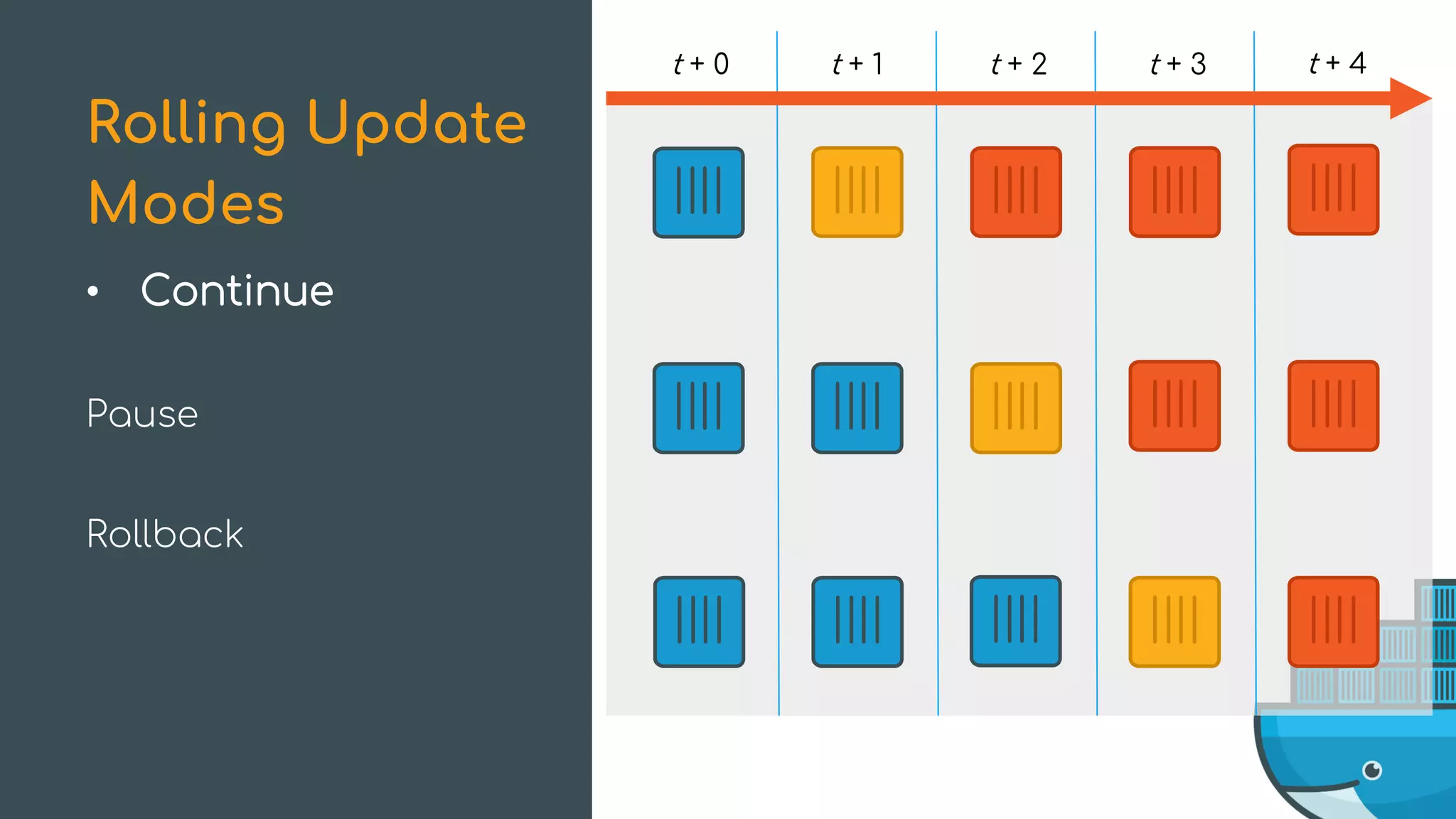
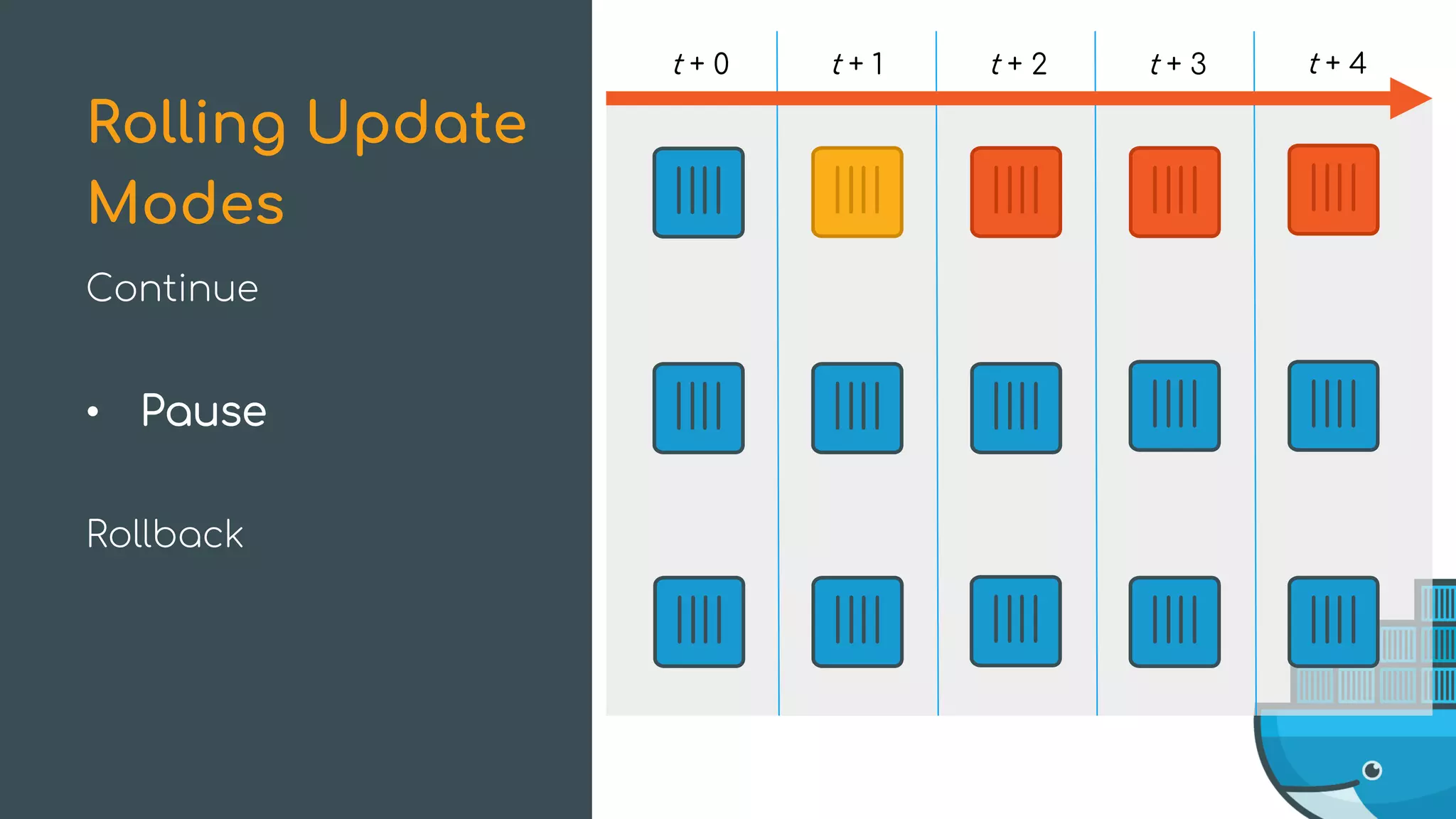
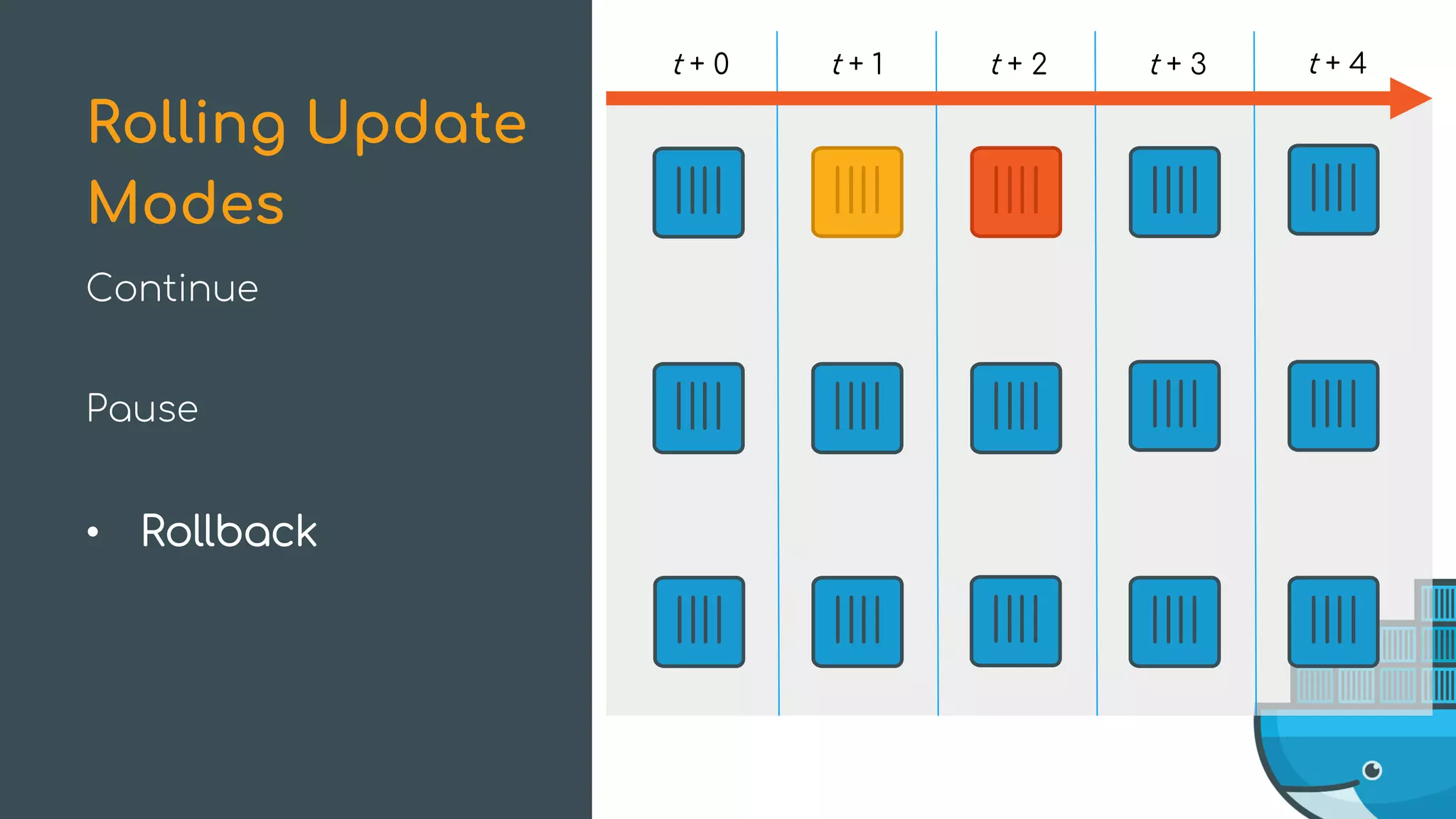
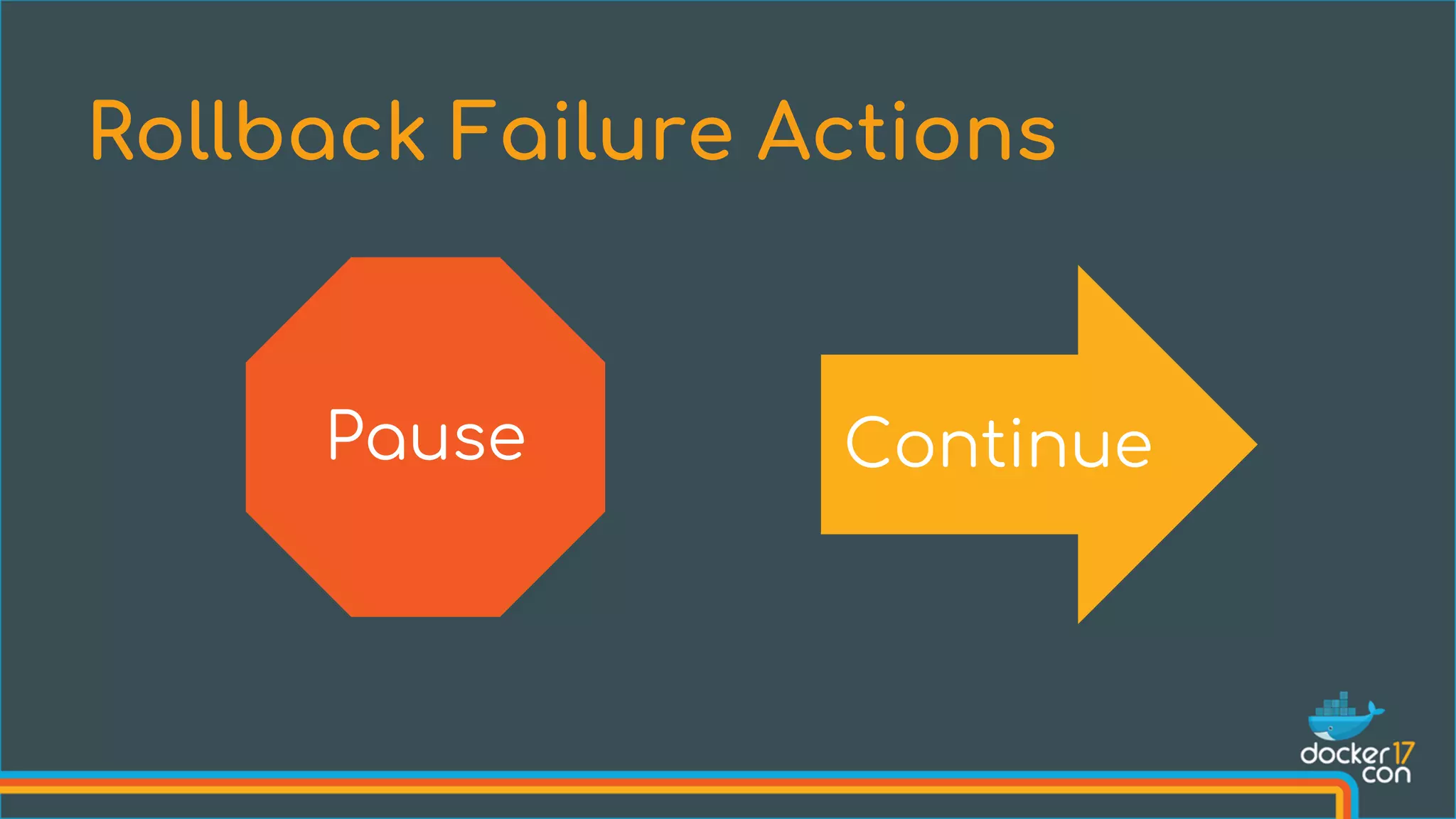
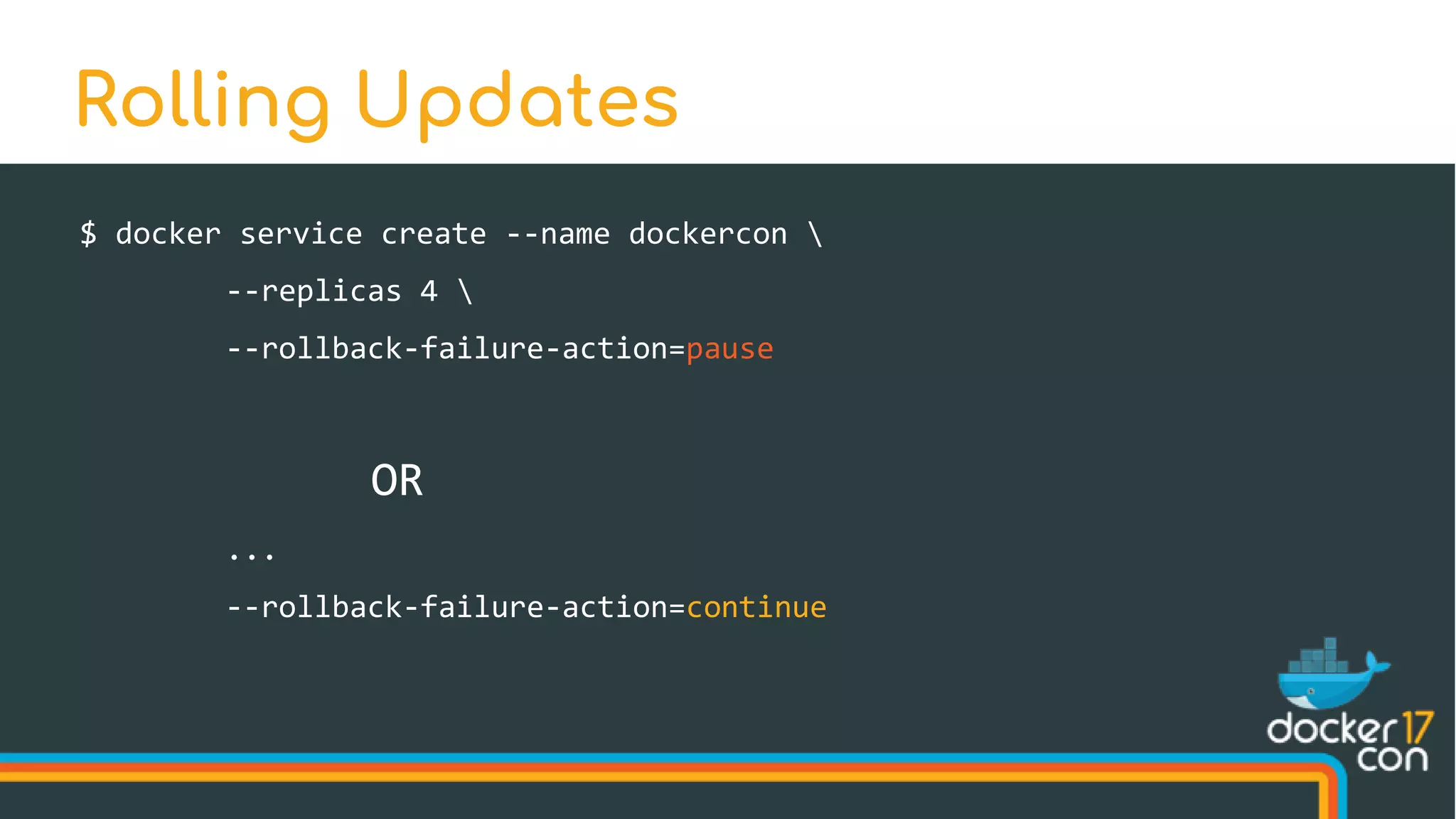
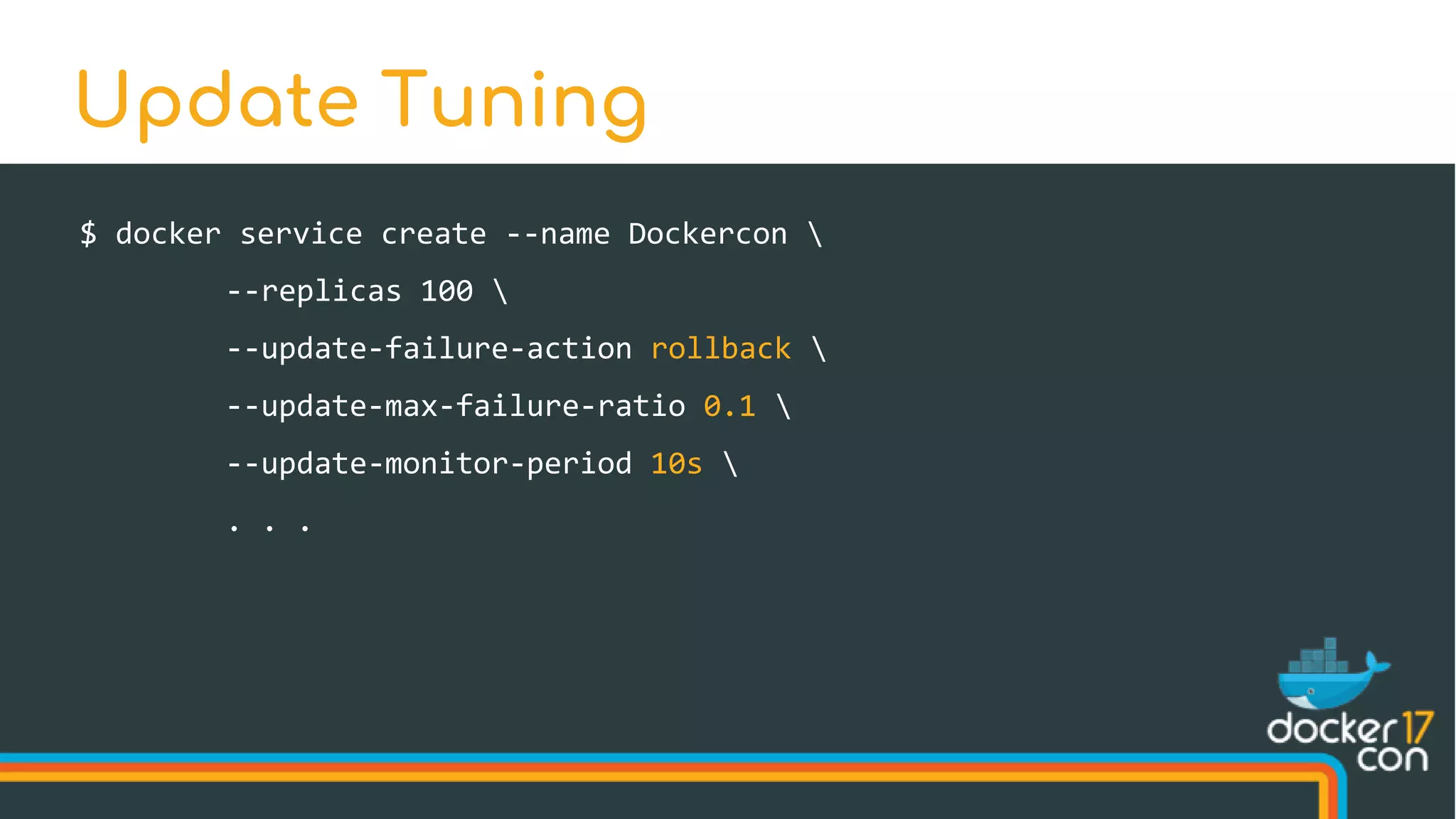
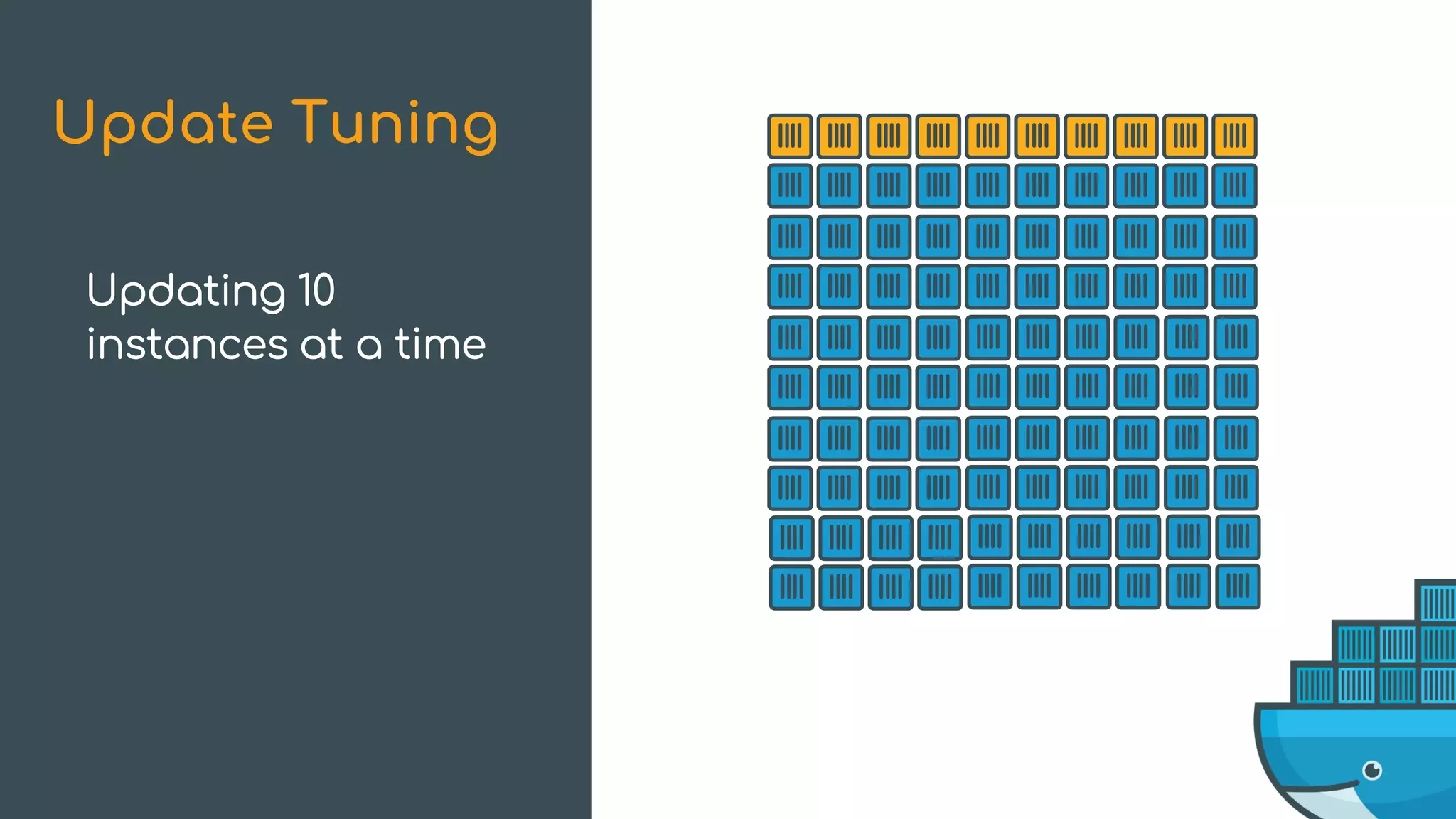
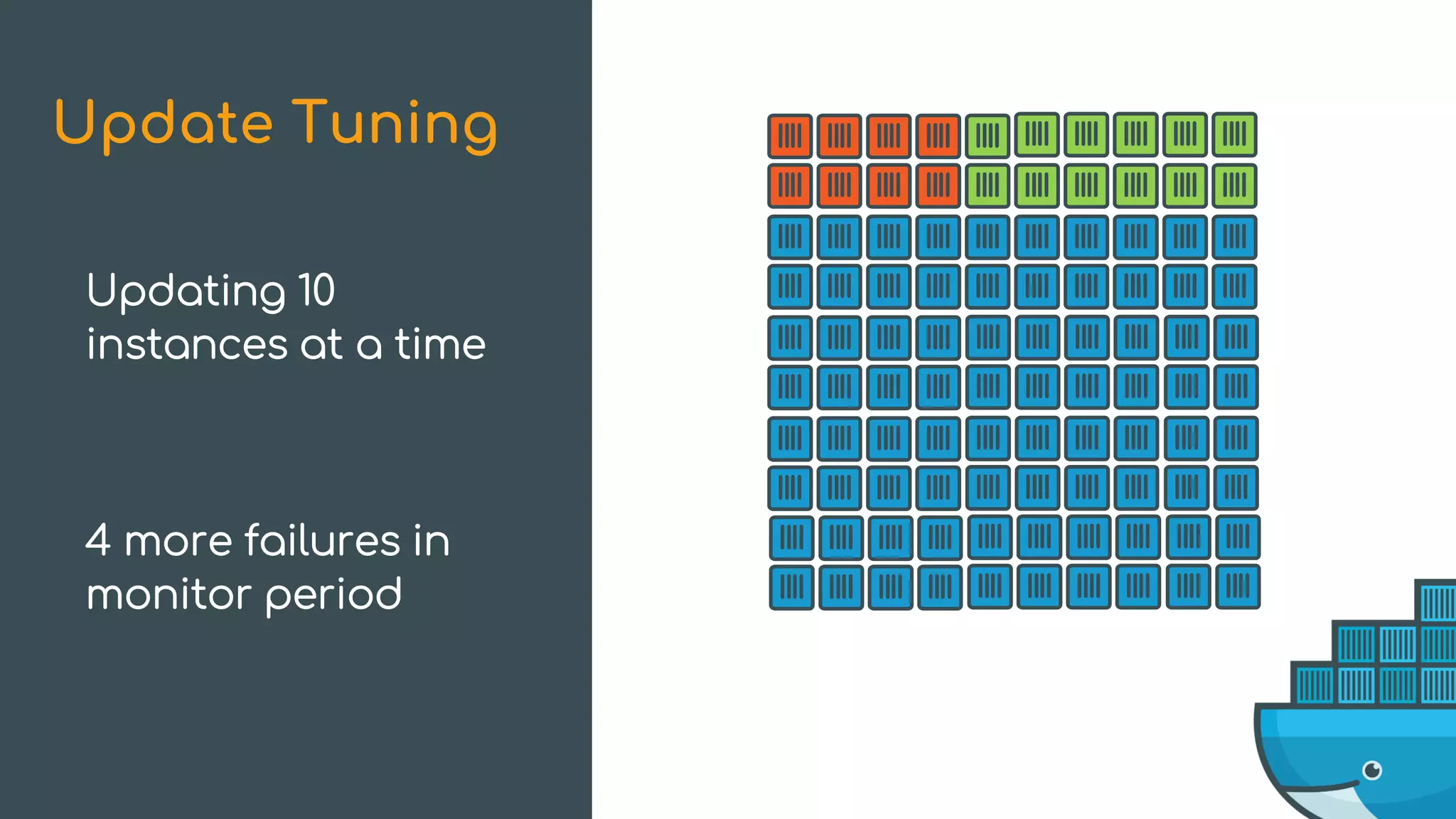
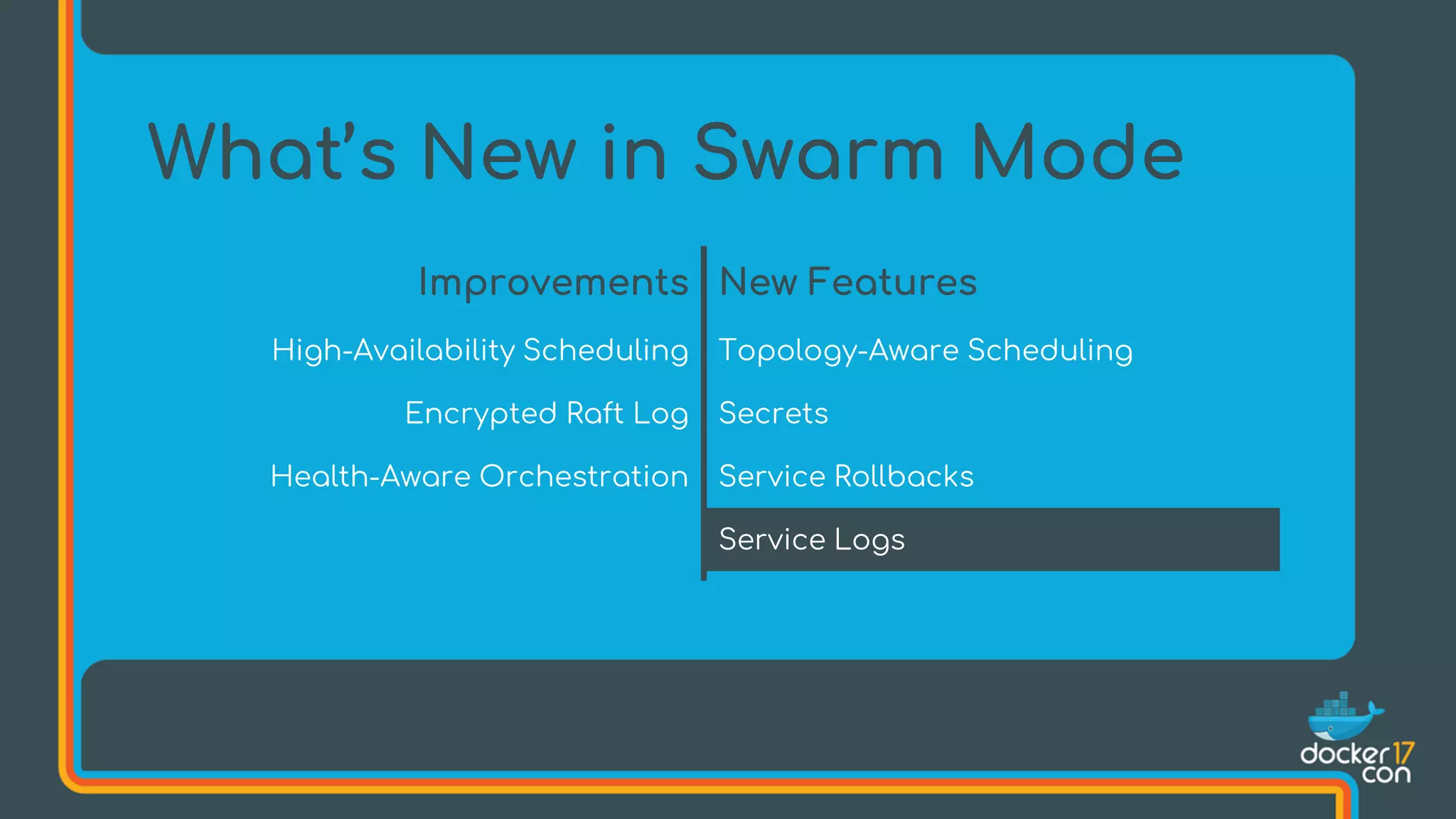
