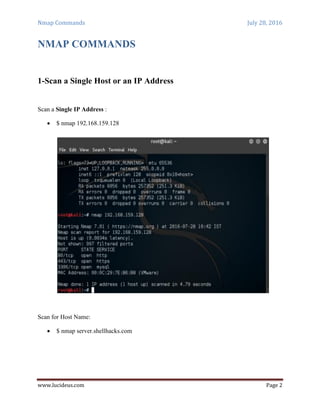
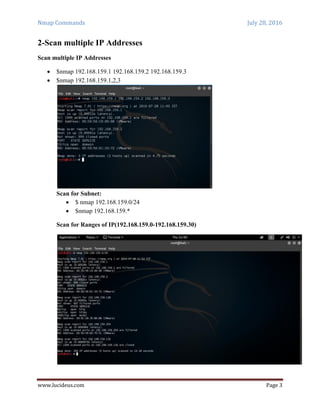
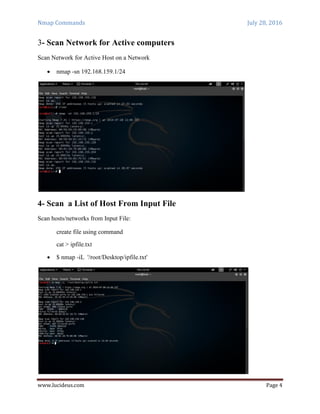
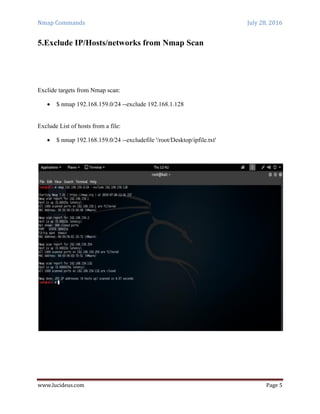
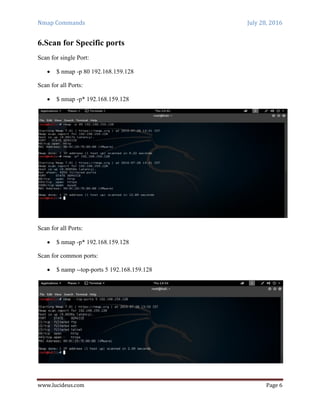
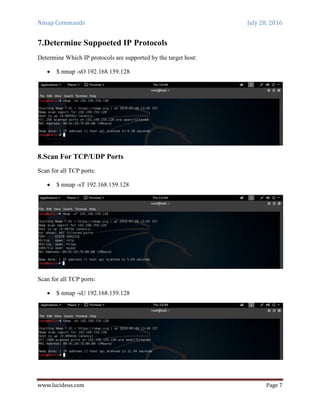
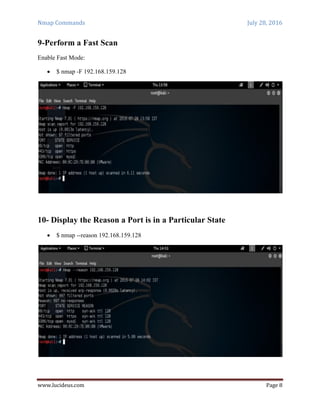
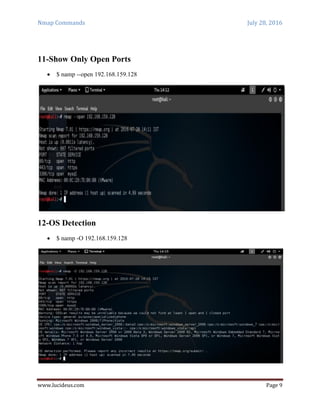
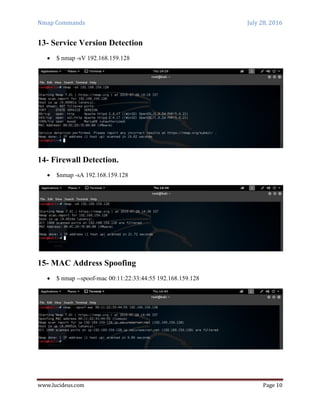
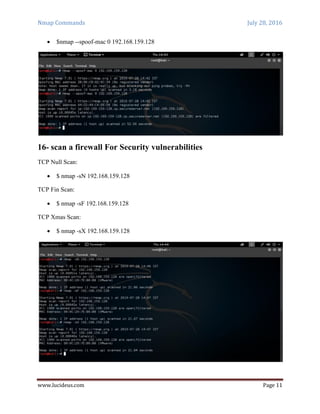
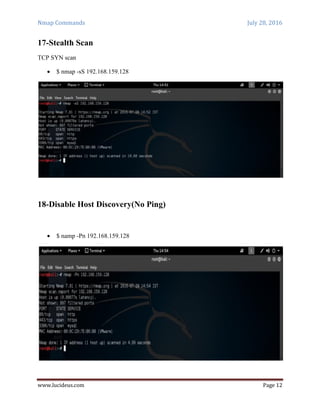
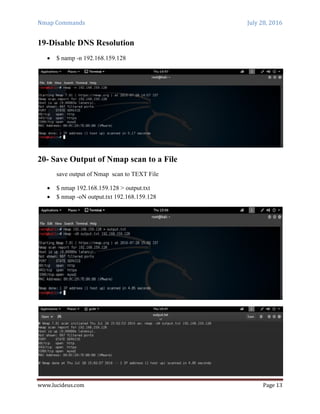
Nmap is a security scanning tool used to discover hosts and services on a computer network. It sends specially crafted packets to target hosts and analyzes the responses to perform functions like host discovery, port scanning, version detection, and operating system detection. The document provides 20 examples of Nmap commands, such as commands to scan a single host or IP address, scan multiple addresses or ranges, perform specific scans like OS detection or version detection, and save scan output to files.