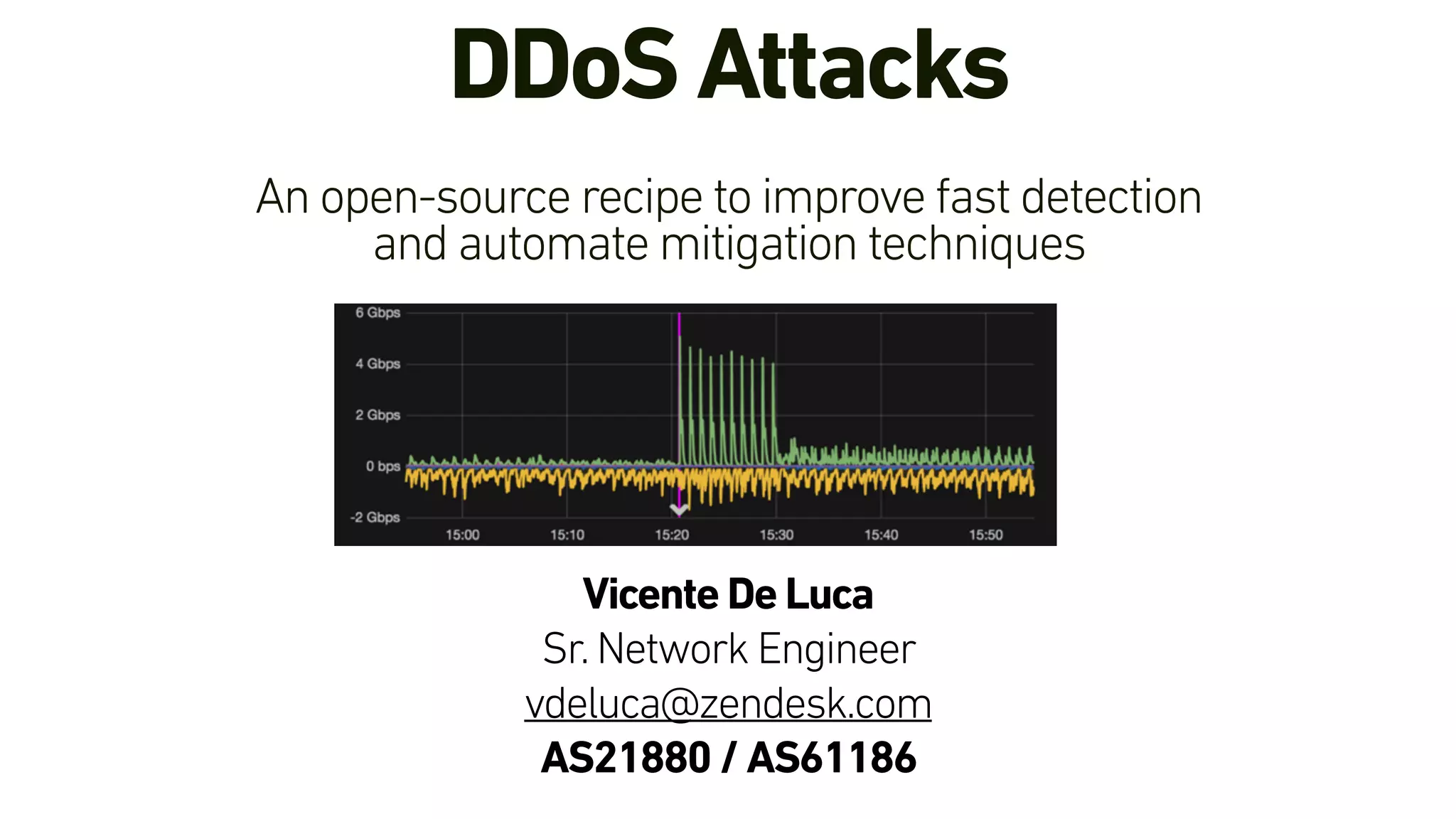
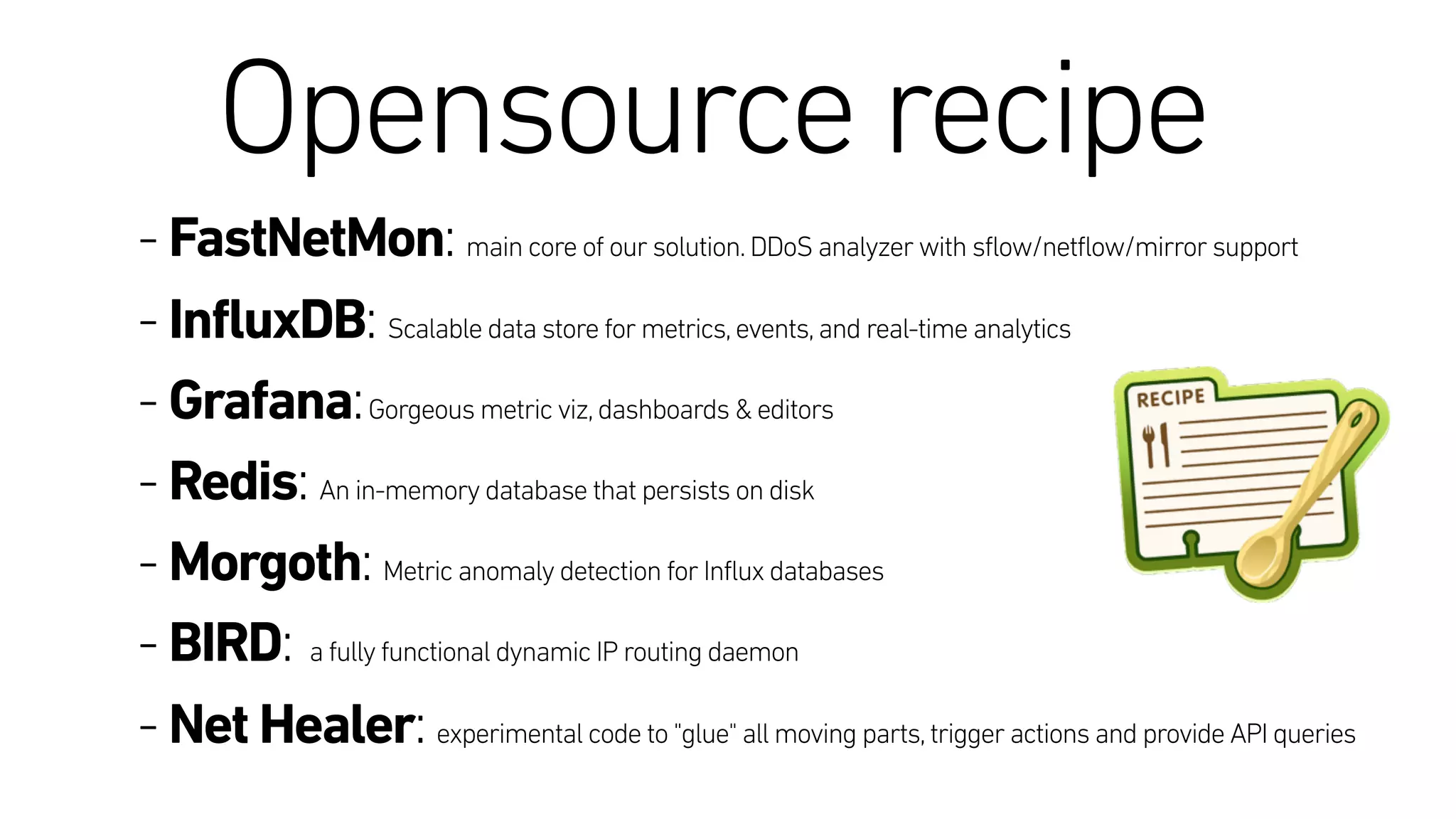
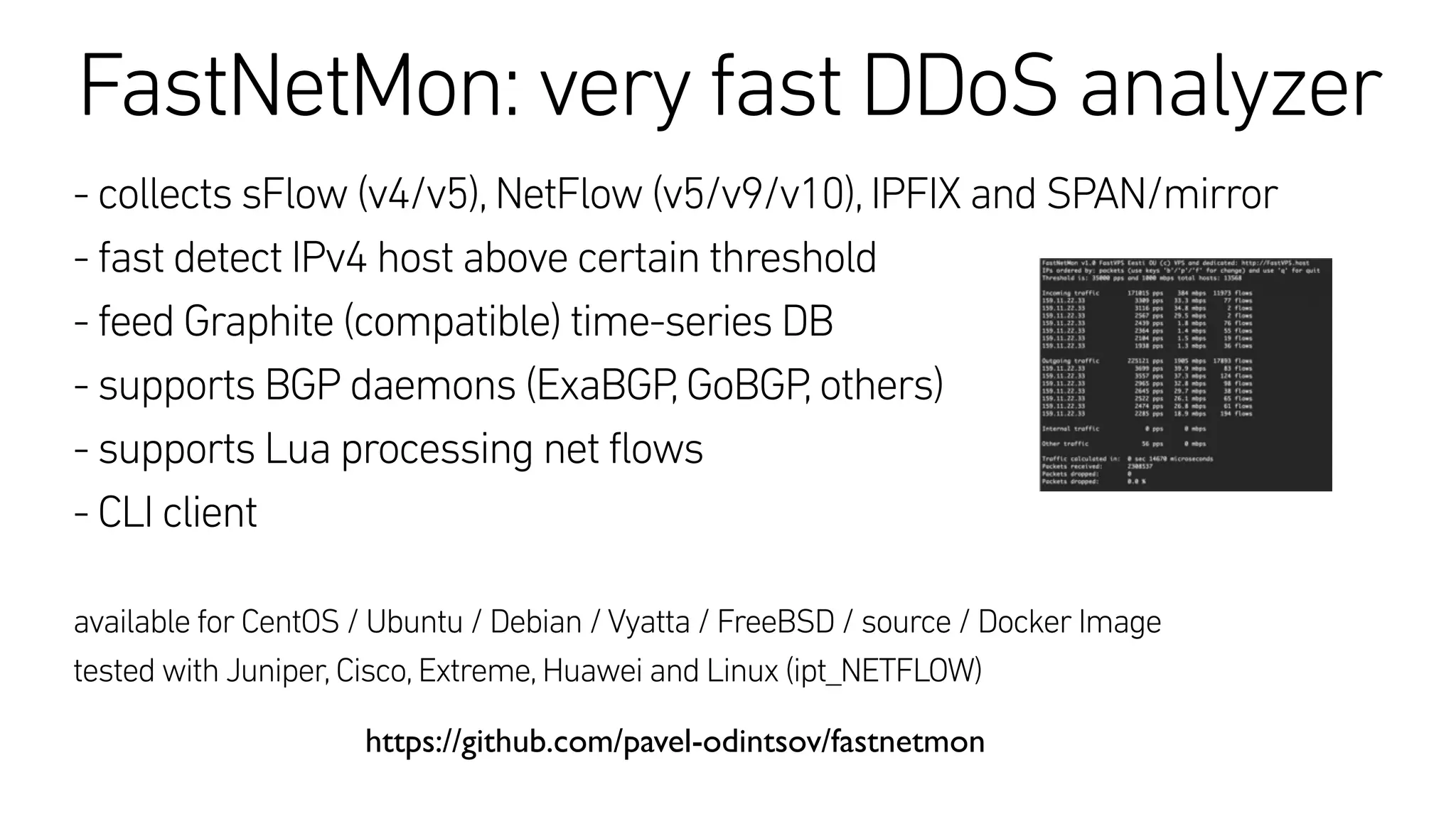
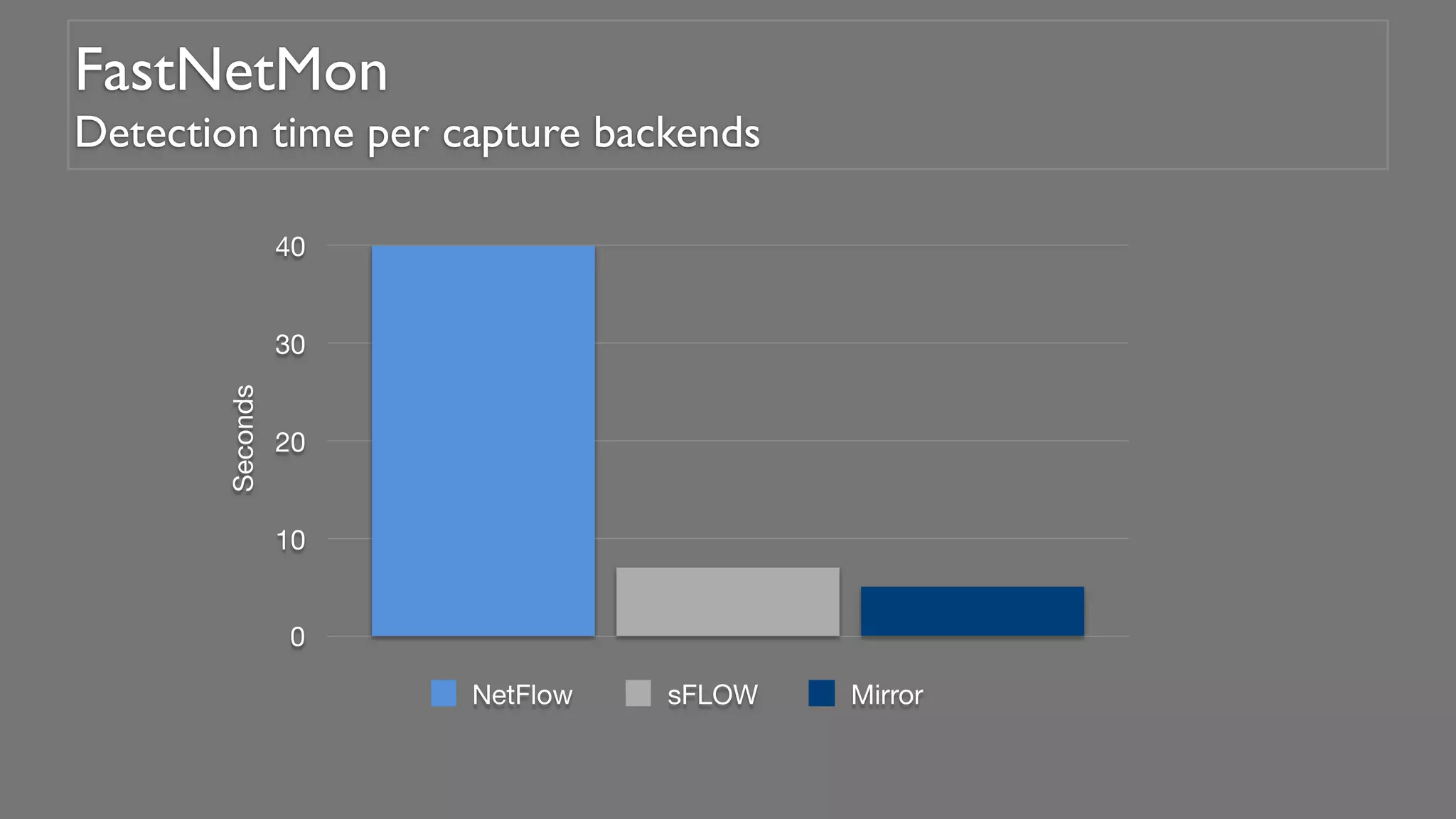
