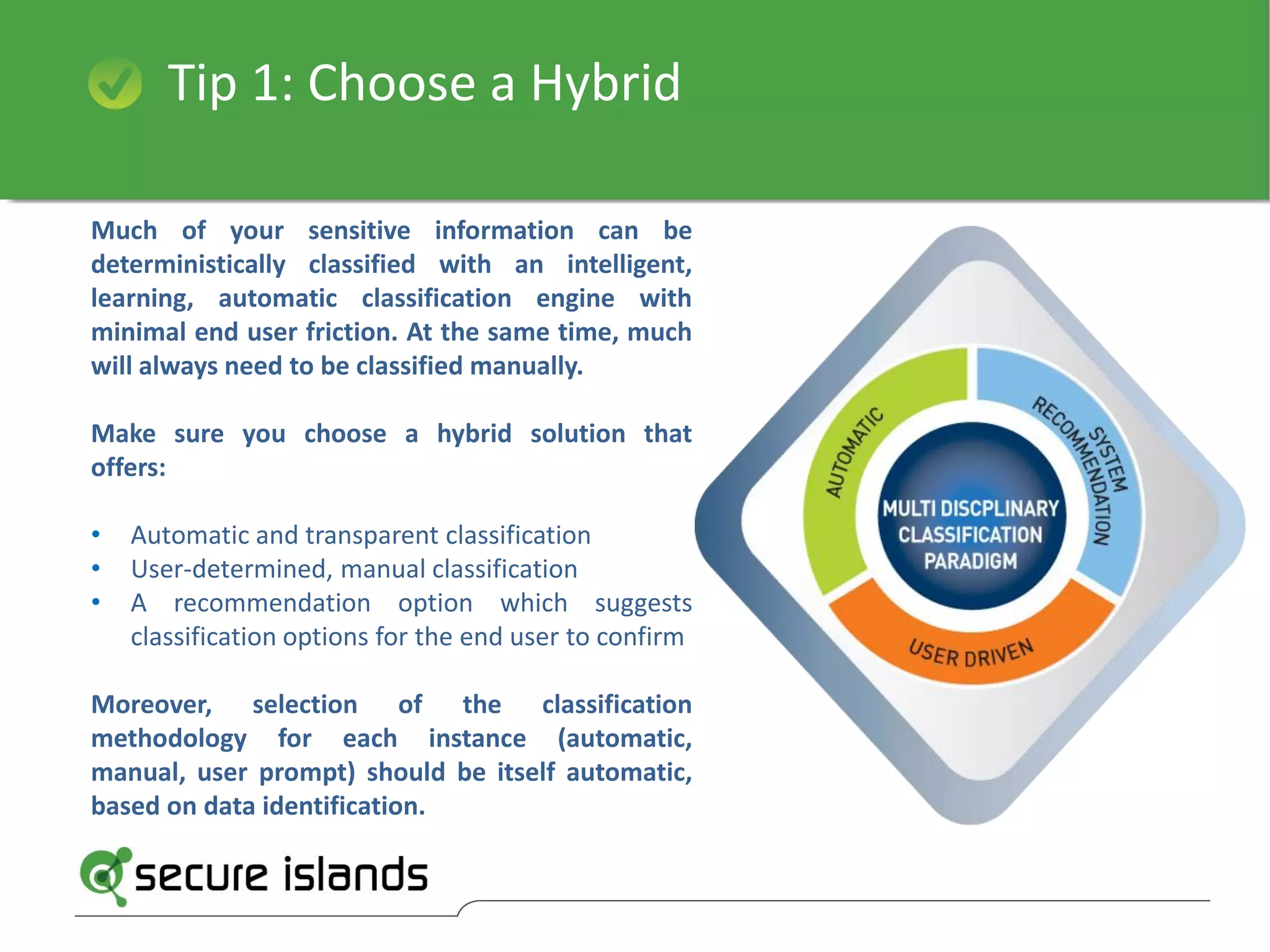
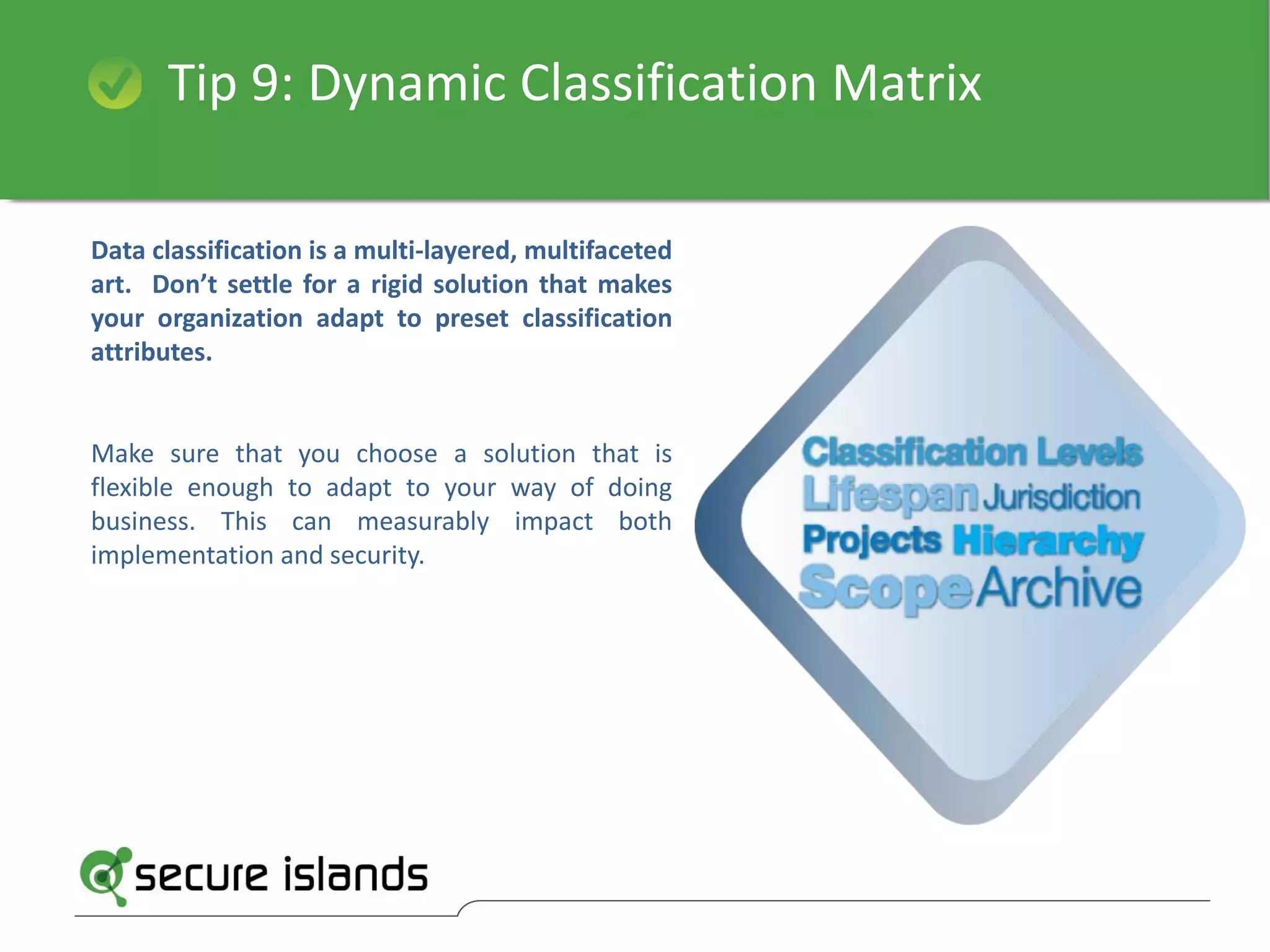
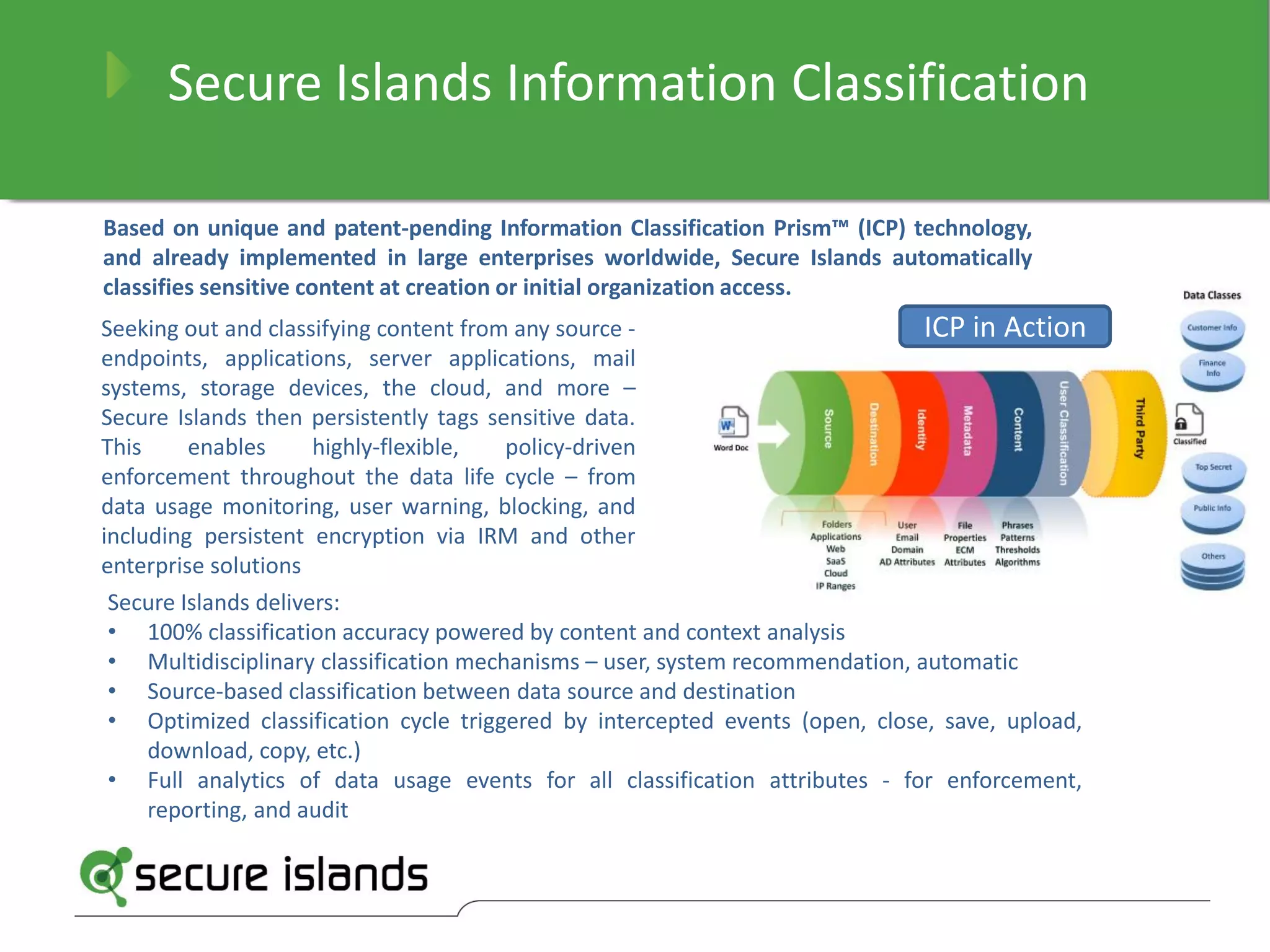
The document provides a comprehensive guide on selecting data classification solutions for enterprises, emphasizing the importance of a hybrid approach that combines automatic and manual classification. It outlines 18 critical factors to consider, including policy-driven classification, integration with existing systems, customizable enforcement, and the ability to handle multi-source and multilingual data. The conclusion highlights Secure Islands' information classification technology as a robust solution that ensures accurate and flexible data management throughout its lifecycle.