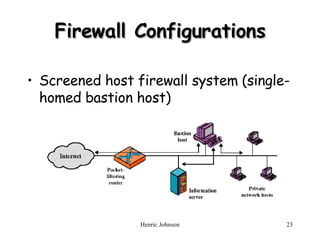
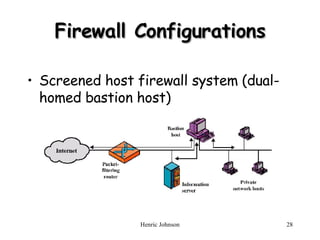
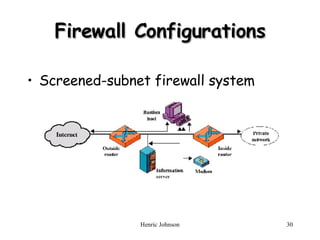
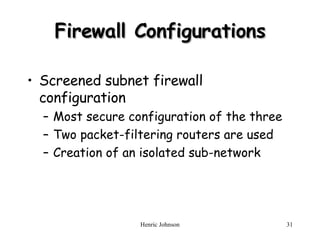
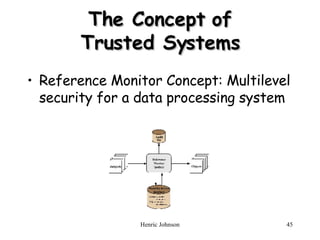
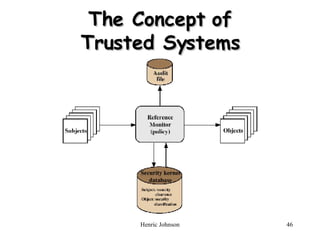
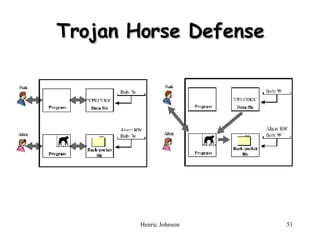
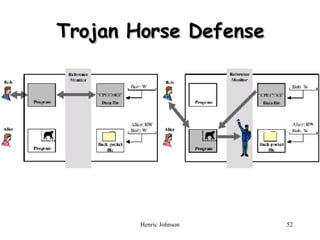
The document discusses firewall design principles, characteristics, and types. It describes three common firewall configurations: screened host with single-homed bastion host, screened host with dual-homed bastion host, and screened subnet. It also covers trusted systems, access control, and defending against Trojan horse attacks.