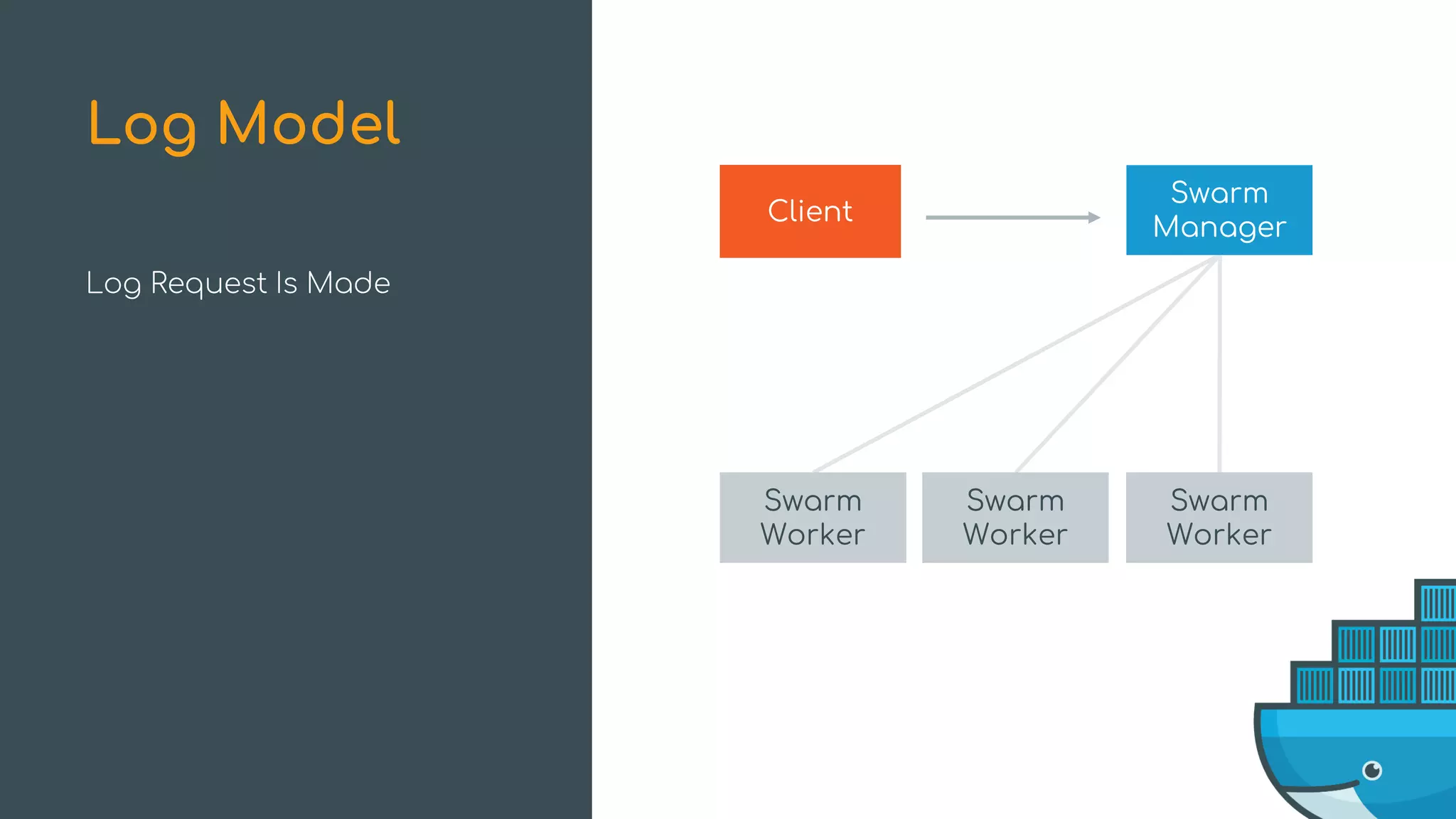
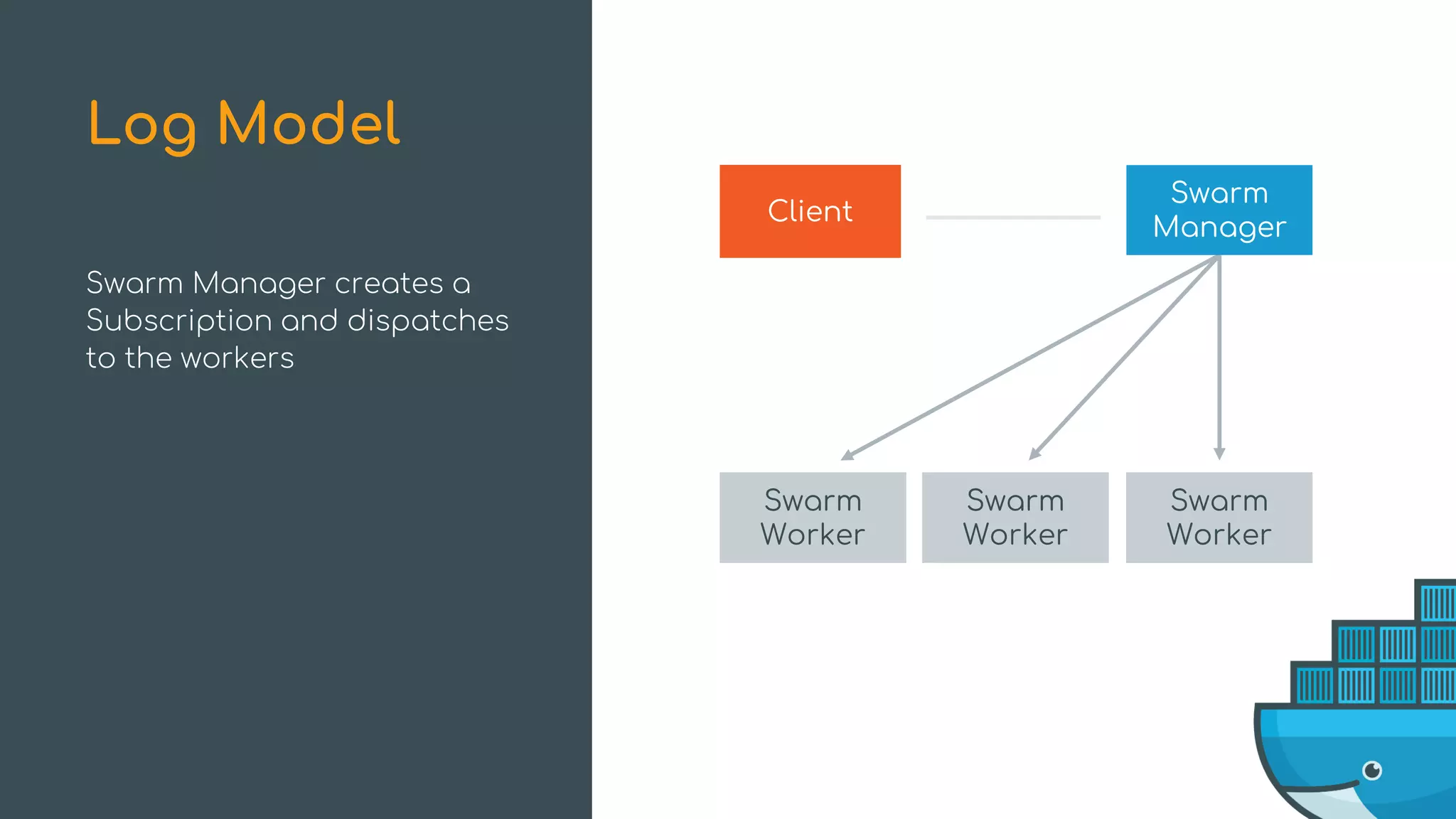
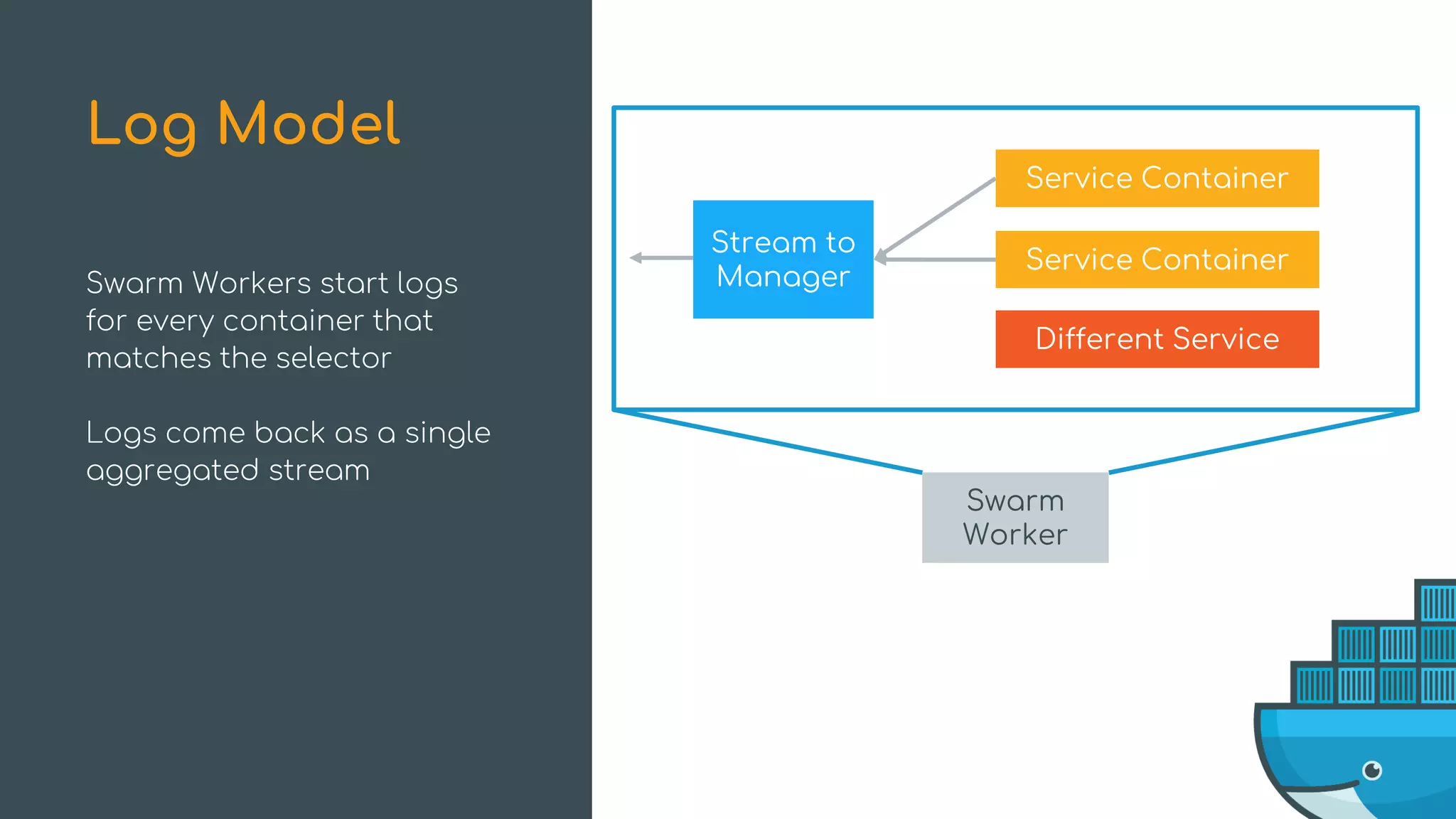
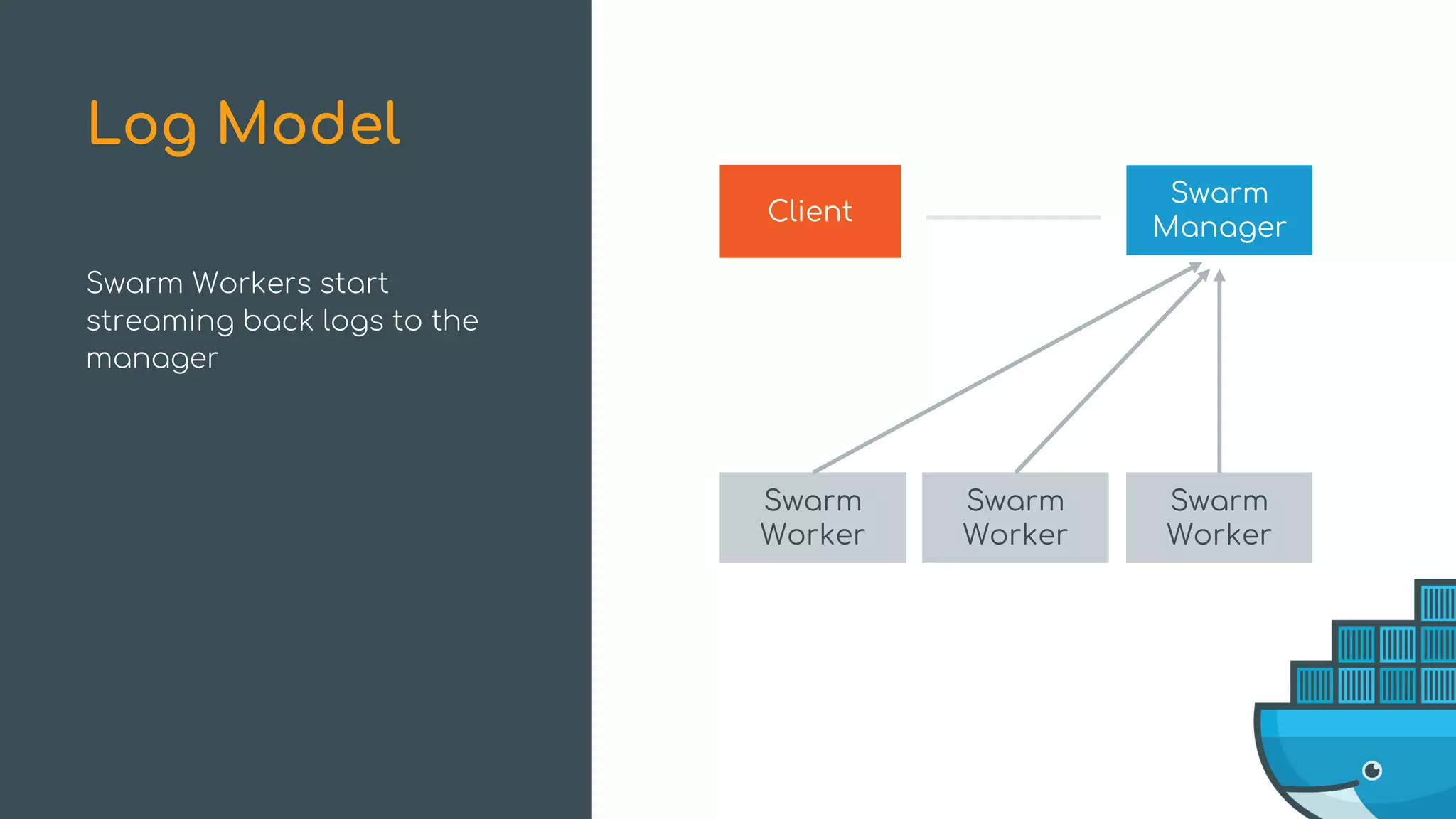
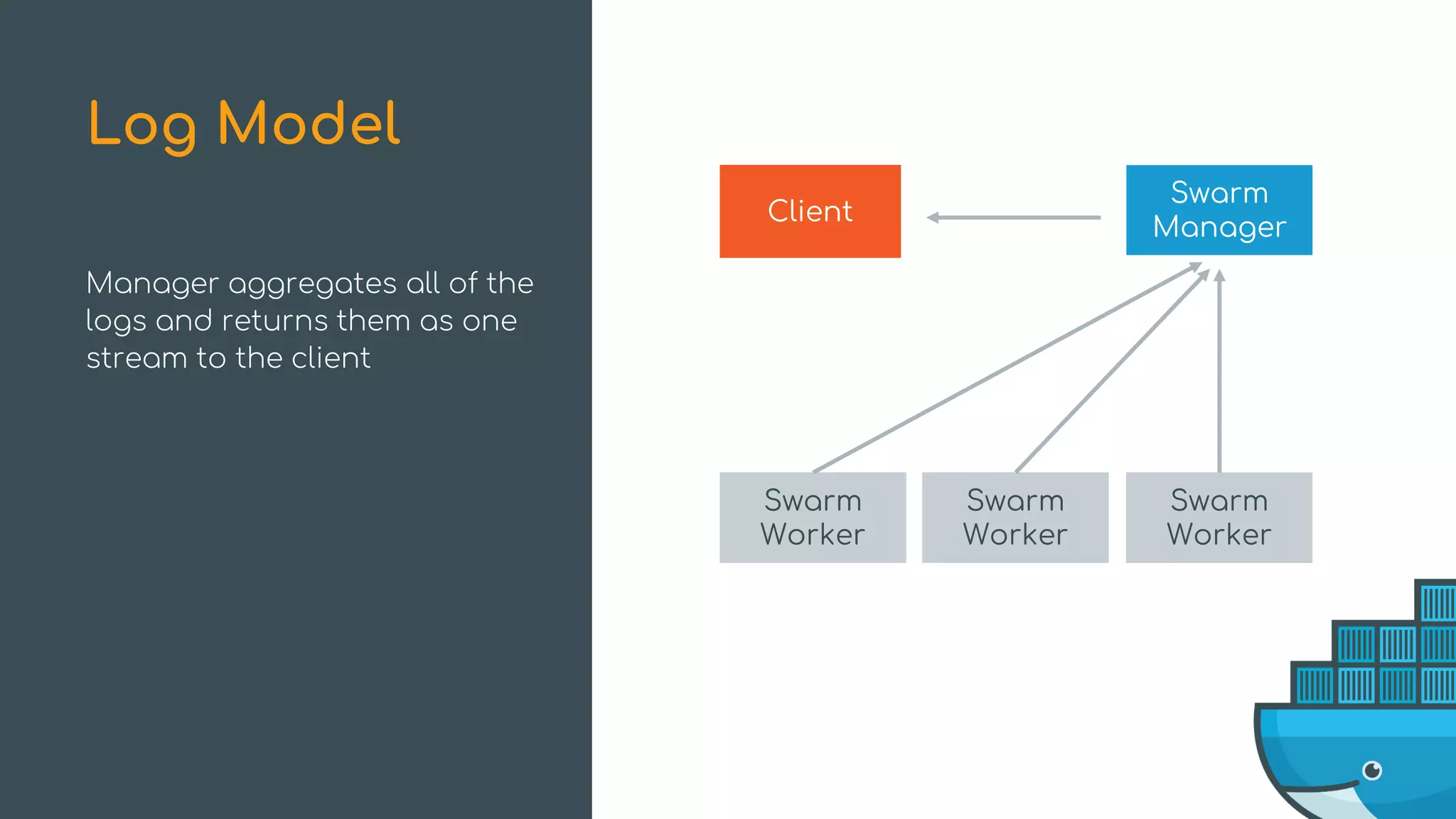
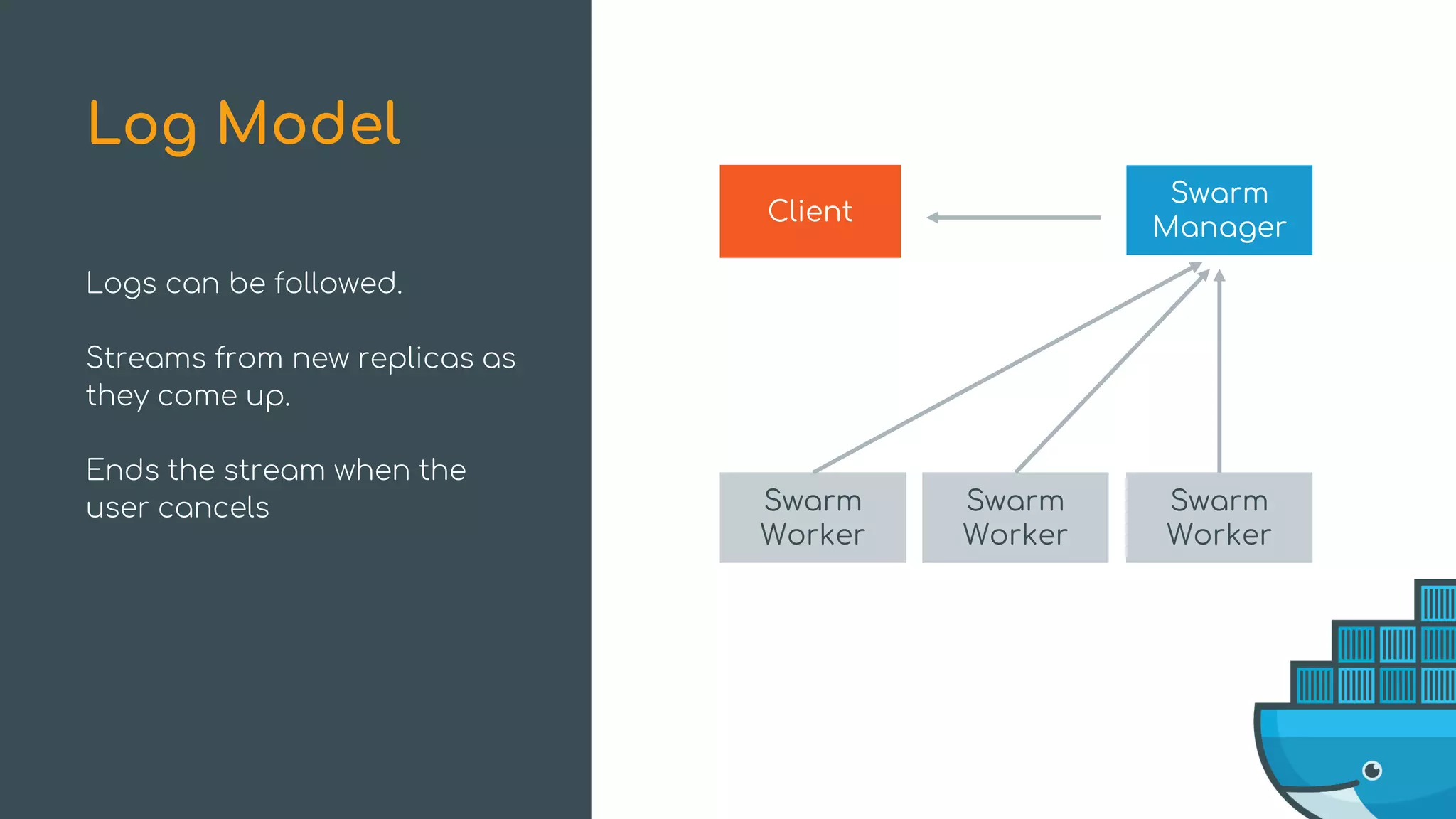
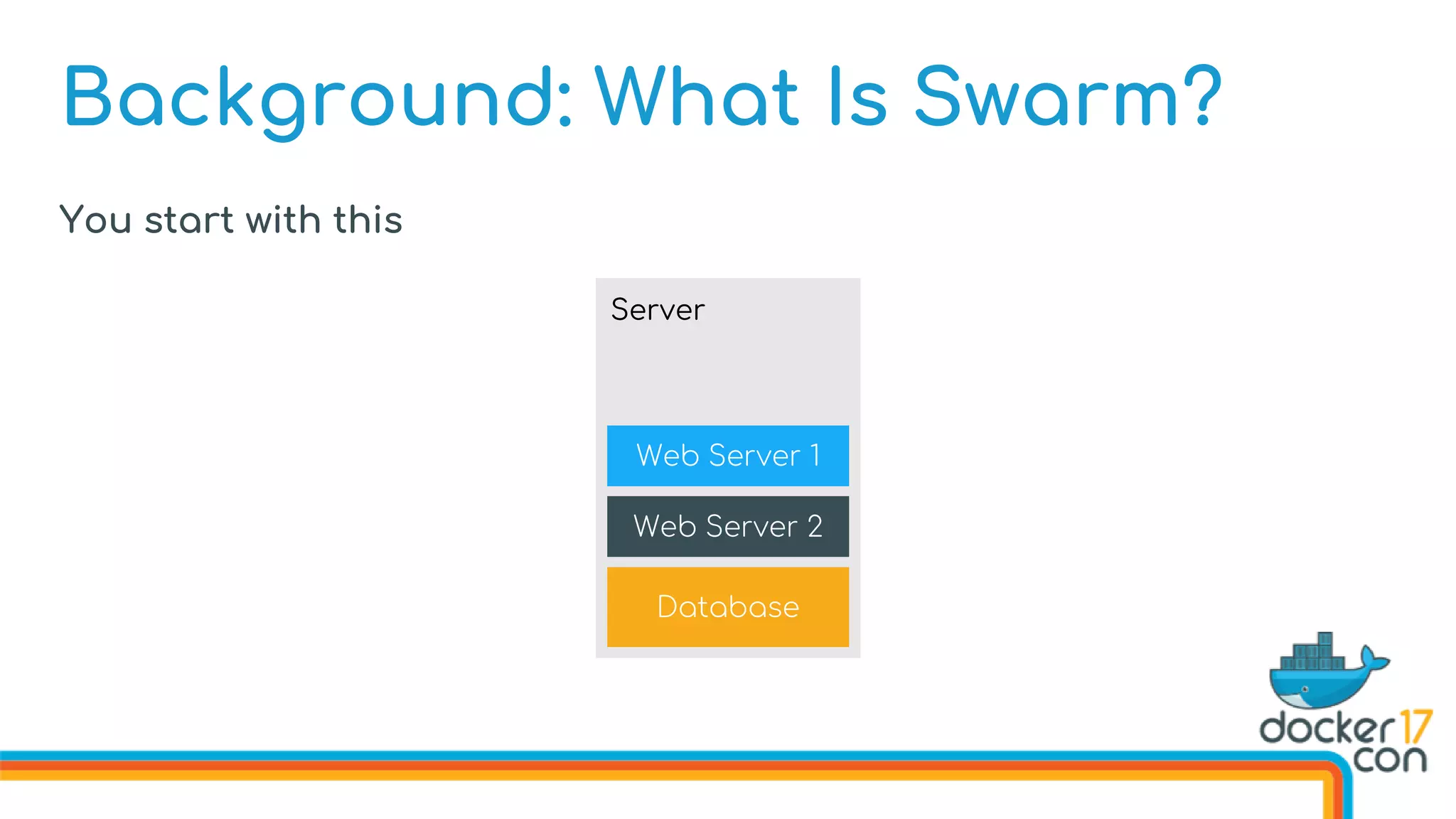
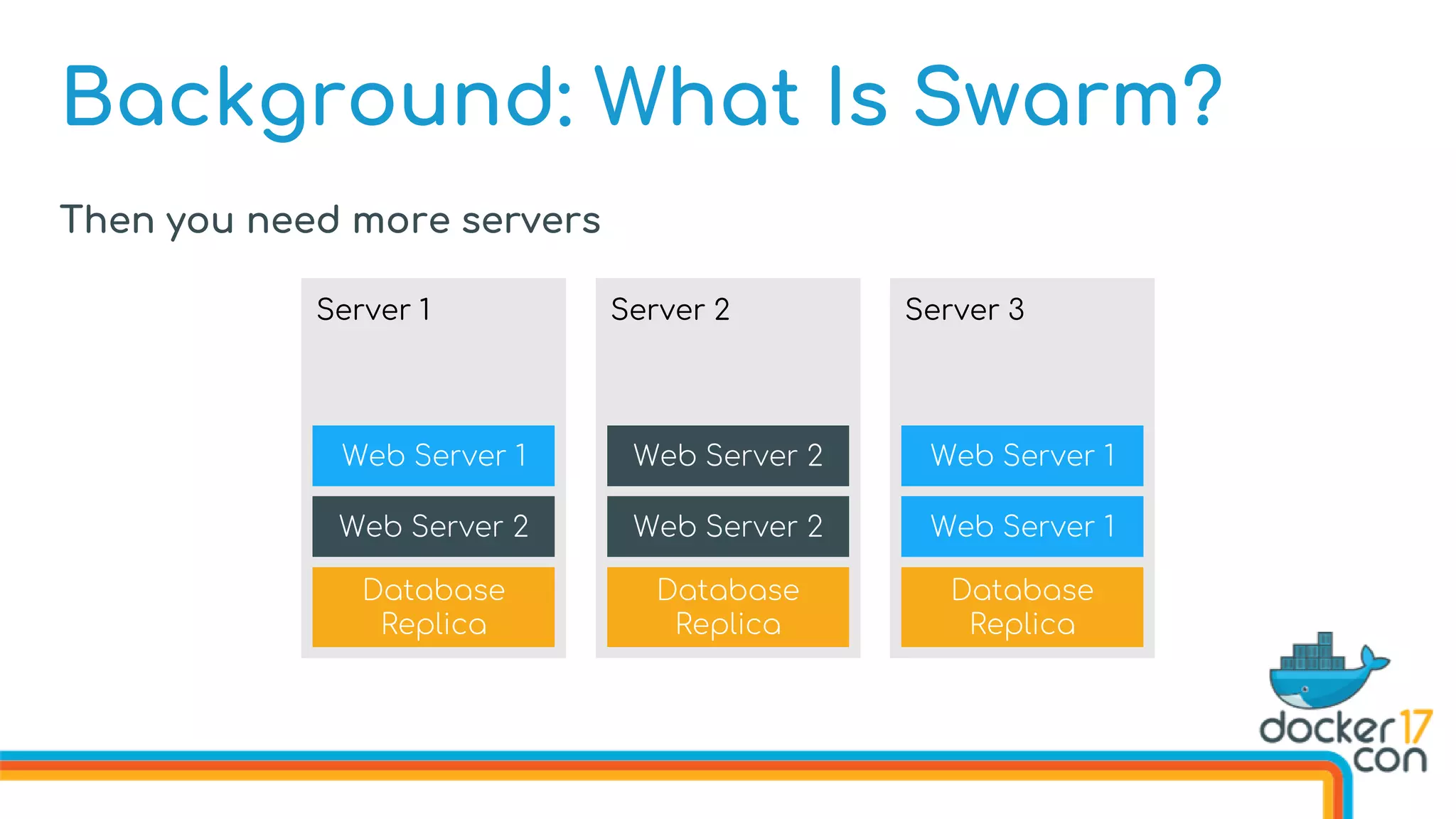
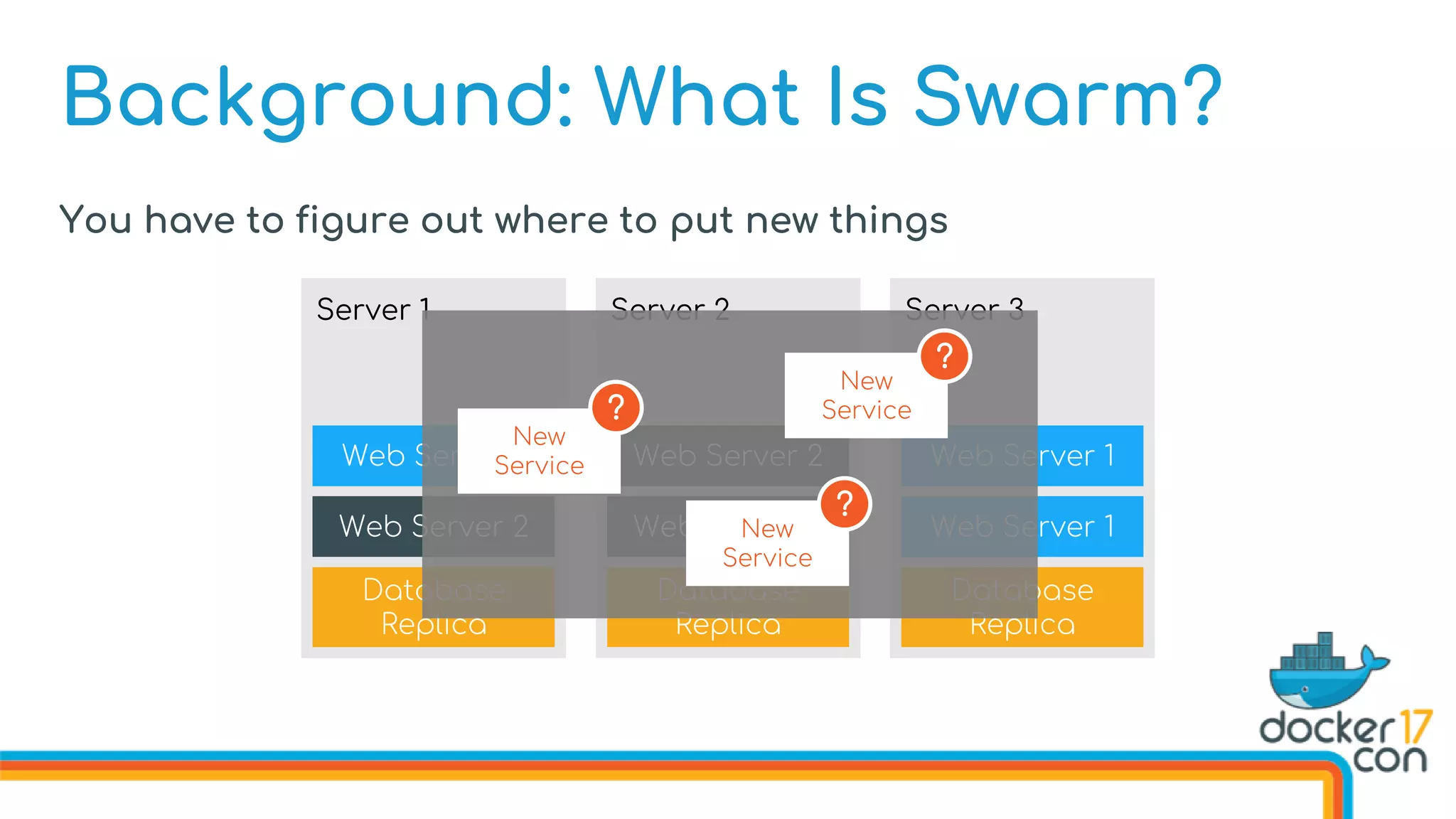
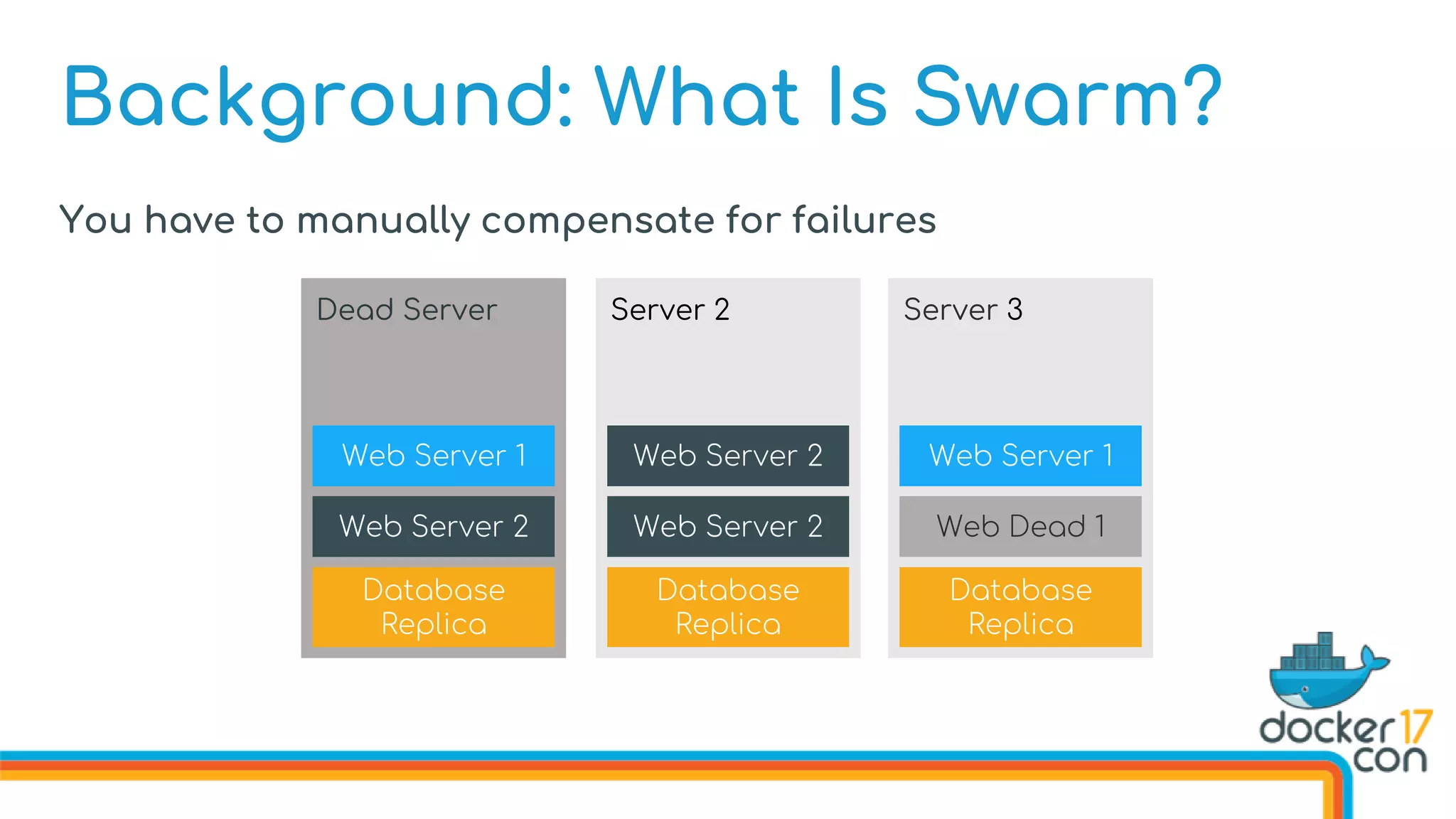
