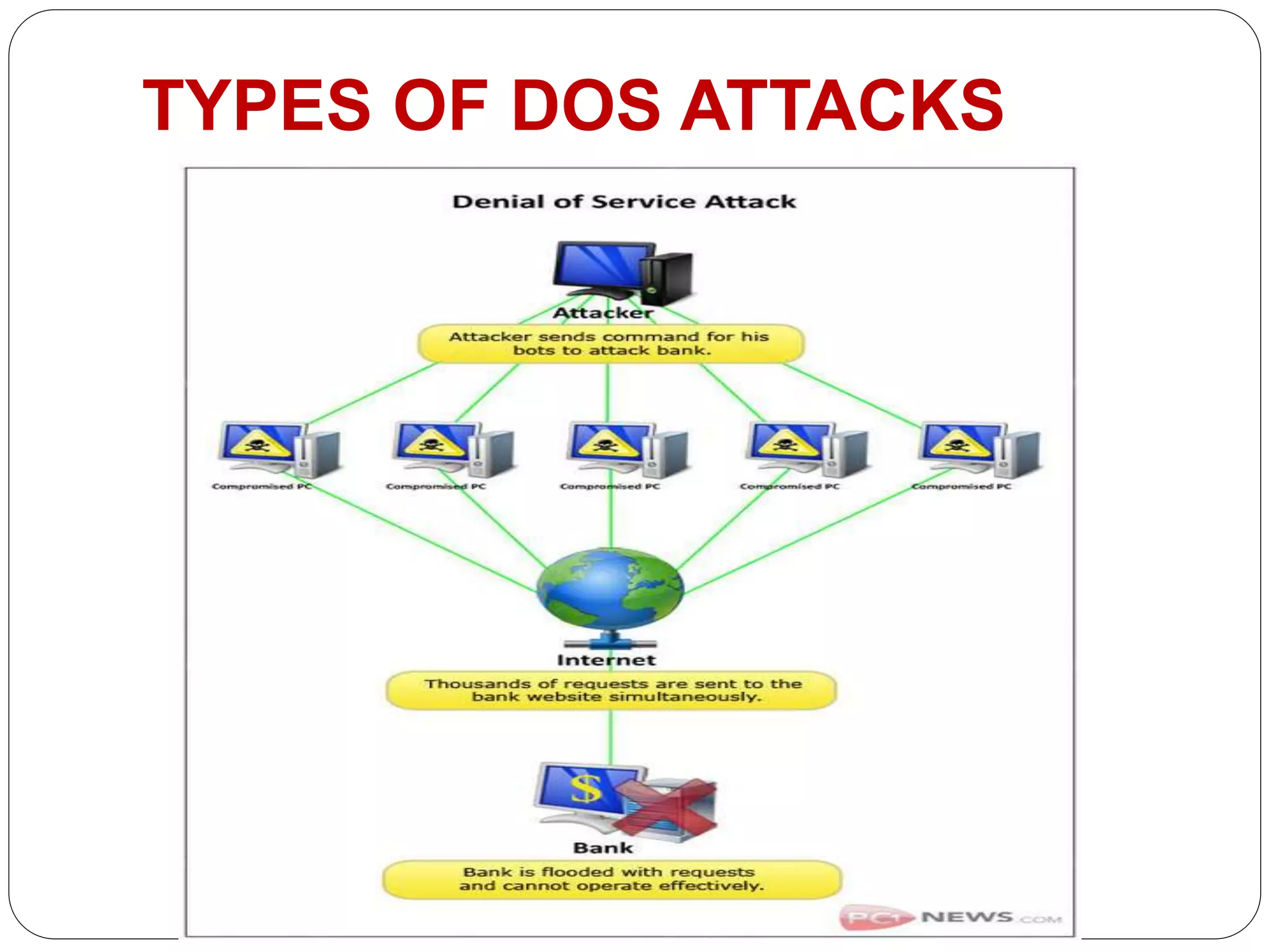
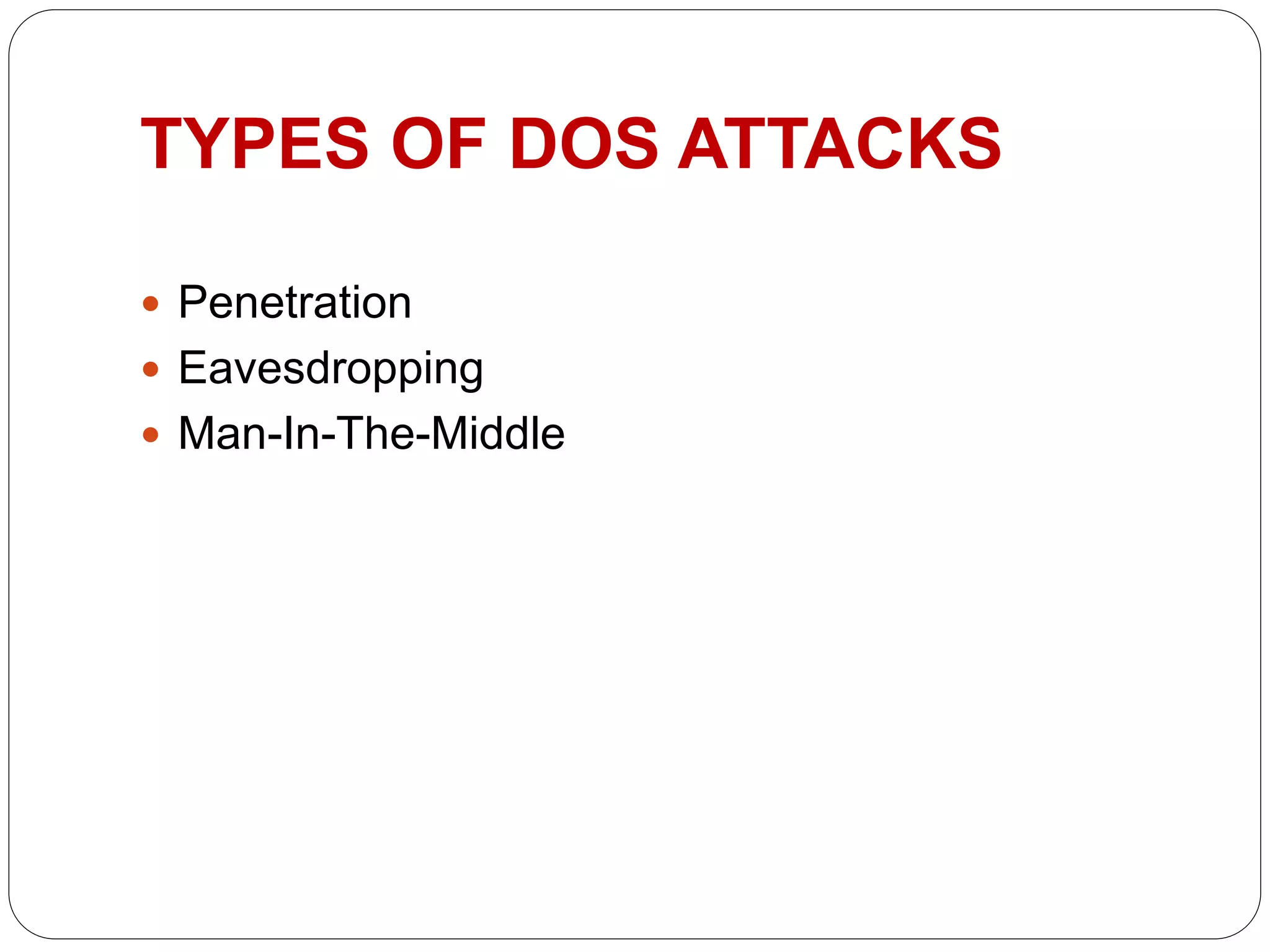
The document discusses denial-of-service (DoS) attacks, defining them as malicious attempts to disrupt services provided to users. It categorizes various types of attacks, including penetration, eavesdropping, and man-in-the-middle attacks, and outlines methods used to launch such attacks, like lbd.sh and slowloris.pl. Additionally, it suggests several protective measures, including firewalls, switches, and routers, that can help mitigate the effects of DoS attacks.