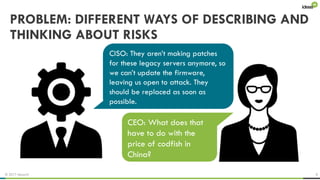
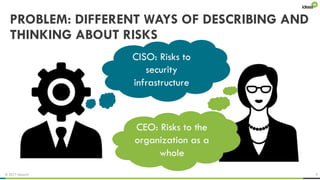
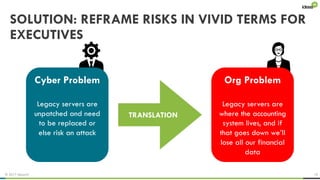
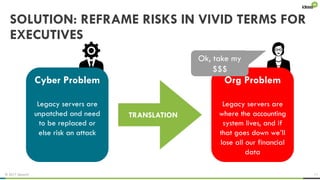
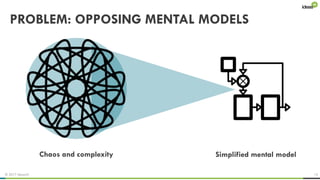
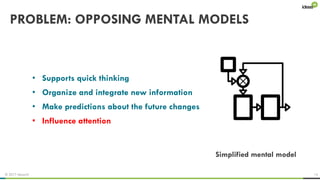
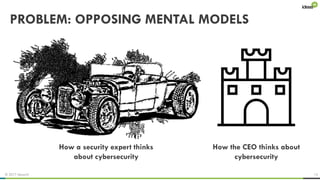
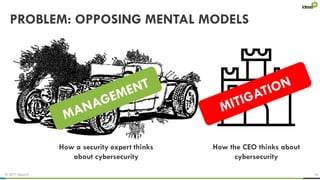
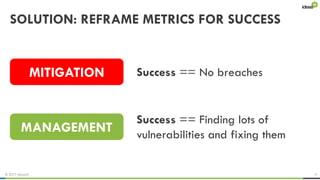
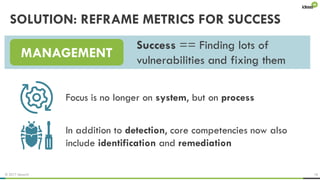
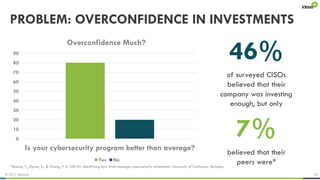
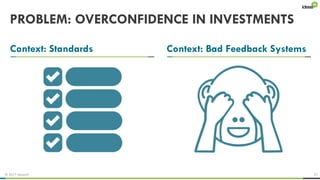
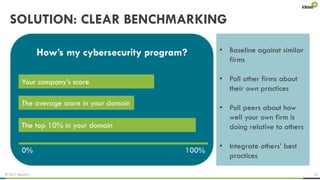
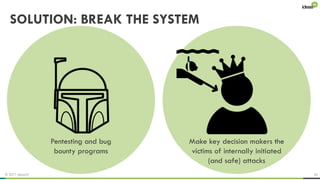
The document explores the behavioral science reasons behind executives' underinvestment in cybersecurity, identifying four main issues: differing risk perceptions, opposing mental models, overconfidence in current investments, and misdirected attention. It recommends reframing risks in relatable terms, adjusting success metrics, employing benchmarking strategies, and engaging decision-makers through simulated attacks. The goal is to enhance executive commitment to cybersecurity investments.