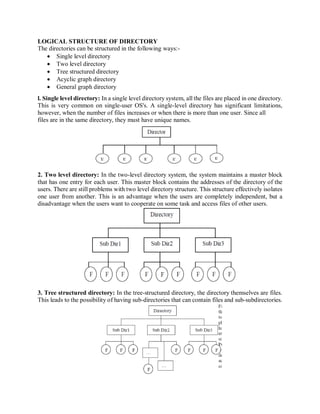
This document discusses file structures, access methods, directory structures, and file protection. It describes the basic structures of different types of files like text files, source files, and object files. It also outlines common file access methods like sequential, direct, and indexed sequential access. The document then explains different directory structures from single-level to general graph and how they organize files. Finally, it covers methods for protecting files through access control lists, user classifications, and passwords as well as issues with each approach.