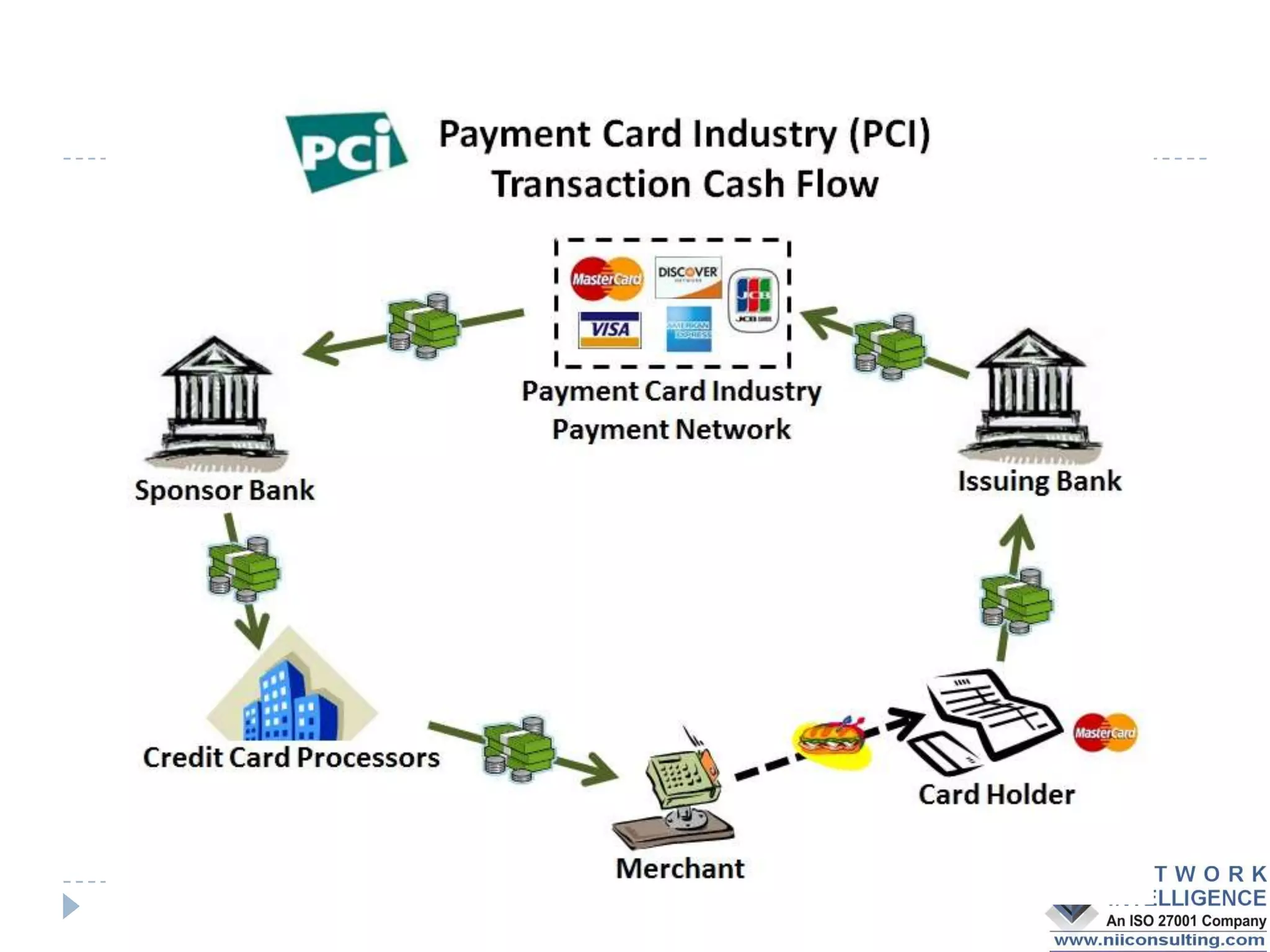
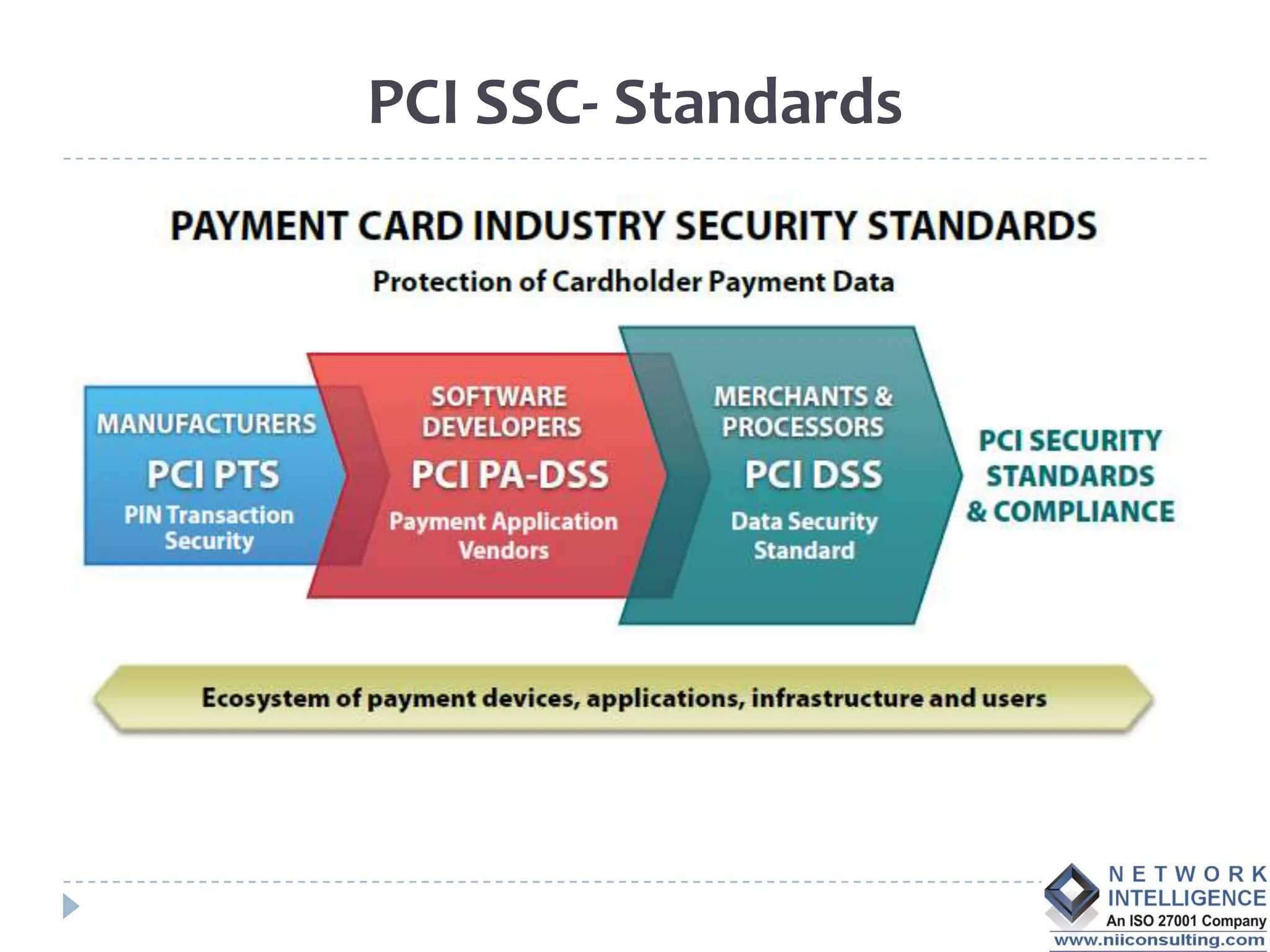
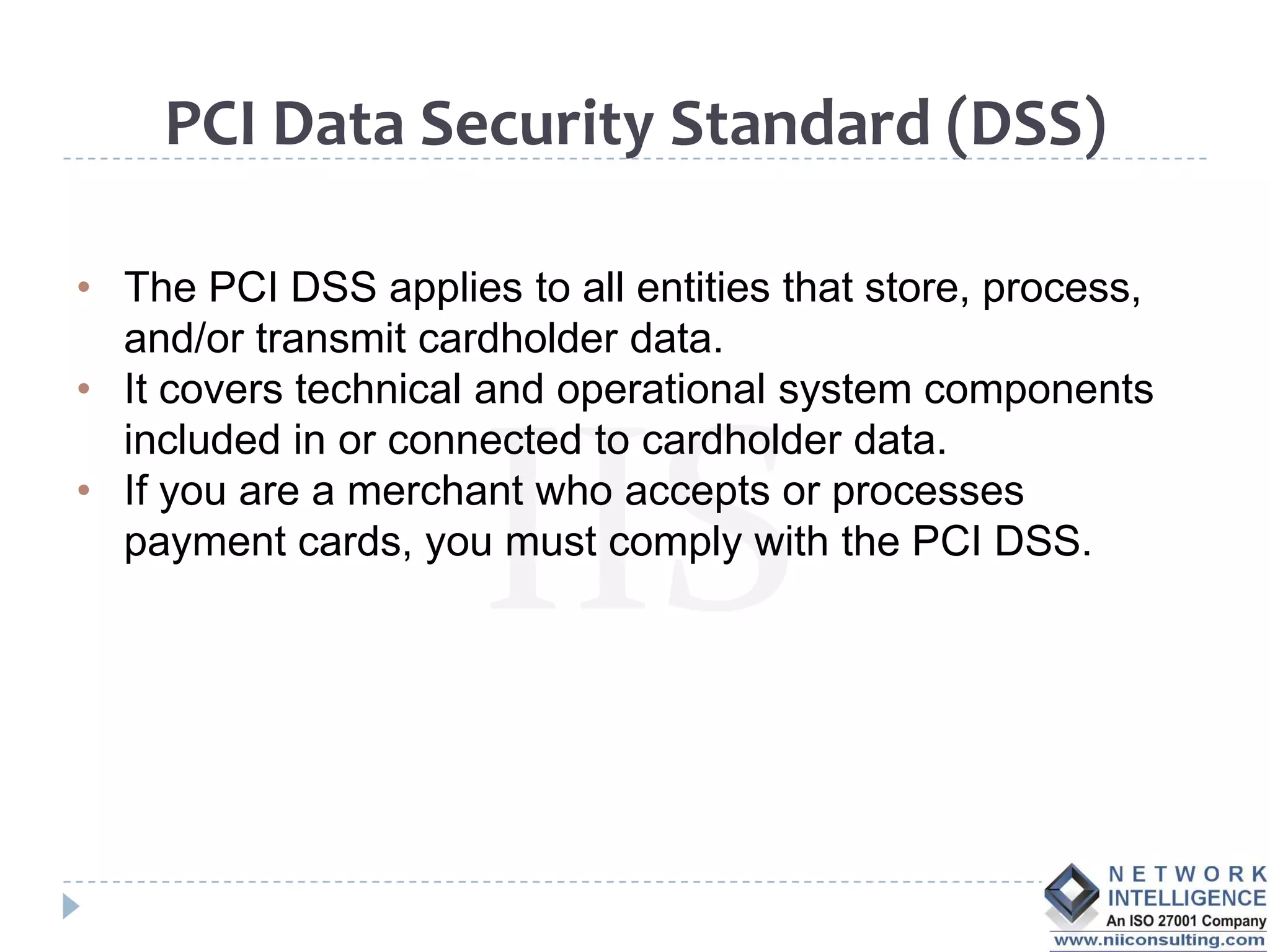