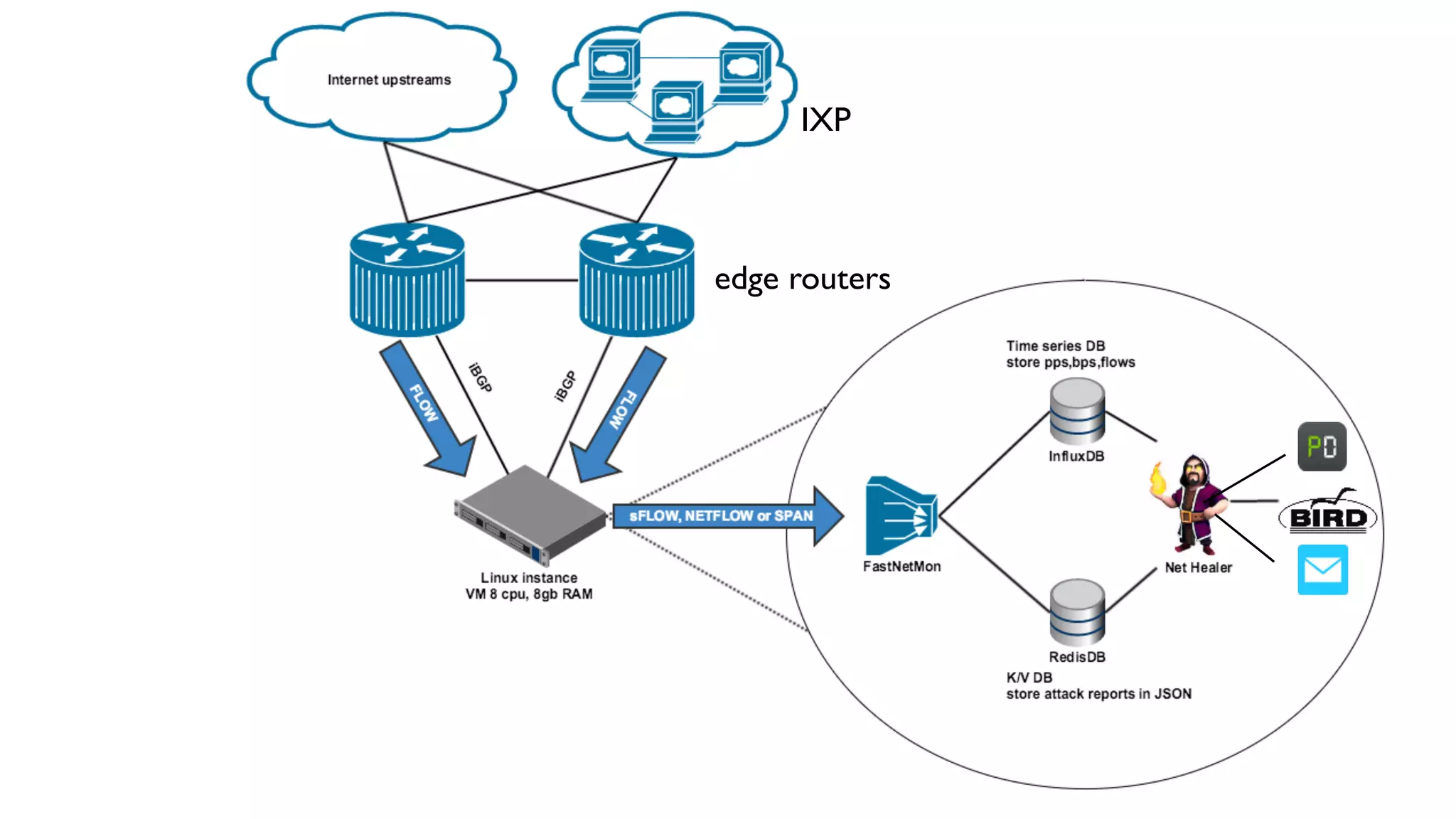
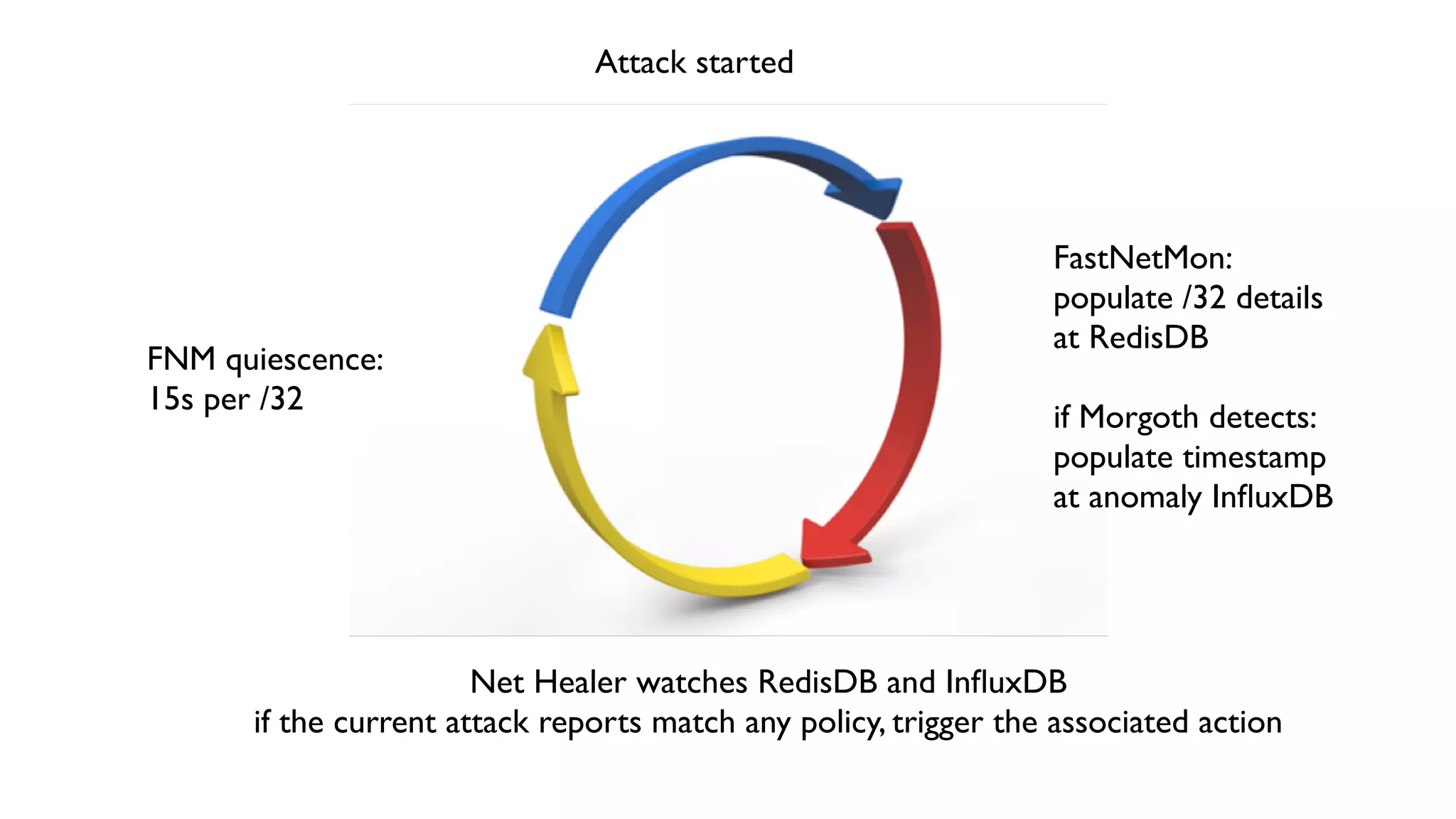
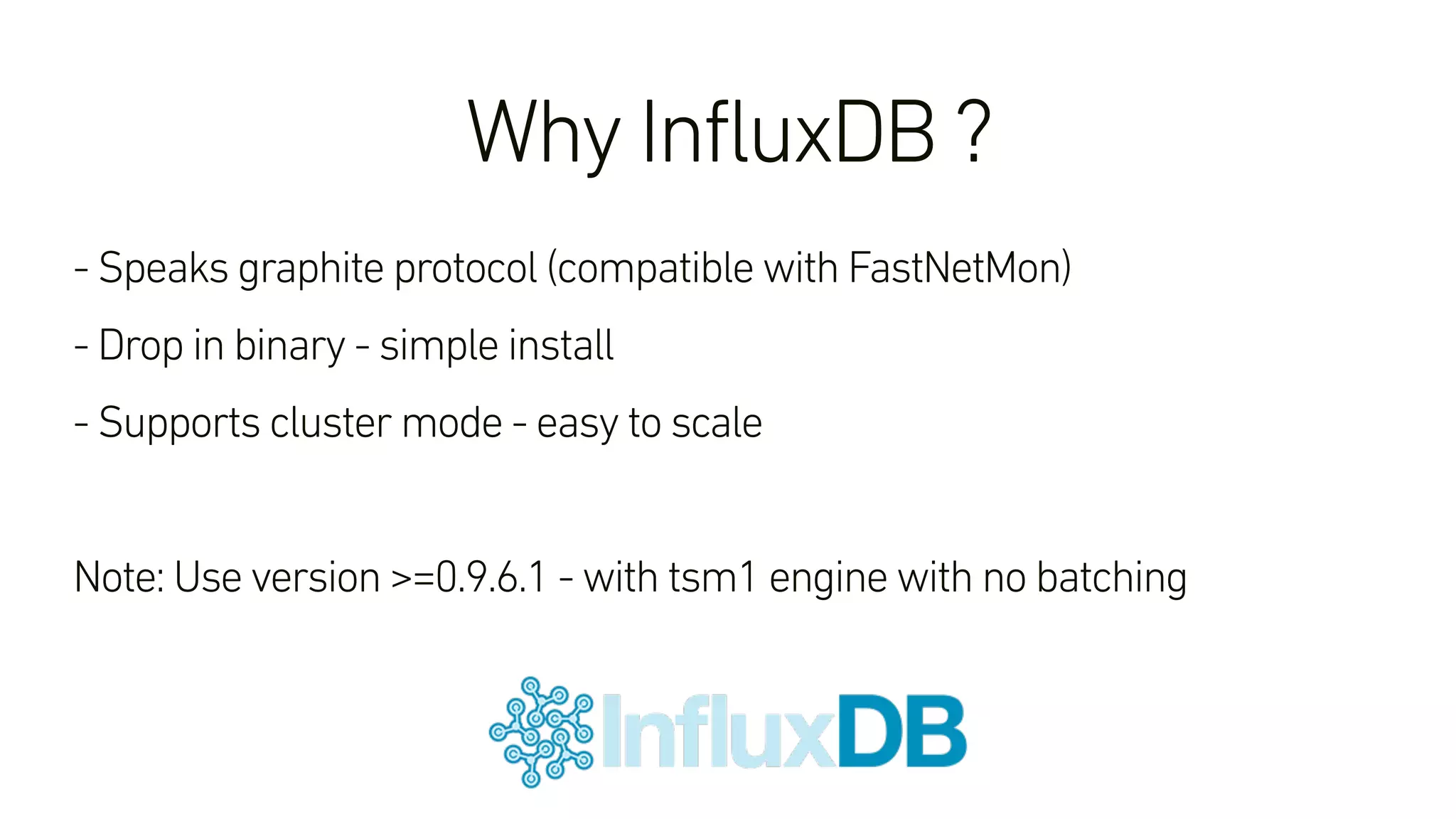
