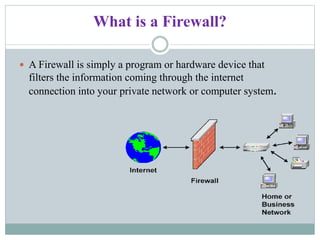
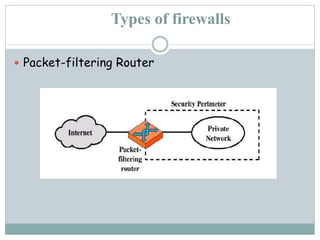
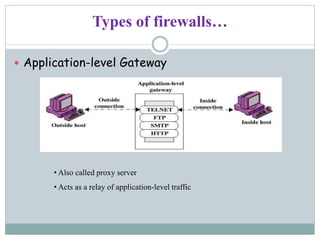
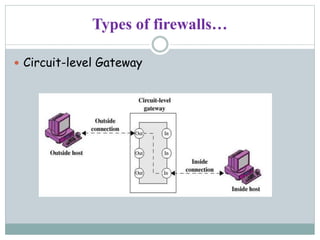
Lakshmi.S presents information on firewalls including definitions, types, and concepts. A firewall filters internet access to protect private networks. There are software and hardware firewalls. Types include packet filtering routers, application-level gateways, and circuit-level gateways. Firewalls concentrate security, filter unnecessary protocols, hide internal information, and require connections through the firewall. While firewalls improve security, they can hamper some network access and concentrating security in one location means compromising the firewall poses risks.