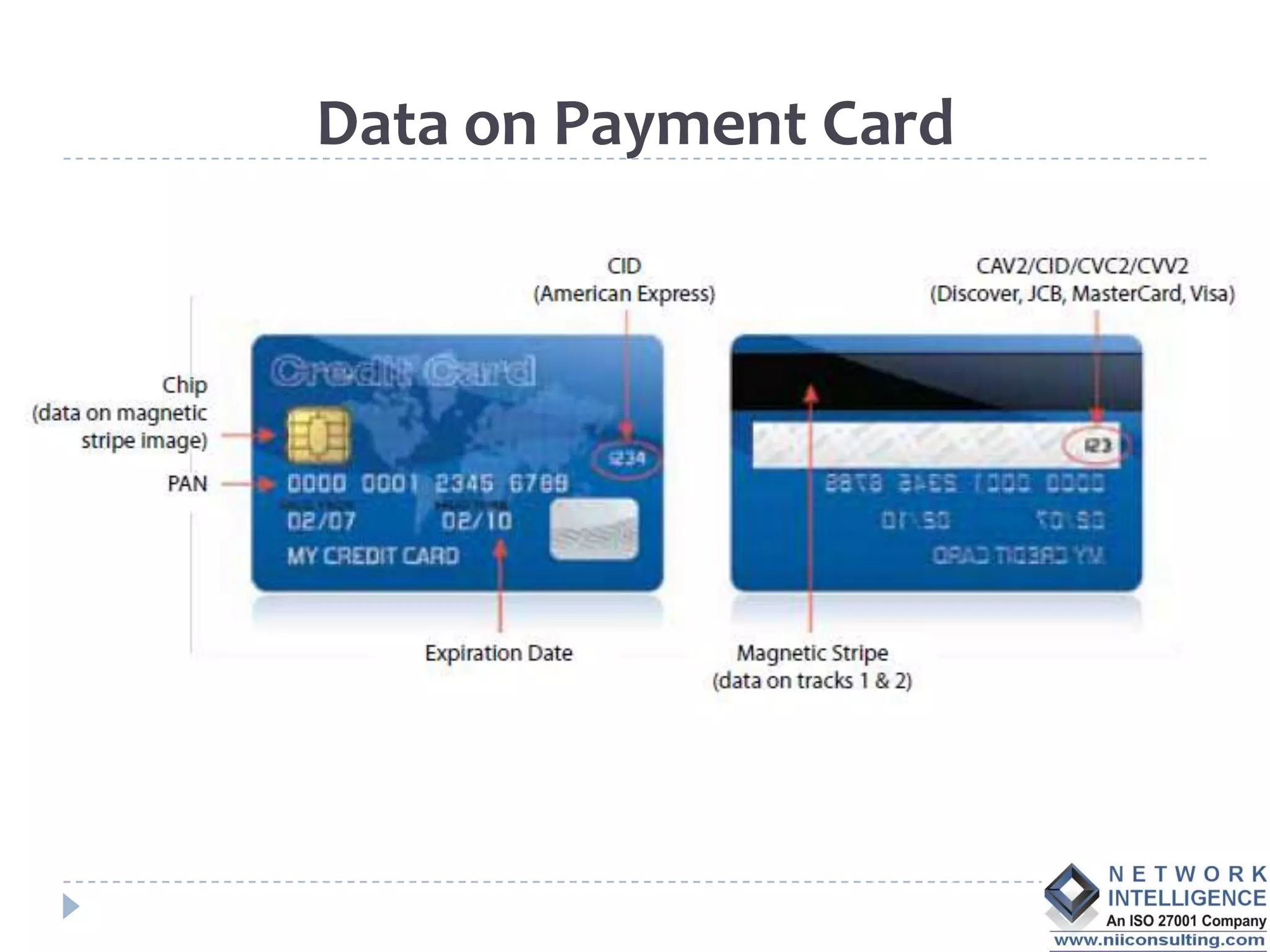
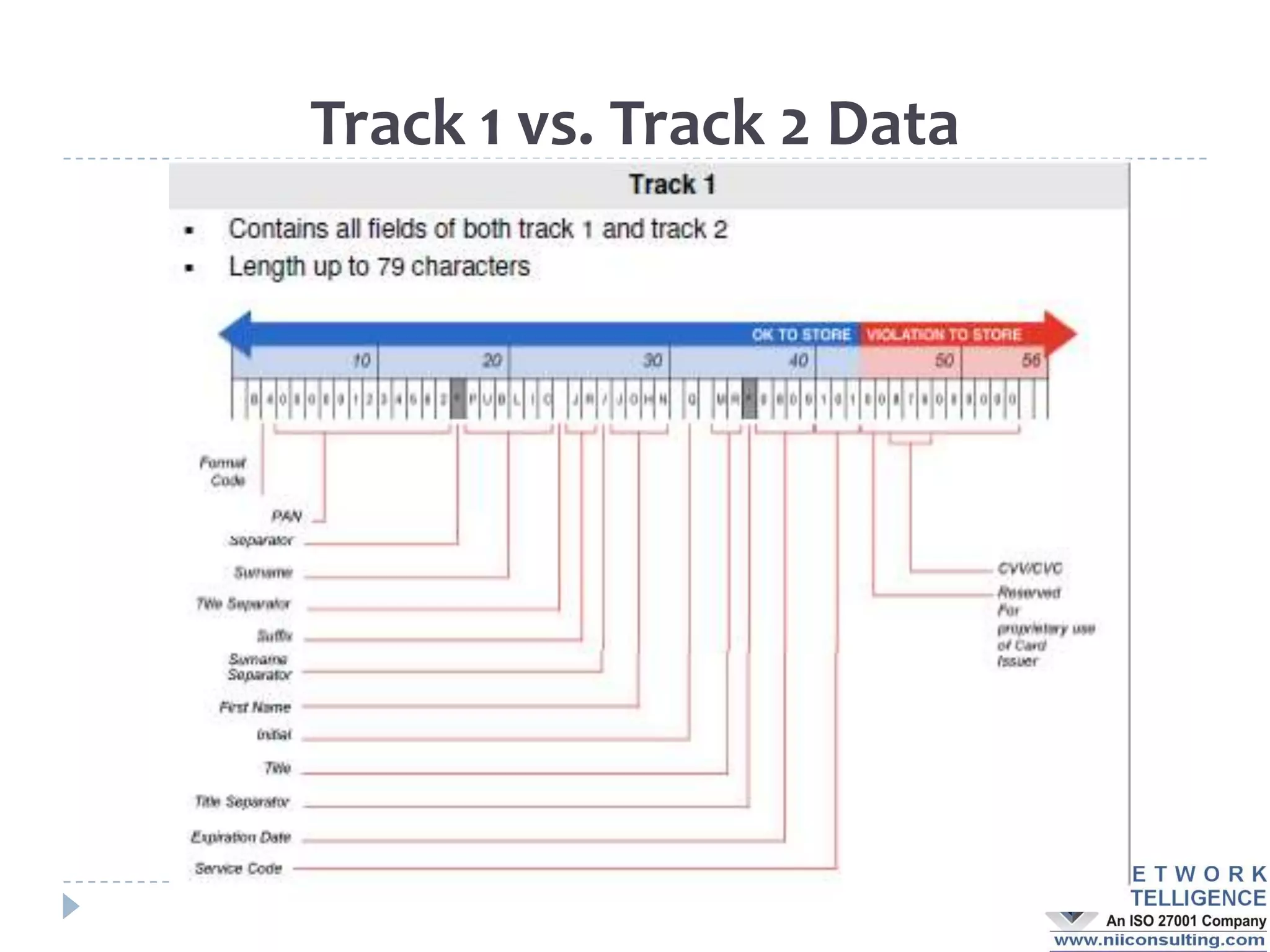
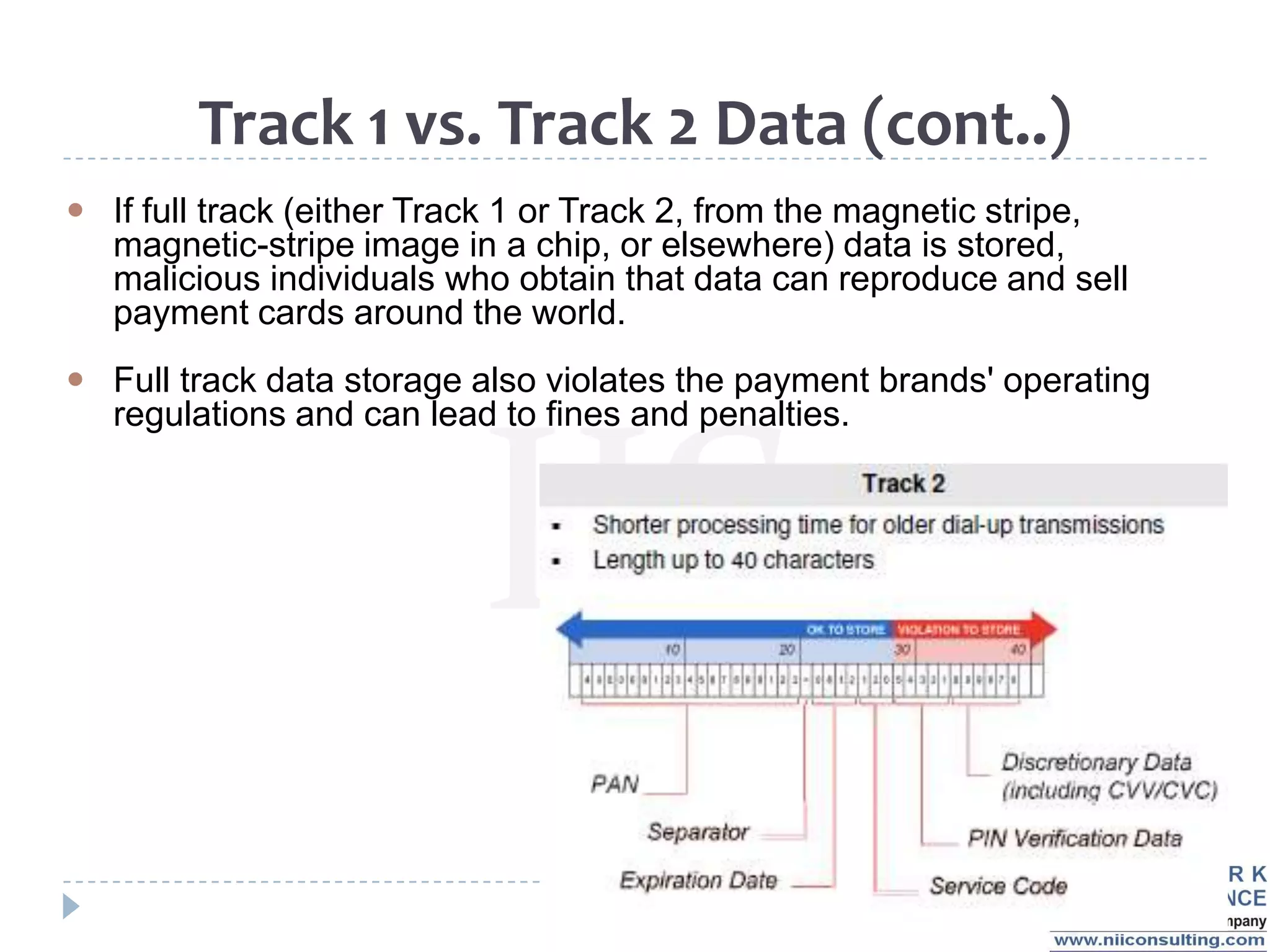
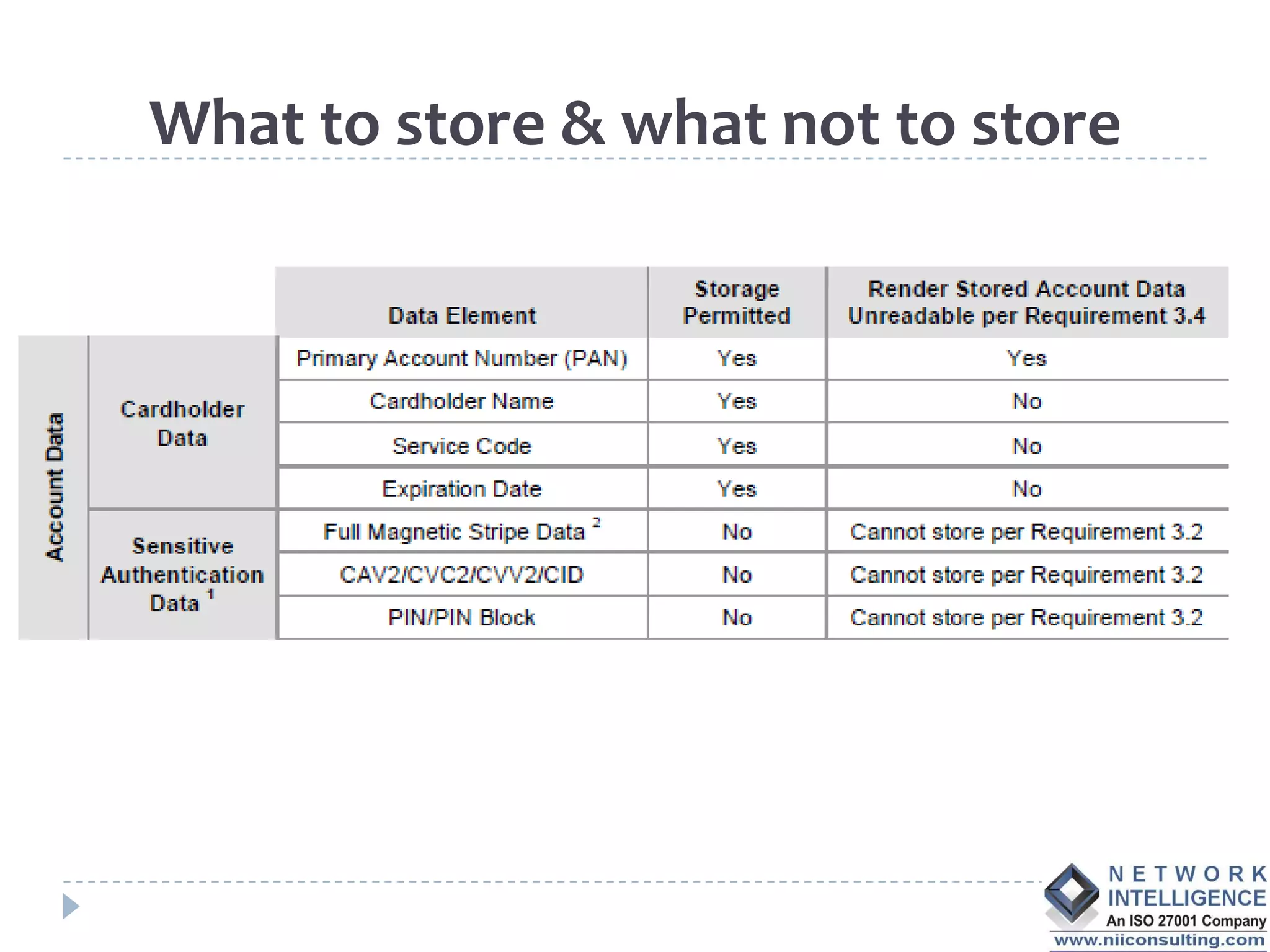