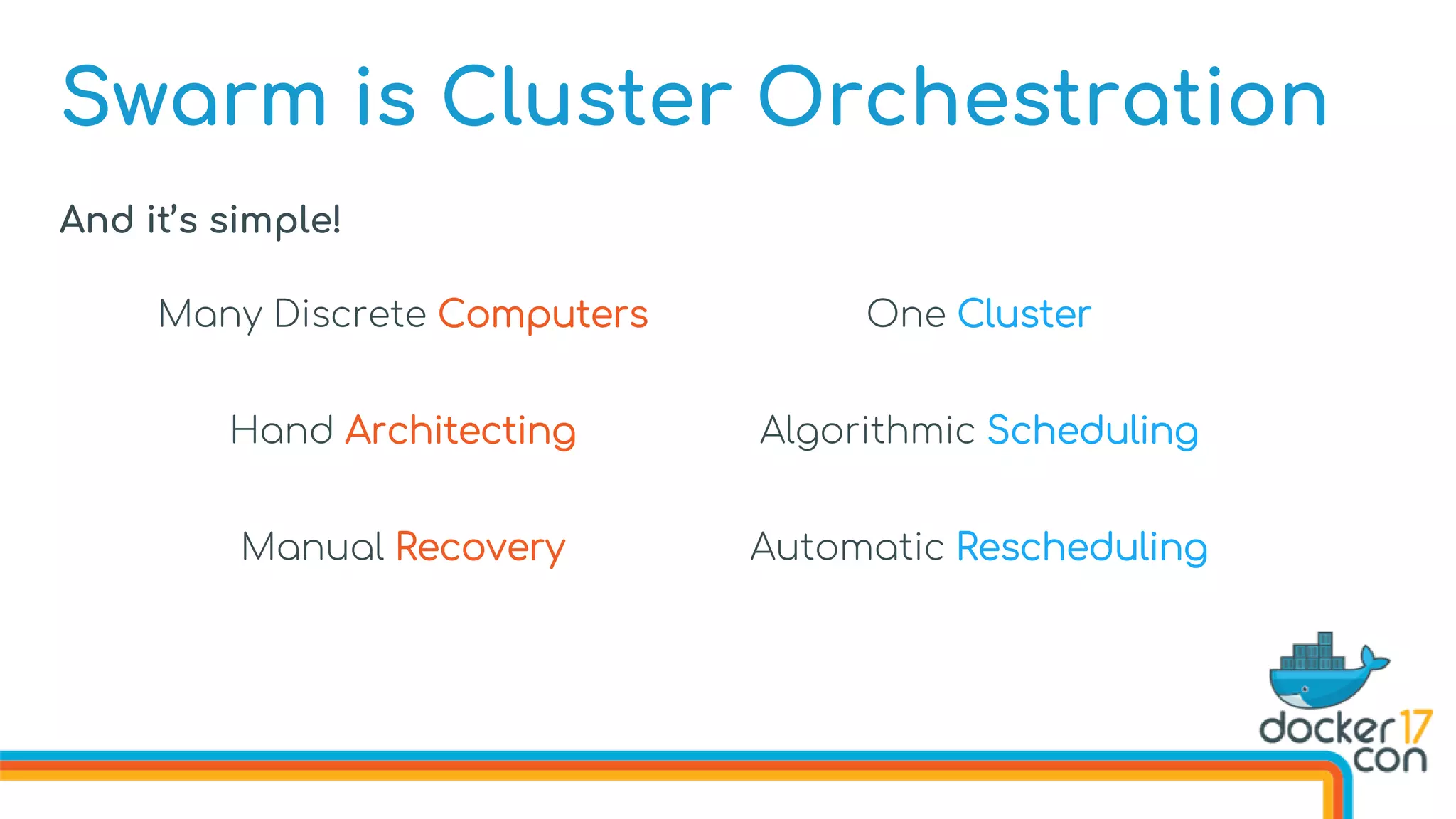
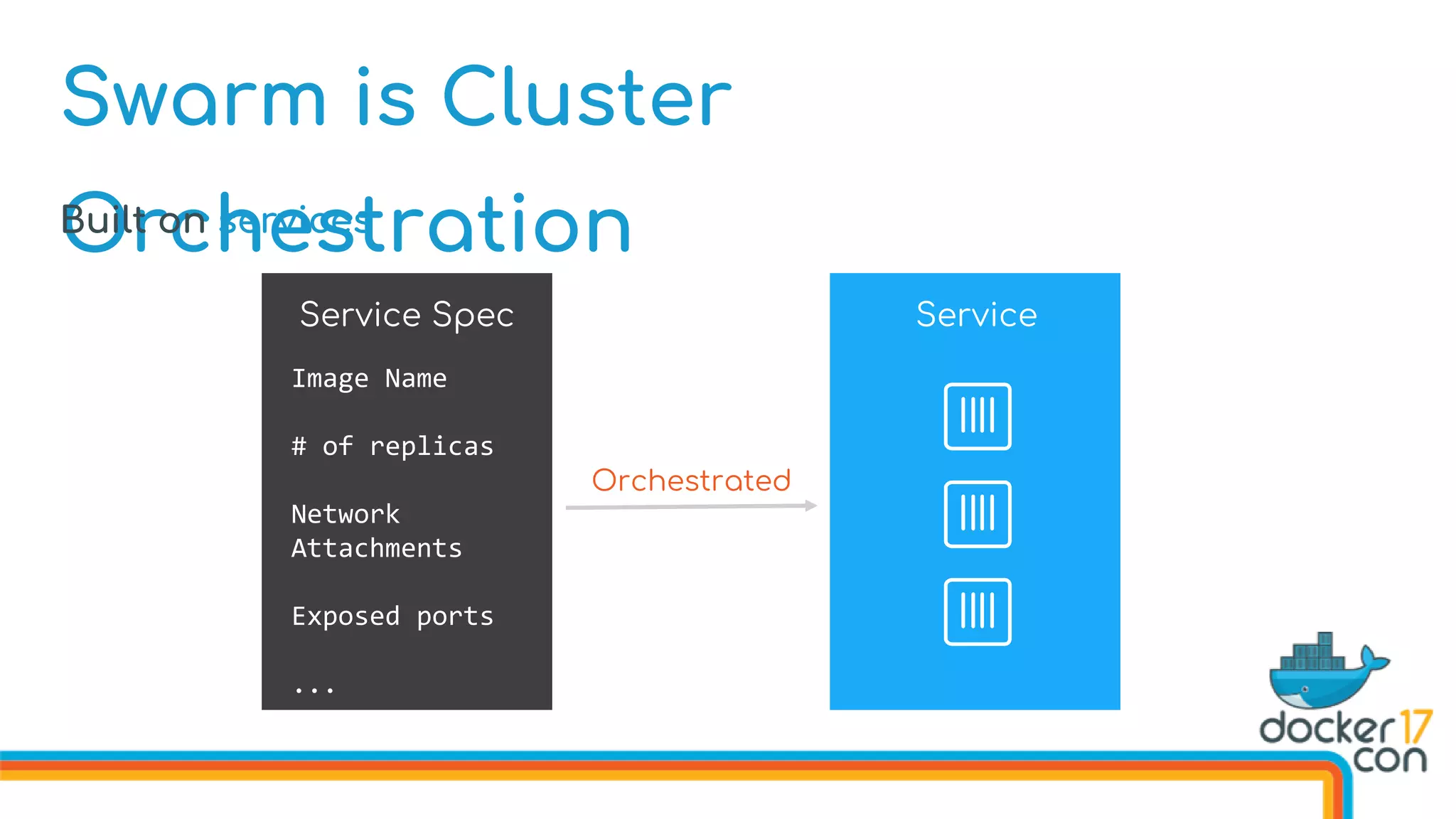
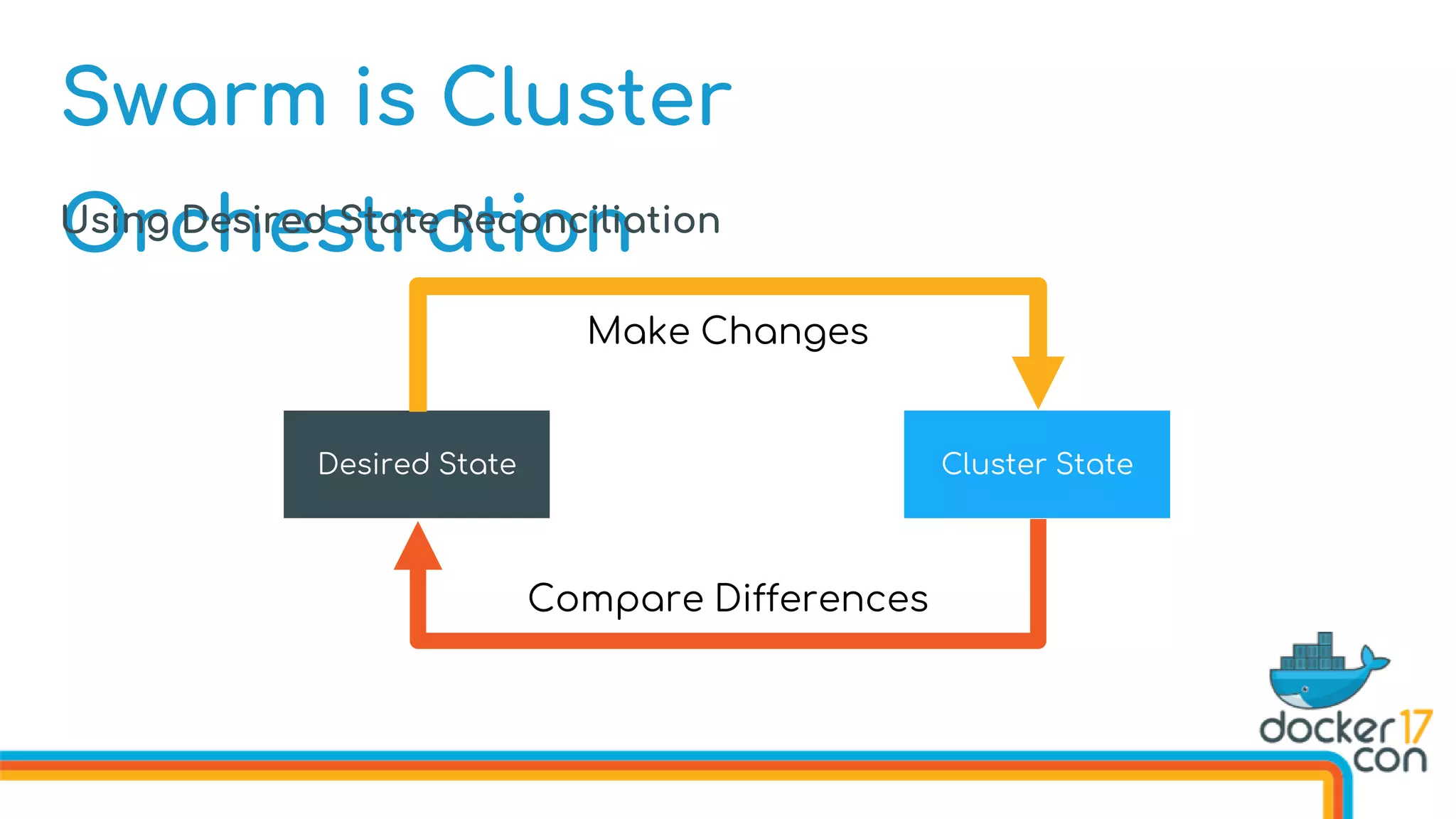
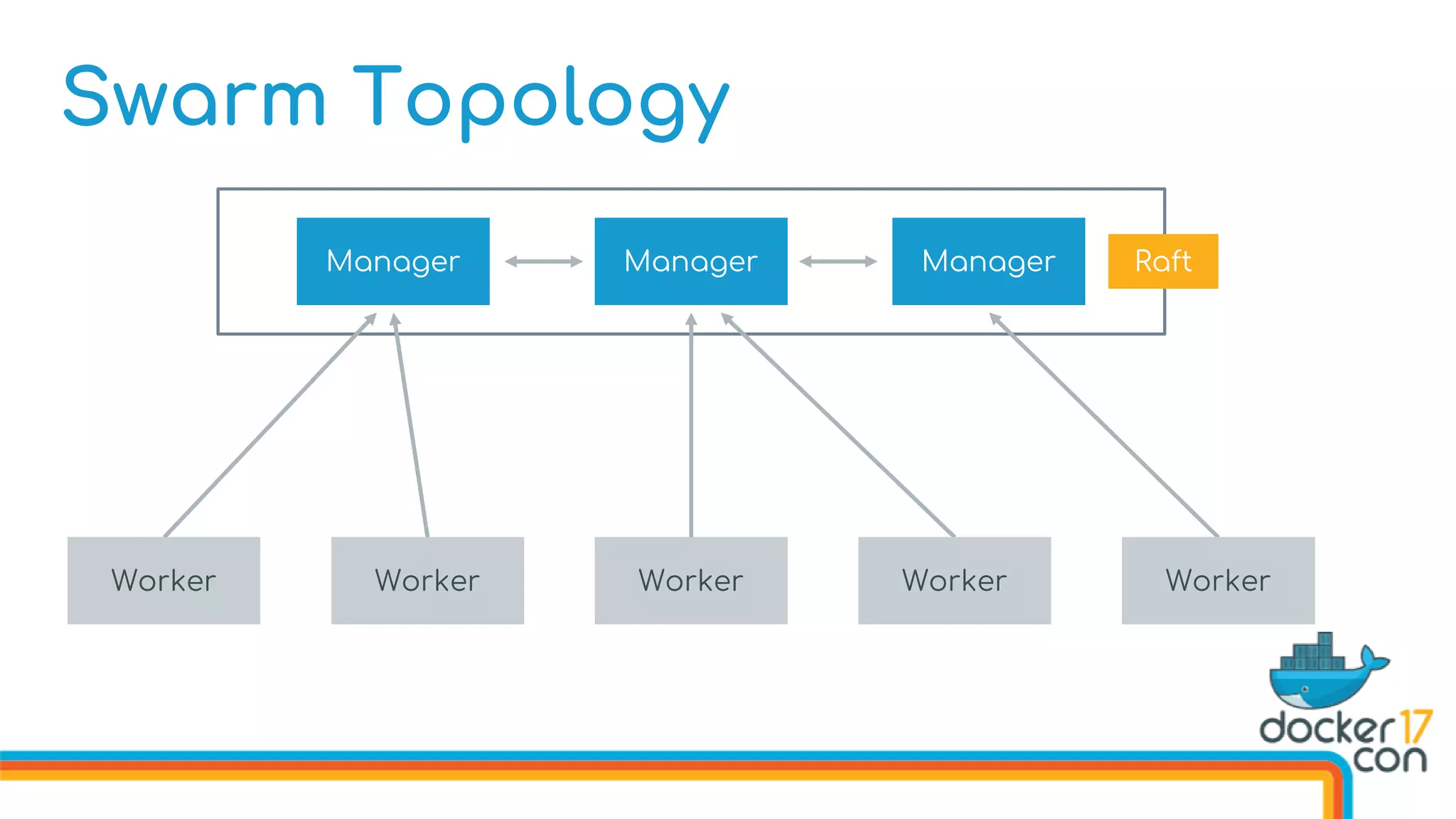
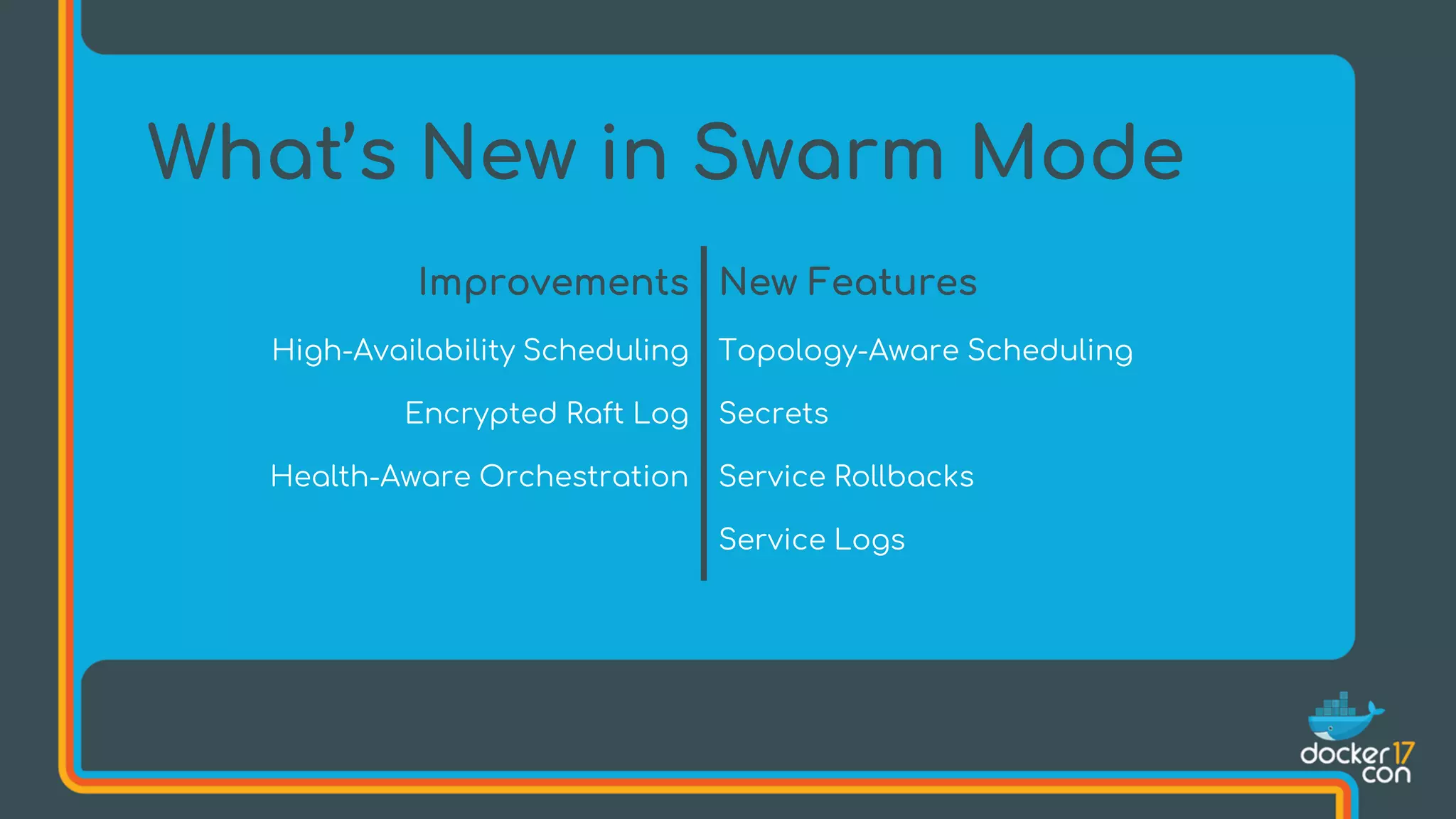
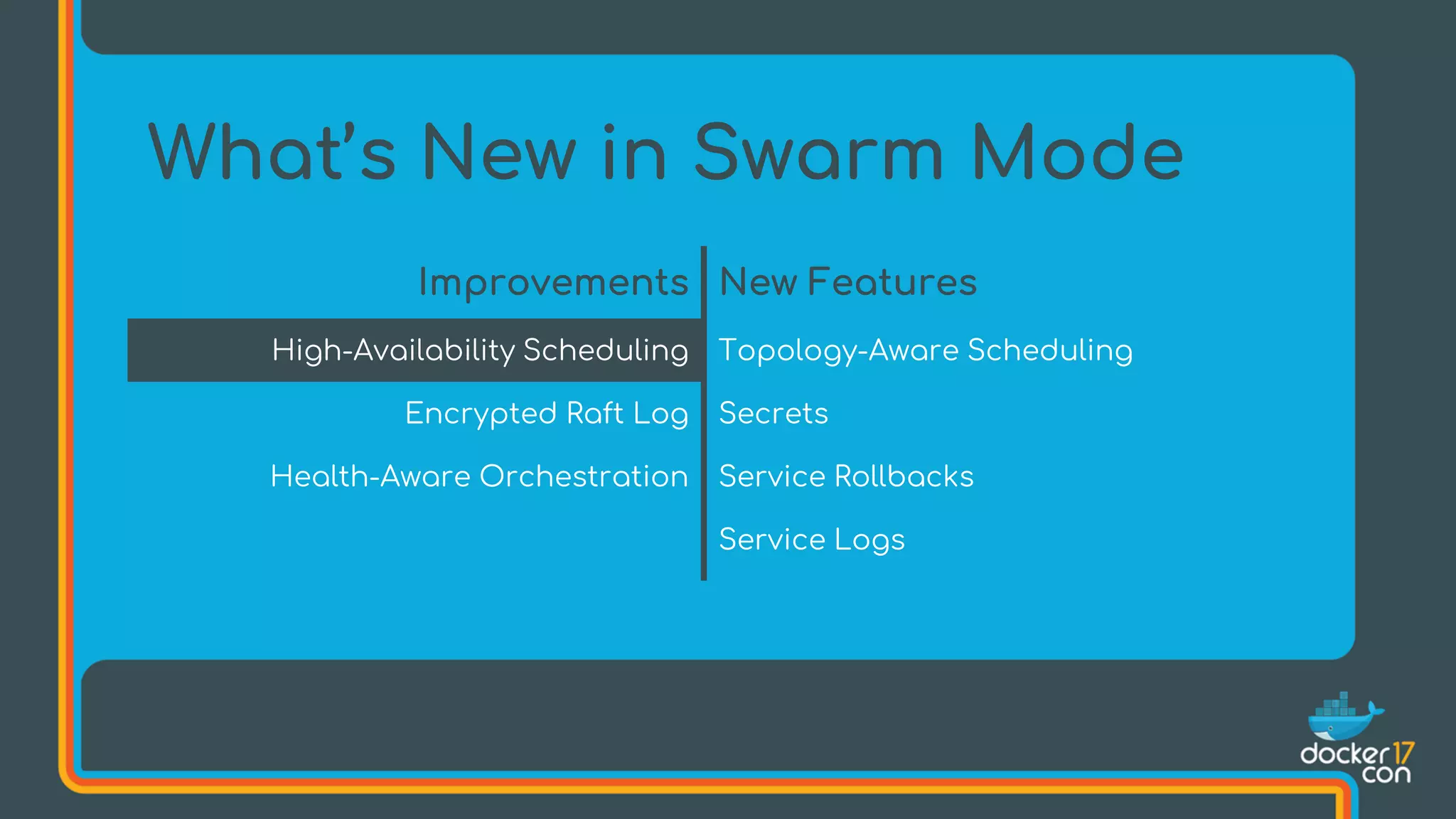
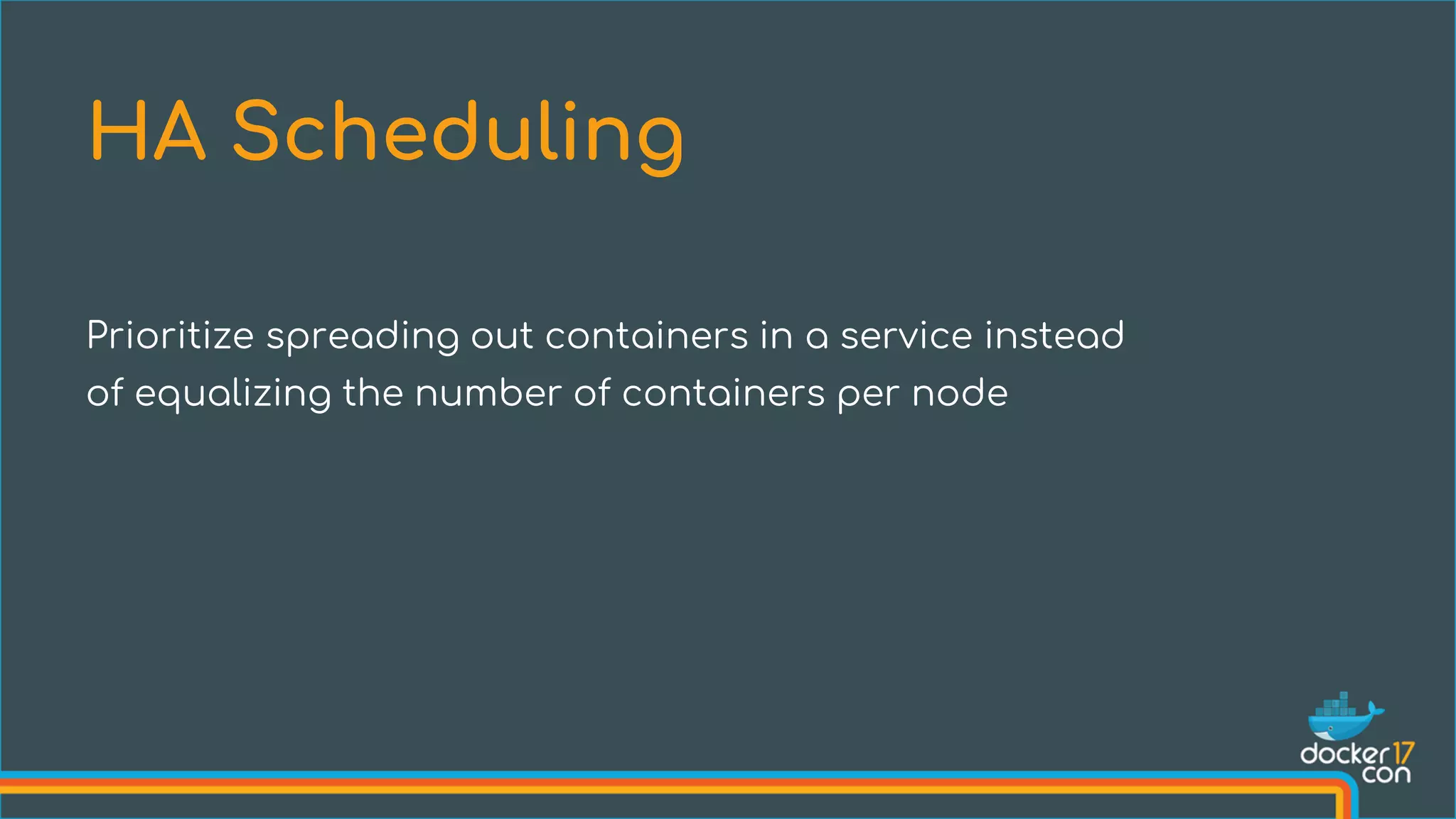
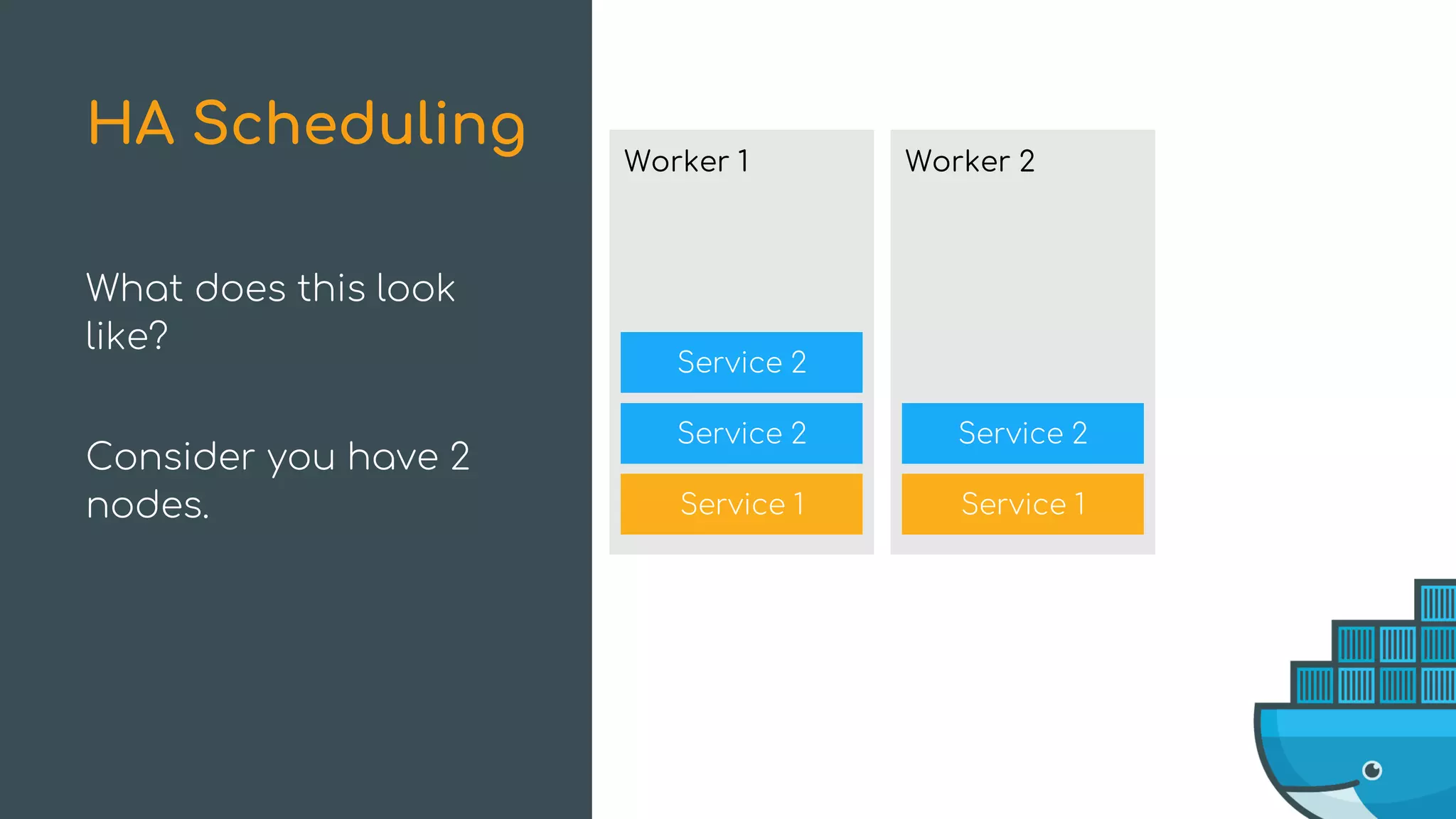
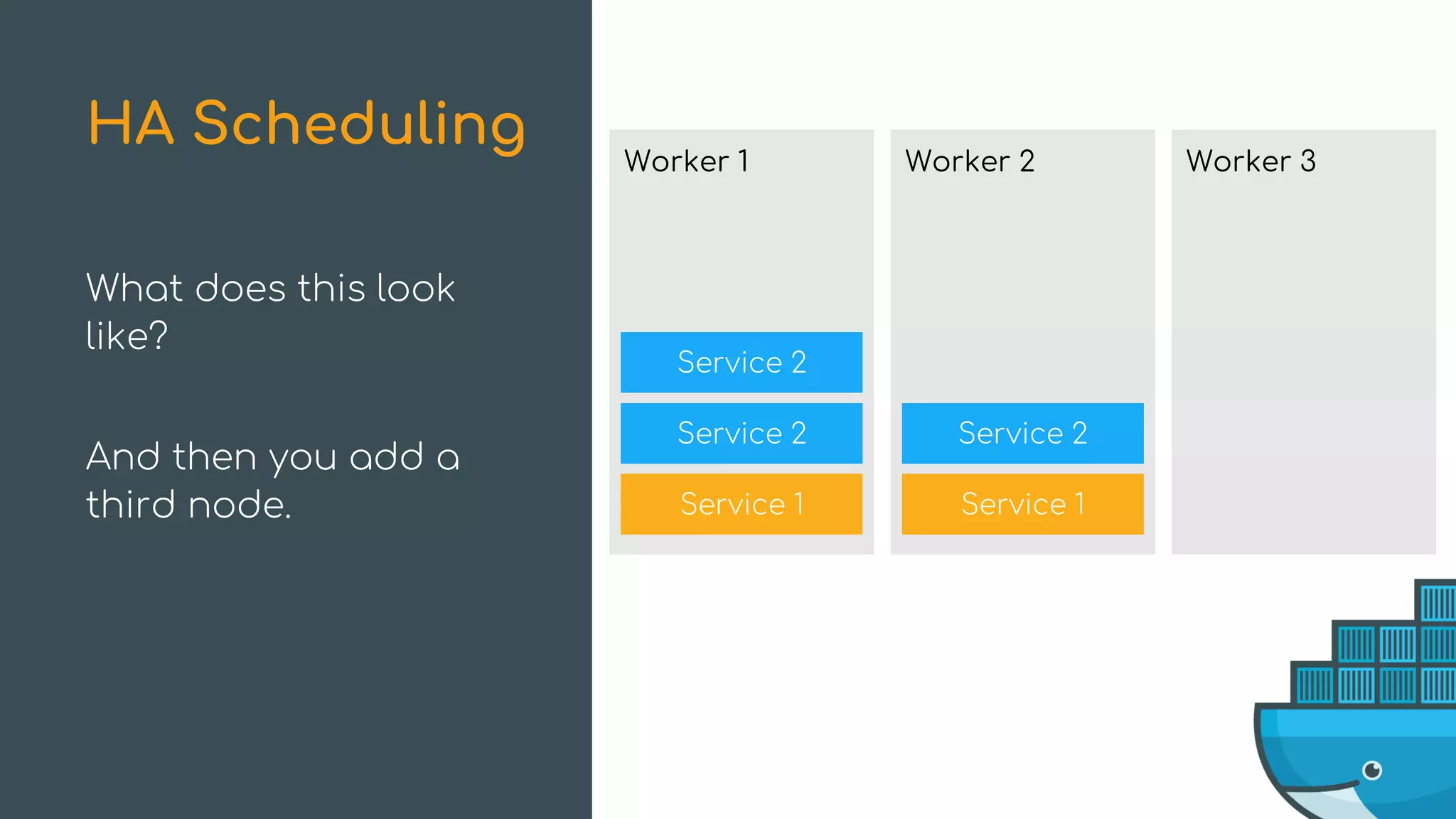
