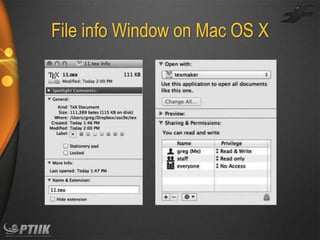
The document discusses file systems and file management. It defines what a file is and common file attributes like name, size, location, and permissions. It describes different types of files and various file operations. It also covers file system concepts like directory structures, access methods, open file management, and file sharing. File system protection and permissions are controlled through access lists, user and group IDs. Remote file systems allow files to be shared over a network using client-server models and distributed file systems.