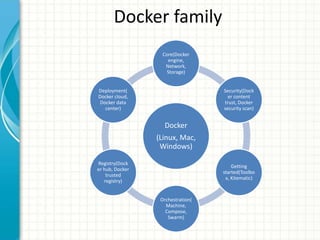
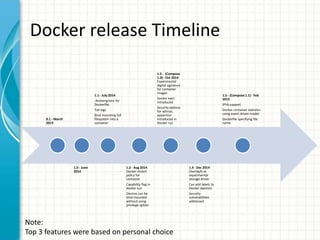
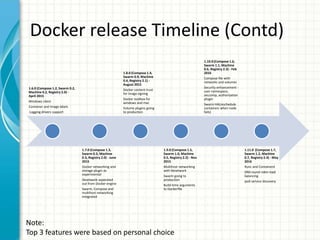
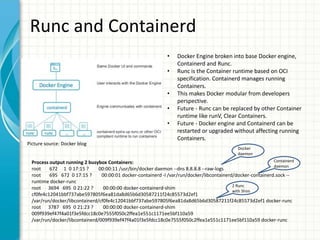
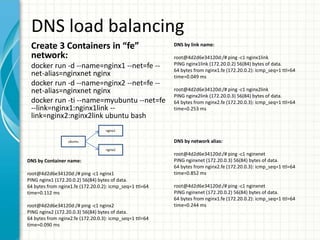
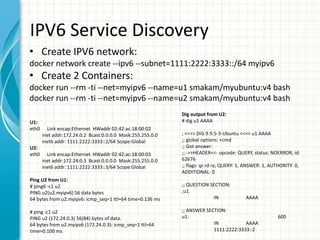
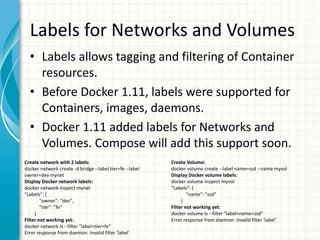
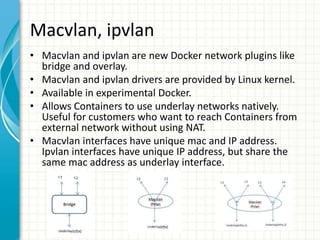
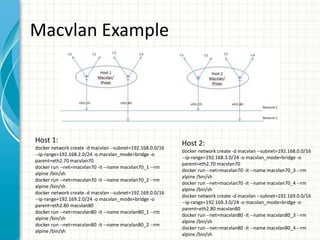
This document provides an overview of Docker 1.11, presented by Sreenivas Makam at a Docker meetup in Bangalore on June 4, 2016. Key features include the introduction of runc and containerd, built-in DNS load balancing, support for IPv6 service discovery, and new networking and volume labeling capabilities. It also discusses the evolution of Docker with a comprehensive release timeline and highlights experimental features such as macvlan and ipvlan networking plugins.