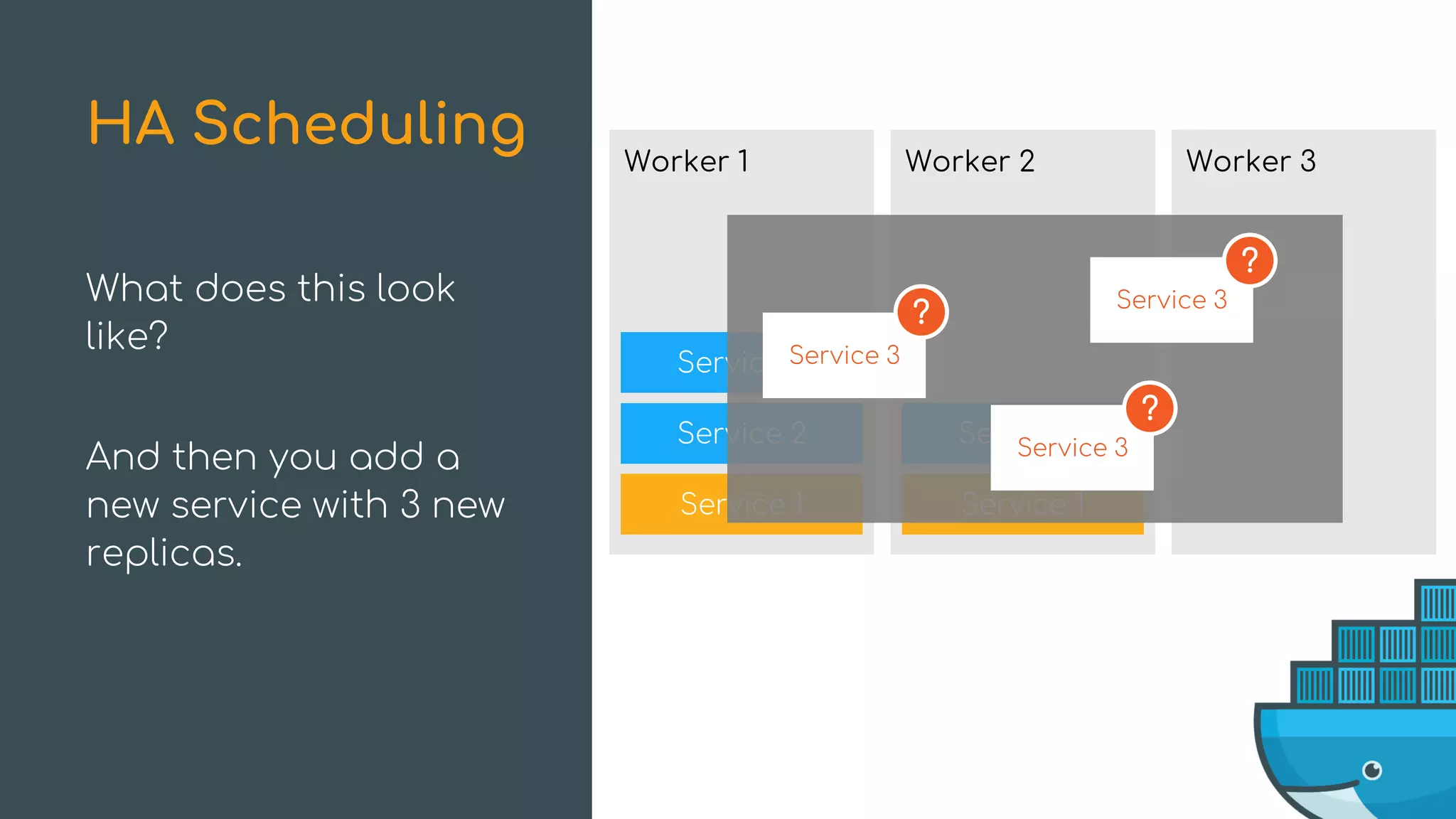
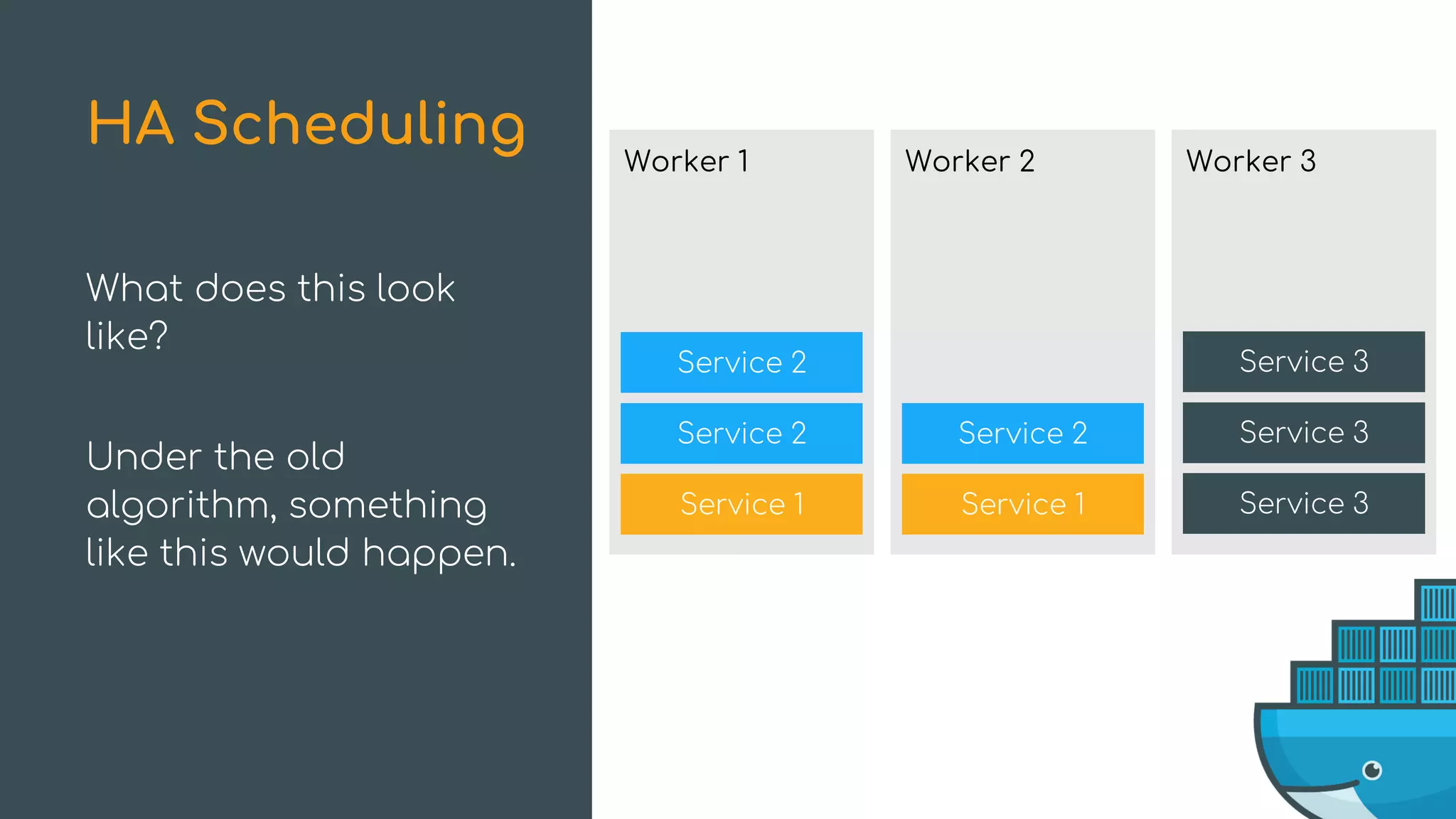
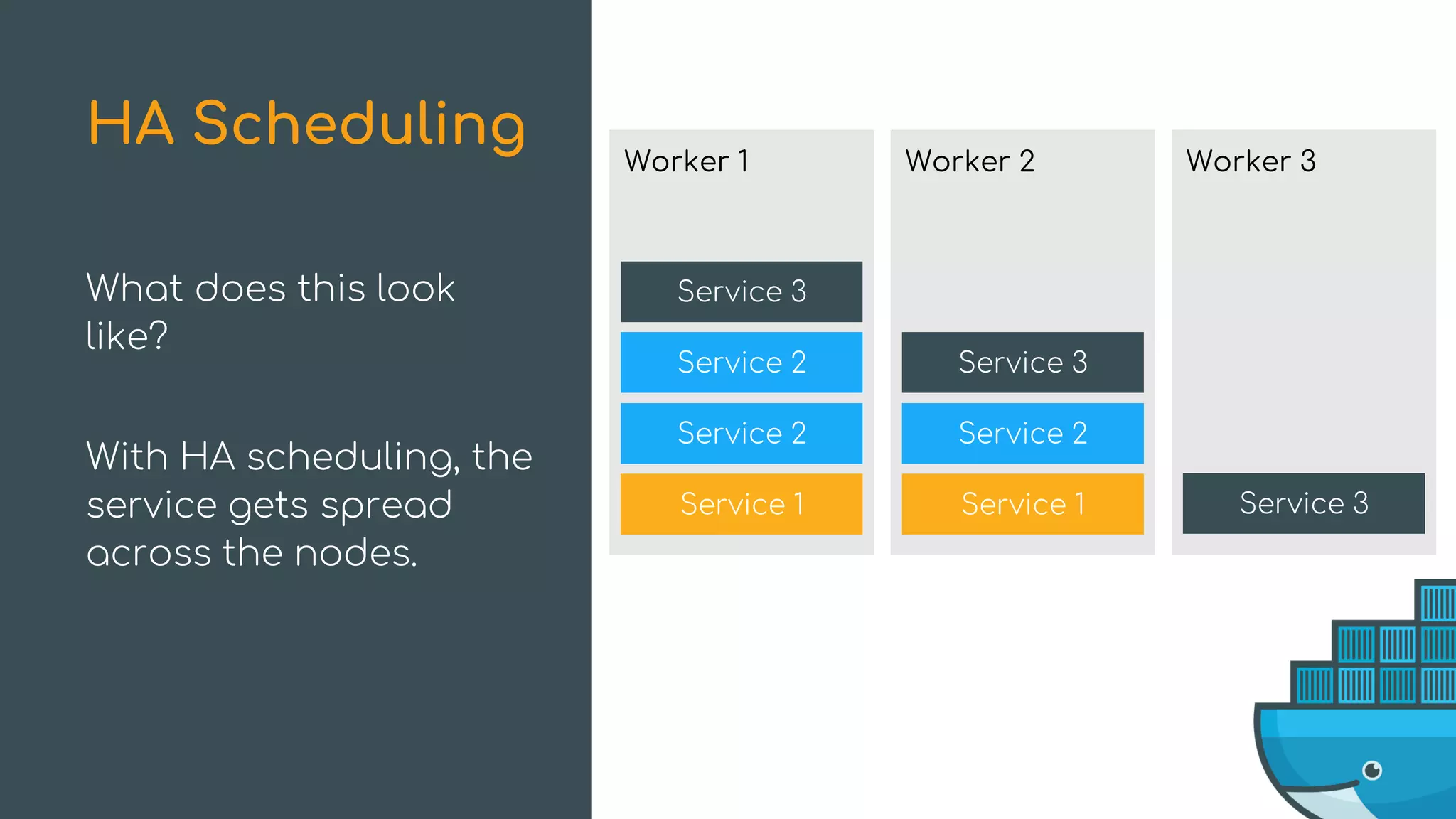
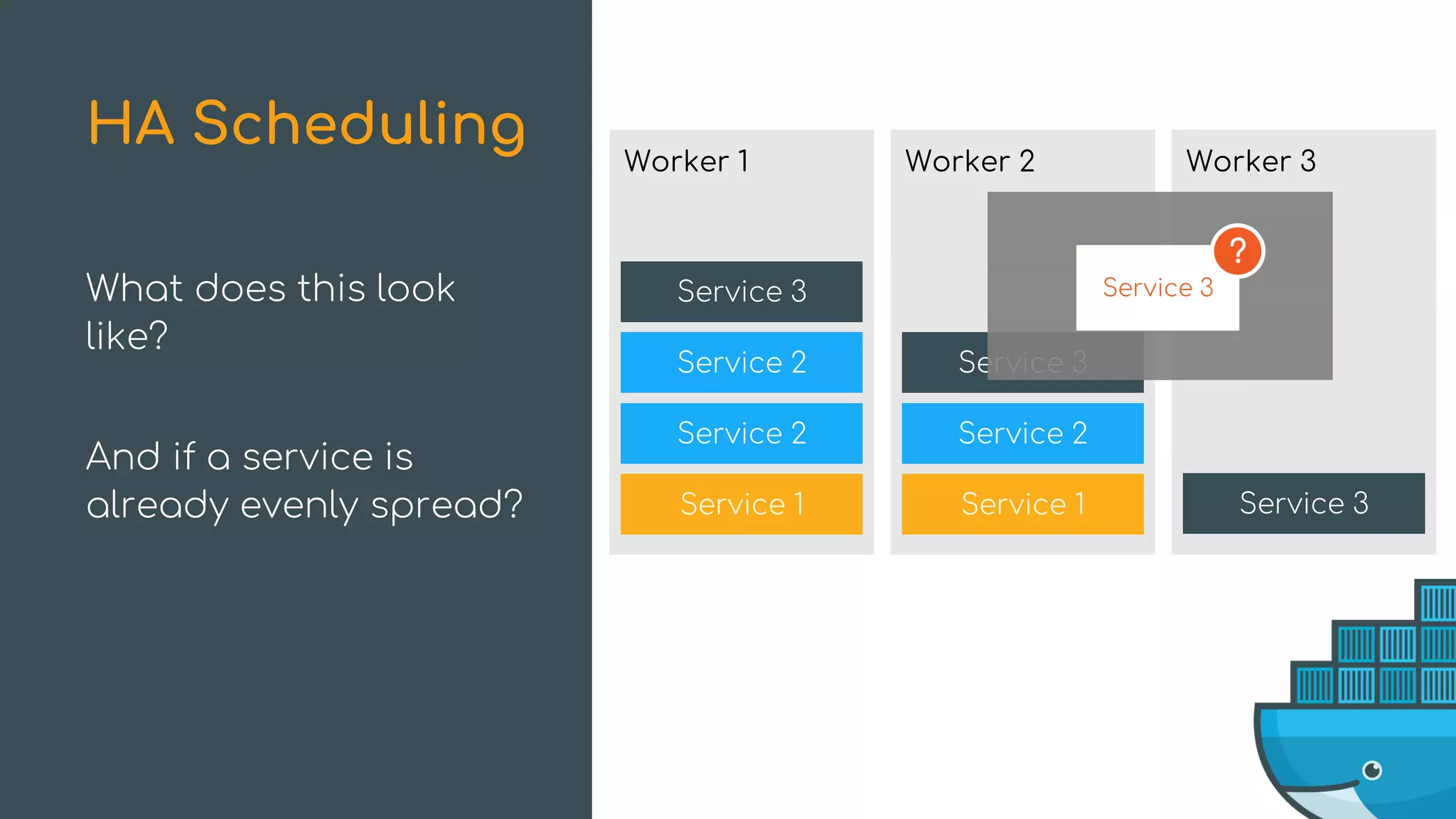
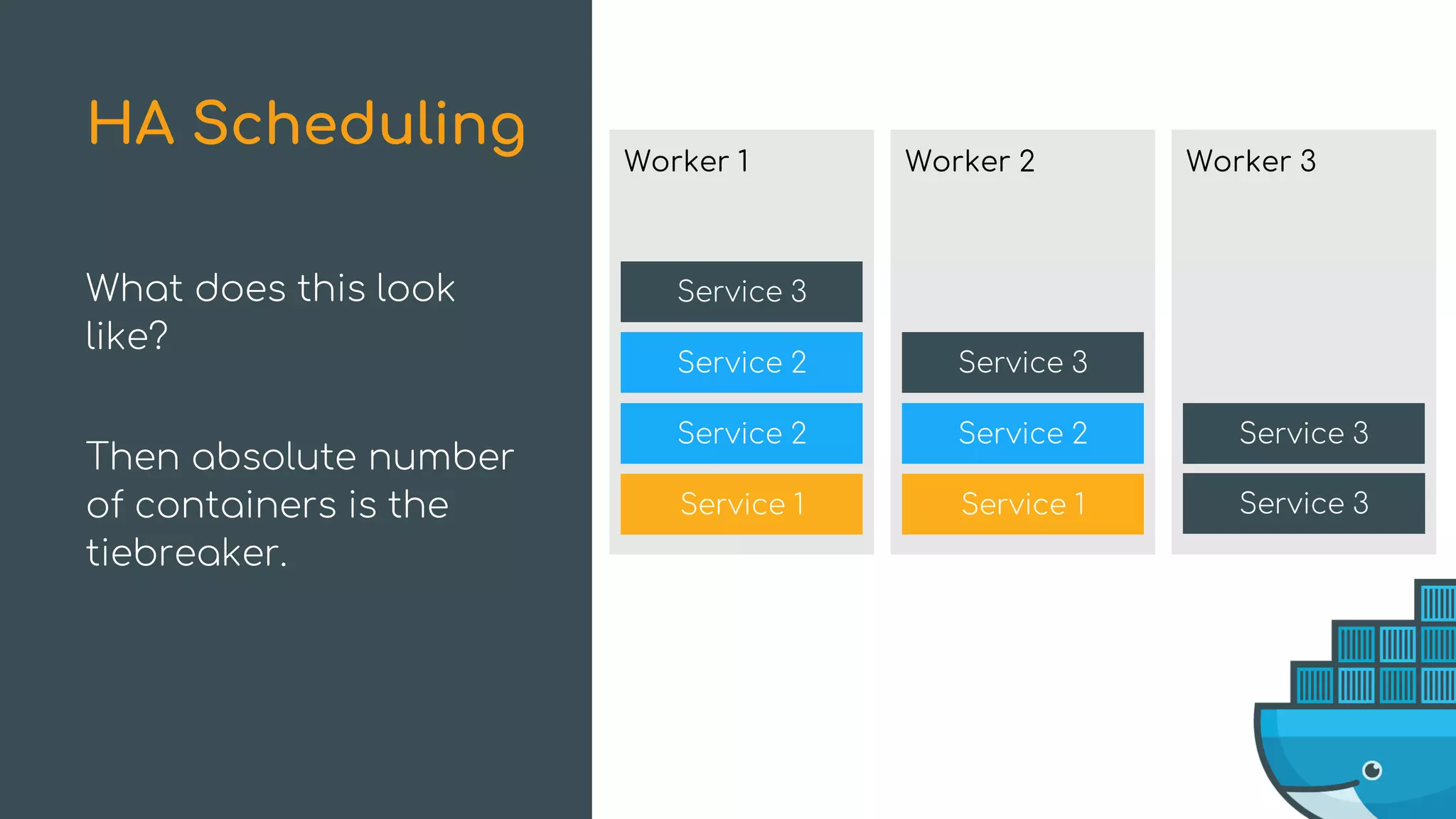
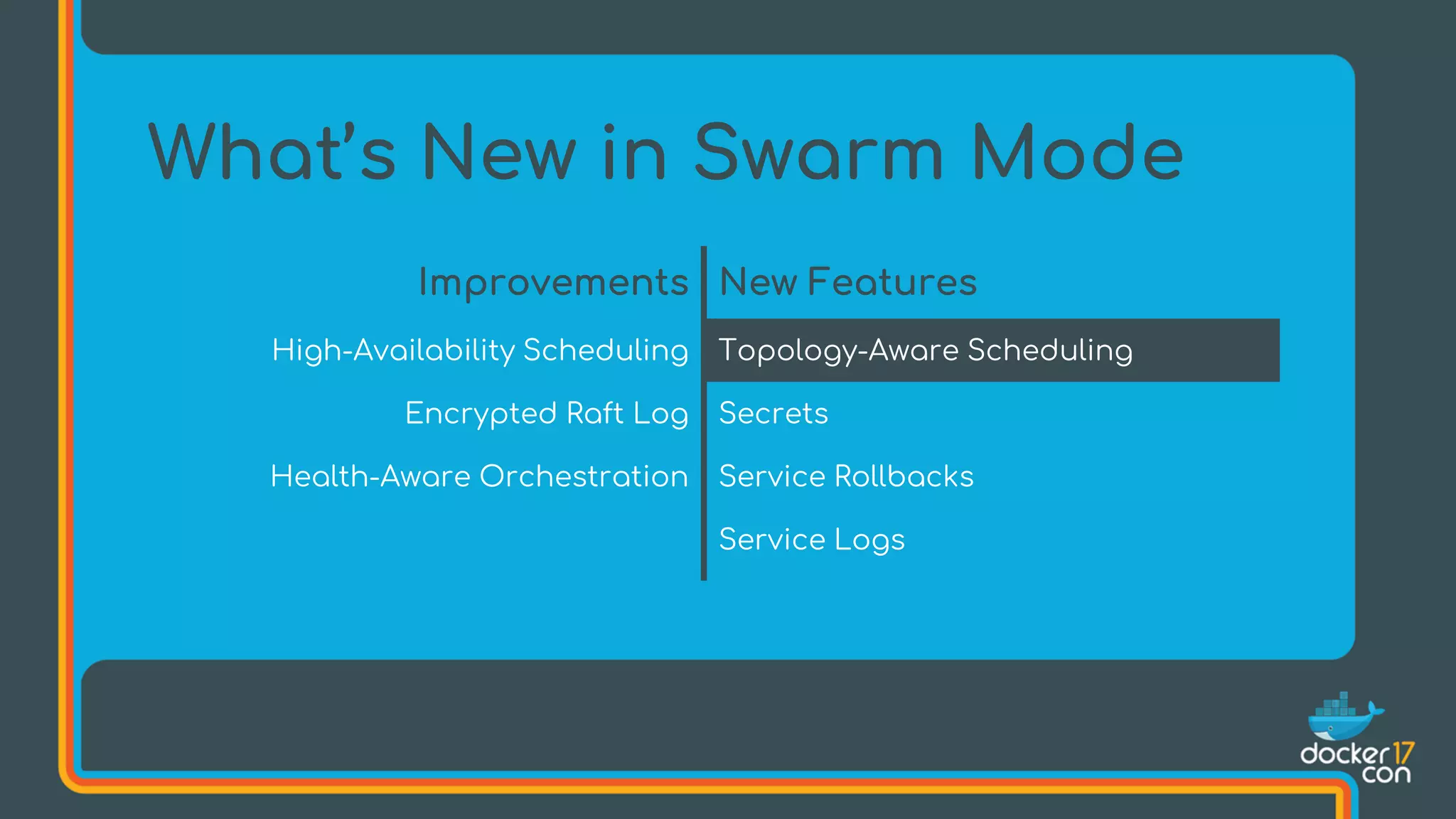
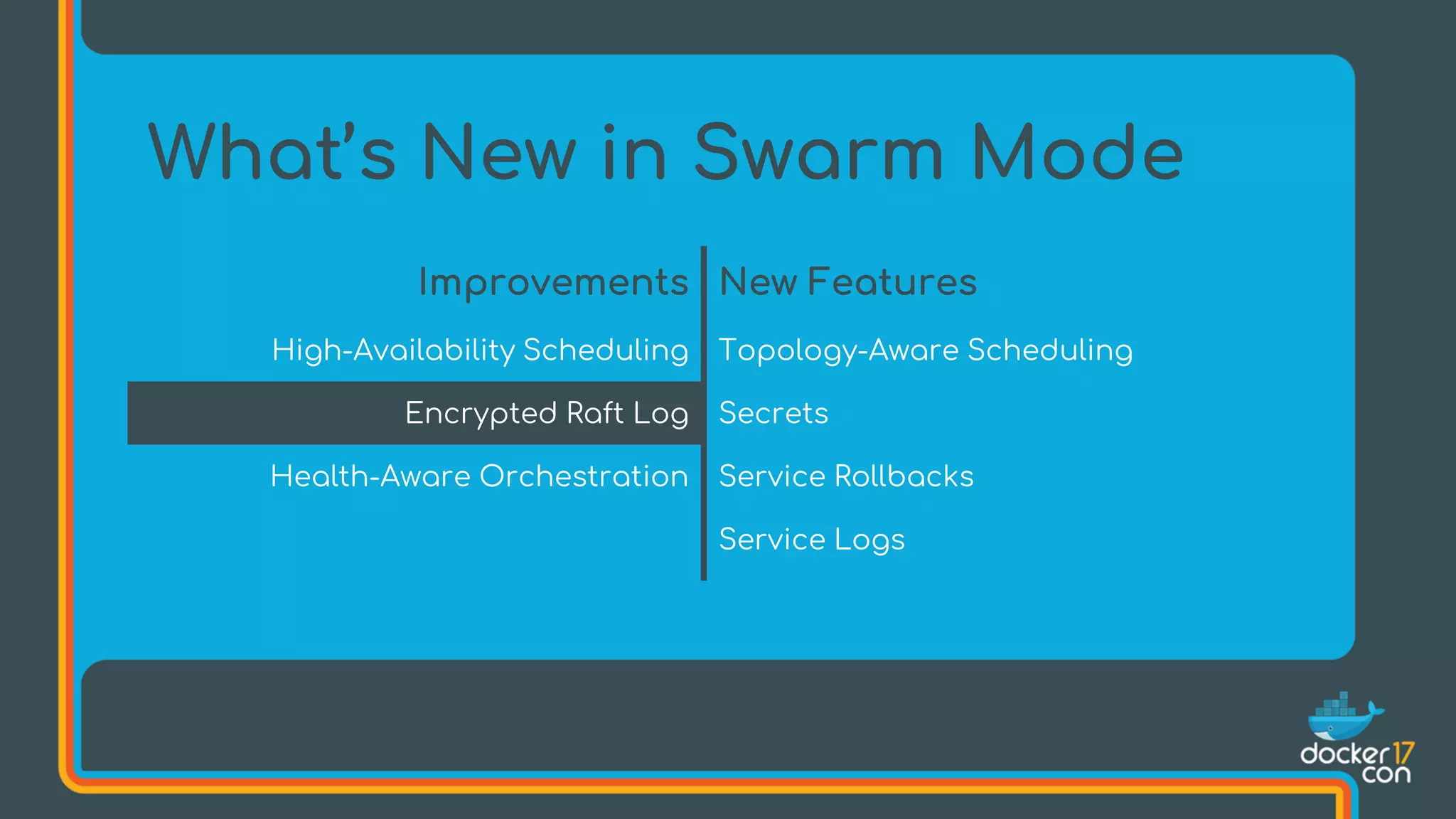
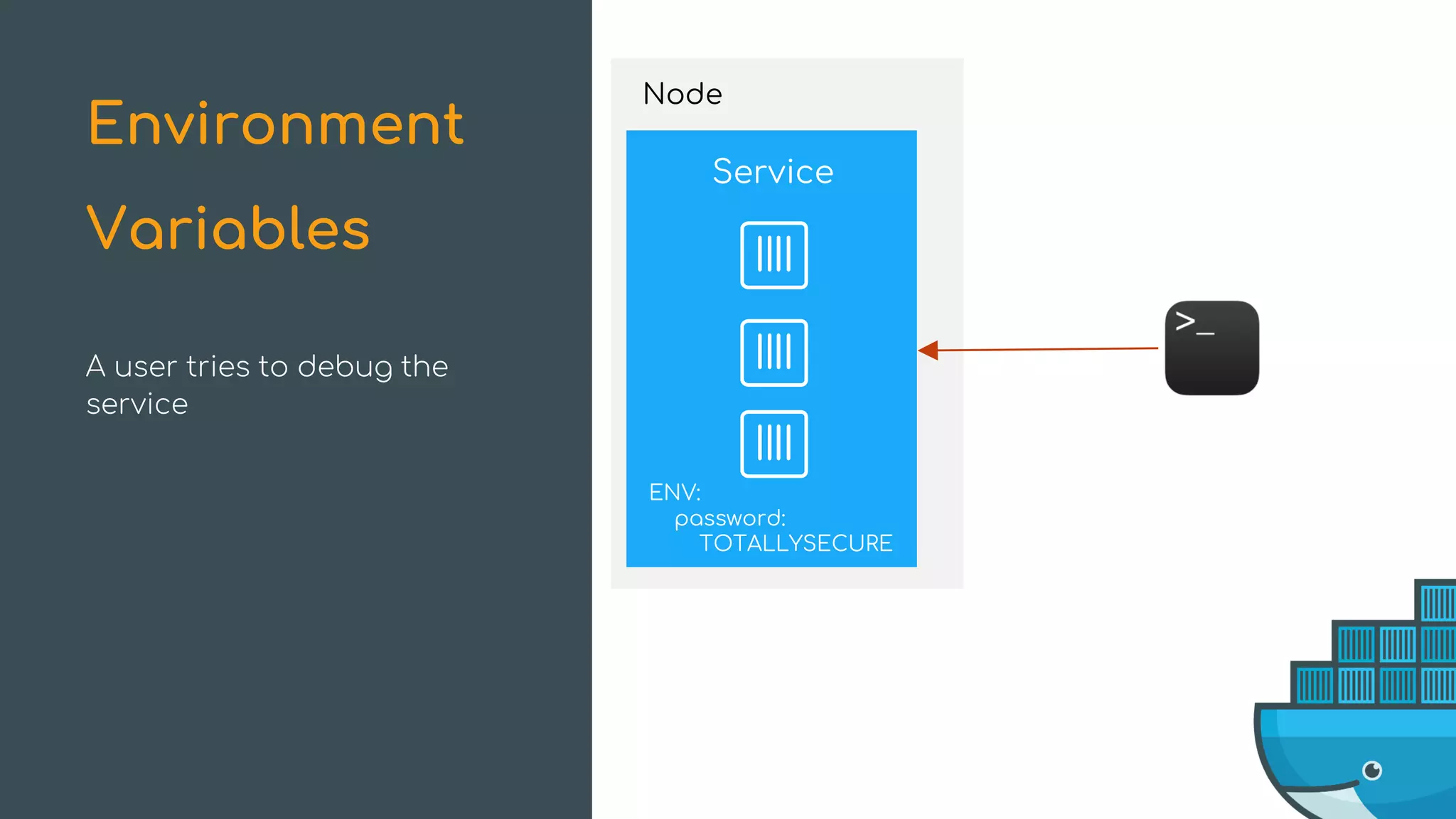
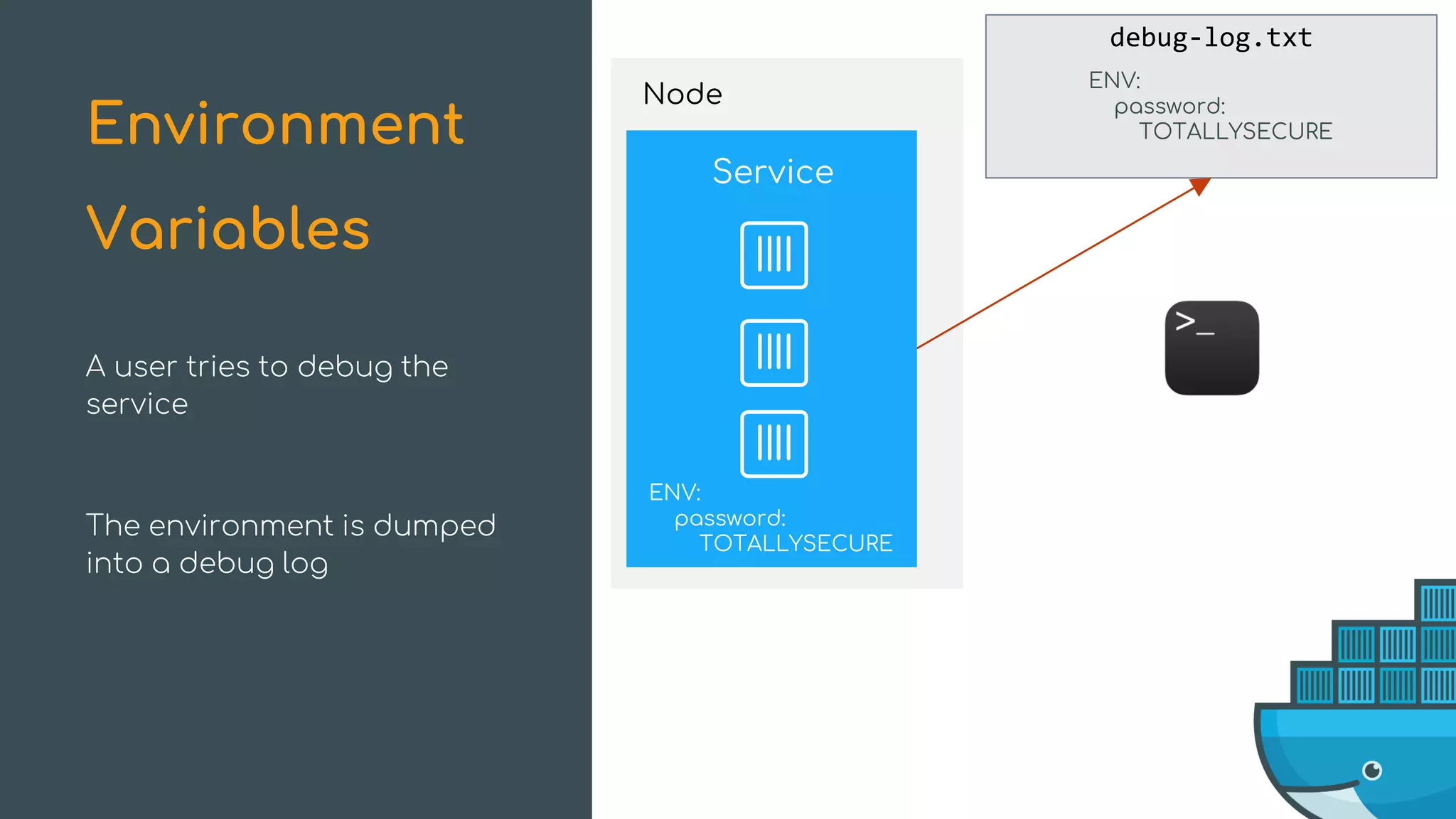