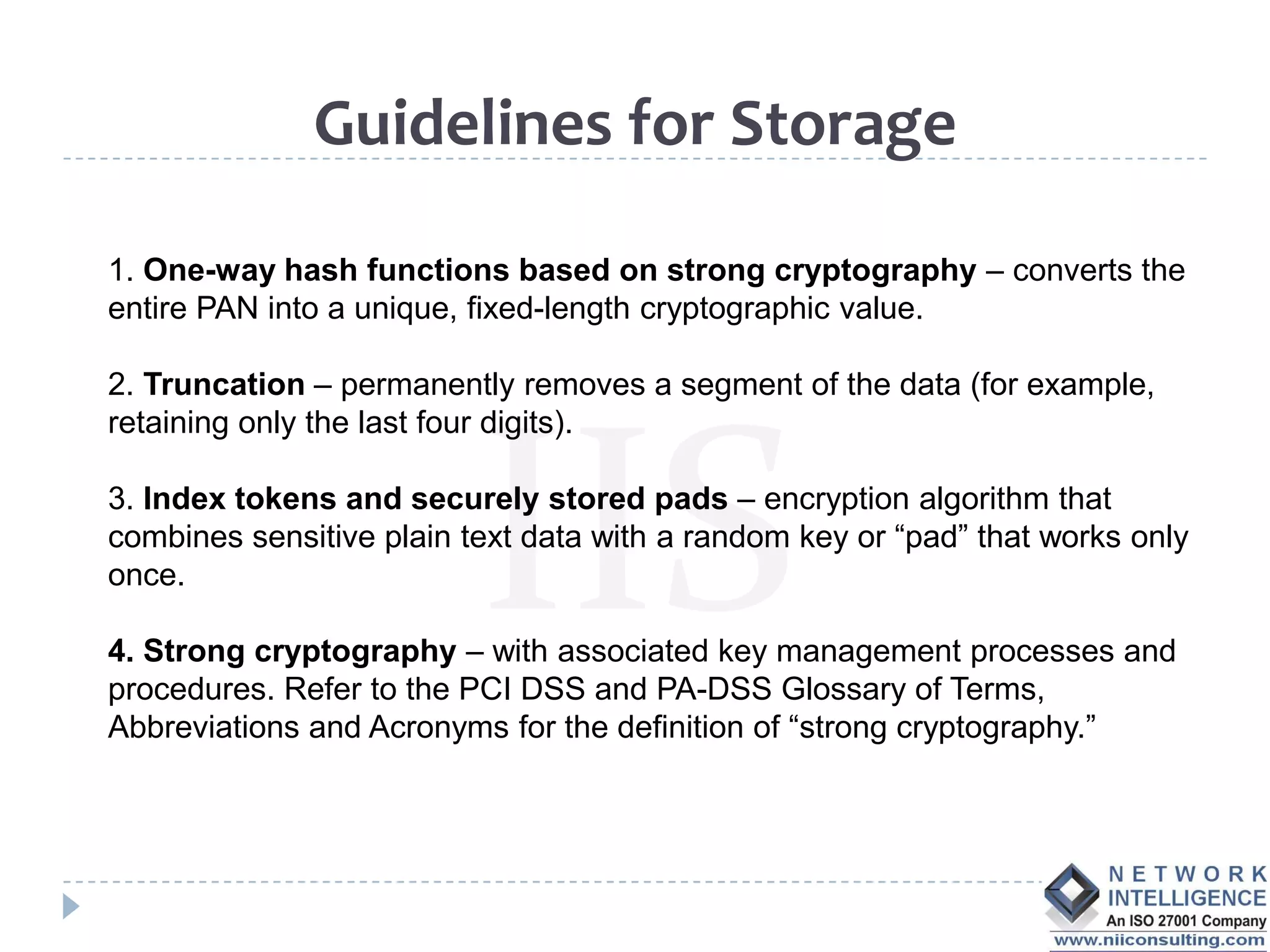
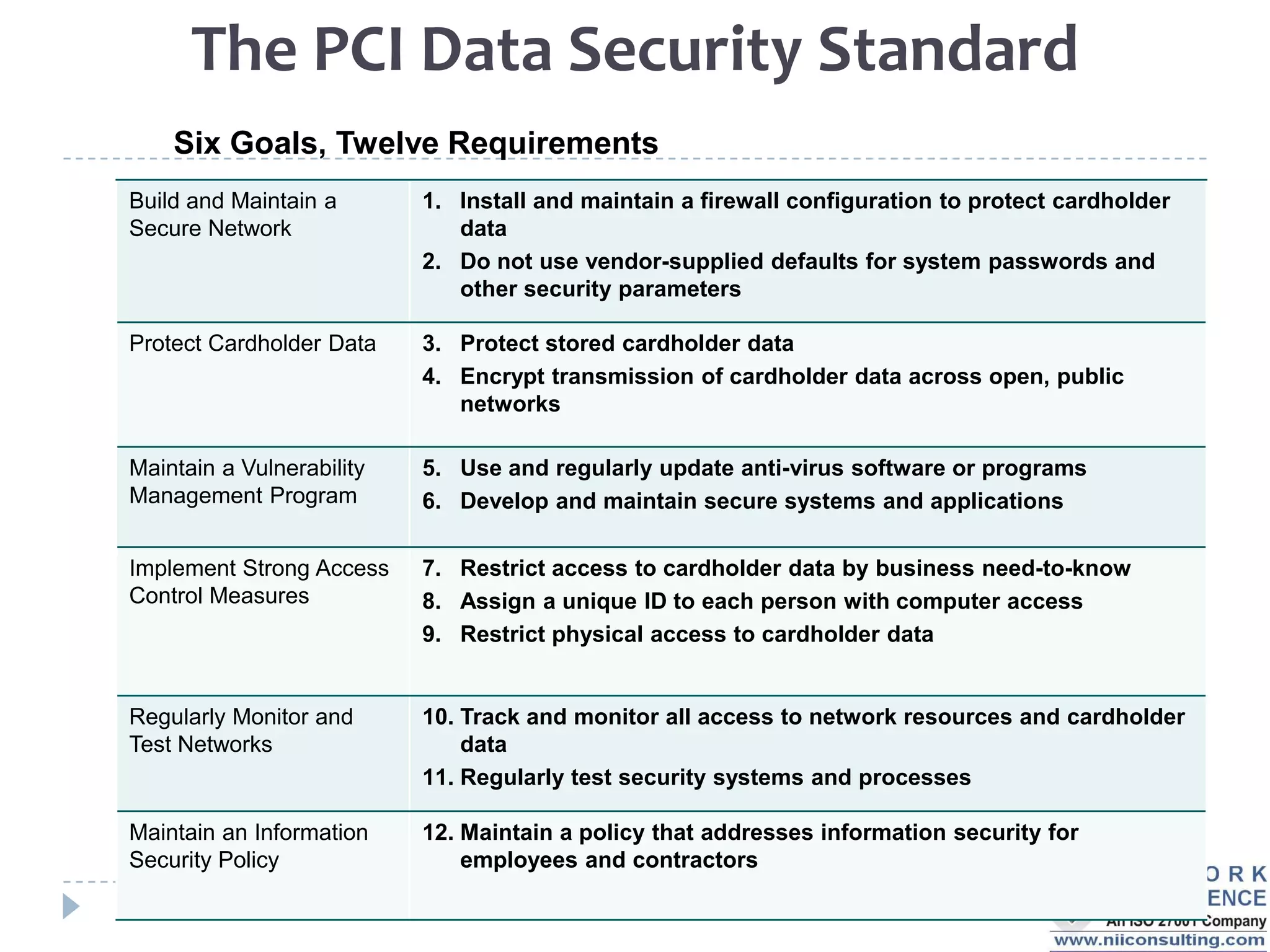
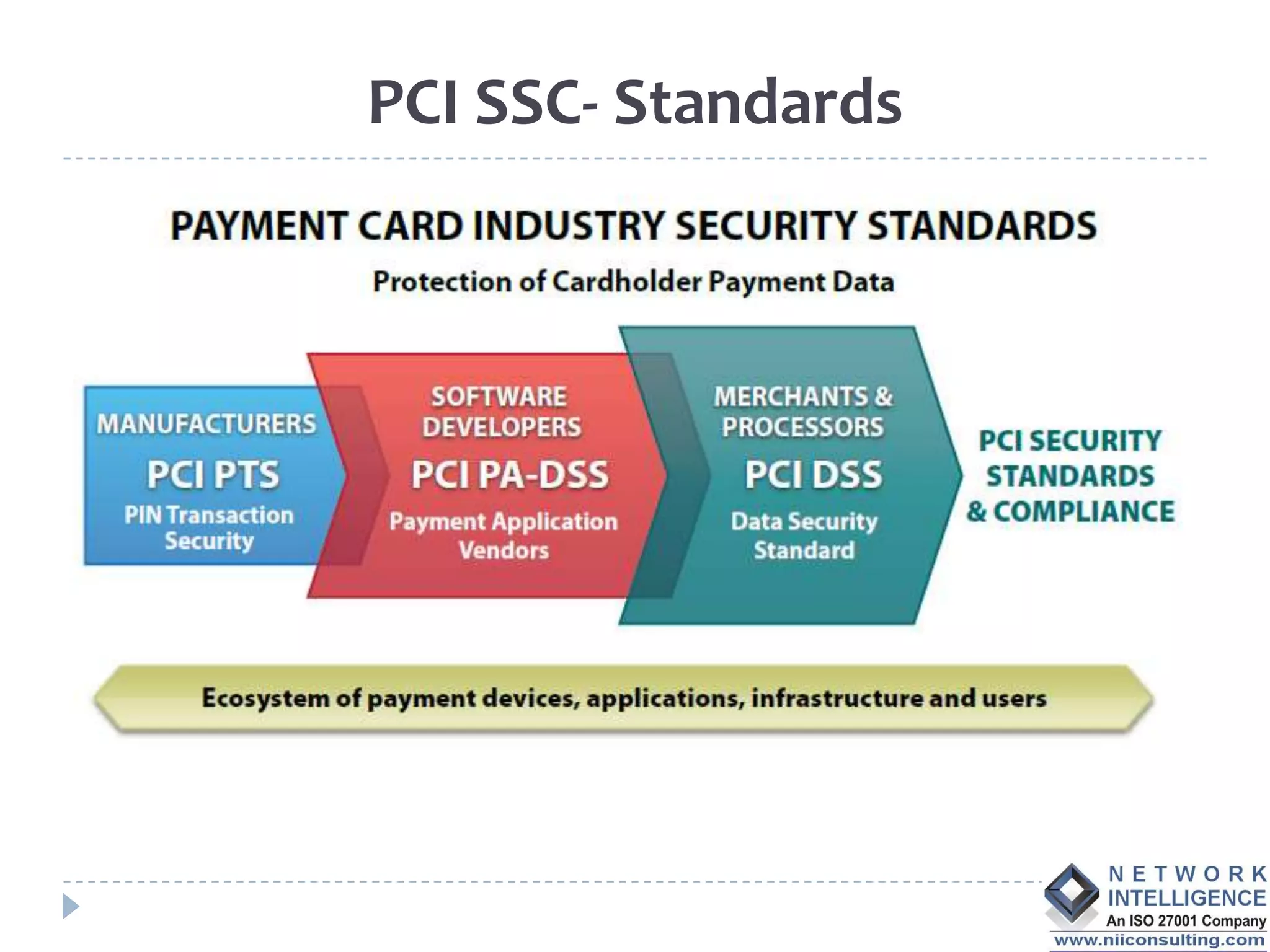