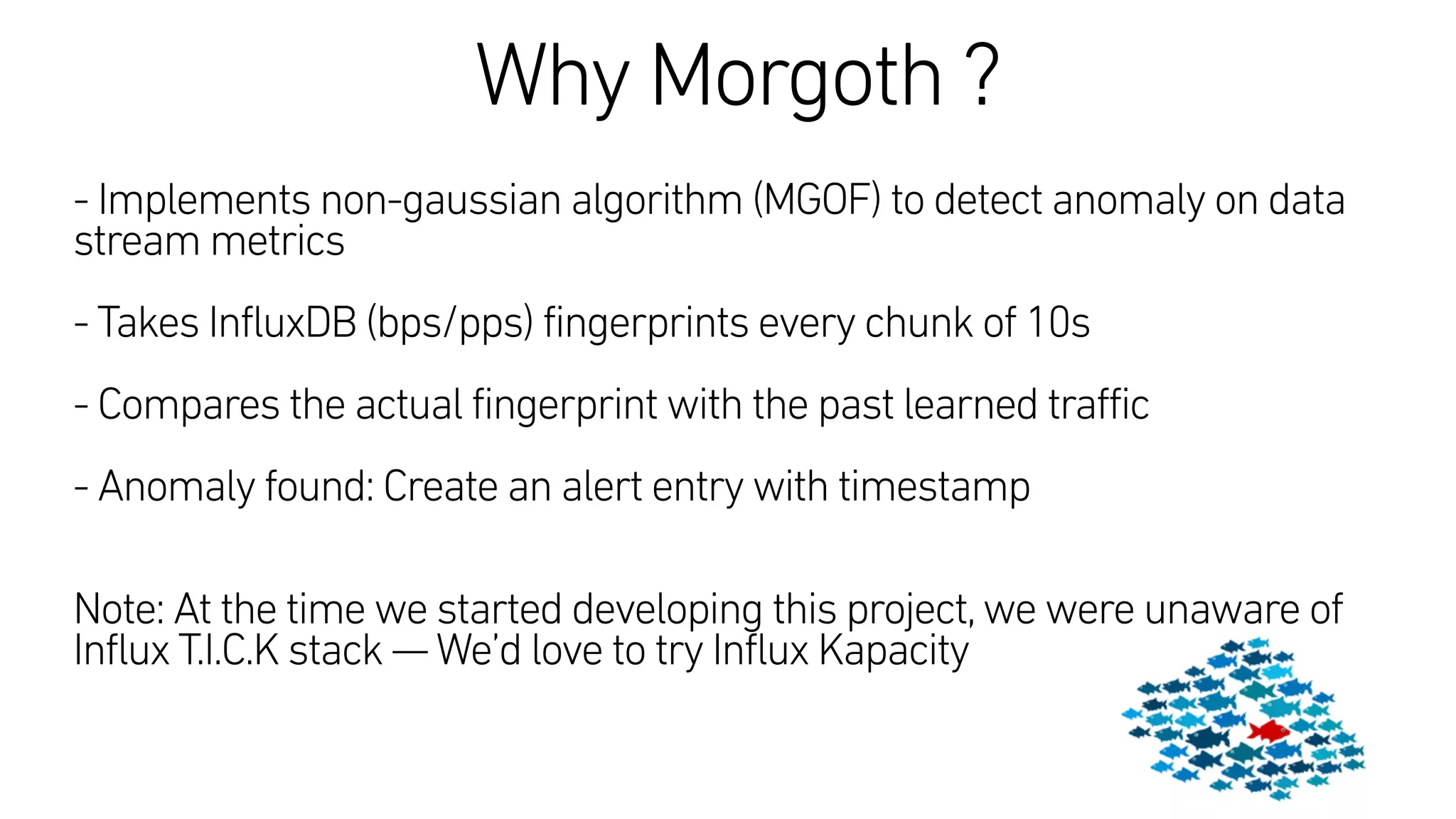
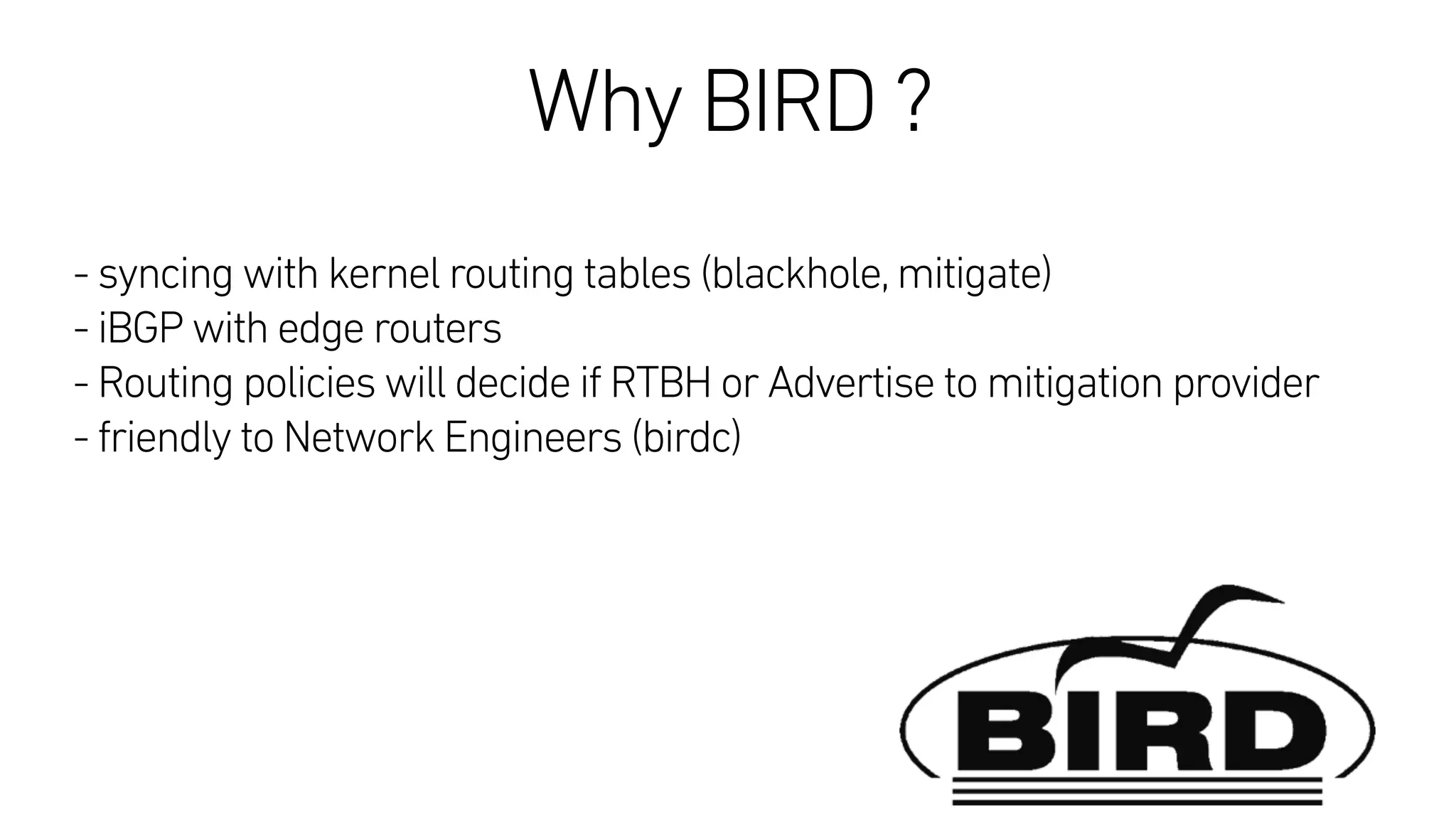
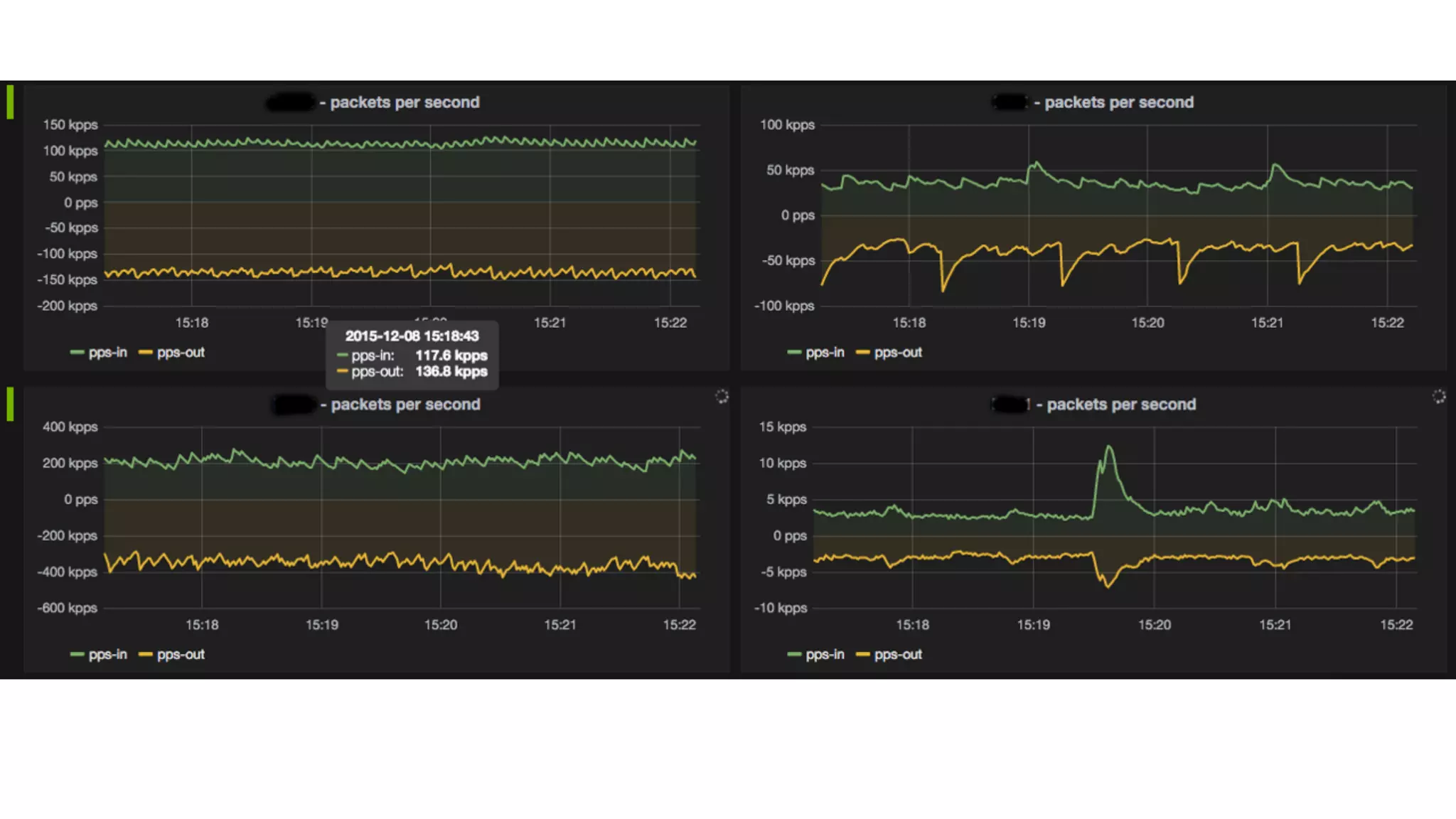
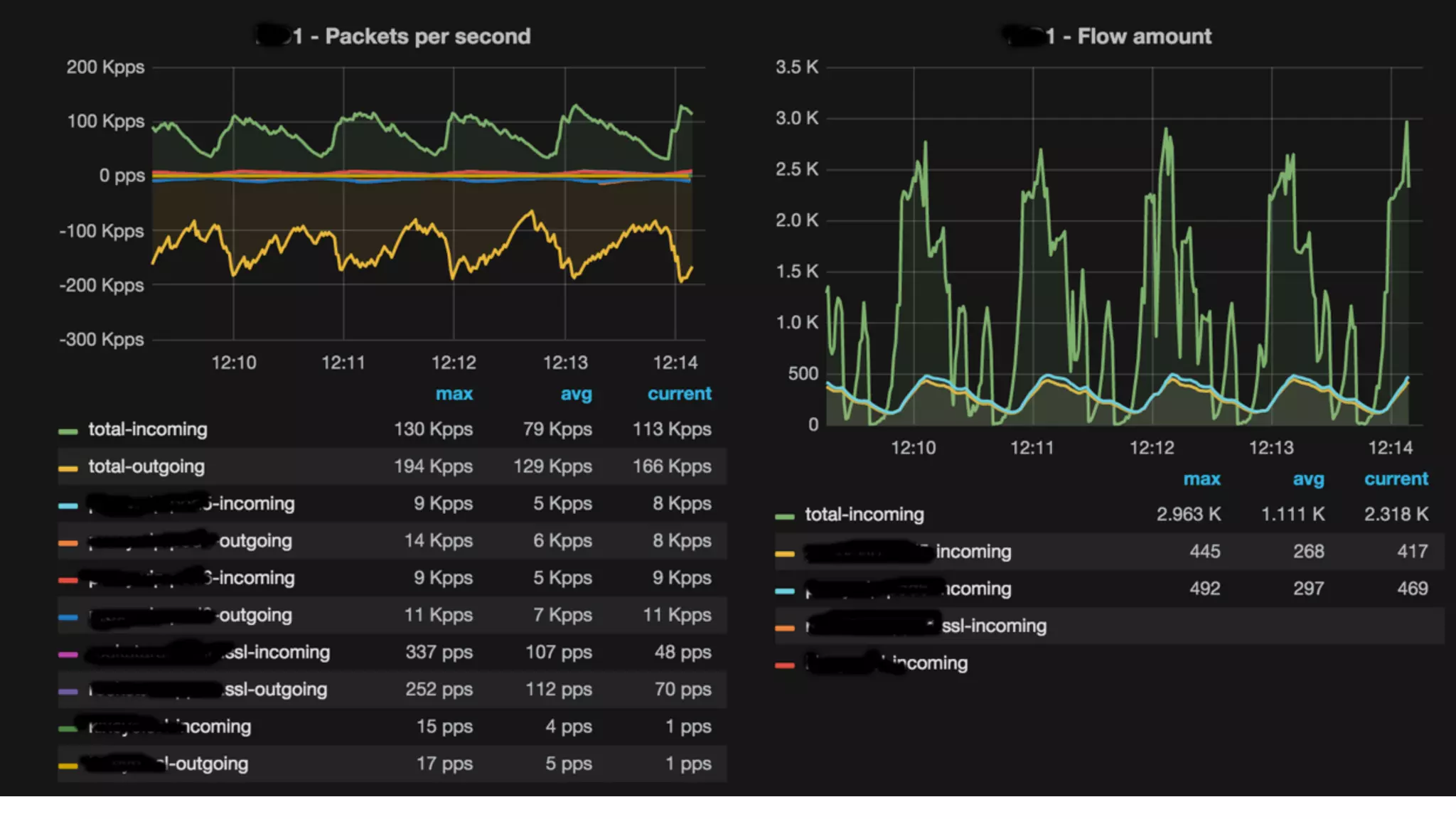
