Embed presentation
Download to read offline



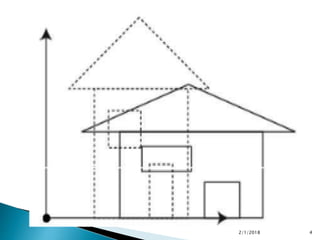

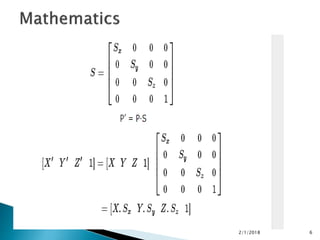


The document discusses scaling in 3D graphics. It explains that scaling changes the size of an object by multiplying the original coordinates by scaling factors along the X, Y, and Z axes. Scaling around a fixed point is accomplished by translating the point to the origin, scaling the object, and then translating the point back to its original position. The document includes figures and references on 3D scaling transformations.