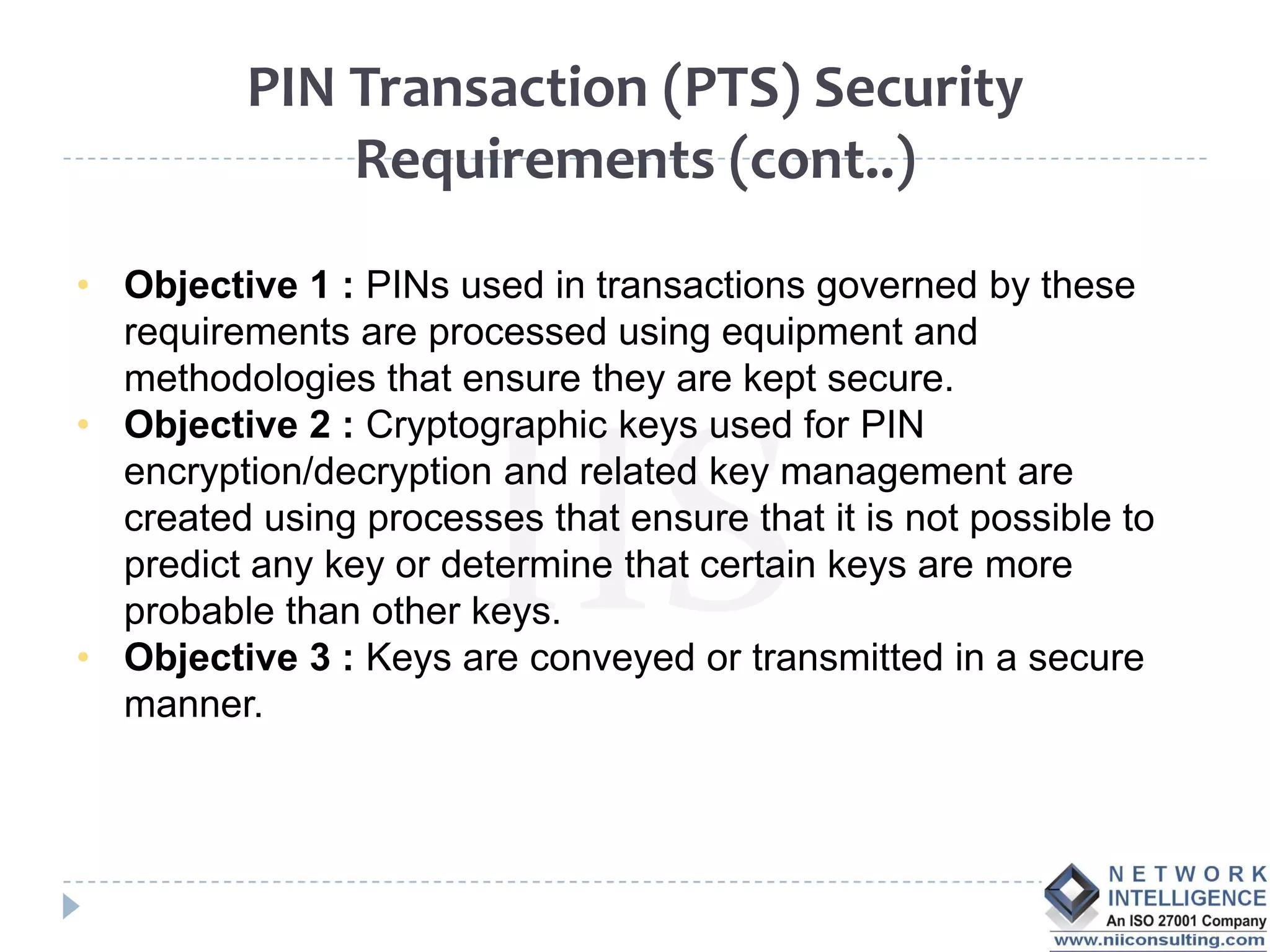
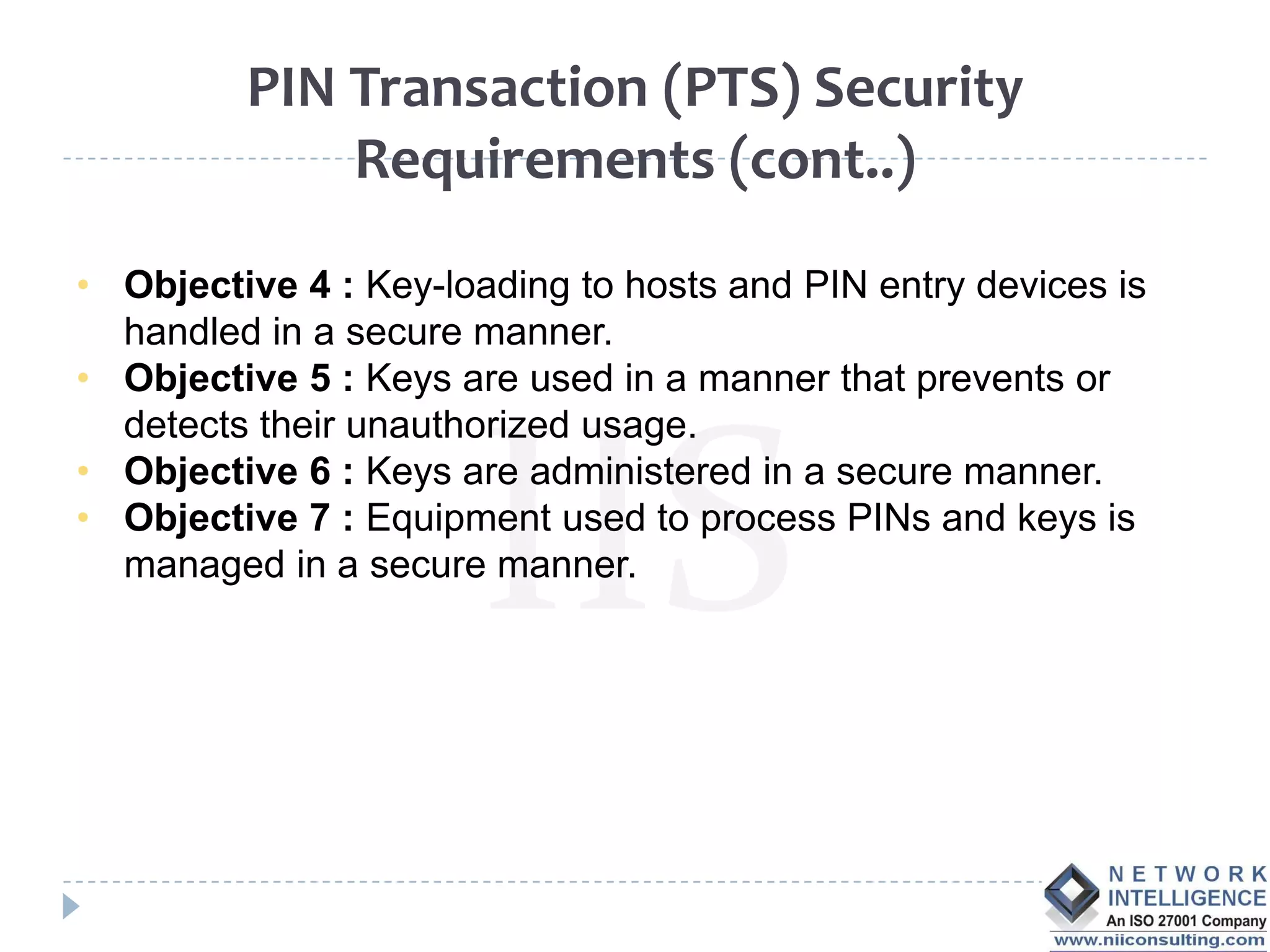
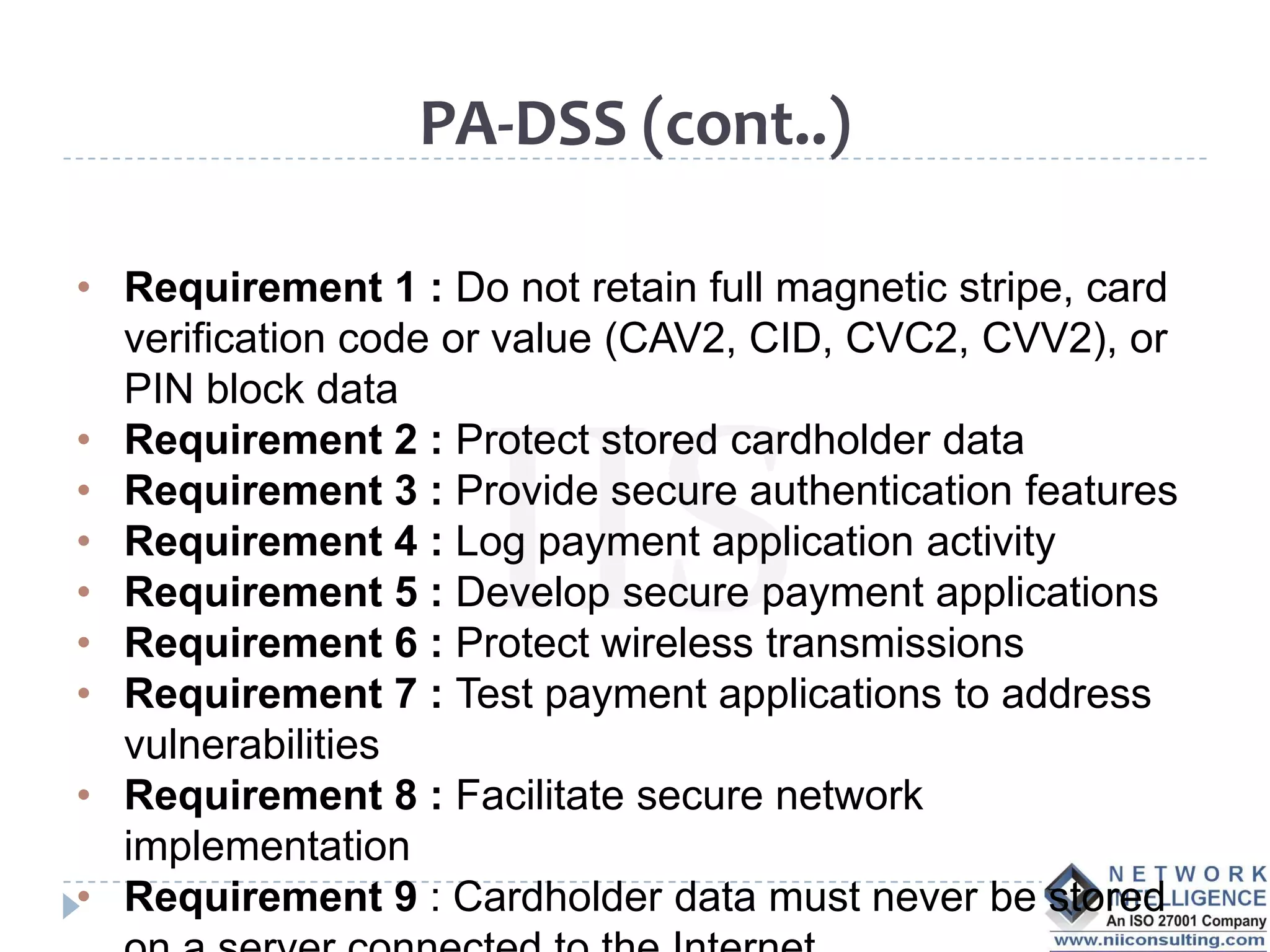
