This document provides an overview of key networking components in Amazon Web Services (AWS) including:
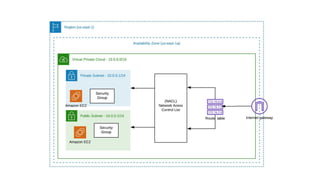
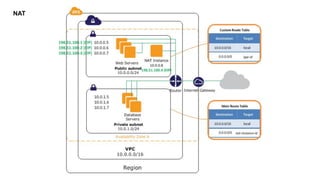
- Virtual Private Cloud (VPC) which acts as a virtual data center in the cloud
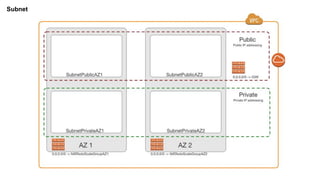
- Subnets which are ranges of IP addresses within a VPC
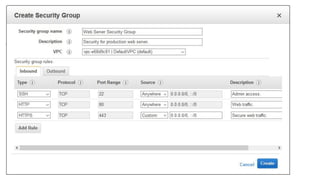
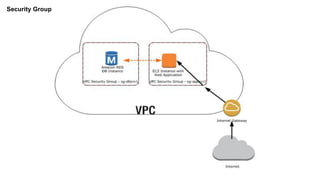
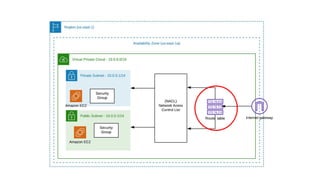
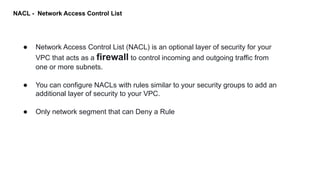
- Security groups and Network Access Control Lists (NACLs) which provide security controls
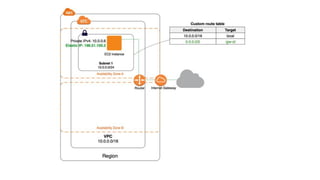
- Route tables which determine traffic routing
- Internet Gateways and NAT Instances/Gateways which control internet access
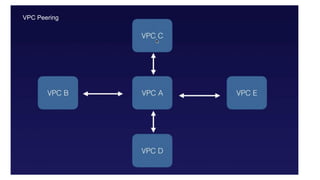
- VPC Peering which enables connectivity between separate VPCs within AWS








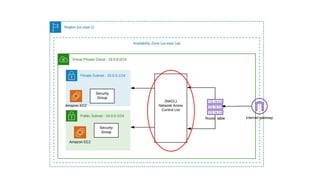
![NACL Rules
● Rule number. The rules are evaluated using the lowest numbered rule.
● Type: SSH, HTTP
● Protocol. ICMP, TCP, UDP
● Port range. The listening port or port range for the traffic. For example, 80 for HTTP traffic.
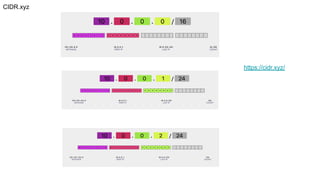
● Source. [Inbound rules only] The source of the traffic (CIDR range).
● Destination. [Outbound rules only] The destination for the traffic (CIDR range).
● Allow/Deny. Whether to allow or deny the specified traffic.](https://image.slidesharecdn.com/awsnetwork-200519032530/85/Aws-Network-Introduction-18-320.jpg)