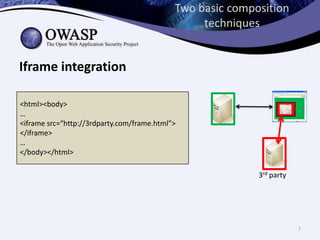
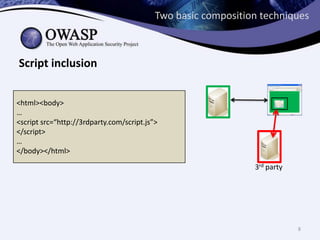
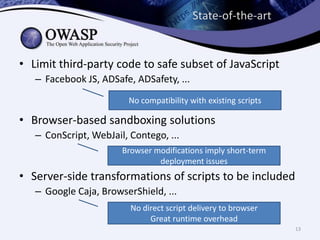
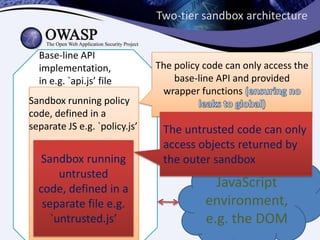
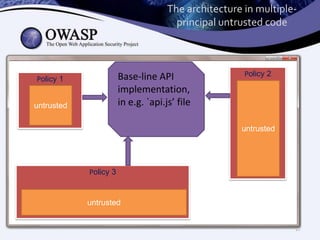
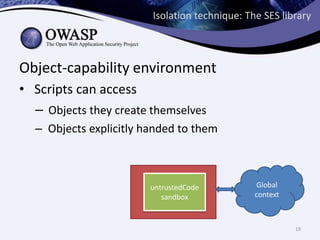
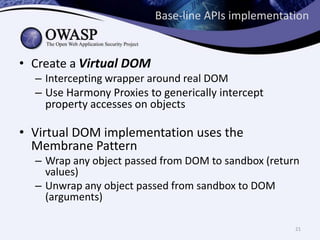
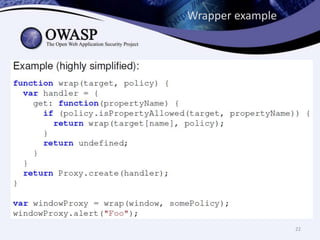
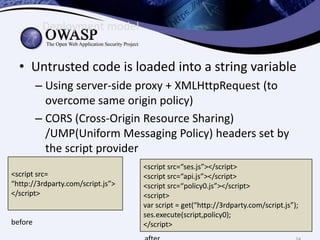
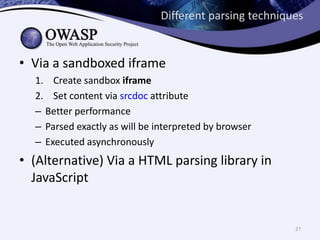
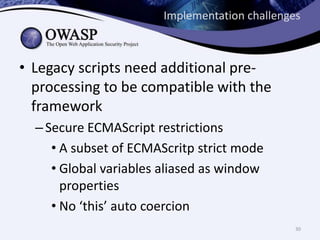
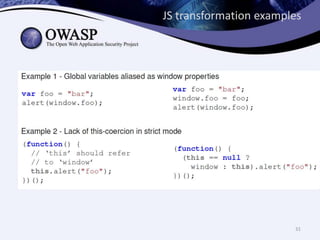
This document discusses sandboxing untrusted JavaScript from third parties to improve security. It proposes a two-tier sandbox architecture that uses JavaScript libraries and wrappers, without requiring browser modifications. Untrusted code is executed in an isolated environment defined by policy code, and can only access approved APIs. This approach aims to mediate access between code and the browser securely and efficiently while maintaining compatibility with existing third-party scripts.




![92% of all websites use JavaScript
[w3techs.com]
“88.45% of the Alexa top 10,000 web
sites included at least one remote
JavaScript library”
CCS’12
5](https://image.slidesharecdn.com/phuappsec13-131217205124-phpapp02/85/Phu-appsec13-5-320.jpg)