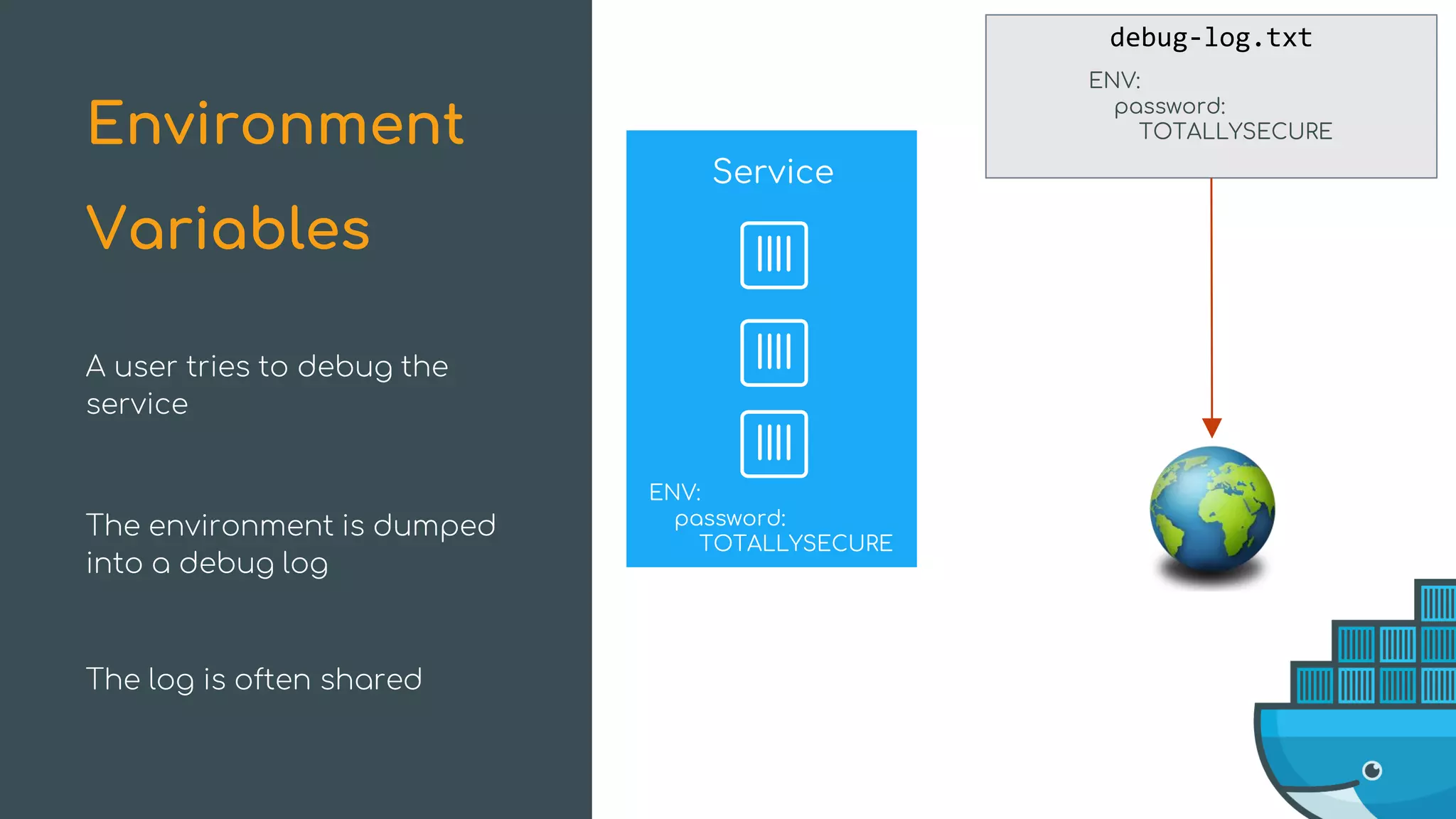
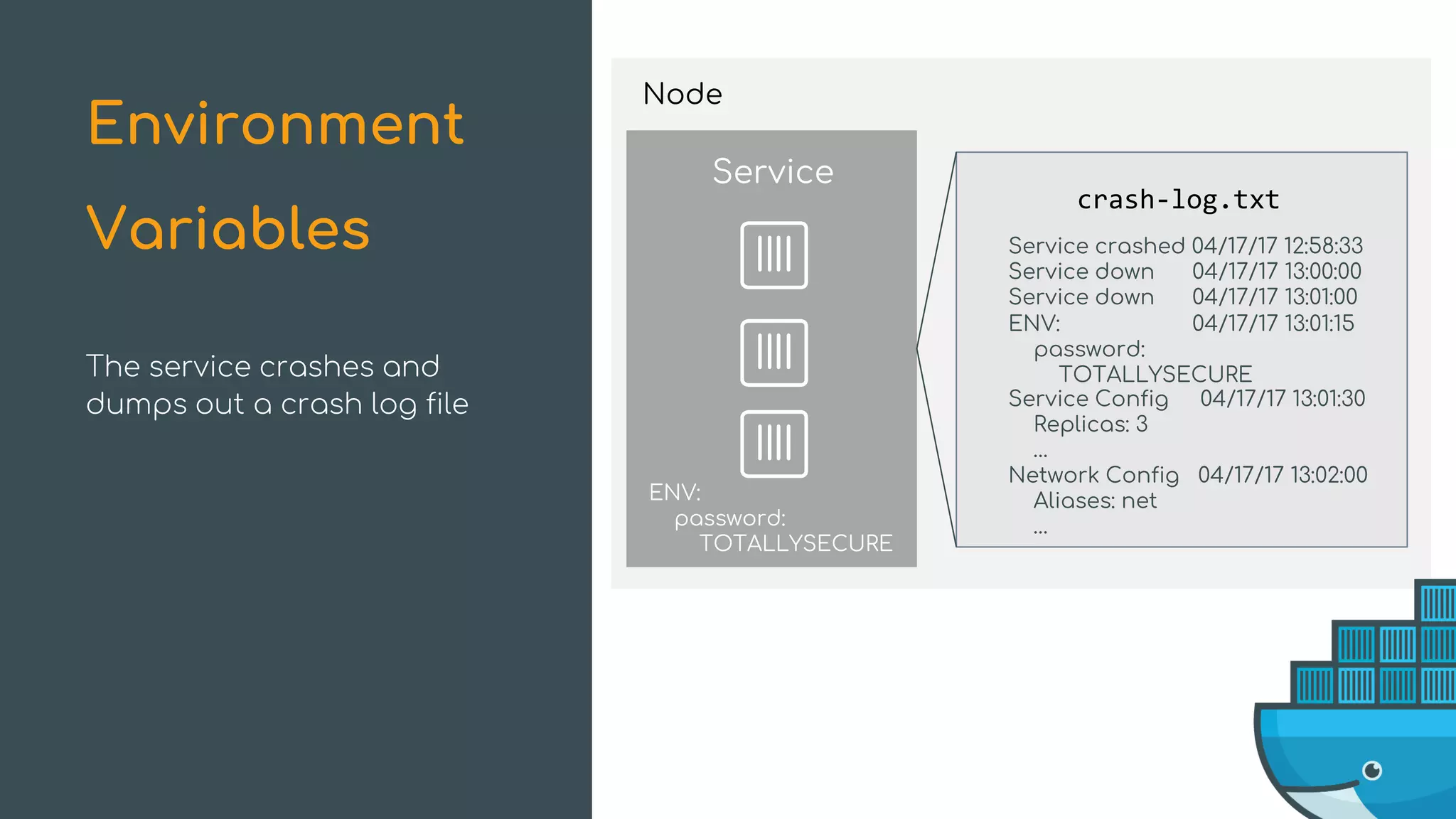
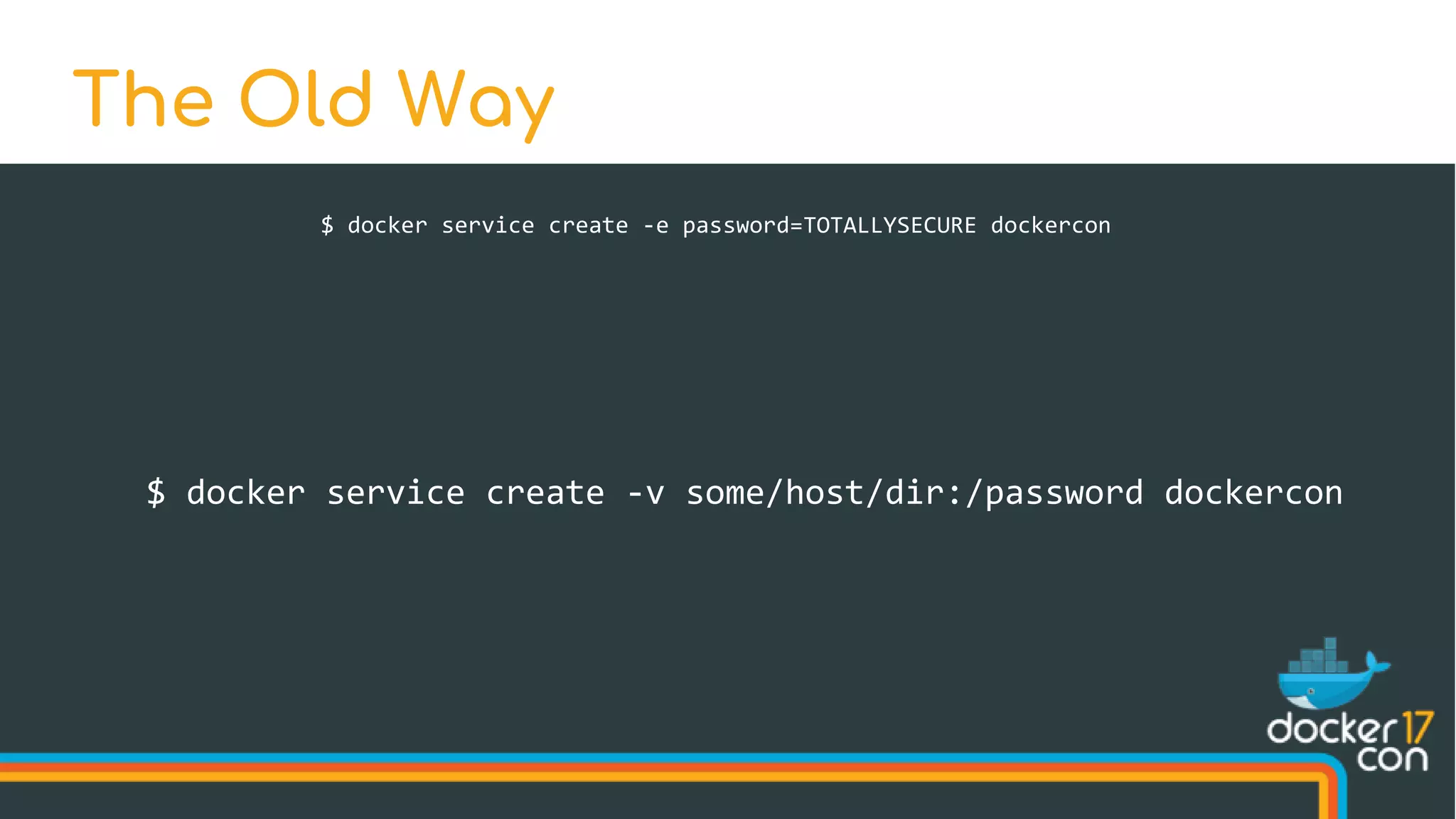
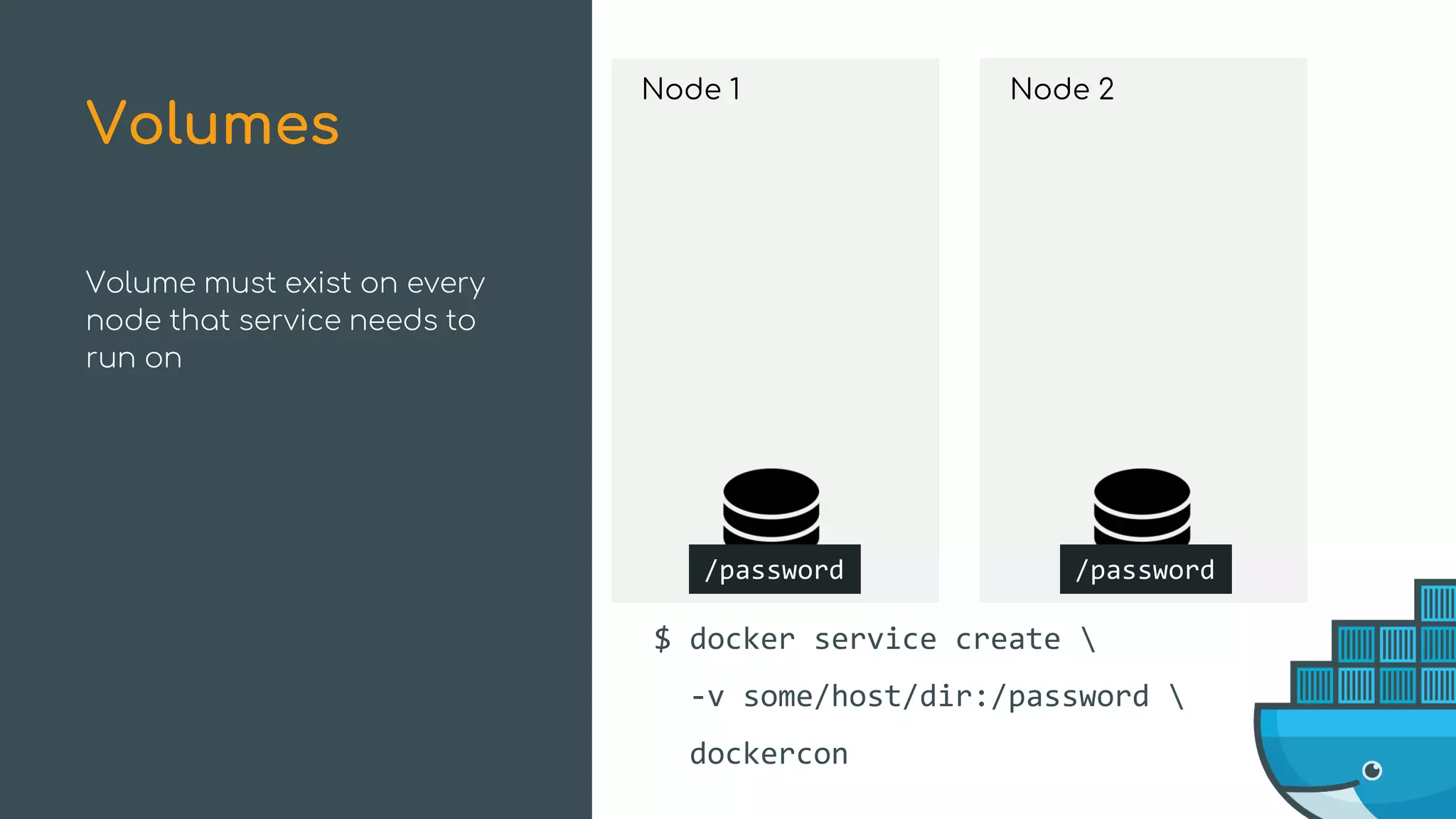
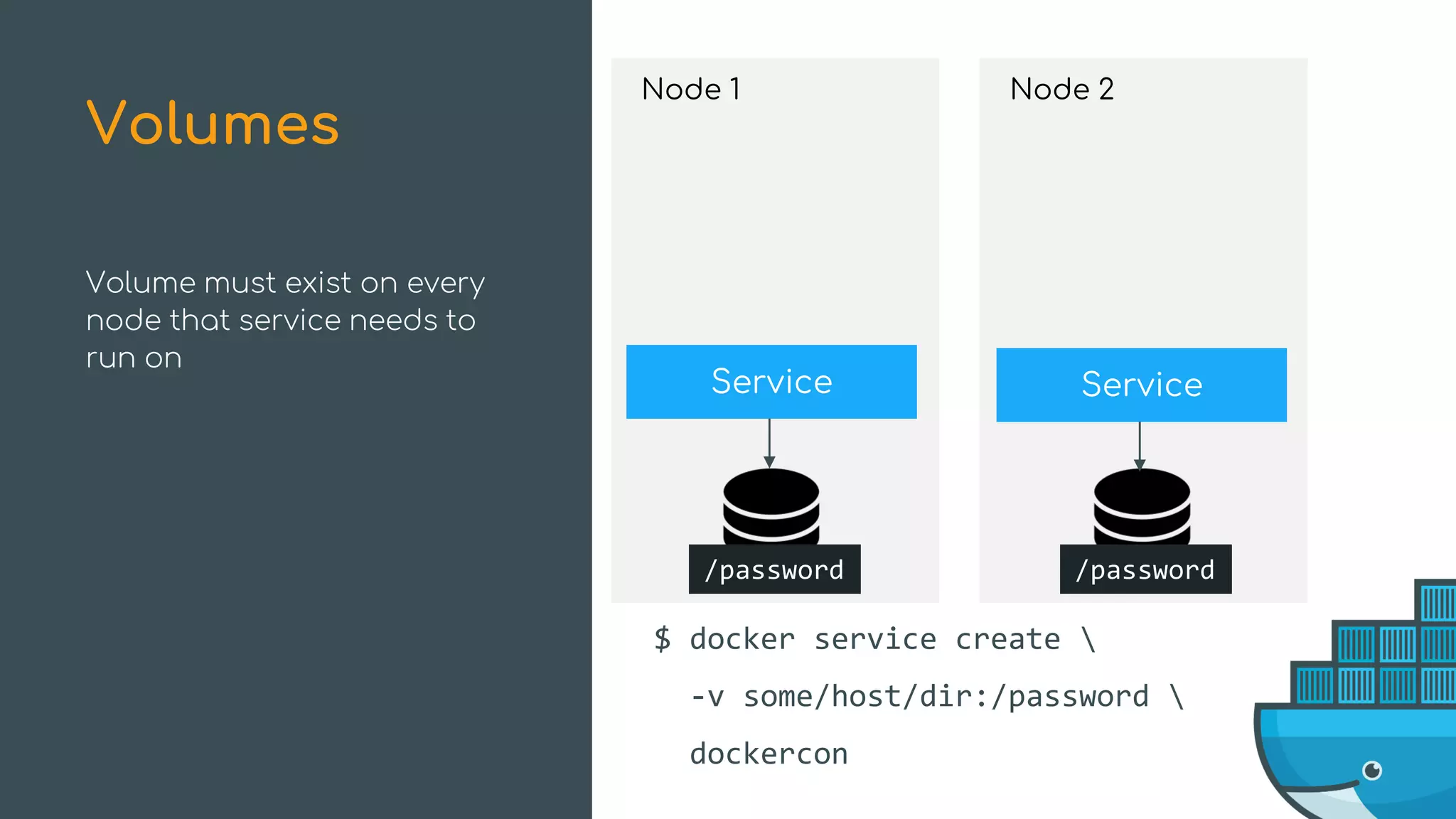
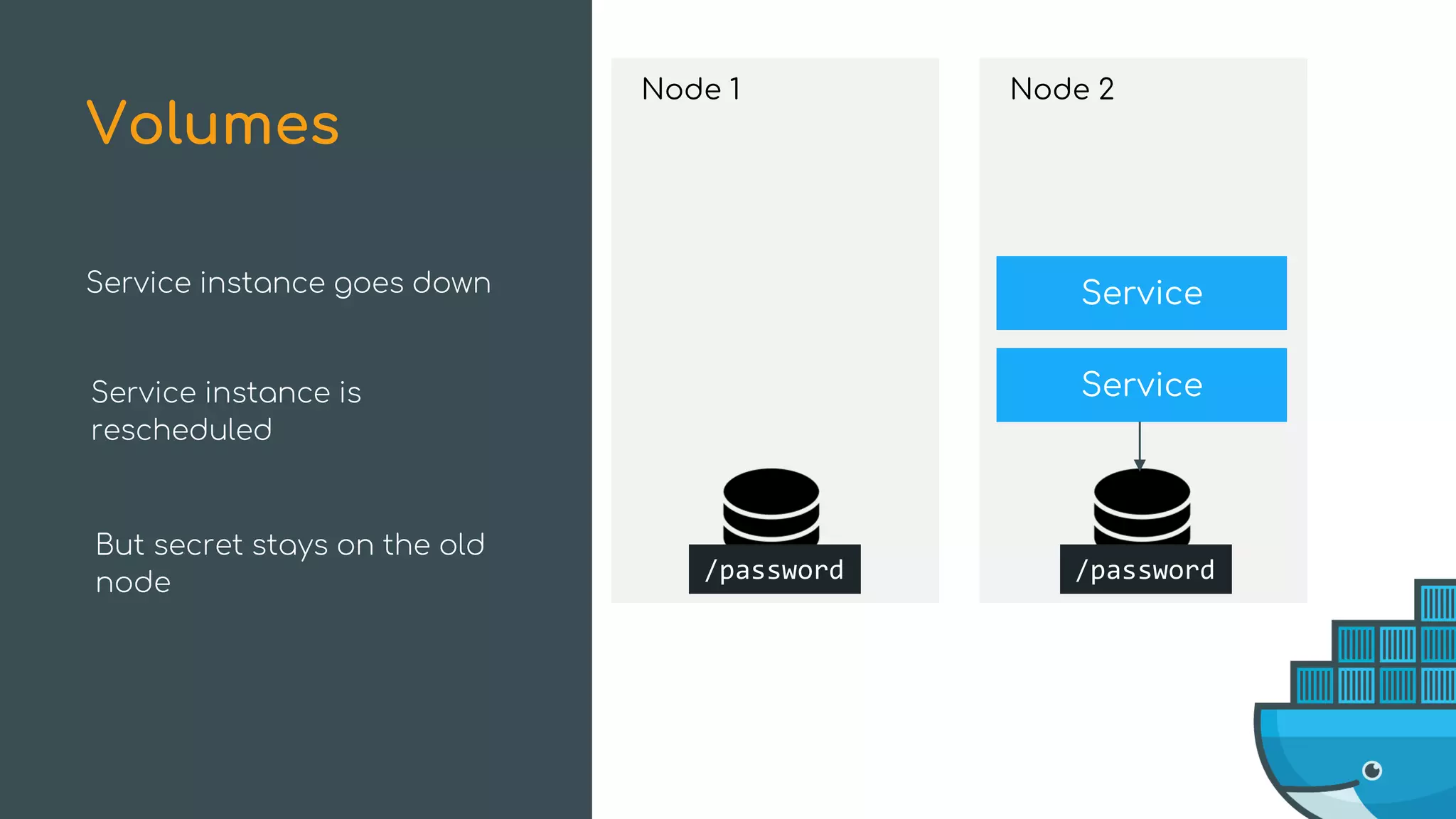
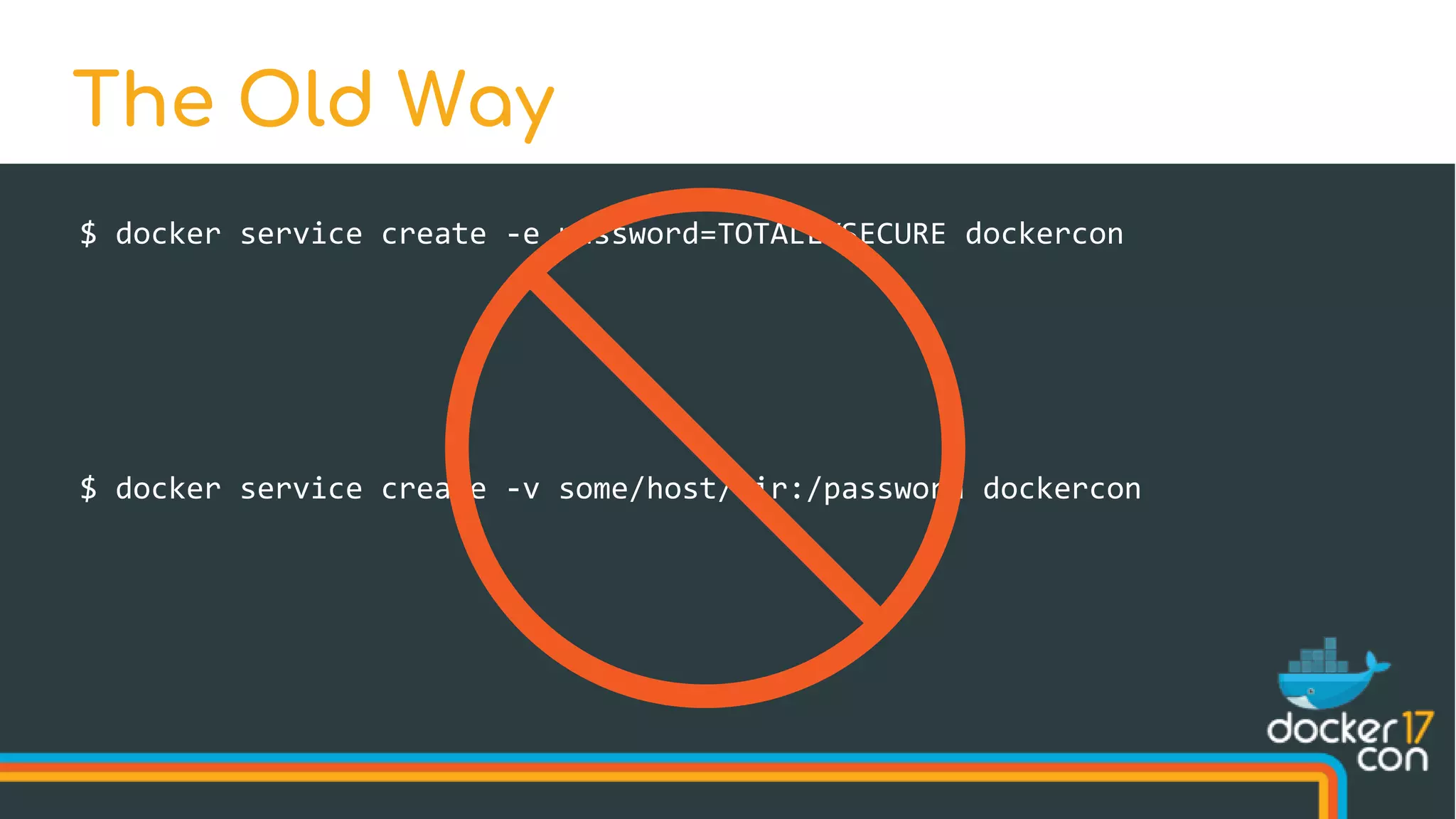
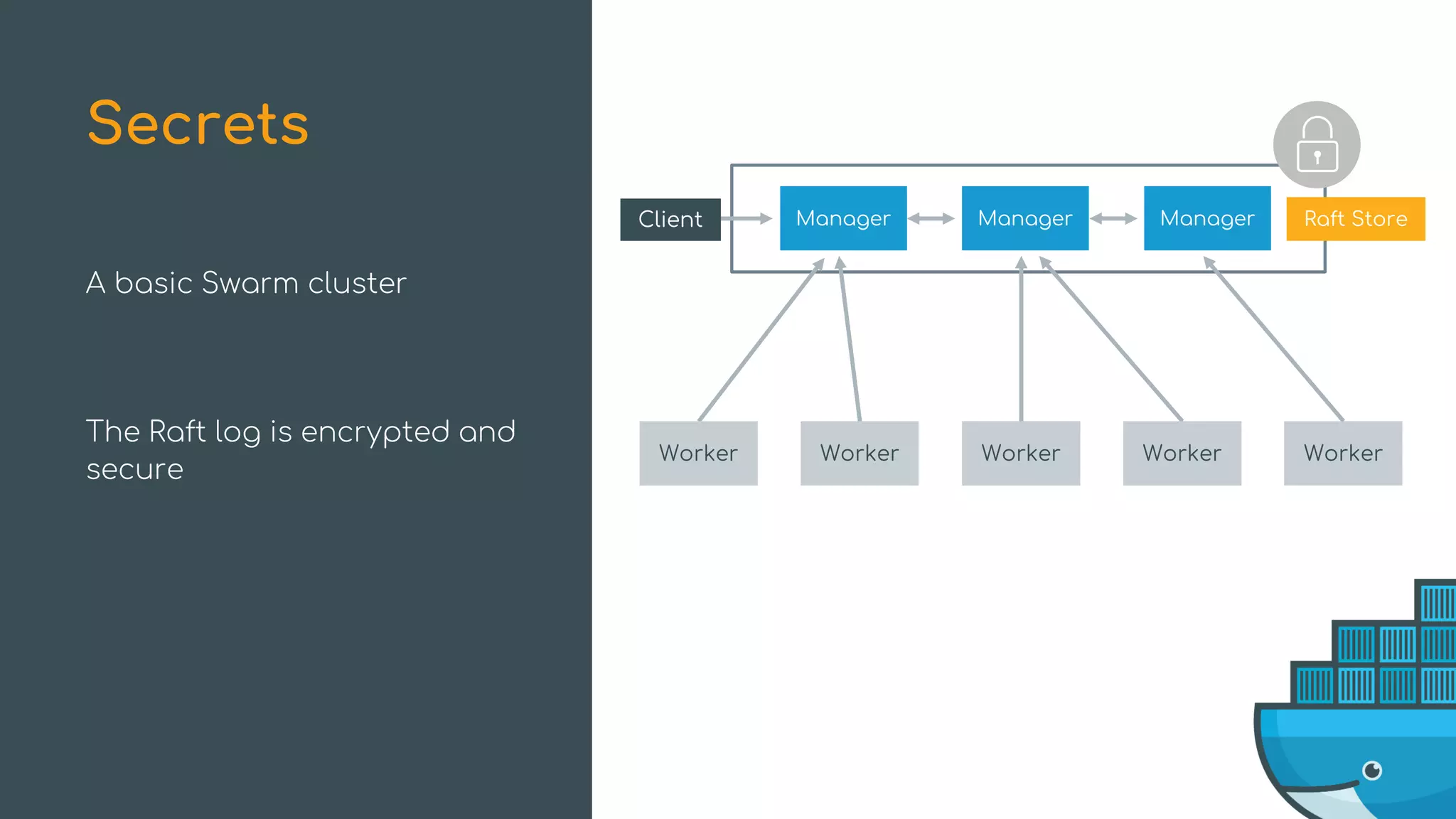
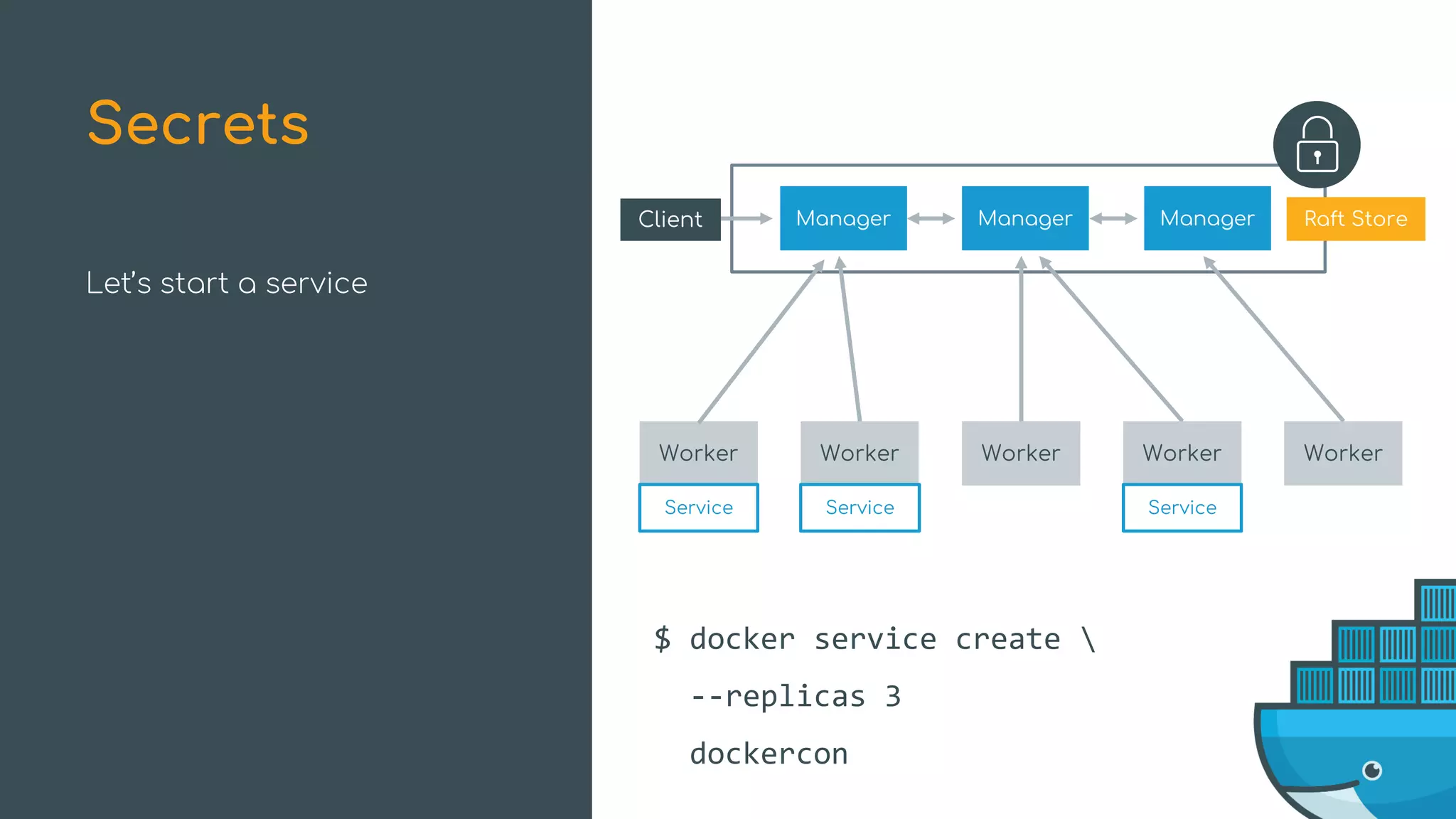
The document discusses Docker Swarm mode, focusing on its architecture, features, and improvements for cluster orchestration. Key topics include high-availability scheduling, topology-aware scheduling, encrypted Raft logs, and service rollbacks. Practical examples and best practices for using these features are also provided to enhance the deployment and management of containerized applications.