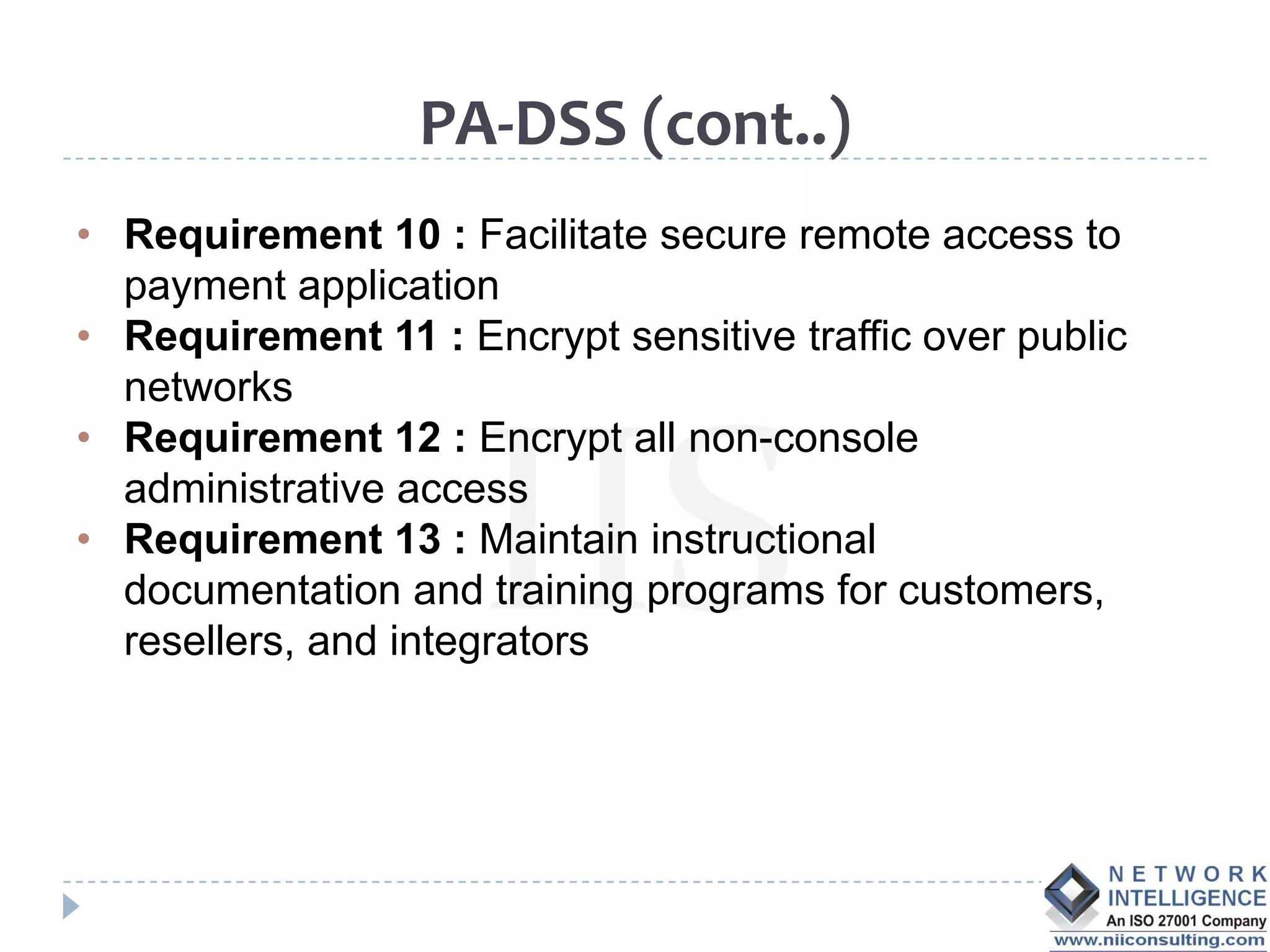
The PCI DSS (Payment Card Industry Data Security Standard) outlines requirements to protect cardholder data, emphasizing the importance of compliance to avoid severe repercussions, including regulatory fines and reputational damage. It includes guidelines for merchants and service providers on managing payment card data securely through various means, such as encryption and access controls. The PCI SSC oversees these standards and encourages the use of validated applications to enhance security in payment processing.