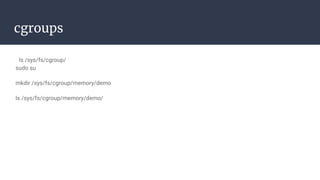
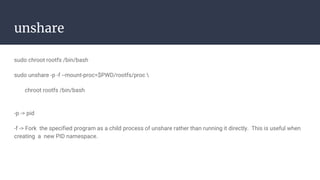
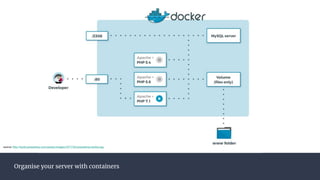
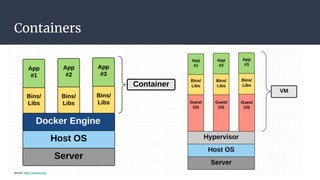
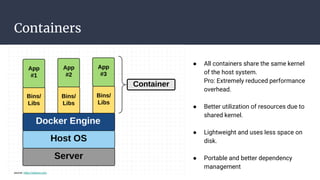
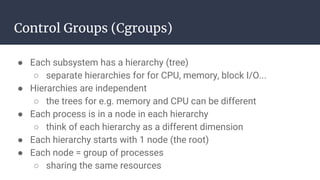
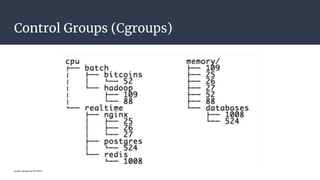
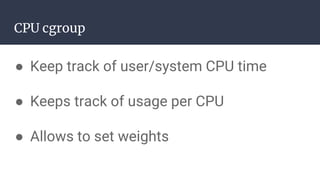
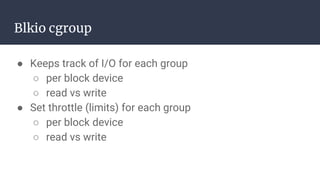
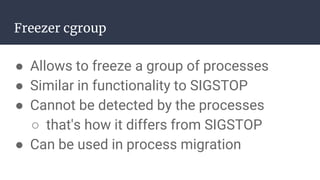
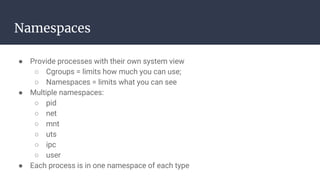
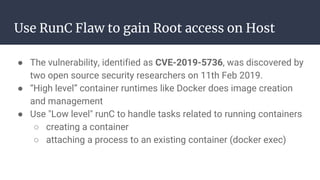
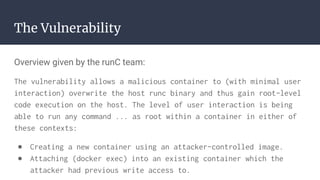
The document provides an introduction to containers, particularly using Docker, outlining their benefits such as lightweight, portability, and efficient resource utilization. It explains key concepts like images, containers, Docker commands, and the underlying building blocks like cgroups and namespaces. Security considerations are also discussed, including a vulnerability in the runc component that could allow malicious access to the host environment.










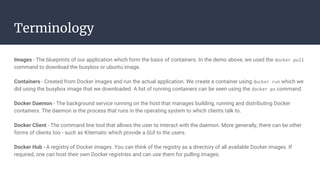






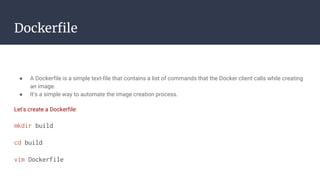
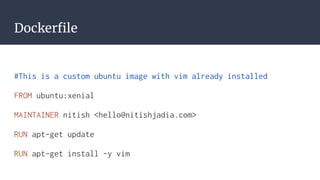
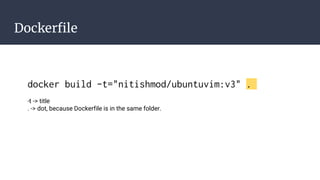
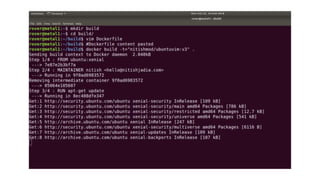
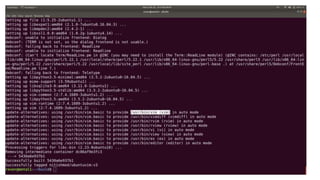

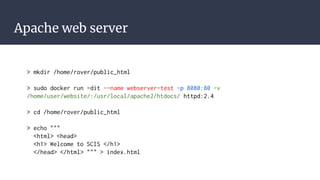
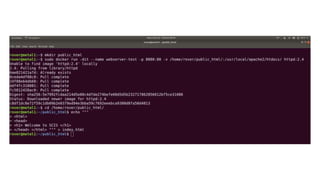















![Bibliography
14. Comparing different containers | https://ieeexplore.ieee.org/document/8075934
15. Beginners Guide to Containers Technology and How it Actually Works[video] | https://is.gd/CzTb1d
16. My Docker Guide | https://github.com/w4rb0y/devOpsNotes/blob/master/dockerGuide.md
17. Google Cloud | https://cloud.google.com/containers/
18. Containers from scratch | https://ericchiang.github.io/post/containers-from-scratch/](https://image.slidesharecdn.com/introductiontocontainers-190813044130/85/Introduction-to-containers-73-320.jpg)