Embed presentation
Downloaded 63 times


![AND 1 = "blah" -> Error ? Why? - Because "blah" can Not be converted to Integer in order to compare with 1 - What If attackers replace "blah" with a [ SQL query that returns a String ] ??](https://image.slidesharecdn.com/sqlinjectionattacksanddefensepresentatio1-100208183724-phpapp01/85/Sql-Injection-Attacks-And-Defense-Presentatio-1-5-320.jpg)


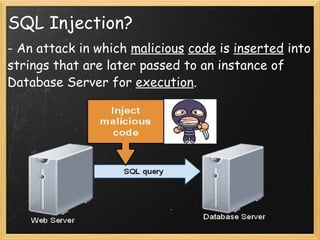
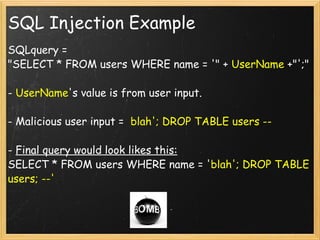
SQL injection is an attack where malicious code is inserted into strings that are passed to a database for execution. For example, a query may select users by name, where the name value comes from user input. A malicious user could insert code like '; DROP TABLE users --' to drop the users table. To prevent SQL injection, user input should not be trusted and meta-characters should be escaped, or parameterized statements using stored procedures can be used. Proper error handling is also important.




![AND 1 = "blah" -> Error ? Why? - Because "blah" can Not be converted to Integer in order to compare with 1 - What If attackers replace "blah" with a [ SQL query that returns a String ] ??](https://image.slidesharecdn.com/sqlinjectionattacksanddefensepresentatio1-100208183724-phpapp01/85/Sql-Injection-Attacks-And-Defense-Presentatio-1-5-320.jpg)

