Embed presentation
Download as PDF, PPTX








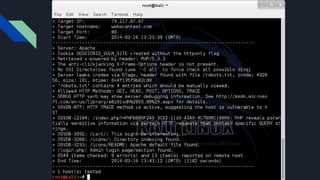
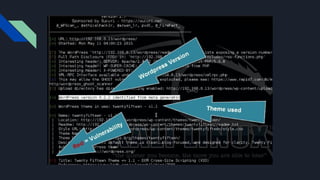




The document provides an introduction to enumeration in penetration testing, outlining its purpose of gathering critical information for initial access and exploitation. It lists various tools used for enumeration, including nmap for network mapping and scanning, and offers warnings regarding the legality and potential service bans associated with these activities. Additionally, it highlights the pros and cons of different tools and methods for effective enumeration.