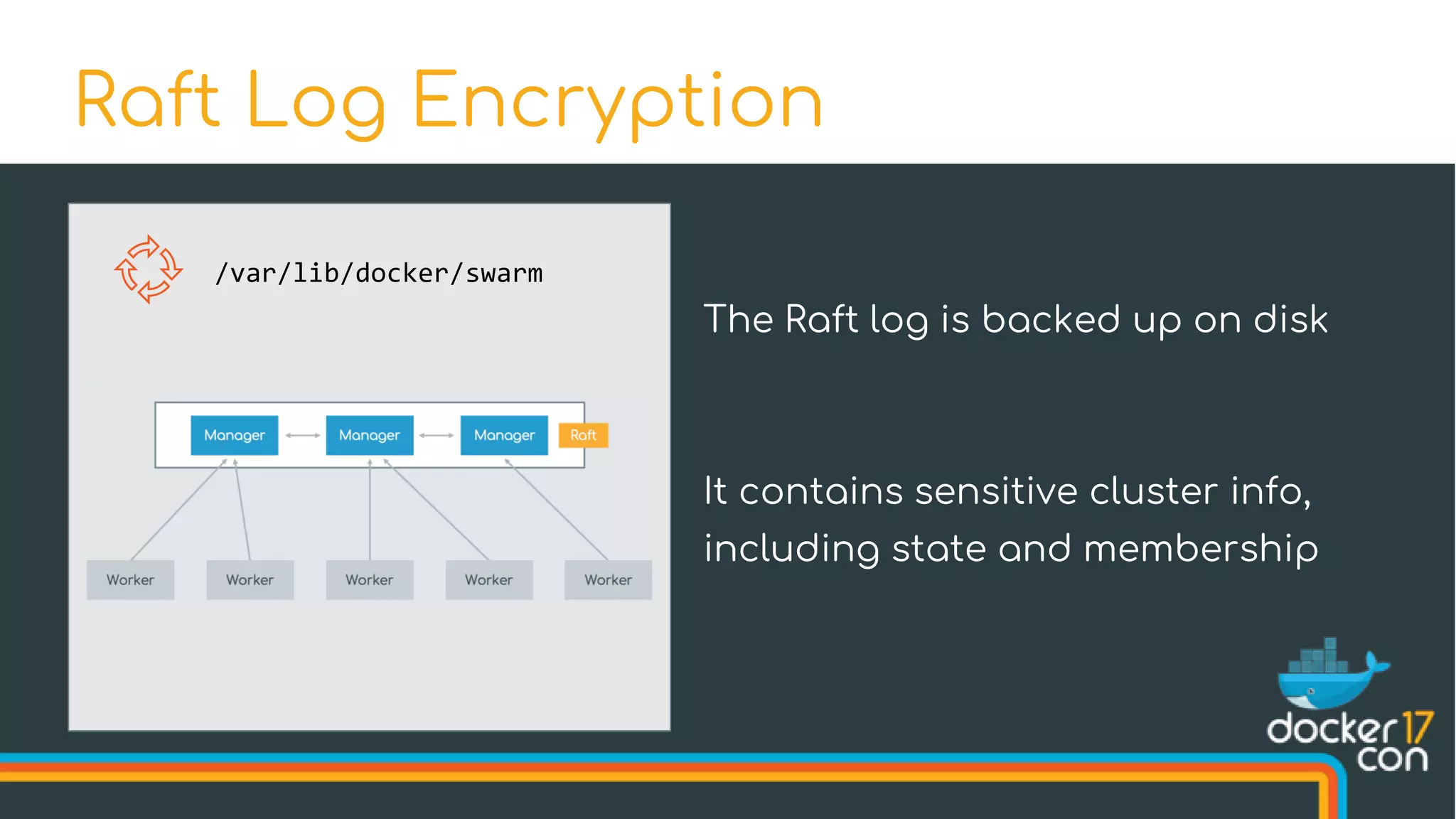
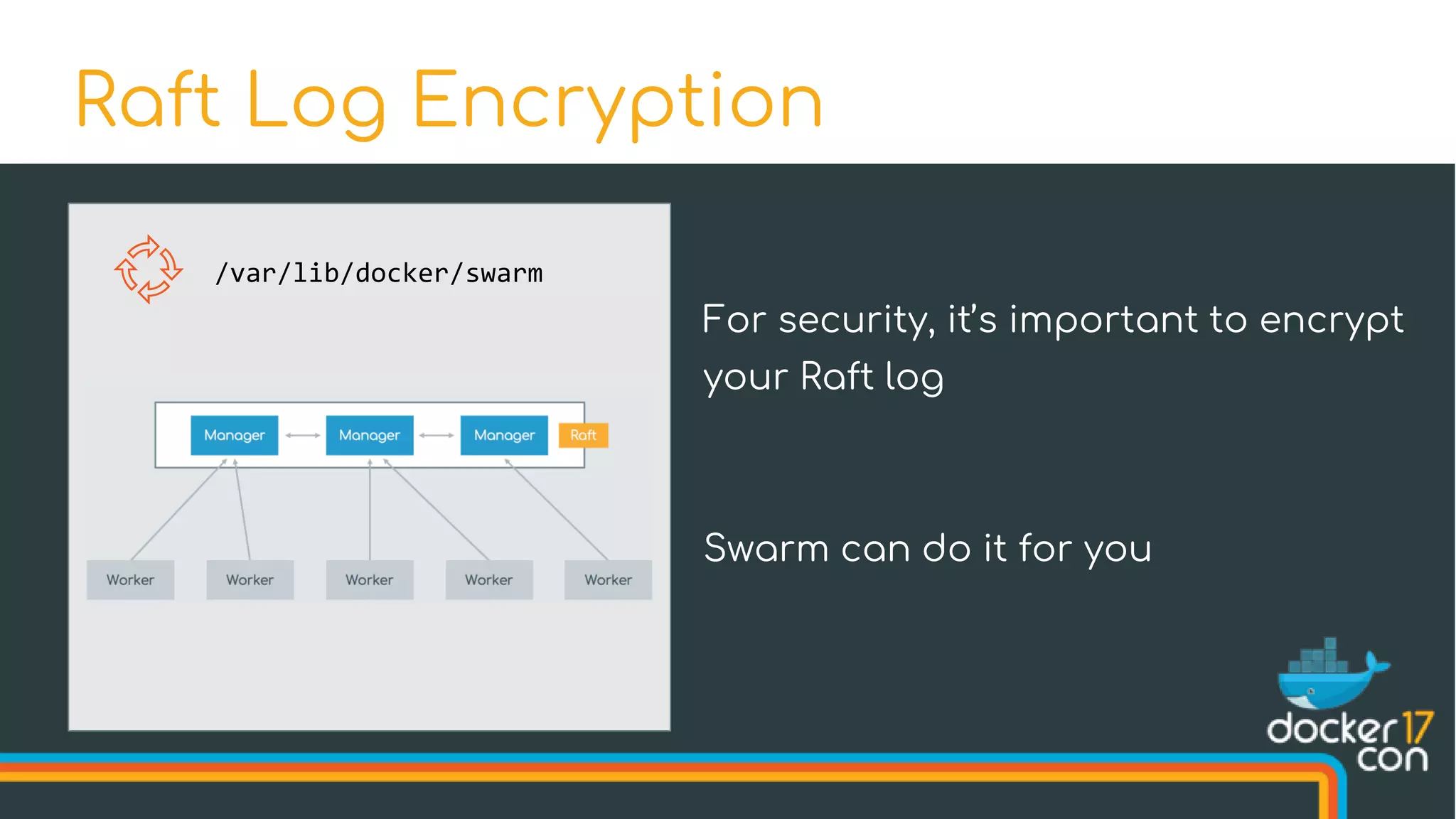
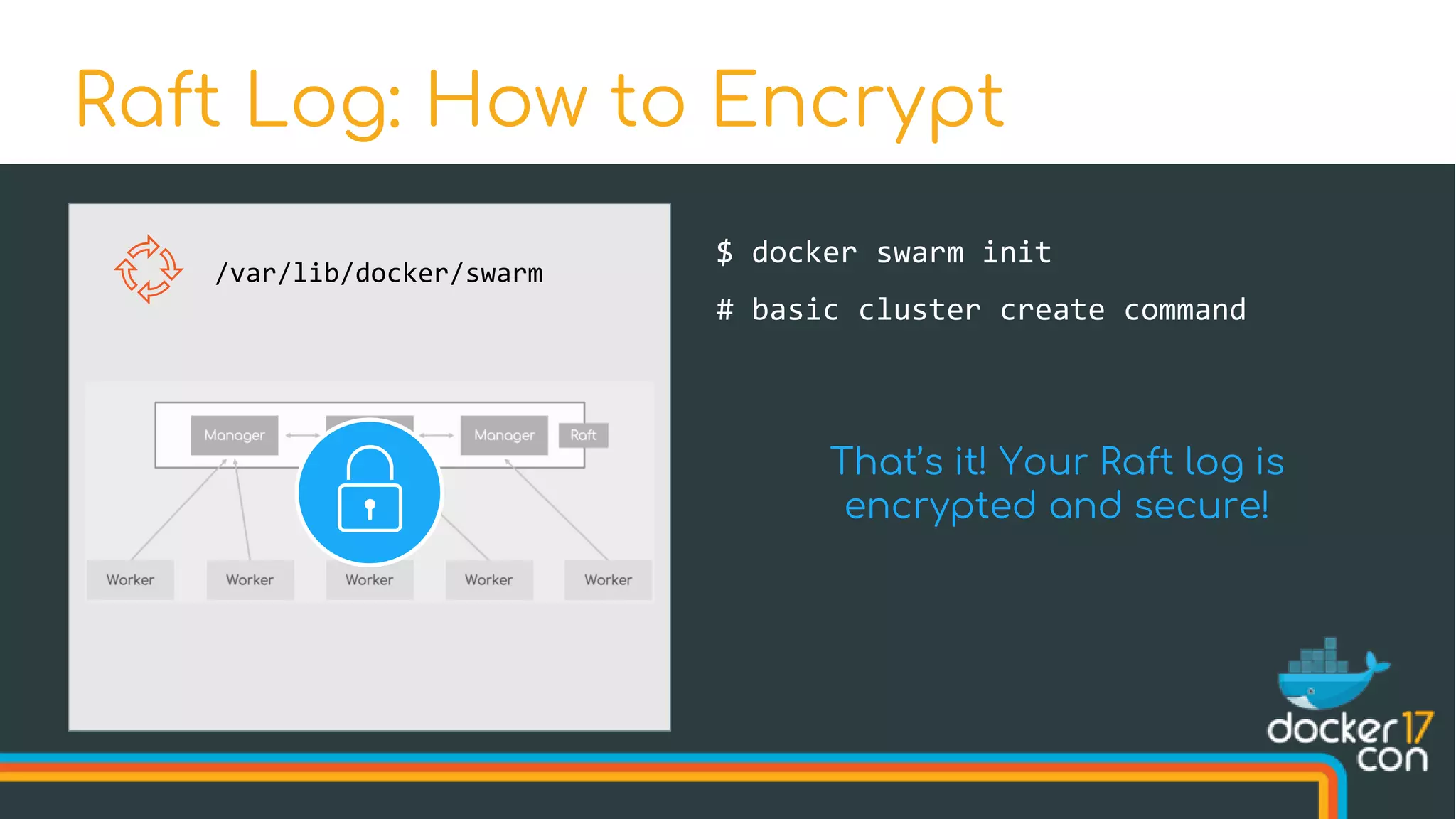

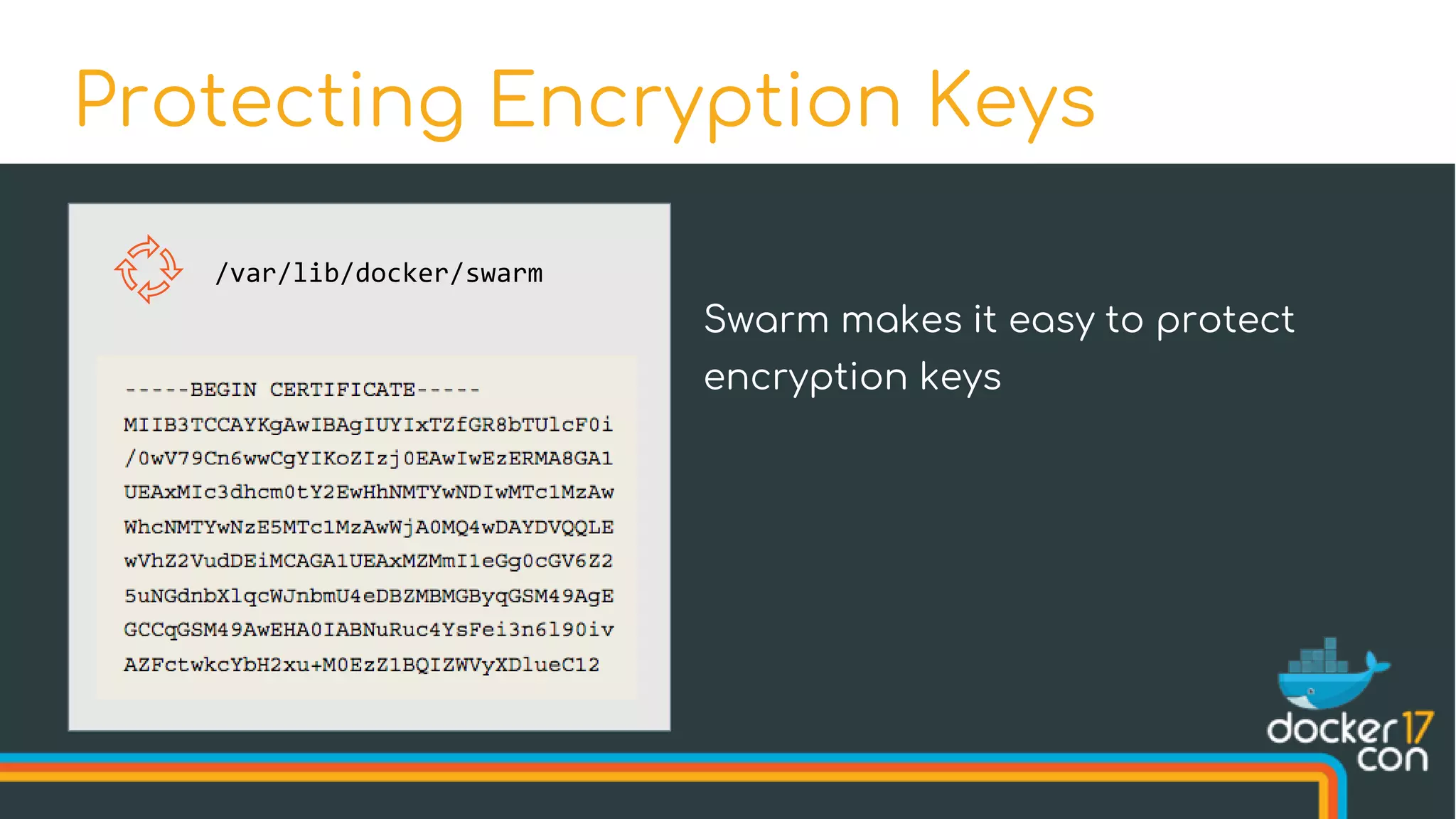
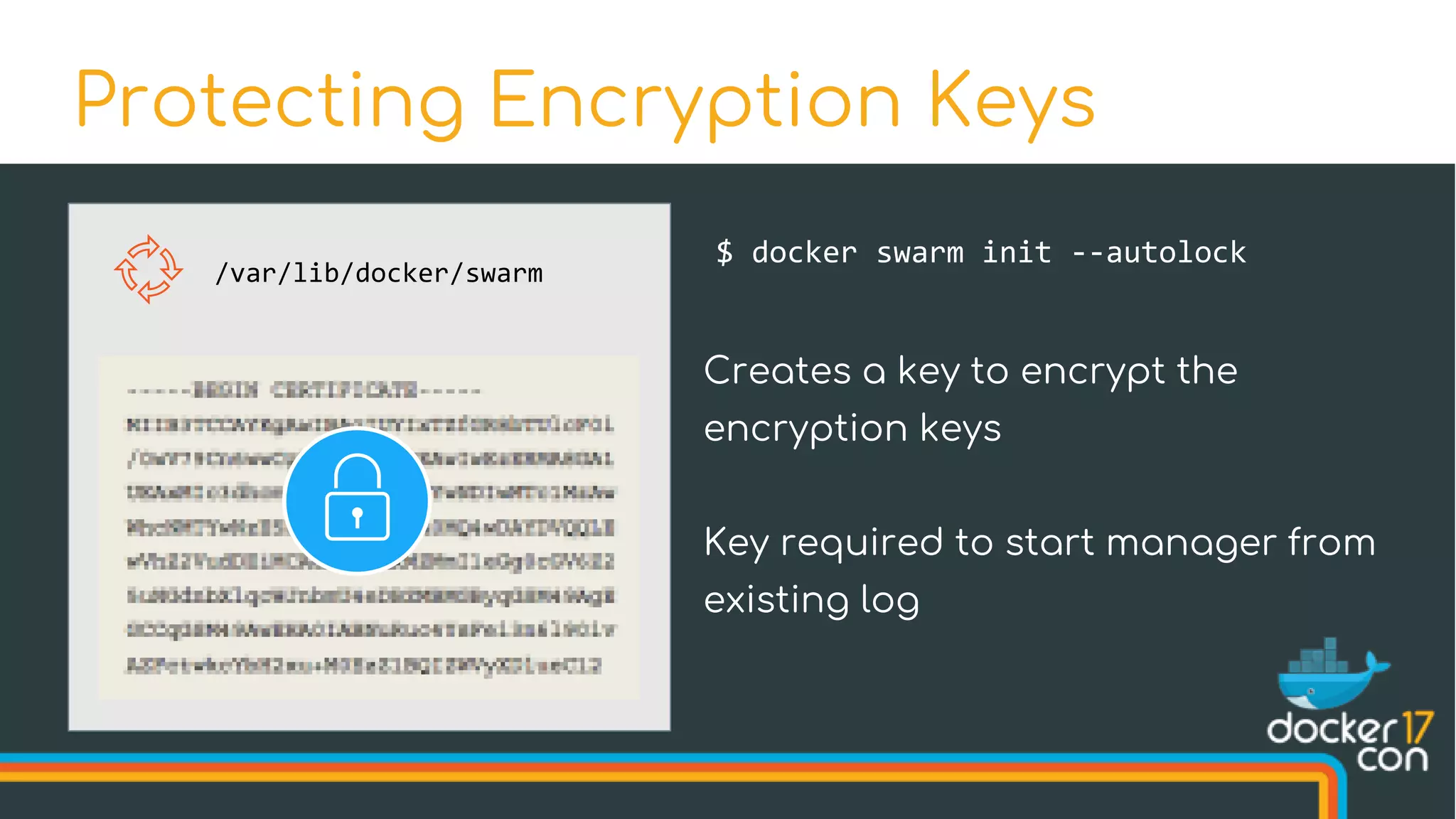
![$ docker swarm init --autolock
Swarm initialized: current node (u3hujejsk5plrmfn3uq10kmu5) is now
a manager.
[...]
To unlock a swarm manager after it restarts, run the `docker swarm unlock`
command and provide the following key:
SWMKEY-1-yDrZW4AyTzPiqpJvYGL5sKqkX5XFvQJBm1ztGwFDgiI
Please remember to store this key in a password manager, since without
it you will not be able to restart the manager.
Protecting Encryption Keys](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-43-2048.jpg)







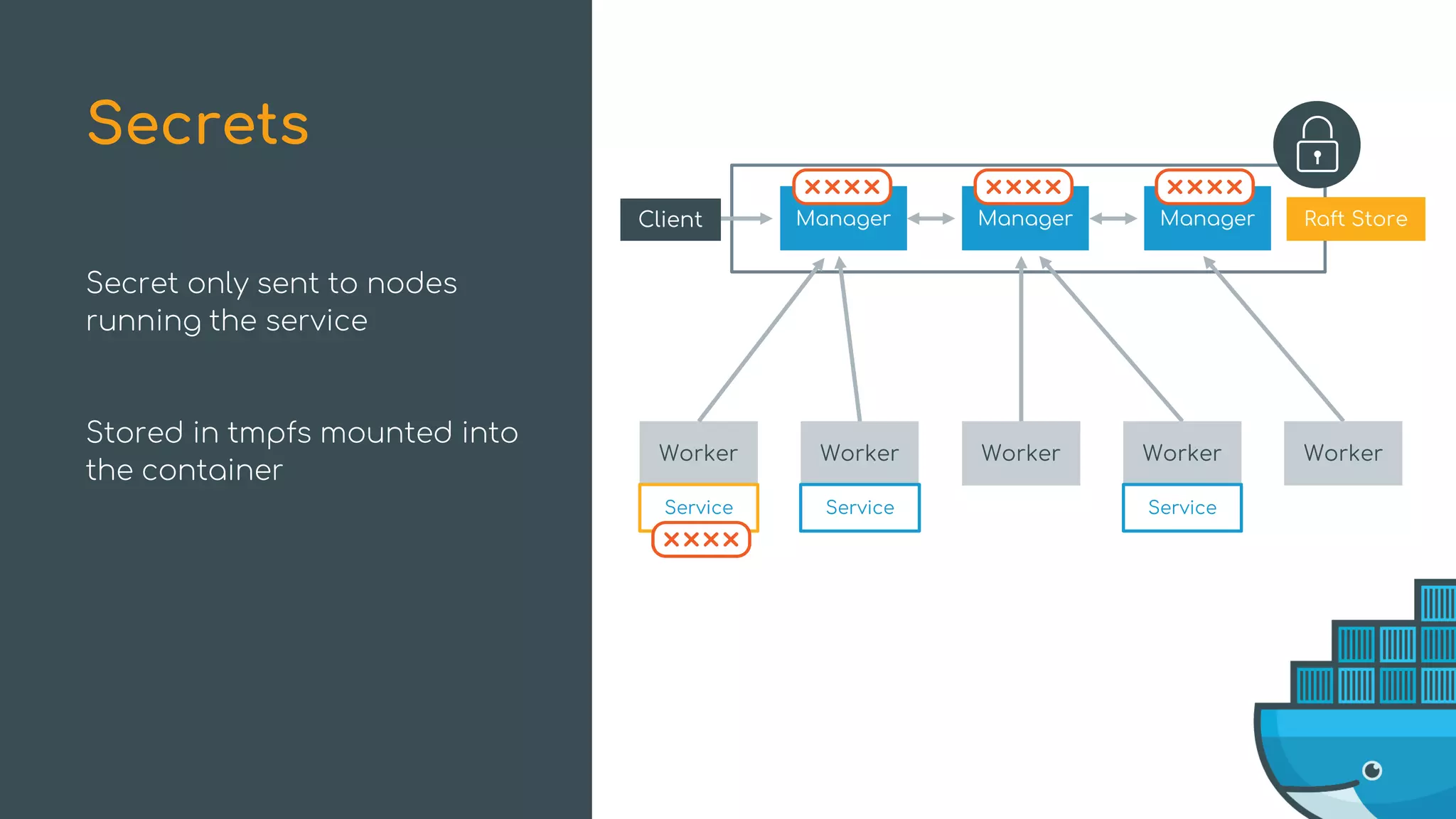
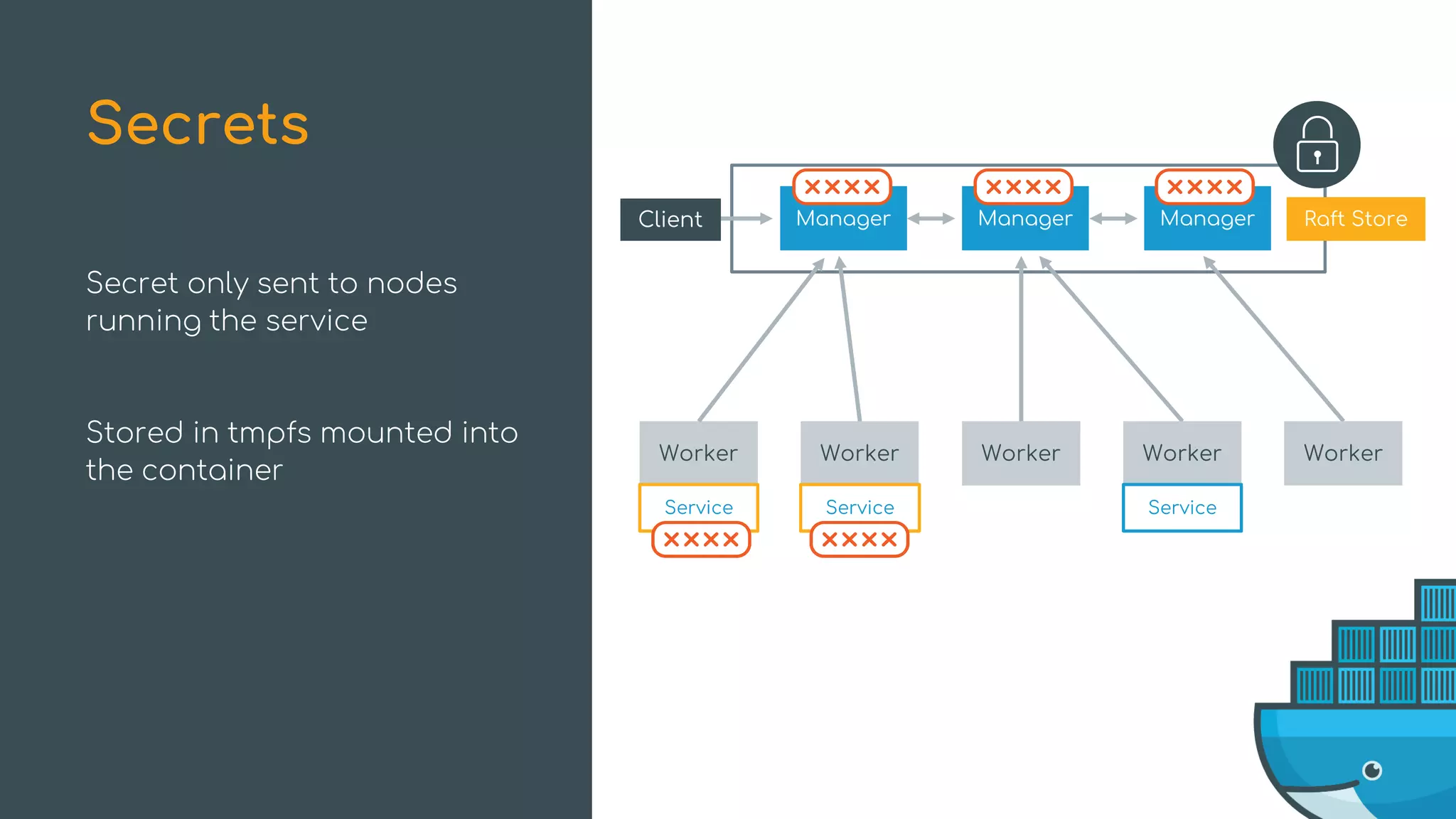
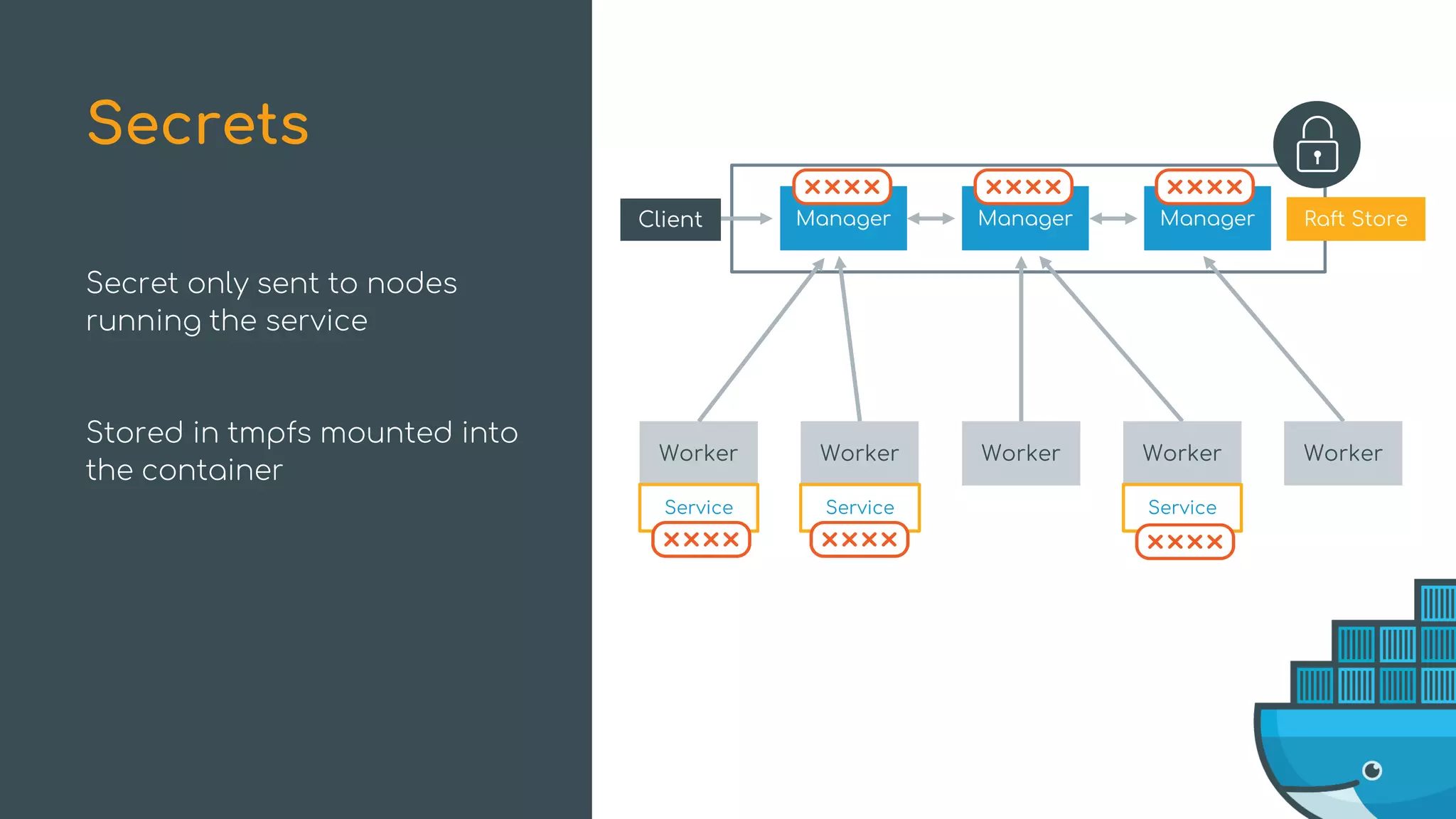
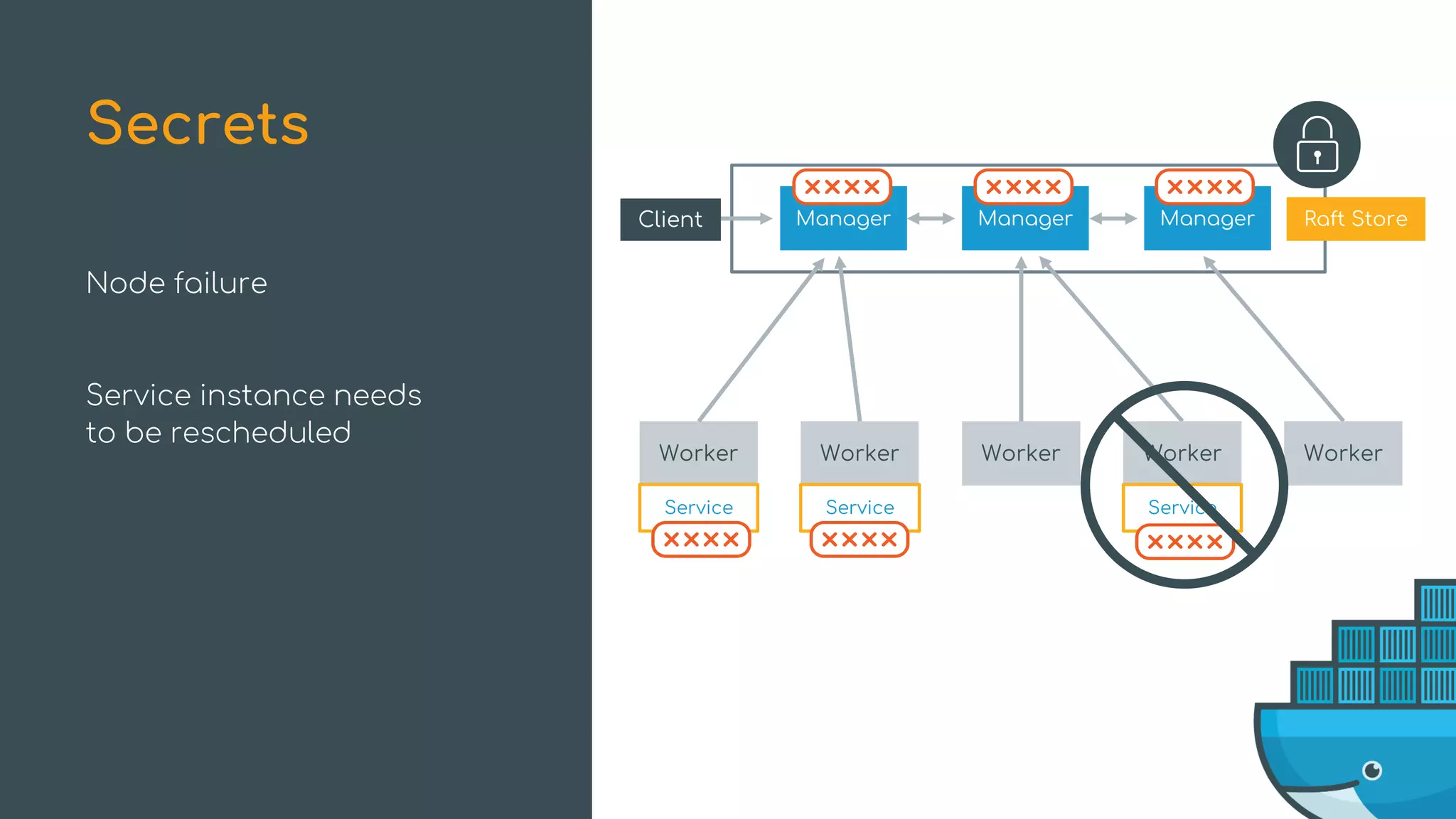

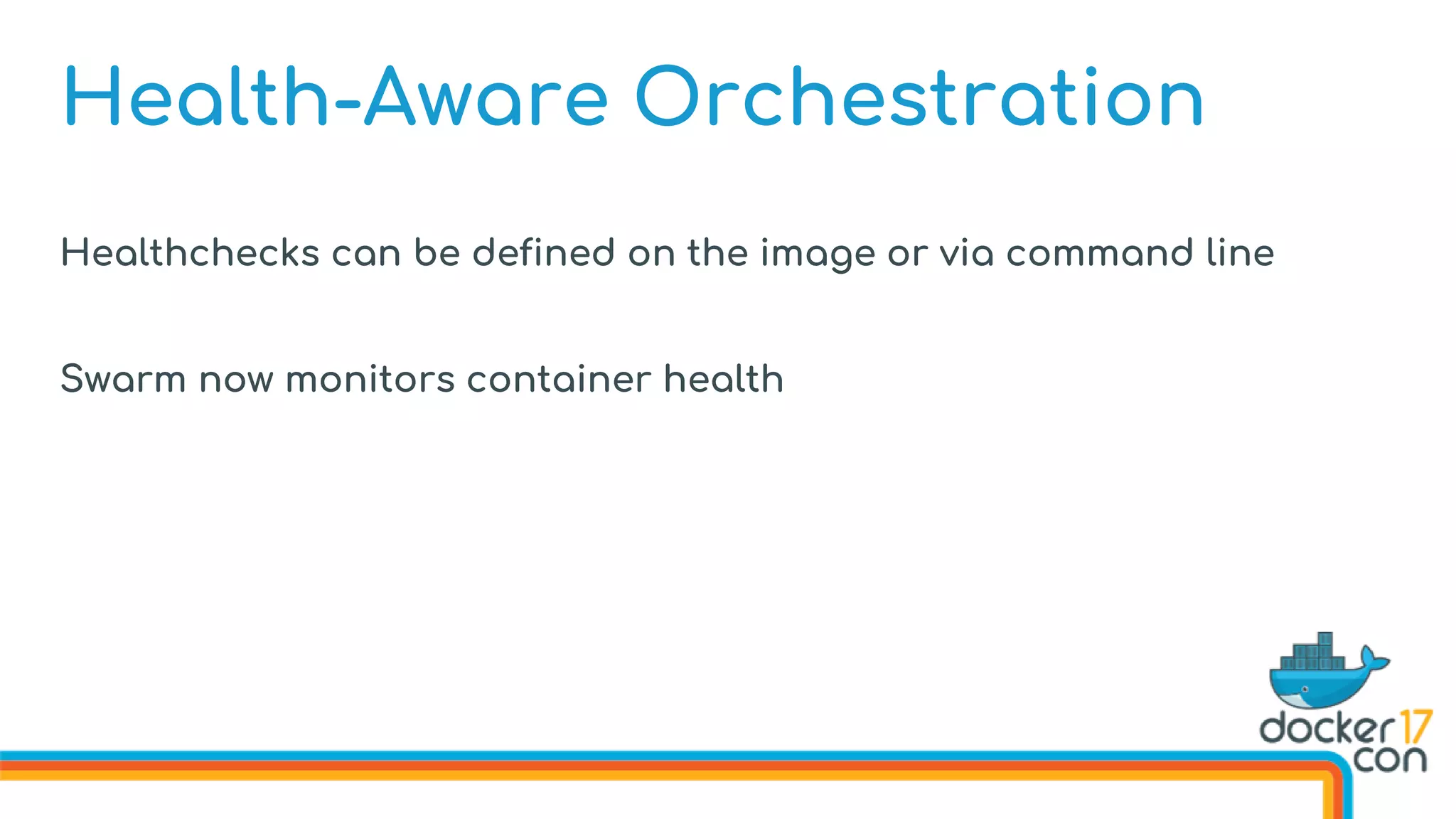
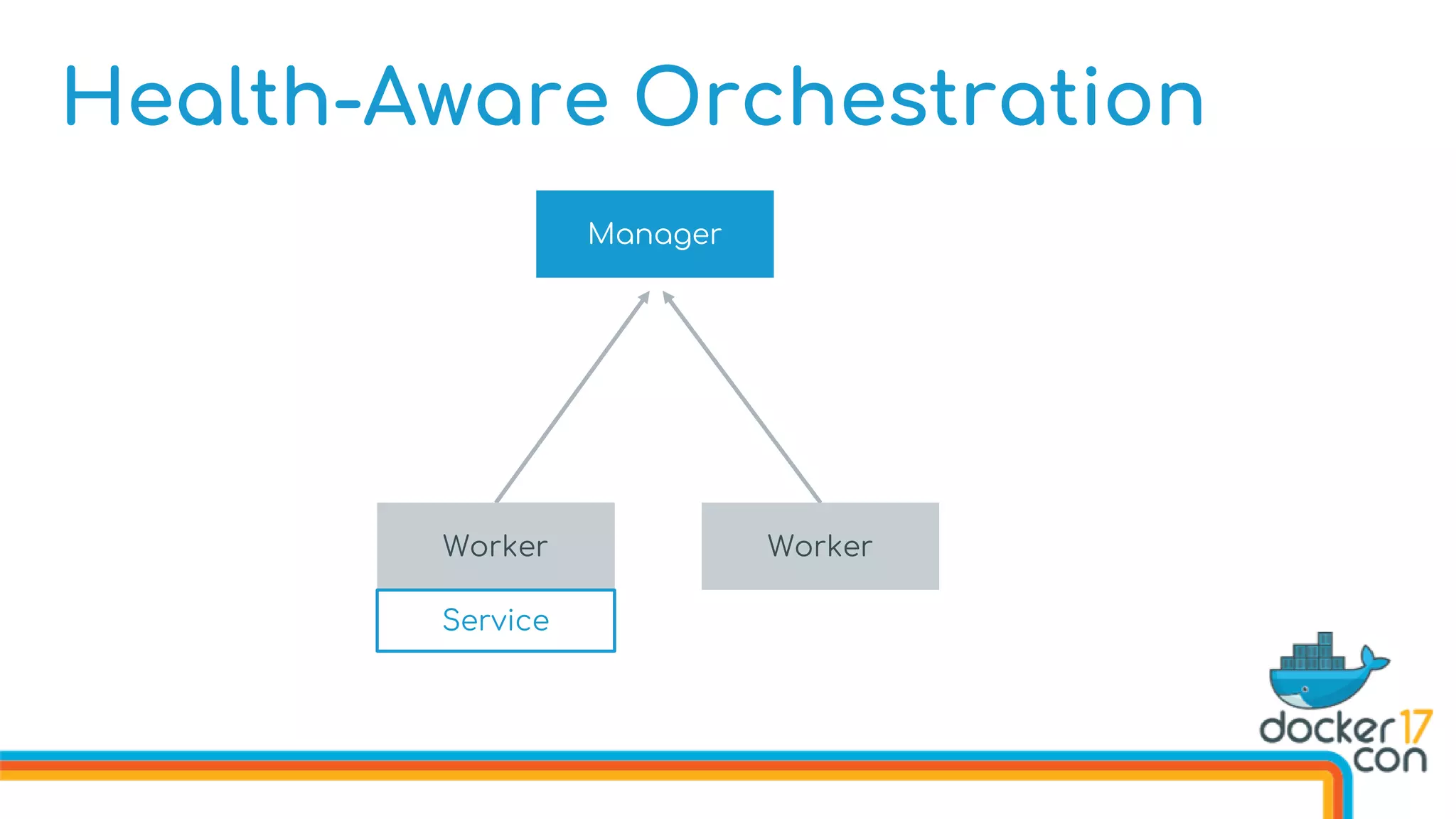
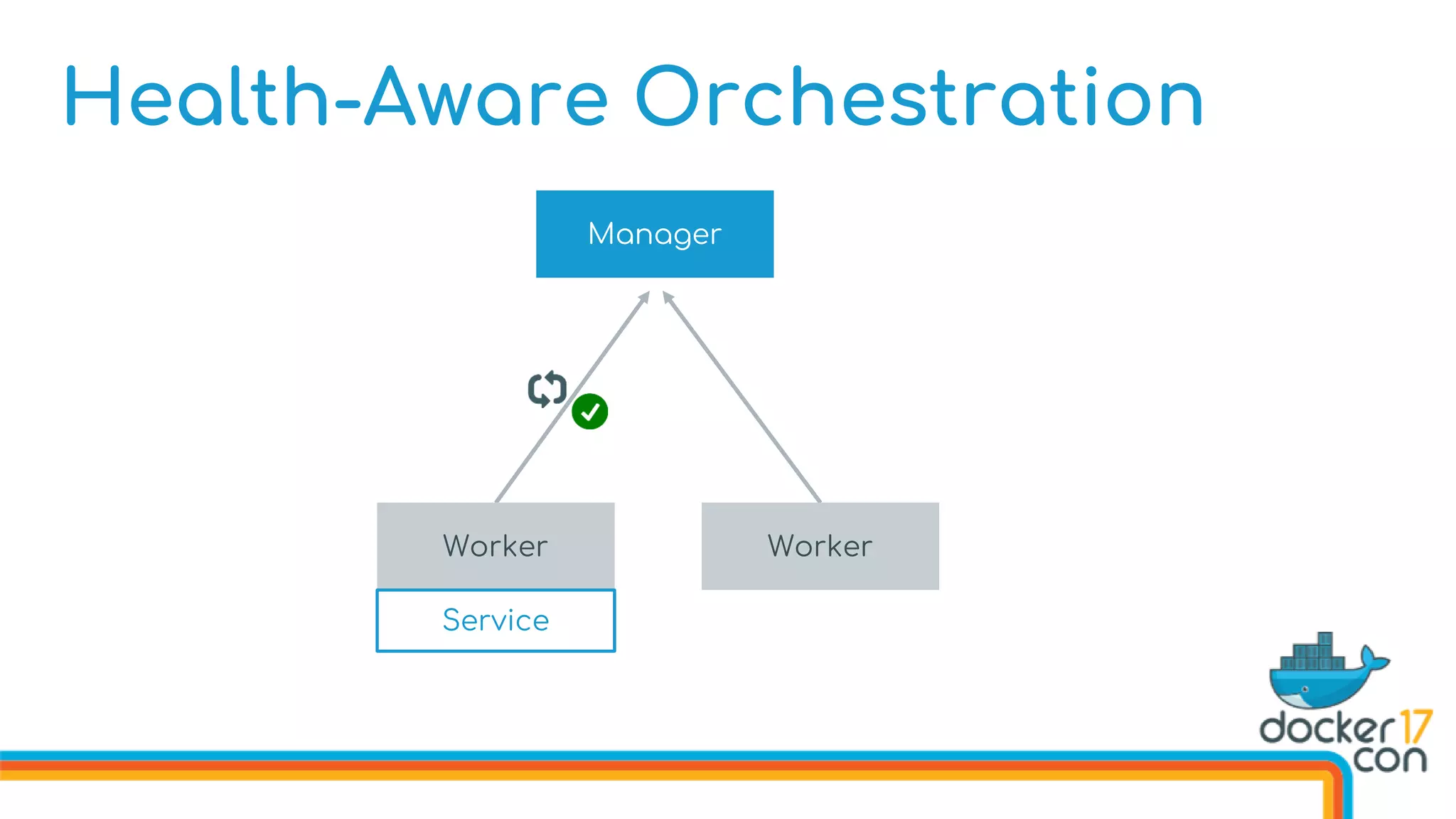
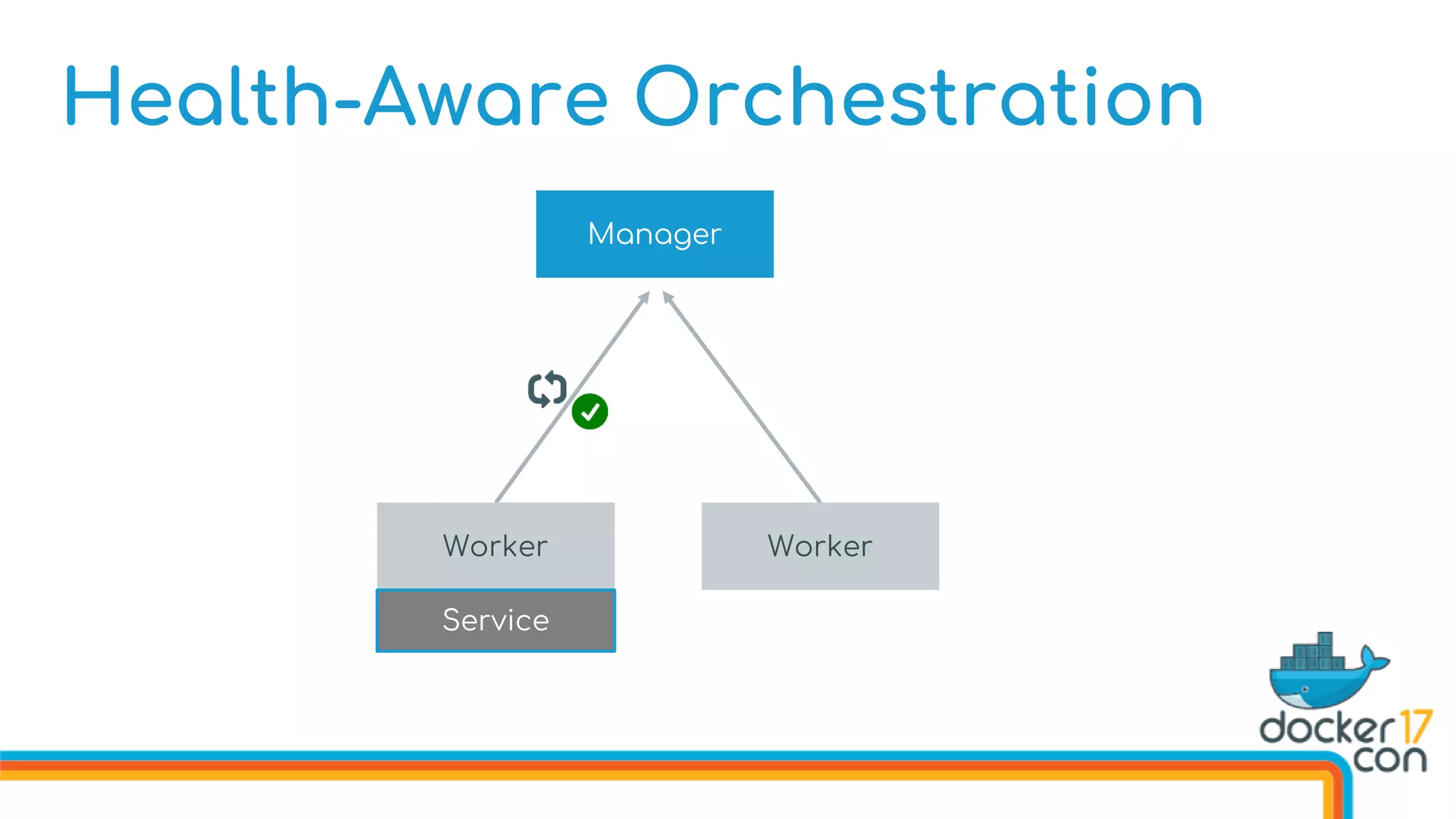
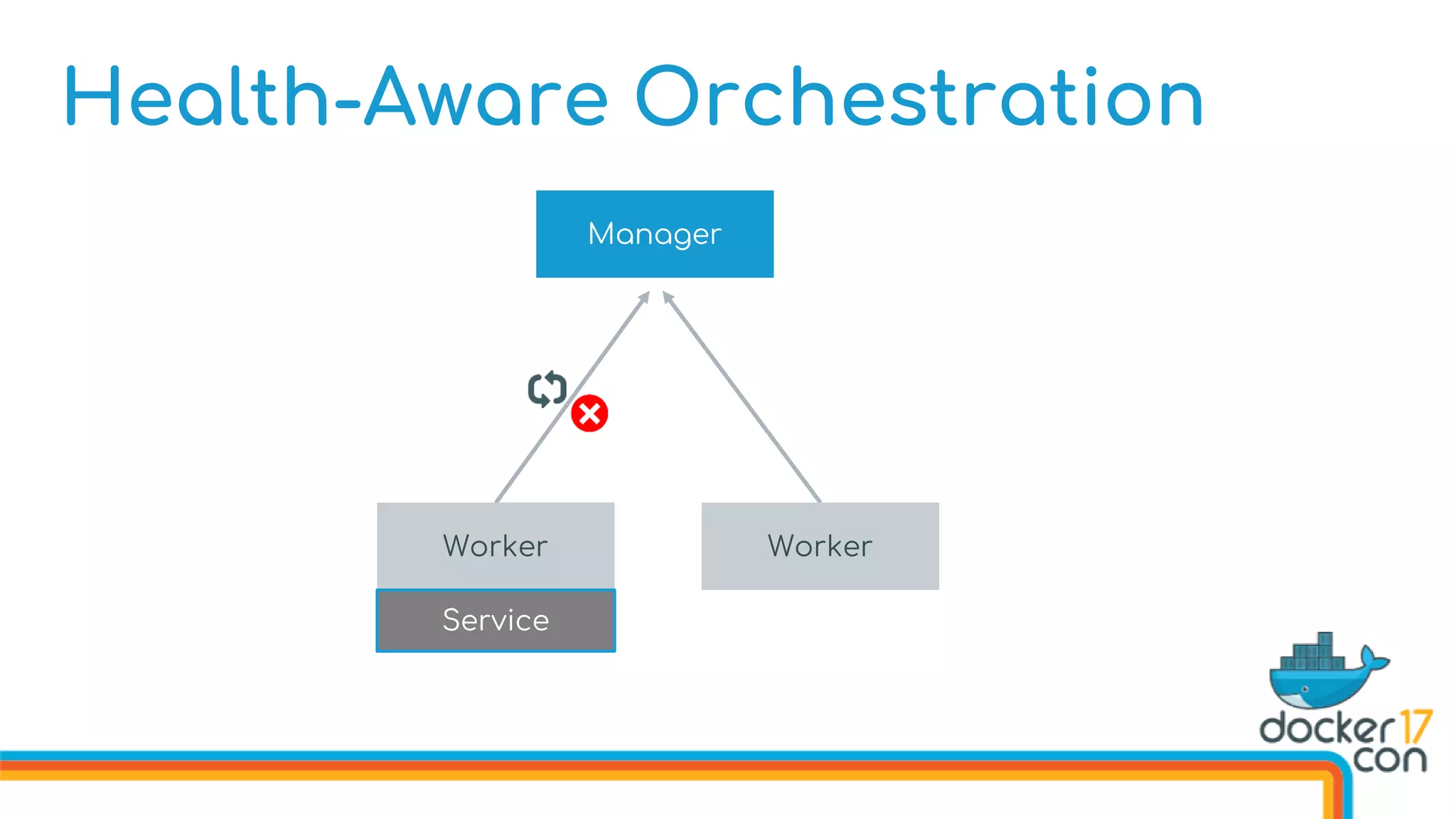
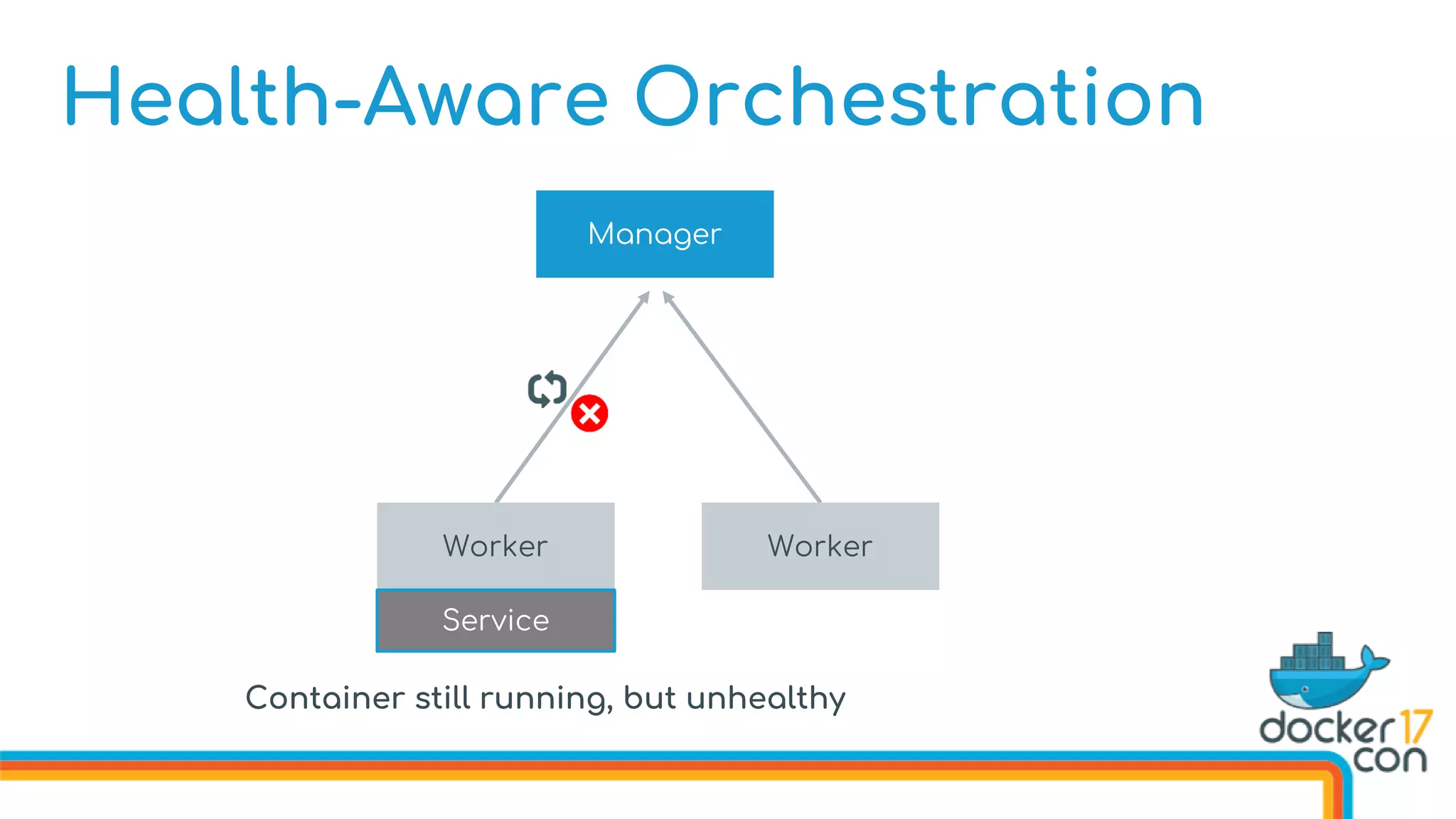
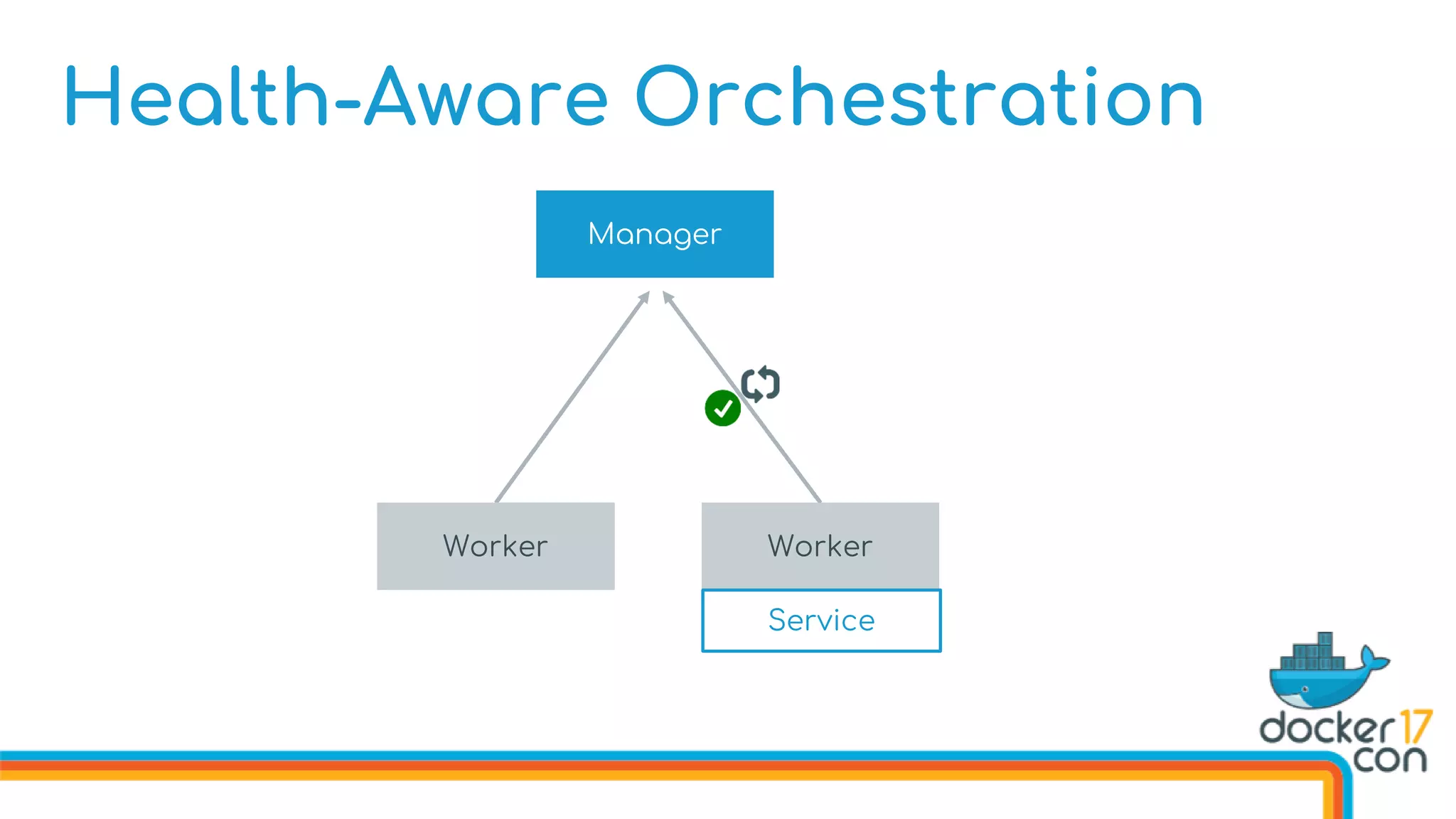
![Health-Aware Orchestration
Defining Image Healthchecks in the Dockerfile
FROM dockercon
. . .
HEALTHCHECK --interval 10s
--timeout 3s
--retries 5
CMD curl http://localhost/health
. . .
CMD [“start”]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-76-2048.jpg)




