The document discusses cross-site scripting (XSS) vulnerabilities, techniques for exploitation, and mitigation strategies. It emphasizes the importance of input validation, output encoding, and the use of security frameworks to prevent XSS attacks. Additionally, it covers various types of XSS and provides references to tools and resources for security best practices.






![Sources of untrusted data
• Url
• Form data
• Cookies
• Request headers
• External services
• Database
Request[“data”]
$_REQUEST
request.getParameter](https://image.slidesharecdn.com/insufficientdatavalidationrisks-xss-140918075648-phpapp02/85/Devouring-Security-Insufficient-data-validation-risks-Cross-Site-Scripting-11-320.jpg)







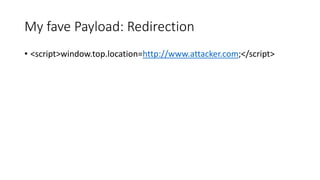
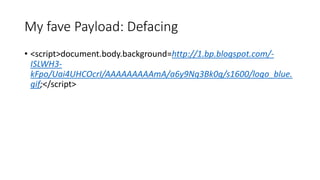
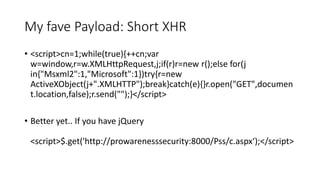


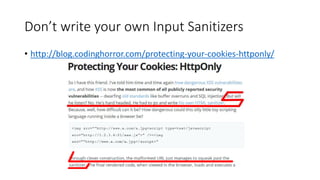








![XSS Defences
• NoScript addon
• Content-Security-Policy [No wide browser support yet especially IE]](https://image.slidesharecdn.com/insufficientdatavalidationrisks-xss-140918075648-phpapp02/85/Devouring-Security-Insufficient-data-validation-risks-Cross-Site-Scripting-34-320.jpg)