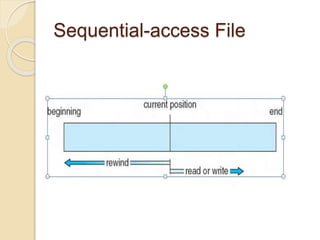
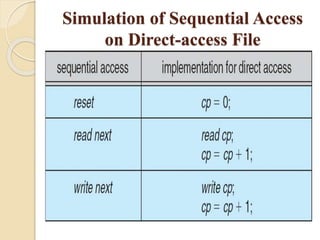
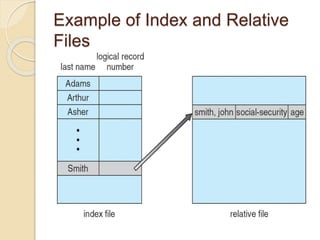
The document discusses file concepts and access methods. It defines what a file is, including its logical view, mapping to physical storage, and common types. File attributes like name, size, and protection are also described. The functions of file systems are explained, including creating, writing, reading, and deleting files. Open file data structures are outlined, as are sequential and direct access methods. File locking, types, and the simulation of sequential access on direct-access files are also summarized.