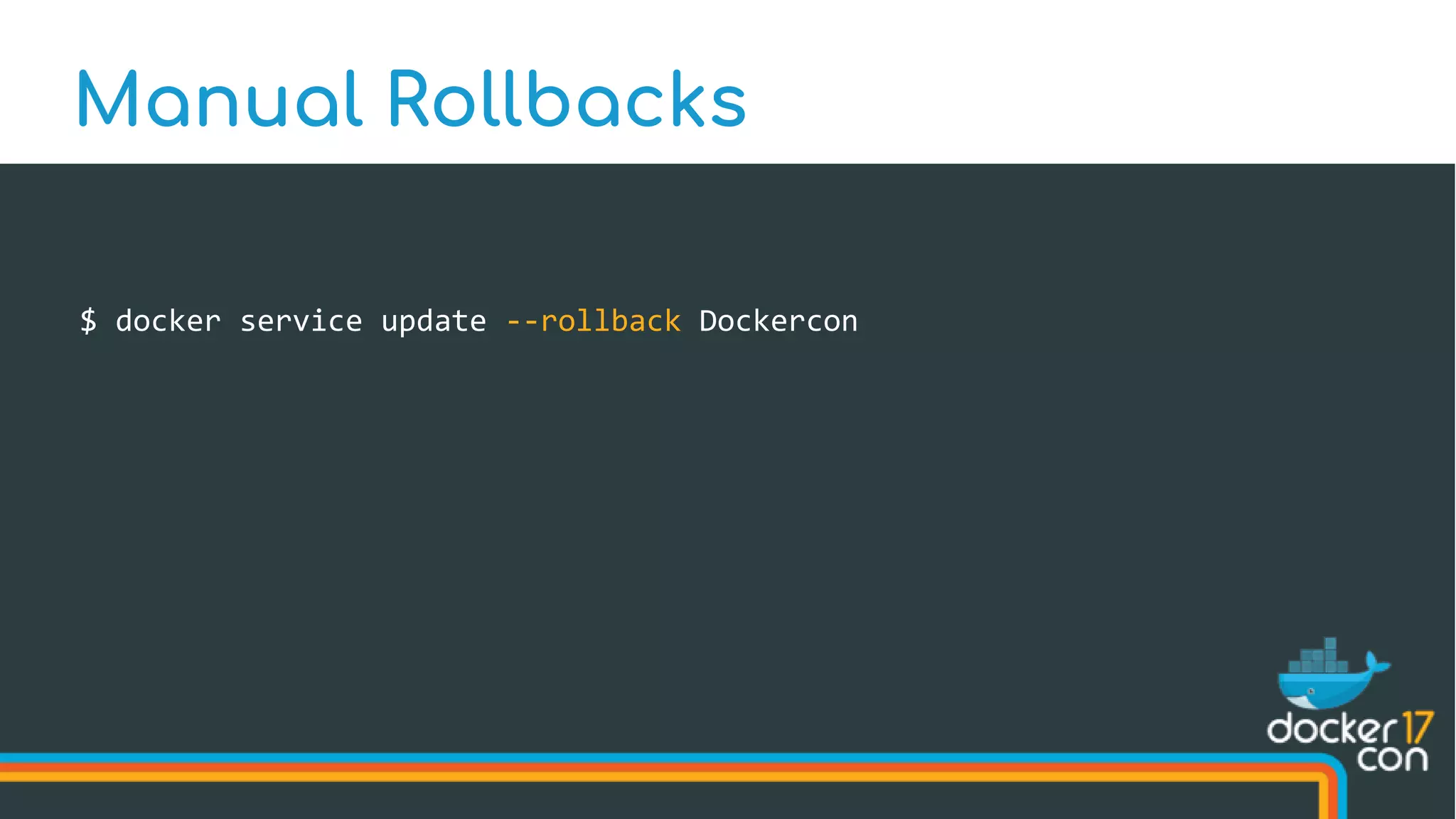
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-89-2048.jpg)

![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image: dockercon
# of replicas:
2017
Ports:
[80,443]
Previous Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-91-2048.jpg)
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image: dockercon
# of replicas:
2017
Ports:
[80,443]
Previous Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-93-2048.jpg)
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image: dockercon
# of replicas:
2017
Ports:
[80,443]
Previous Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-94-2048.jpg)
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image: dockercon
# of replicas:
2017
Ports:
[80,443]
Previous Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-95-2048.jpg)
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Service Spec
Image: dockercon
# of replicas:
2017
Ports:
[80,443]
Service Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-96-2048.jpg)
![Manual Rollbacks
Service Object
Name:
Dockercon
Service State
Task States
Network Status
Previous Spec
Image:
dockercon
# of replicas:
2017
Ports:
[80,443]
Service Spec
Image:
texas
# of replicas:
1845
Ports:
[80]](https://image.slidesharecdn.com/drewandnishantunderthehood2017-170504025426/75/Under-the-Hood-with-Docker-Swarm-Mode-Drew-Erny-and-Nishant-Totla-Docker-97-2048.jpg)