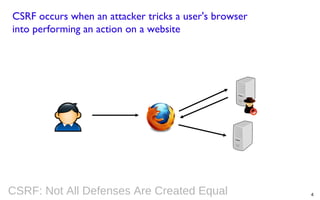
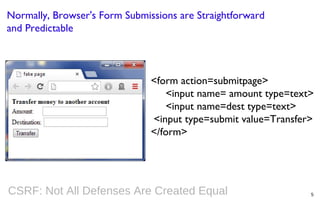
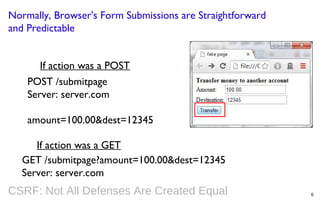
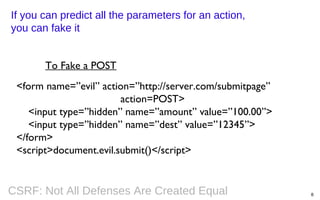
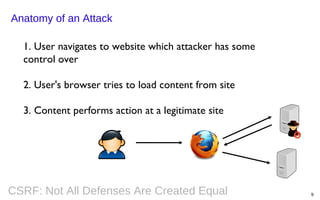
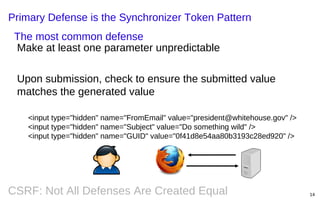
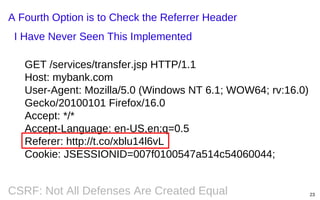
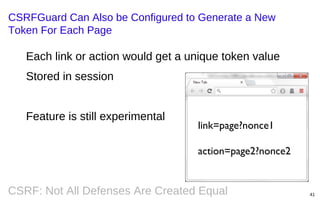
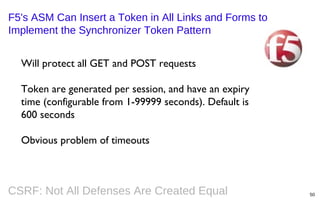
This document summarizes a presentation on defending against CSRF (cross-site request forgery) attacks. It discusses four main design patterns for CSRF defenses: the synchronizer token pattern, double submit cookies, challenge-response systems, and checking the referrer header. It then provides details on implementing these patterns, specifically looking at libraries and features in .NET, .NET MVC, Anticsrf, CSRFGuard, and HDIV that can help implement CSRF tokens and validation. The document covers the tradeoffs of different approaches and considerations for using them effectively on the code and server level.






















![.net MVC Applications Can Use AntiForgeryToken
Validate the token in the controller
[ValidateAntiForgeryToken]
public ActionResult FunctionToProtect()
{
// this is now run only if the token is valid
}
CSRF: Not All Defenses Are Created Equal
33](https://image.slidesharecdn.com/csrf-not-all-defenses-are-created-equal-131217205018-phpapp01/85/Csrf-not-all-defenses-are-created-equal-33-320.jpg)
















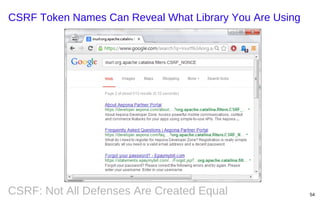


![A single XSS flaw makes all of these CSRF defenses useless
There are numerous ways for a script to access the CSRF
token value
document.cookie
document.getElementByID('csrftoken')
document.forms[0].elements[0]
CSRF: Not All Defenses Are Created Equal
58](https://image.slidesharecdn.com/csrf-not-all-defenses-are-created-equal-131217205018-phpapp01/85/Csrf-not-all-defenses-are-created-equal-58-320.jpg)



