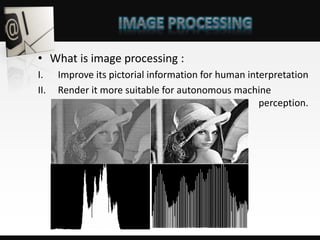
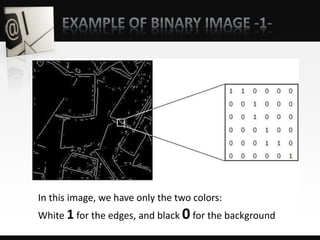
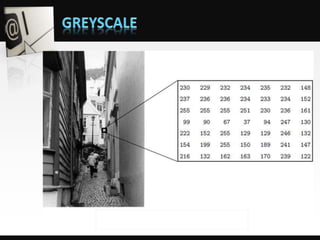
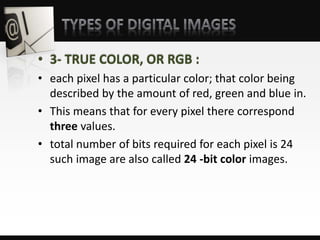
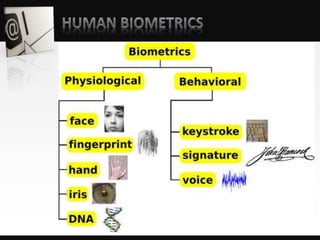
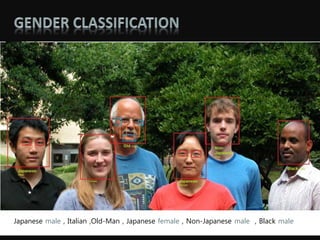
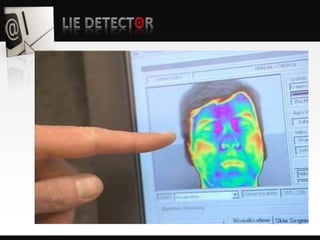
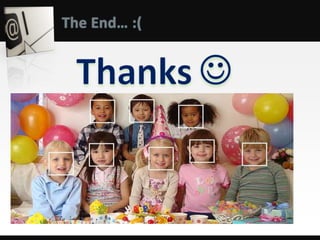
Object detection is a computer vision technique that identifies objects in images and videos. It can detect things like faces, humans, buildings, and cars. Object detection has applications in areas like image retrieval, video surveillance, and face detection. Image processing techniques are used to both improve images for human interpretation and to make images more suitable for machine perception. These techniques include enhancing edges, converting images to binary, greyscale, or true color formats. Face detection is a common application that finds faces in images and ignores other objects. It is often used as the first step in face recognition systems.