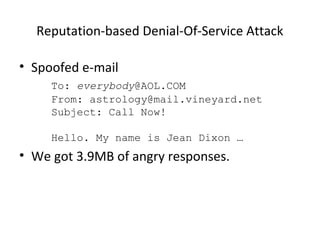
The document discusses various security issues related to using the internet and networking. It introduces basic security concepts like confidentiality, integrity and availability. It then examines specific problems such as hijacked web servers, denial of service attacks, unsolicited commercial email, operator errors and natural disasters. It also defines and explains security terms like probes, scans, packet sniffers and malicious code. The overall document provides a high-level overview of internet security risks and challenges.