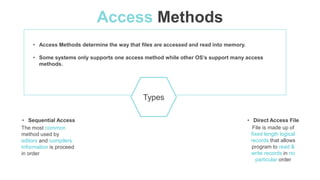
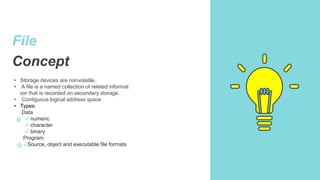
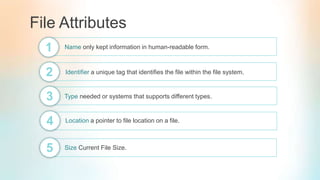
The document summarizes key concepts about file systems, including that it provides mechanisms for online storage and access to data and programs. It discusses files, directories, access methods, and protection. Files have attributes like name, size, timestamps. Access methods include sequential and direct access. Directories organize files in a tree structure and allow operations like search, create, delete, list, rename. Protection controls permissions for reading, writing and executing files.






![Claypool Example
Unix open()
Path
Is the name of file
On success
Return index
flags
Is bitmap to set switch
int open (char * path,int flags[,int model])](https://image.slidesharecdn.com/filesysteminterface-181125141540/85/File-system-interface-9-320.jpg)