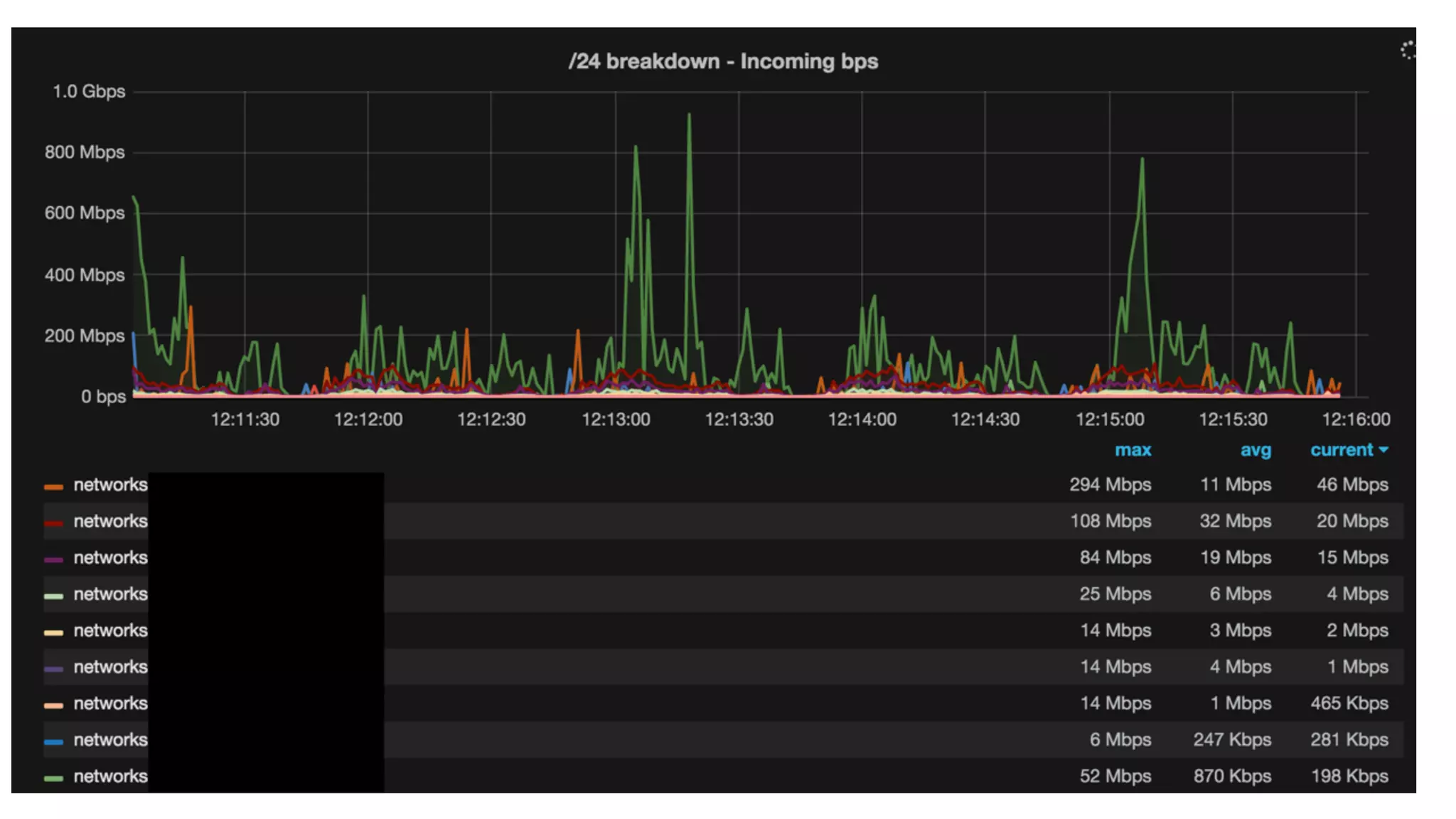
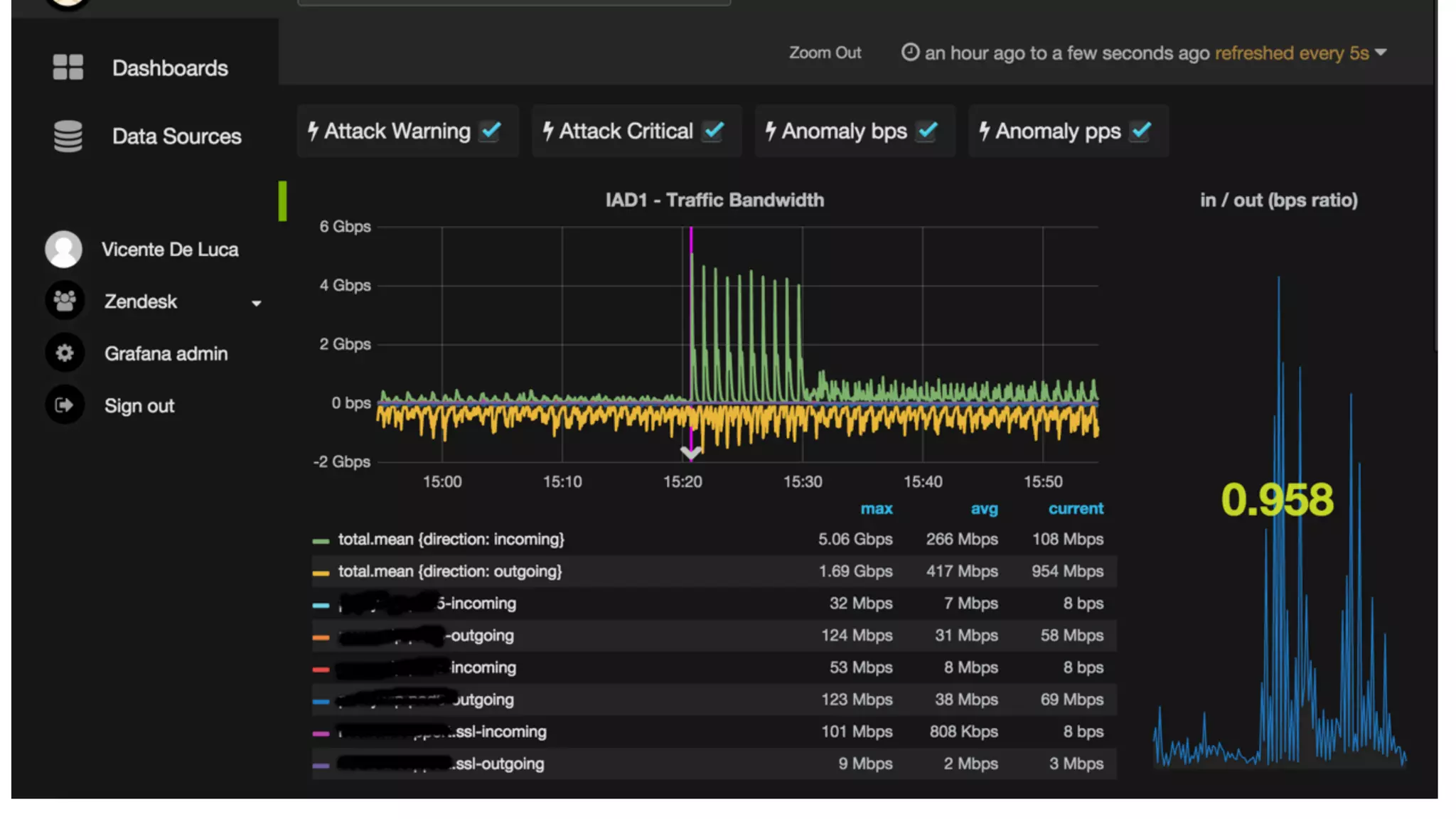
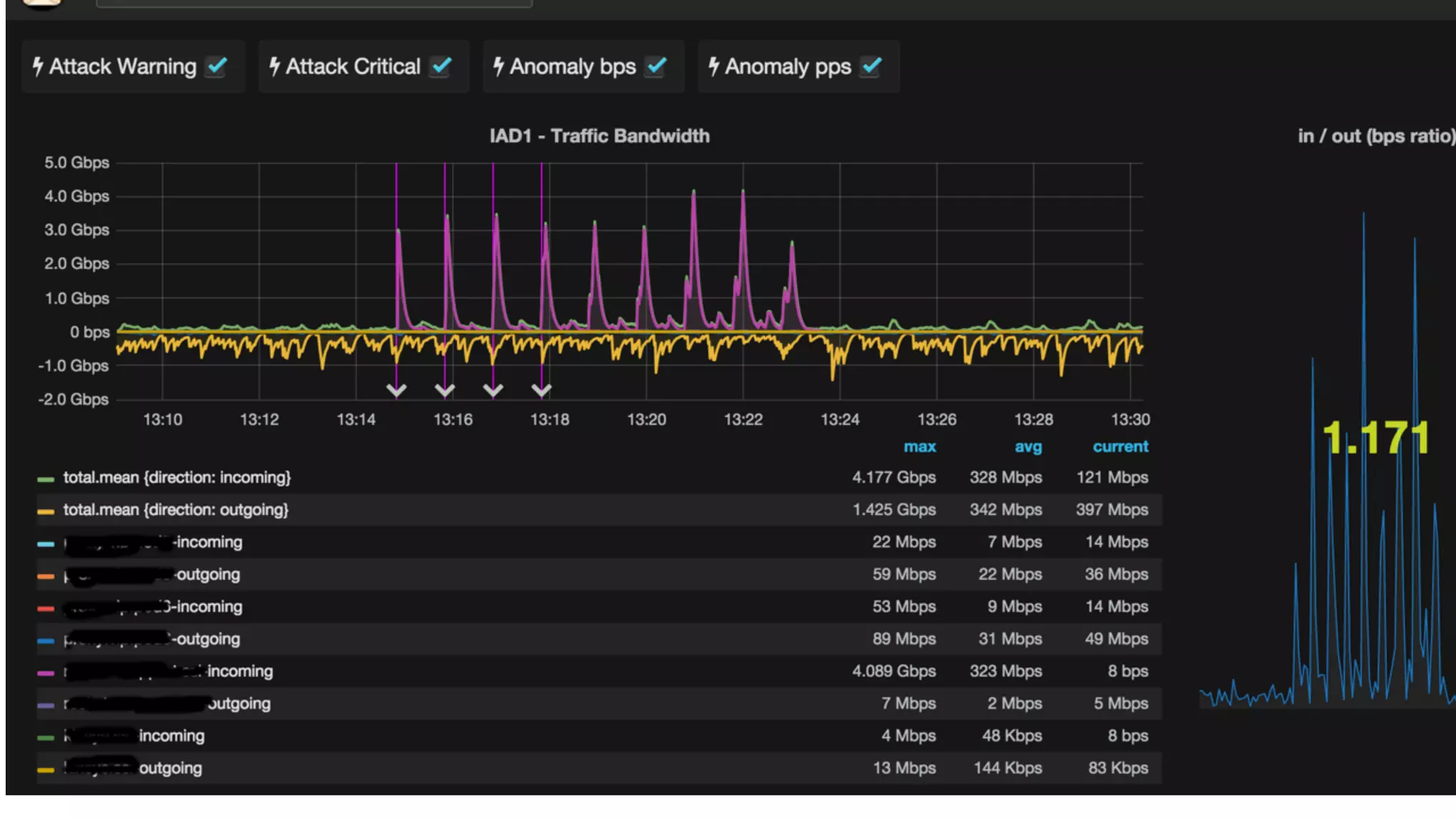
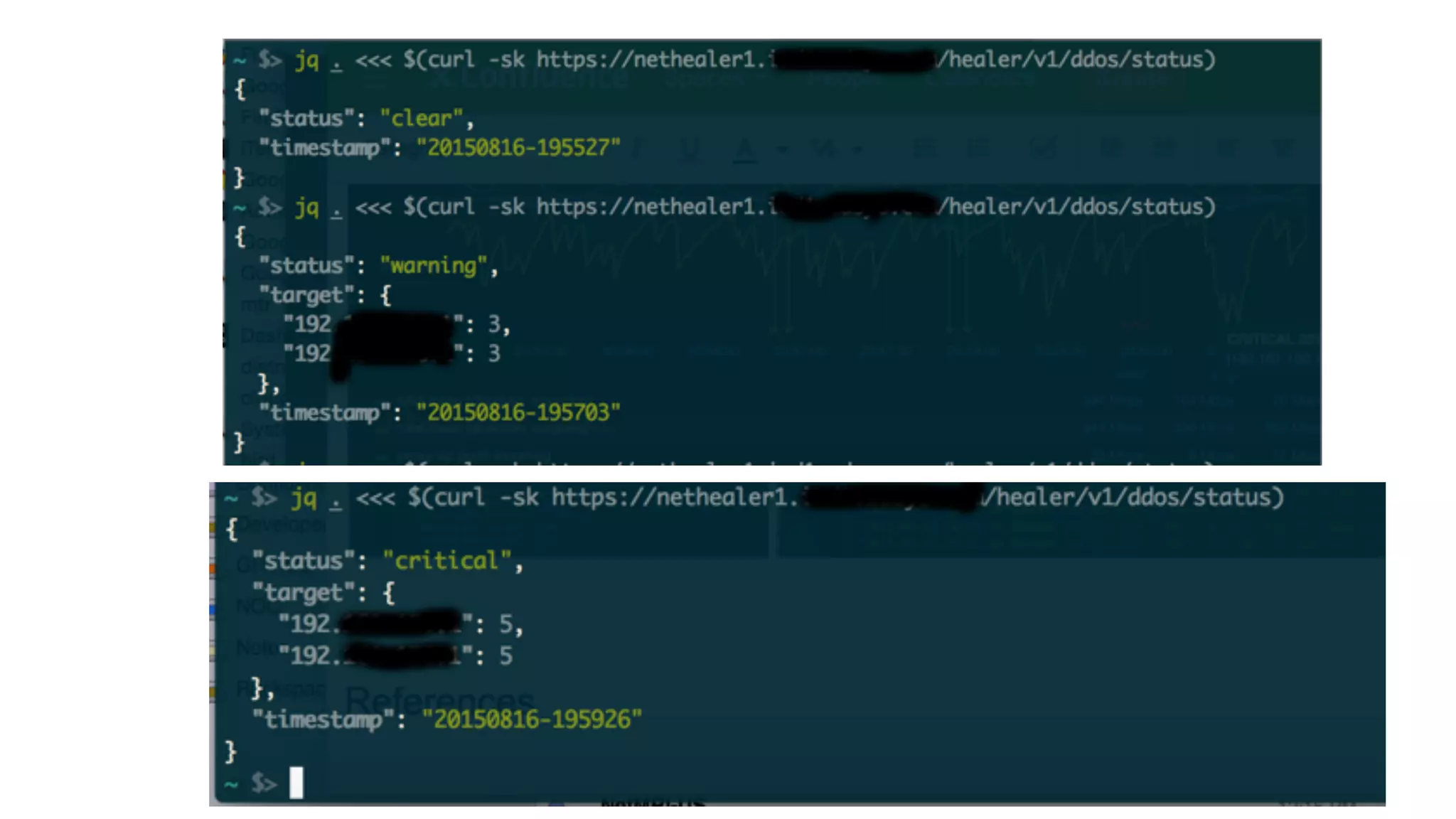
This document describes an open-source solution for improving fast detection of and automating mitigation of DDoS attacks. The solution uses FastNetMon for fast detection of attacks from sFlow, NetFlow, or port mirroring. Metrics and events are stored in InfluxDB for analysis by Morgoth and visualization in Grafana. Net Healer uses policies to trigger actions like blackholing routes in BIRD based on data from Redis and anomalies detected by Morgoth in InfluxDB. This provides faster detection and reaction than traditional hardware appliances alone.